One frustrating aspect of email phishing is the frequency with which scammers fall back on tried-and-true methods that really have no business working these days. Like attaching a phishing email to a traditional, clean email message, or leveraging link redirects on LinkedIn, or abusing an encoding method that makes it easy to disguise booby-trapped Microsoft Windows files as relatively harmless documents.
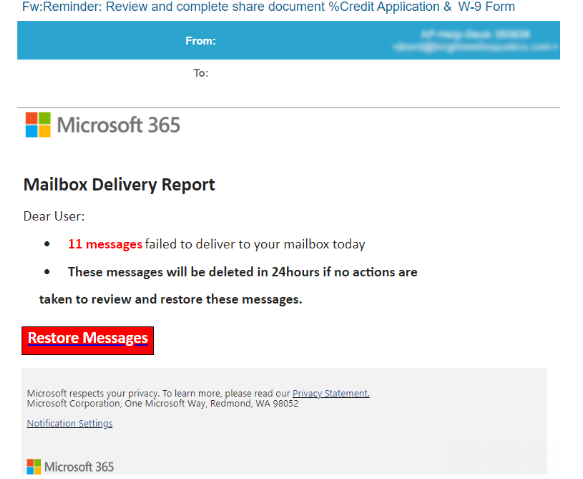
KrebsOnSecurity recently heard from a reader who was puzzled over an email he’d just received saying he needed to review and complete a supplied W-9 tax form. The missive was made to appear as if it were part of a mailbox delivery report from Microsoft 365 about messages that had failed to deliver.
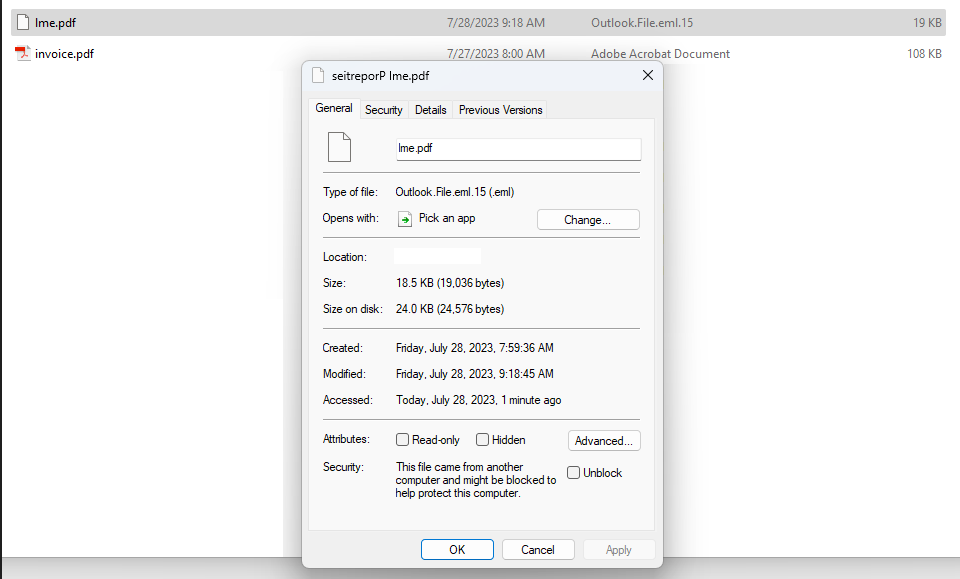
The reader, who asked to remain anonymous, said the phishing message contained an attachment that appeared to have a file extension of “.pdf,” but something about it seemed off. For example, when he downloaded and tried to rename the file, the right arrow key on the keyboard moved his cursor to the left, and vice versa.
The file included in this phishing scam uses what’s known as a “right-to-left override” or RLO character. RLO is a special character within unicode — an encoding system that allows computers to exchange information regardless of the language used — that supports languages written from right to left, such as Arabic and Hebrew.
Look carefully at the screenshot below and you’ll notice that while Microsoft Windows says the file attached to the phishing message is named “lme.pdf,” the full filename is “fdp.eml” spelled backwards. In essence, this is a .eml file — an electronic mail format or email saved in plain text — masquerading as a .PDF file.
“The email came through Microsoft Office 365 with all the detections turned on and was not caught,” the reader continued. “When the same email is sent through Mimecast, Mimecast is smart enough to detect the encoding and it renames the attachment to ‘___fdp.eml.’ One would think Microsoft would have had plenty of time by now to address this.”
Indeed, KrebsOnSecurity first covered RLO-based phishing attacks back in 2011, and even then it wasn’t a new trick.
Opening the .eml file generates a rendering of a webpage that mimics an alert from Microsoft about wayward messages awaiting restoration to your inbox. Clicking on the “Restore Messages” link there bounces you through an open redirect on LinkedIn before forwarding to the phishing webpage.
As noted here last year, scammers have long taken advantage of a marketing feature on the business networking site which lets them create a LinkedIn.com link that bounces your browser to other websites, such as phishing pages that mimic top online brands (but chiefly Linkedin’s parent firm Microsoft).
The landing page after the LinkedIn redirect displays what appears to be an Office 365 login page, which is naturally a phishing website made to look like an official Microsoft Office property.
In summary, this phishing scam uses an old RLO trick to fool Microsoft Windows into thinking the attached file is something else, and when clicked the link uses an open redirect on a Microsoft-owned website (LinkedIn) to send people to a phishing page that spoofs Microsoft and tries to steal customer email credentials.
According to the latest figures from Check Point Software, Microsoft was by far the most impersonated brand for phishing scams in the second quarter of 2023, accounting for nearly 30 percent of all brand phishing attempts.
An unsolicited message that arrives with one of these .eml files as an attachment is more than likely to be a phishing lure. The best advice to sidestep phishing scams is to avoid clicking on links that arrive unbidden in emails, text messages and other mediums. Most phishing scams invoke a temporal element that warns of dire consequences should you fail to respond or act quickly.
If you’re unsure whether a message is legitimate, take a deep breath and visit the site or service in question manually — ideally, using a browser bookmark to avoid potential typosquatting sites.




Email is a Continuous Integration/Continuous Delivery (CI/CD) Environment in Fed speak. That’s why the tricks come back around.
There’s general guidance: https://media.defense.gov/2023/Jun/28/2003249466/-1/-1/0/CSI_DEFENDING_CI_CD_ENVIRONMENTS.PDF
re: “Teach a Man to Phish and He’s Set for Life”
This is an old saw from the UN … Give a man a fish and you’ve fed him for a day, teach a man to fish and you’ve fed him for life.
A coworker fixed it for me: Feed blowfish sushi to spammers as often as necessary.
Will the “Message source” on View tab show that this is a scam?
I consider anything that says “Dear User”, or “Dear Customer”, to be a spam or phishing email. Legitimate emails know my name.
Sure, until the scammer can find out your trivially available name, (or address, DOB, phone#, etc.)
Then they’ve got just enough to fool you into making a mistake and clicking the link.
Definitely agree this is not a good UX, but looking at it from the developer perspective, Windows is handling the encoded character correctly by displaying the characters after the invisible special characters from right to left. Mimecast fails to understand the encoding and replaces the special character with underscores. Rather than Mimecast being “smart enough”, we got lucky it failed in the way it did.
You can use software restriction policy (secpol.msc) to block executable files with an RLO character in the name, though that won’t help in this case where the file is read but not executed. To do it add an “Additional Rules” new disallowed path rule with two asterisks ** and then put the cursor between the asterisks, right-click and choose Insert Unicode Control Character RLO from the menu. Confirm the cursor is still in between the two asterisks. Though you can’t see the RLO control character it’s there. To test, create one of the “Designated File Types” (eg bat or something) executable file and then add RLO anywhere in the filename. For example mrof.bat and make the batch script one line the command “pause”. It should run and pause. Rename the file and put the cursor at the beginning of the file name, insert RLO and it shows as tab.form. When you click on it again it should say blocked by software restriction policy or blocked by administrator.
From the makers of Windows 9/11 – (now shipping with adverts right in the menu bar,
because our users demanded it) – and the leading information-freeing cloud service
formerly known as Azure, now rando-rebranded for enhanced multi-factor obscurity,
it’s LinkedIn, the pseudo-obligatory opt-in self-pwn for “lanoisseforp” network marketing,
featuring random pen-IQ tests to keep users at their very best security posture, or else!
Clippy has detected your organization is trying to do work, are you sure?
Click YES to EOL, or NO to subscribe to this insanity for a monthly fee.
(bleepingcomputer.com/news/microsoft/microsoft-fixes-flaw-after-being-called-irresponsible-by-tenable-ceo/)
TLDR, “Did Microsoft quickly fix the issue that could effectively lead to the breach of multiple customers’ networks and services? Of course not. They took more than 90 days to implement a partial fix – and only for new applications loaded in the service,”
“That means that as of today, the bank I referenced above is still vulnerable, more than 120 days since we reported the issue, as are all of the other organizations that had launched the service prior to the fix. And, to the best of our knowledge, they still have no idea they are at risk and therefore can’t make an informed decision about compensating controls and other risk mitigating actions.”
“Change the product name and pretend it never happened.”
“Boss… you can’t just… everyone can see everything…”
“Azure… 2. Secure Edition. I don’t care, make something up by lunch.”
Here’s a free to to fix and remove all RTL characters in a files.
https://metadataconsulting.blogspot.com/2022/02/How-to-fix-right-to-left-files-bulk-command-line-tool.html
I’ve already switched to using an e-mail account with a long and hard to guess username for banks, credit card companies, and insurance and have set e-mail filters that check to see if any e-mail claiming to be from each bank is being directed to the proper e-mail for that bank, credit card company, or insurance company. If my address used in the e-mail does not match the supposed sender, then it flags the e-mail with a “WARNING” tag to help warn me that it is probably bogus.
For example, I am receiving more and more e-mails that purport to be from one certain bank but to an e-mail address that is not the one for that bank. The addresses are flagged which makes them trivial to spot. Digging into the headers makes it clear that they did not come from the bank.
One thing that I think would be useful is if every e-mail from the banks would be digitally signed to verify that they were actually from the bank. What would be really cool is if an e-mail could have multiple layers of digital signature. For example, a digital signature for the employee sending the e-mail, a digital signature for that person’s department, and a digital signature for the bank itself. The same would go for anyone else, especially from government agencies. Even if a scammer managed to steal one private key, there were be more that would be needed for all signatures to match.
Your approach is similar to what you can do with some email forwarding services that make it easy to use aliases, with a simple username but with an extension that acts like an email PIN of sorts. If the sender purporting to be your bank uses the address that you used for a different party, the message is visibly a scam. I use ManyMe.com for this purpose.
The root cause of phishing and all other exploits coming around again and being a continuous threat is the total lack of focus on software assurance. The software industry needs to stop getting a pass by being treated as something special. It is not and should come under full engineering discipline just like avionics and automotive industries. Software in avionics and automotive components is not even rigorously tested and quality controlled like the mechanical and electrical components. Real security, software, and systems engineering should be MANDATORY on all software put out for commercial use such that attacks become extremely hard to develop. Artificial Intelligence is constantly being touted but again security and software assurance and quality control is the last thing to get any attention. Why? The answer is government incompetence in real governance and understanding and corporate greed and lack of due diligence. I lived through the development of the technology over the last half century and I am well into my sixties and I still see software treated as a novelty far too often instead of making it a sector needing compliance with mandated engineering standards and quality assurance that meets the obligation of due diligence and due care. All the technology nuts will say that having all this basic engineering discipline will “stifle innovation” and I say, rubbish because we do not need anymore vulnerable and unreliable software that we now rely on for serious business.
As a retired Software Engineer your comments are spot on. I once had a CEO who posed the question, “Fast and Wrong or Slow and Right”. Generally, companies choose the former. Sadly, many executives (and some engineers) are clueless when it comes to developing quality software. In essence, software customers are really beta testers and sometimes even alpha!
Software is everywhere. It’s in your computer, it’s in your phone, it’s in your car. All of your appliances use software too. Your TV channels and streaming services are driven by software. Most of your food has been processed and packaged by software. The electricity, natural gas and water coming into your house is controlled by software. And the outgoing water is treated by software too. Alternative fuels are managed by software. Your furniture was probably designed using software, as well as your entire house. Children’s toys and games, more software. And when you go into a hospital, software monitors your vitals.
When you think about it, most people want to do a good job … and most people have done a good job, including software developers. Software is complicated. Are there mistakes? Sure. Can we do better? Sure. I’ve reviewed bad software before, but I’ve also seen a lot of well-written standards-based code too.
Anything designed by people is going to be flawed. It’s a testament to our collective creativity that things work as well as they do. For me, the important metric to watch is what happens once a flaw is discovered. Is it addressed and corrected? Or is it swept under the rug and ignored? The article illustrates that concept perfectly.
Don’t worry, AI will hallucinate the solution to everything.
Very informative. The urgency in the message “24 hours” should be a flag too.
Is there a way to:
1) disable execution of binaries with unicode characters in the filename or at least make it EXTREMELY visible that there’s special characters in the filename (I did not consent to my system “helpfully” displaying heiroglyphs I cannot read — even Firefox has a very easy to fatfinger shortcut to swap to RTL that you can’t disable)
2) disable execution of .BAT, .SCR, .COM, .PS1, etc
3) disable shortcut execution (the “rundll” trick)
3a) Disable shortcut DNS resolving, if you try to open a context menu on a network shortcut / URL shortcut, it presumably attempts a DNS lookup
4) require confirmation / UAC for ANY executable, even ones without administrator, or have a whitelist for known good applications
if there isn’t, consider Microsoft complacent in these scams. 2011 was a long time ago.
Not only do I regard Microsoft as complacent, I regard them as complicit.
how can we updated with this websites if something new article comes?
This has surfaced before, but I believe we are approaching the need to charge for email. Even a cost of $ 0.01, would make it costly for any spammer sending millions of email. It would also force individuals to protect their email accounts at the risk of running up big charges. Maybe $0.01, is not the right amount, but sending email for free has had a large cost on many individuals and companies.
The bad guys would simply pay with stolen credit cards. Only legitimate users would be impacted by the additional cost and responsibility. Larger retailers, banks, credit card companies would pass any new costs onto the customer. Small businesses and charities would be negatively affected.
This article is really interesting, and I appreciate your explanation. However, your comment that certain methods “really have no business working these days” begs the question, so why are they still working? The techy answer is too often “people are stupid” (or put more politely, “not as smart as I am”), but that’s not really helpful. With scads of money spent on technology and security awareness, we still find that old tricks are still “working these days.” So what is the fundamental solution? Changing email protocols or charging for email have been talked about for decades, but they are non-starters. What should we be doing that we’re not doing now?
Or as Marcus Ranum said way back in 2005, “If user education was going to work, it would have worked by now.”
Unix systems are also vulnerable to this, and even the base utilities can get quite confused when this trick is used.
Unicode is hard to get away from…