
Domain names ending in “.US” — the top-level domain for the United States — are among the most prevalent in phishing scams, new research shows. This is noteworthy because .US is overseen by the U.S. government, which is frequently the target of phishing domains ending in .US. Also, .US domains are only supposed to be available to U.S. citizens and to those who can demonstrate that they have a physical presence in the United States.
.US is the “country code top-level domain” or ccTLD of the United States. Most countries have their own ccTLDs: .MX for Mexico, for example, or .CA for Canada. But few other major countries in the world have anywhere near as many phishing domains each year as .US.
That’s according to The Interisle Consulting Group, which gathers phishing data from multiple industry sources and publishes an annual report on the latest trends. Interisle’s newest study examined six million phishing reports between May 1, 2022 and April 30, 2023, and found 30,000 .US phishing domains.
.US is overseen by the National Telecommunications and Information Administration (NTIA), an executive branch agency of the U.S. Department of Commerce. However, NTIA currently contracts out the management of the .US domain to GoDaddy, by far the world’s largest domain registrar.
Under NTIA regulations, the administrator of the .US registry must take certain steps to verify that their customers actually reside in the United States, or own organizations based in the U.S. But Interisle found that whatever GoDaddy was doing to manage that vetting process wasn’t working.
“The .US ‘nexus’ requirement theoretically limits registrations to parties with a national connection, but .US had very high numbers of phishing domains,” Interisle wrote. “This indicates a possible problem with the administration or application of the nexus requirements.”
Dean Marks is emeritus executive director for a group called the Coalition for Online Accountability, which has been critical of the NTIA’s stewardship of .US. Marks says virtually all European Union member state ccTLDs that enforce nexus restrictions also have massively lower levels of abuse due to their policies and oversight.
“Even very large ccTLDs, like .de for Germany — which has a far larger market share of domain name registrations than .US — have very low levels of abuse, including phishing and malware,” Marks told KrebsOnSecurity. “In my view, this situation with .US should not be acceptable to the U.S. government overall, nor to the US public.”
Marks said there are very few phishing domains ever registered in other ccTLDs that also restrict registrations to their citizens, such as .HU (Hungary), .NZ (New Zealand), and .FI (Finland), where a connection to the country, a proof of identity, or evidence of incorporation are required.
“Or .LK (Sri Lanka), where the acceptable use policy includes a ‘lock and suspend’ if domains are reported for suspicious activity,” Marks said. “These ccTLDs make a strong case for validating domain registrants in the interest of public safety.”
Sadly, .US has been a cesspool of phishing activity for many years. As far back as 2018, Interisle found .US domains were the worst in the world for spam, botnet (attack infrastructure for DDOS etc.) and illicit or harmful content. Back then, .US was being operated by a different contractor.
In response to questions from KrebsOnSecurity, GoDaddy said all .US registrants must certify that they meet the NTIA’s nexus requirements. But this appears to be little more than an affirmative response that is already pre-selected for all new registrants.
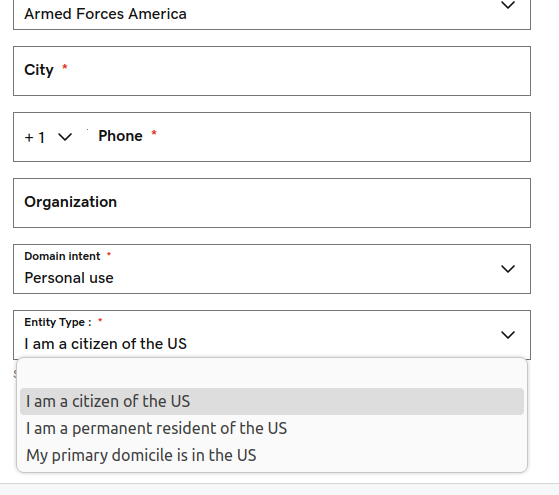
Attempting to register a .US domain through GoDaddy, for example, leads to a U.S. Registration Information page that auto-populates the nexus attestation field with the response, “I am a citizen of the US.” Other options include, “I am a permanent resident of the US,” and “My primary domicile is in the US.” It currently costs just $4.99 to obtain a .US domain through GoDaddy.
GoDaddy said it also conducts a scan of selected registration request information, and conducts “spot checks” on registrant information.
“We conduct regular reviews, per policy, of registration data within the Registry database to determine Nexus compliance with ongoing communications to registrars and registrants,” the company said in a written statement.
GoDaddy says it “is committed to supporting a safer online environment and proactively addressing this issue by assessing it against our own anti-abuse mitigation system.”
“We stand against DNS abuse in any form and maintain multiple systems and protocols to protect all the TLDs we operate,” the statement continued. “We will continue to work with registrars, cybersecurity firms and other stakeholders to make progress with this complex challenge.”
Interisle found significant numbers of .US domains were registered to attack some of the United States’ most prominent companies, including Bank of America, Amazon, Apple, AT&T, Citi, Comcast, Microsoft, Meta, and Target.
“Ironically, at least 109 of the .US domains in our data were used to attack the United States government, specifically the United States Postal Service and its customers,” Interisle wrote. “.US domains were also used to attack foreign government operations: six .US domains were used to attack Australian government services, six attacked Great’s Britain’s Royal Mail, one attacked Canada Post, and one attacked the Denmark Tax Authority.”
The NTIA recently published a proposal that would allow GoDaddy to redact registrant data from WHOIS registration records. The current charter for .US specifies that all .US registration records be public.
Interisle argues that without more stringent efforts to verify a United States nexus for new .US domain registrants, the NTIA’s proposal will make it even more difficult to identify phishers and verify registrants’ identities and nexus qualifications.
In a written statement, the NTIA said DNS abuse is a priority issue for the agency, and that NTIA supports “evidence-based policymaking.”
“We look forward to reviewing the report and will engage with our contractor for the .US domain on steps that we can take not only to address phishing, but the other forms of DNS abuse as well,” the statement reads.
Interisle sources its phishing data from several places, including the Anti-Phishing Working Group (APWG), OpenPhish, PhishTank, and Spamhaus. For more phishing facts, see Interisle’s 2023 Phishing Landscape report (PDF).’
Update, Sept. 5, 1:44 p.m. ET: Updated story with statement provided today by the NTIA.




In my experience, GoDaddy is not a serious company and should not be entrusted with anything resembling due diligence.
Absolutely verified.
I have been in the industry for over thirty years and GoDaddy has always perked my attention for being somewhat shady in all areas of their offerings.
A sketchy company at best.
“Also, .US domains are only supposed to be available to U.S. citizens and to those who can demonstrate that they have a physical presence in the United States.”
Nothing a pay-to-play contract with one of Hunter’s “consulting” firms can’t fix…
SHOW US THE LAPTOP!
I seriously hope you are being satirical and not shoveling this right-wing nonsense about corrupt Biden’s laptop…
RIIIGHT… it’s not real. 🙂 Spare me the partisan nuttery.
wow today I learn Krebs drinks the republican kool-aid, yikes!
I guess when you constantly have to explain sarcasm, it’s not worth it.
Facebook = meta, sarcasm = AI
heh heh – so right.
Brian is the man.
The reporting was thorough and plain, the analyses unbiased. Be nice.
The laptop has been shown, there is the data, now only we need any Judge willing to risk their life and career for it, which is unlikely to be found…
Oh, wonderful. When I relocated from Chicago to the DC metro area in ’09, I broke down, registered a domain, and bought hosting. I’m not a business, nor an organization, and I had no idea what state/commonwealth/district I’d wind up in… so I chose .us.
Some clarity around the .us previously being operated by another contractor…GoDaddy acquired Neustar’s registry business, which is how it ended up with the contract.
My issue with .us is they won’t let you use domain privacy. So it’s a non-stop parade of phone calls wanting to “help me with my site”
The phishers have probably been using stolen credit cards with a US address, a Gmail address and an anonymous US proxy IP address. It gives a few months for the phishing domain to live until the stolen credit card is detected. Those attributes alone cannot filter out US residents.
I asked GoDaddy about whether they used credit card data as one of the factors in determining nexus. According to them, it is not. Here’s what they said in response: “As the usTLD Administrator/Registry Operator, GoDaddy Registry does not process customer orders or hold credit card data.”
Does anybody really think that youtu.be is based in Belgium? ME is Montenegro and I’ve seen US companies use that as a TLD.
Countries have different policies. The .be domain is the country code top-level domain for Belgium, but it is open for registration to entities both inside and outside of Belgium.
As someone who worked at the Commerce Department and spent 20 years in DC circles, I can assure you that NTIA is an understaffed backwater bureau with no accountability that will do nothing about this.
Krebs on Security, are you some kind of establishment shill lying fraud?
American citizens and businesses NOT having the right to whois privacy like virtually every other type of domain user and registrant has been one of the BIGGEST SCANDALS of .US since it was released to the public in April 2002.
Placing American citizens and businesses in all kinds of obvious involuntary danger and risk, with all the ramifications for society and use and adoption of .US that entails.
And it’s no wonder why either – as in *anything but* the virtuous reasons that have been suggested for that travesty.
This obscene reality toward American citizens and businesses has been since day 1 nothing less than un-American, anti-American, and worse.
So try again, Krebs.
“The NTIA recently published a proposal that would allow GoDaddy to redact registrant data from WHOIS registration records. The current charter for .US specifies that all .US registration records be public.
Interisle argues that without more stringent efforts to verify a United States nexus for new .US domain registrants, the NTIA’s proposal will make it even more difficult to identify phishers and verify registrants’ identities and nexus qualifications.”
Looks like my first “PS” comment was too spicy to be approved out of moderation.
The short version is this:
To anyone so inclined, don’t even try it if you think you’re going to play dumb and pretend that whois privacy is any problem whatsoever for everyone who legitimately needs access to underlying data, including law enforcement, “powers that be,” and even people given access who shouldn’t be.
“Krebs on Security, are you some kind of establishment shill lying fraud?”
The best kind.
Which parent establishment would make it most obvious to you?
Nestle Kraft Monsanto Tesla Nvidia US Steel Disney
Well… Tesla is not part of the stablishment so you can discard that.
Also the Washcrapton Post, as he got fired from there…
I gotta disagree. Brian in my eyes goes against establishment views. It’s fine if you think some of his work isn’t but I digress.
It doesn’t seem to me that he’s advocating for no whois privacy. The article is about how the .US domain is supposed to be like other country domains, you only get it if you actually live there. So why not have the same validation standards for proving where you live as other country domains? That has nothing to do with whois, it’s just about the process of receiving a domain.
As for comments not showing, wait for moderation. Lot of my posts take time to go through, it should show up eventually unless your post was inappropriate.
Figures – my comment not appearing…
Ok, now it is, but I have a “PS” reply awaiting moderation, no doubt because I used the words “retar***” and “a**h*les,” though I did only use an “*” in the latter between the “h” and the “l.”
What do you think moderation is for exactly? BK’s forum is not a bathroom wall.
He’ll give you many chances to say what you’re trying to say if you say it respectfully.
Surely you can find a more clever way of getting your thoughts out in public than ****’s…
This issue with the .US is that it was implemented with the wrong oversight, period. The NTIA or any other organization needs an oversight board with such powers, best case appointed officials to sit on it, by-laws, and a clear charter, of course. simply put these things can’t be overlooked! since we know how they seem to be so are prone to politics.
Jeff, I was there in April 2002. It was released under a rock so the American public would virtually not even know it existed, has been kept that way ever since, and the scandal of not allowing whois privacy is for the same reasons. Hopefully I don’t need to spell it out. Or spell out the supreme irony of that in light of exactly when it was released, i.e. soon after 9/11. It’s an un-American, anti-American, national scandal and disgrace by the crooked “ptb.” Aka, business as usual.
Is there a reason why about half the comments that were here just minutes ago have been CENSORED now, Krebs?
Not sure why you’re so angry at me over this story, but your comments were never censored. They were held for moderation because you posted like 5 comments in a row very quickly, and one contained so much profanity it’s not going to be approved. Make your point civilly or not at all.
You should also mention that dot AI (ccTLD Anguilla) is being misused for Artificial intelligence
“is committed to supporting a safer online environment and proactively addressing this issue by assessing it against our own anti-abuse mitigation system.”
Someone used ChatGPT to write up their response. Love it when companies blatantly fail at something and their response is copy pasted “We’re committed to (generic platitude here)”. It drives me nuts, how about “We’re committed to raising our standards and from now on will be ensuring our customers will actually have U.S. residency”
maybe requiring id verification for buying domains will be useful
why are people allowed to get ccTLDs in the first place? these should be reserved for countries officials only.
I guess there is one part of the story that does make the US (and the meaning of the .us ccTLD) different from (most of) the rest. Nearly any relevant business in the US has been using the .com domain, all government authorities use .gov and nearly any relevant non-profit uses .org.
In (most of) the rest of the world, all of these would be using the respective countries’ ccTLD (yes I know, there are exceptions like the UK with .gov.uk, but these are rare on an international scale). This alone – the fact that government entities and their websites are involved in nearly all “other” countries – motivates some more decent oversight I would guess.
Then of course there are the “speaking” ccTLDs, that make some countries very different. Niue for one is very special, because its ccTLD .nu means “now” in Danish, Swedish and Norwegian. So going for a Niue ccTLD as a Scandinavian company, this allows you to occupy domain names like “Cars now” in their language. I believe there are some other similar examples, though the well known “youtu.be” is really an outlier.
In a nutshell, there may be good (commercial) reasons to allow also non-residents to use your ccTLD. However this really is a political decision and should be taken consciously rather than just somehow happen through sloppiness, as seems to be the case with .us.
That said, has any hardware store already occupied the domain “screws.us”?
Our government is consistent— > they protect the domains just like our southern border. In other words… nada. They’d rather throw billions upon billions on Ukraine and send American advisors over there to fight for another country’s borders
Let’s build a wall around the .US tld!
Some sort of protection is definitely needed, maybe razor balls…
It is this kind of attack which keeps me from using ANY password manager. A better solution is design an algorithm for your websites. I do the following.
1. For each site that requires a password I have picked one of three key mispelled words. One for financial, one for information, and one for purchases. I captialize the nth character of the word to meet password requirements.
2. I Add a special charater and a number to the end of this. The same for each site though.
3. I take the month and day of the first Monday of the current month of when I’m setting the password and insert it in a consistent location in the password. So, for setting a password on 9/6/23 the four characters added are “0904”.
I keep one file which has an abbreviation of the websites and the dates the password was set and which of the three keywords that I used for it. Sometimes websites can fall into more than one category.
Yes, it can take me several attempts to log into a site as I “think” that I know the password but I have to open up my file to see the actual date it was (re)set. And most importantly, this cryptic file is backed up offsite.
While I use my local browser to store passwords as I haven’t read that this is a serious threat to them, only that people feel that third party managers can create better passwords. I can live without that.
I like how the opportunity to comment on whois privacy was so well publicized so that people would even have a good chance to comment before the deadline which came and went only months ago. Never saw a single mention anywhere.
Reminds of that time in April 2002 when .us was released to the public virtually under a rock, and kept that way ever since to this day.
Sucks this is an issue with .US domains.
Should be a strong ccTLD considering it used to be only for US government institutions.
I run a mail server on a .us domain. I’ve had at least one site (a travel agency) who would not permit a .us email address. I can’t tell if that’s because their programmer assumed all emails end in .com, or if they were blocking it specifically. But I *am* concerned that I moved into a bad virtual neighborhood, and the postman will refuse to collect or deliver my mail.
I am probably better off because I’ve run that server for a couple of decades now, so there should be plenty of clues (other than the domain name) that my server is legitimate.
This is why we can’t have nice things…
GoDaddy says it “is committed to supporting a safer online environment and proactively addressing this issue by assessing it against our own anti-abuse mitigation system.”
Was that a legion of flying pigs I saw going past?
It looks written by ChatGPT, or worse, some Markov chain
eriously hope you are being satirical and not shoveling this right-wing nonsense about corrupt Biden’s laptop…maybe requiring id verification for buying domains will be useful