Many organizations — including quite a few Fortune 500 firms — have exposed web links that allow anyone to initiate a Zoom video conference meeting as a valid employee. These company-specific Zoom links, which include a permanent user ID number and an embedded passcode, can work indefinitely and expose an organization’s employees, customers or partners to phishing and other social engineering attacks.

Image: @Pressmaster on Shutterstock.
At issue is the Zoom Personal Meeting ID (PMI), which is a permanent identification number linked to your Zoom account and serves as your personal meeting room available around the clock. The PMI portion forms part of each new meeting URL created by that account, such as:
zoom.us/j/5551112222
Zoom has an option to include an encrypted passcode within a meeting invite link, which simplifies the process for attendees by eliminating the need to manually enter the passcode. Following the previous example, such a link might look something like this:
zoom.us/j/5551112222/pwd=jdjsklskldklsdksdklsdkll
Using your PMI to set up new meetings is convenient, but of course convenience often comes at the expense of security. Because the PMI remains the same for all meetings, anyone with your PMI link can join any ongoing meeting unless you have locked the meeting or activated Zoom’s Waiting Room feature.
Including an encrypted passcode in the Zoom link definitely makes it easier for attendees to join, but it might open your meetings to unwanted intruders if not handled responsibly. Particularly if that Zoom link is somehow indexed by Google or some other search engine, which happens to be the case for thousands of organizations.
Armed with one of these links, an attacker can create meetings and invite others using the identity of the authorized employee. And many companies using Zoom have made it easy to find recently created meeting links that include encrypted passcodes, because they have dedicated subdomains at Zoom.us.
Using the same method, KrebsOnSecurity also found working Zoom meeting links for The National Football League (NFL), LinkedIn, Oracle, Humana, Disney, Warner Bros, and Uber. And that was from just a few minutes of searching. And to illustrate the persistence of some of these Zoom links, Archive.org says several of the links were first created as far back as 2020 and 2021.
KrebsOnSecurity received a tip about the Zoom exposures from Charan Akiri, a researcher and security engineer at Reddit. In April 2023, this site featured research by Akiri showing that many public Salesforce websites were leaking private data, including banks and healthcare organizations (Akiri said Salesforce also had these open Zoom meeting links before he notified them).
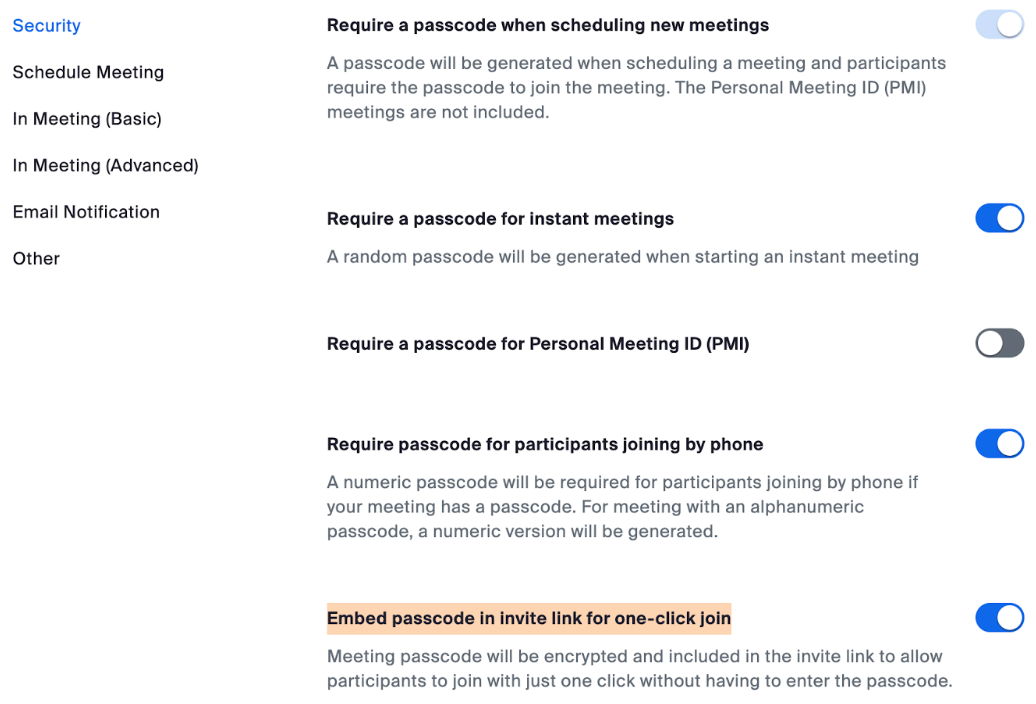
The Zoom links that exposed working meeting rooms all had enabled the highlighted option.
Akiri said the misuse of PMI links, particularly those with passcodes embedded, can give unauthorized individuals access to meetings.
“These one-click links, which are not subject to expiration or password requirement, can be exploited by attackers for impersonation,” Akiri said. “Attackers exploiting these vulnerabilities can impersonate companies, initiating meetings unknowingly to users. They can contact other employees or customers while posing as the company, gaining unauthorized access to confidential information, potentially for financial gain, recruitment, or fraudulent advertising campaigns.”
Akiri said he built a simple program to crawl the web for working Zoom meeting links from different organizations, and so far it has identified thousands of organizations with these perfectly functional zombie Zoom links.
According to Akiri, here are several tips for using Zoom links more safely:
Don’t Use Personal Meeting ID for Public Meetings: Your Personal Meeting ID (PMI) is the default meeting that launches when you start an ad hoc meeting. Your PMI doesn’t change unless you change it yourself, which makes it very useful if people need a way to reach you. But for public meetings, you should always schedule new meetings with randomly generated meeting IDs. That way, only invited attendees will know how to join your meeting. You can also turn off your PMI when starting an instant meeting in your profile settings.
Require a Passcode to Join: You can take meeting security even further by requiring a passcode to join your meetings. This feature can be applied to both your Personal Meeting ID, so only those with the passcode will be able to reach you, and to newly scheduled meetings. To learn all the ways to add a passcode for your meetings, see this support article.
Only Allow Registered or Domain Verified Users: Zoom can also give you peace of mind by letting you know exactly who will be attending your meeting. When scheduling a meeting, you can require attendees to register with their email, name, and custom questions. You can even customize your registration page with a banner and logo. By default, Zoom also restricts participants to those who are logged into Zoom, and you can even restrict it to Zoom users whose email address uses a certain domain.
Further reading: How to Keep Uninvited Guests Out of Your Zoom Meeting
Update 12:33 p.m.: The list of affected organizations was updated, because several companies listed apparently only exposed links that let anyone connect to existing, always-on meeting rooms — not initiate and completely control a Zoom meeting. The real danger with the zombie links described above is that anyone can find and use them to create new meetings and invite others.




With all the reports of attacks as well as your “Badguy uses for your PC” article and chart, I think that the day is rapidly approaching when I switch to using Qubes OS instead of the current Suse Linux on this workstation.
I’ve tried Qubes out before, but ran into issues of not having enough memory on this computer. My first step will be to max out the memory.
That said, I don’t use Zoom and I doubt that those who do would be at all amenable to switching to Qubes.
Good Halloween article. Heh I bet the owners of those links cry “I was hacked!” No.. you were careless.
After some thought, I am curious about the nature of the Zoom links with the encrypted passpcode. If web crawlers are finding them in web pages, then how did the links get into the web pages?
Are people posting them in mailing lists that are published on some web site? Posting them on web pages? News articles? Comments to news articles? Facebook accounts?
This must be a slow news day. Because I’m not following how this can be dangerous? Ok. So you are in some boring corporate meeting that no one wants to attend and then the bad guy joins in. And then what? The most he can do is yell “baba Booya” before he is kicked out. Plus; this is a video conference and no scammer would want to show their face on it.
Dennis, the point of the story is that companies are exposing links that let anyone *START* a Zoom meeting in the employee’s name, and then invite others. I can think of several ways this could be abused, particularly business email compromise scams.
It does nat take much imagination to see how impersonating a firm employee, or eavesdropping on inside information is a Bad Thing ™
Don’t you mean Zoombie link?
Winner!
Winner!
Questions I have:
1) Does Zoom Inc. have any statements or are they looking into additional mitigation options (thru new features or configurations) regarding this risk?
2) Is there a method for an organization to generate report on PMI existence and/or configurations that can be used to determine risk mitigation/acceptance plans?
Thank you for sharing this with us Brian. This is a very interesting wrinkle in the Zoom landscape.
I’ve known about zoom bombing (I think that’s what it’s called) where trolls connect to ongoing meetings to mess with people.
I had no idea that these links could allow someone to host in your name. I could definitely see this being used as a social engineering tactic. Thanks for the info!
Welcome to Fauci’s Covid world, circa 2020, when every school-aged kid figured this out. Seriously.
WTH does this have to do with COvid? or Fauci for that matter?
snowflake
♂️
I cannot seem to find the Security page that is displayed in the article. I am using Zoom on a Mac. The Settings tab does not have a Security tab. A search in the Zoom search bar for “security” does not bring up any results.
Can someone please advise me on how to access those security settings?
Thanks
Start by opening the Zoom app on your Mac.
Then join or start a meeting. If you’re in a meeting, you can find security options in the meeting controls.
During an active meeting, move the cursor to the bottom of the zoom window to open the meeting controls.
You should see a toolbar with various options.
Look for a button labeled Security among the meeting controls. This button allows you to access security features such as blocking a meeting, enabling a waiting room, or managing participant privileges.
NBC has a story about zoom zombies, but of a different kind:
https://www.nbcnews.com/business/autos/zoom-zombies-are-zoning-out-behind-wheel-after-video-calls-n1263367
From the article:
A new study by Root Insurance found 54 percent of the 1,819 adult motorists surveyed said they have had trouble concentrating on the road after videoconferences.
The younger the driver, the worse the problem. For Gen Z motorists, 65 percent reported losing focus while driving, while it was 61 percent for millennials and 48 percent for Gen Xers.
Many organizations are cost-conscious, including non-profits as a particular class. To avoid the cost of multiple ZOOM accounts, one person in the organization will get a ZOOM account that is shared throughout the organization. Collisions will occur. When a second host attempts to start a meeting after a first host has already started a meeting, the second host is denied. (Note: I may have the ZOOM terms and roles confused, so substitute appropriate terms for your vendor.) In a recent example, a 3-person meeting blocked a 90-person training meeting because no one knew the identity of the first host. Clearly there needs to be a scheduling protocol, but that is a high-order skill for some organizations. Using the example, the training for the 90-person team was blocked in favor of the 3-person team, and the organization had to reschedule training (to say nothing of the confusion during the original meeting interval). In The Olden Tymes, we used to have a similar problem with conference calls in that some hosts would send out both the user and host passcodes in their meeting invitations. That means someone could cause telecomm charges to be billed against another organization as a bit of intracorporate piracy.