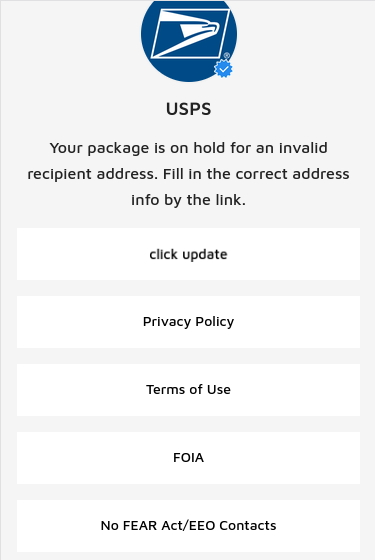
The fake USPS phishing page.
Recent weeks have seen a sizable uptick in the number of phishing scams targeting U.S. Postal Service (USPS) customers. Here’s a look at an extensive SMS phishing operation that tries to steal personal and financial data by spoofing the USPS, as well as postal services in at least a dozen other countries.
KrebsOnSecurity recently heard from a reader who received an SMS purporting to have been sent by the USPS, saying there was a problem with a package destined for the reader’s address. Clicking the link in the text message brings one to the domain usps.informedtrck[.]com.
The landing page generated by the phishing link includes the USPS logo, and says “Your package is on hold for an invalid recipient address. Fill in the correct address info by the link.” Below that message is a “Click update” button that takes the visitor to a page that asks for more information.
The remaining buttons on the phishing page all link to the real USPS.com website. After collecting your address information, the fake USPS site goes on to request additional personal and financial data.
This phishing domain was recently registered and its WHOIS ownership records are basically nonexistent. However, we can find some compelling clues about the extent of this operation by loading the phishing page in Developer Tools, a set of debugging features built into Firefox, Chrome and Safari that allow one to closely inspect a webpage’s code and operations.
Check out the bottom portion of the screenshot below, and you’ll notice that this phishing site fails to load some external resources, including an image from a link called fly.linkcdn[.]to.
A search on this domain at the always-useful URLscan.io shows that fly.linkcdn[.]to is tied to a slew of USPS-themed phishing domains. Here are just a few of those domains (links defanged to prevent accidental clicking):
usps.receivepost[.]com
usps.informedtrck[.]com
usps.trckspost[.]com
postreceive[.]com
usps.trckpackages[.]com
usps.infortrck[.]com
usps.quicktpos[.]com
usps.postreceive].]com
usps.revepost[.]com
trackingusps.infortrck[.]com
usps.receivepost[.]com
usps.trckmybusi[.]com
postreceive[.]com
tackingpos[.]com
usps.trckstamp[.]com
usa-usps[.]shop
usps.infortrck[.]com
unlistedstampreceive[.]com
usps.stampreceive[.]com
usps.stamppos[.]com
usps.stampspos[.]com
usps.trckmypost[.]com
usps.trckintern[.]com
usps.tackingpos[.]com
usps.posinformed[.]com
As we can see in the screenshot below, the developer tools console for informedtrck[.]com complains that the site is unable to load a Google Analytics code — UA-80133954-3 — which apparently was rejected for pointing to an invalid domain.
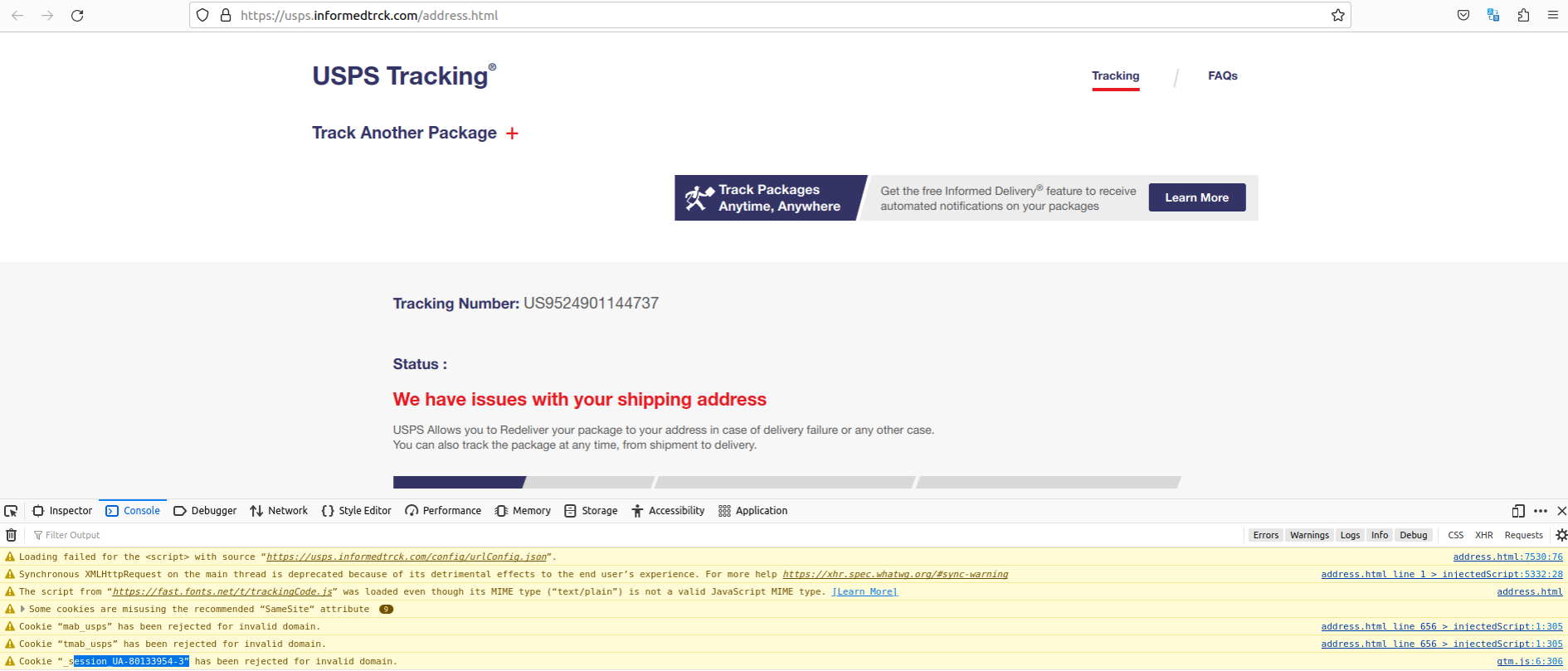
Notice the highlighted Google Analytics code exposed by a faulty Javascript element on the phishing website. Click to enlarge. That code actually belongs to the USPS.
The valid domain for that Google Analytics code is the official usps.com website. According to dnslytics.com, that same analytics code has shown up on at least six other nearly identical USPS phishing pages dating back nearly as many years, including onlineuspsexpress[.]com, which DomainTools.com says was registered way back in September 2018 to an individual in Nigeria.
A different domain with that same Google Analytics code that was registered in 2021 is peraltansepeda[.]com, which archive.org shows was running a similar set of phishing pages targeting USPS users. DomainTools.com indicates this website name was registered by phishers based in Indonesia.
DomainTools says the above-mentioned USPS phishing domain stamppos[.]com was registered in 2022 via Singapore-based Alibaba.com, but the registrant city and state listed for that domain says “Georgia, AL,” which is not a real location.
Alas, running a search for domains registered through Alibaba to anyone claiming to reside in Georgia, AL reveals nearly 300 recent postal phishing domains ending in “.top.” These domains are either administrative domains obscured by a password-protected login page, or are .top domains phishing customers of the USPS as well as postal services serving other countries.
Those other nations include the Australia Post, An Post (Ireland), Correos.es (Spain), the Costa Rican post, the Chilean Post, the Mexican Postal Service, Poste Italiane (Italy), PostNL (Netherlands), PostNord (Denmark, Norway and Sweden), and Posti (Finland). A complete list of these domains is available here (PDF).
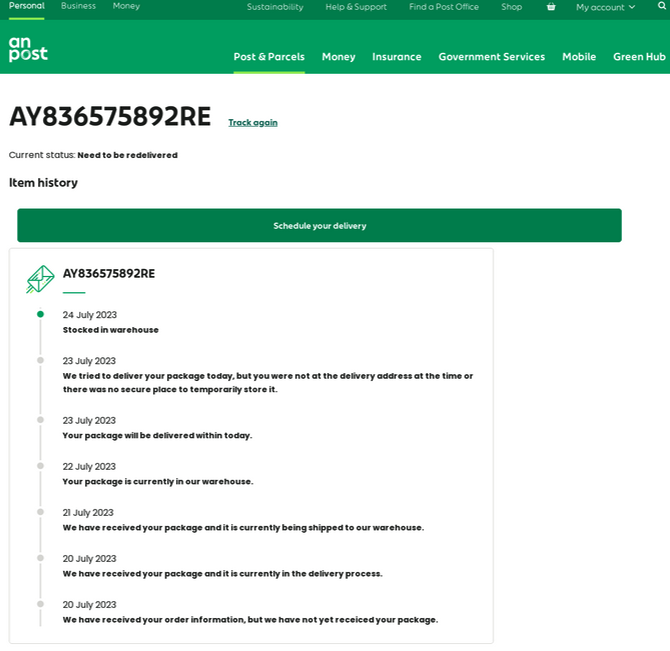
A phishing page targeting An Post, the state-owned provider of postal services in Ireland.
The Georgia, AL domains at Alibaba also encompass several that spoof sites claiming to collect outstanding road toll fees and fines on behalf of the governments of Australia, New Zealand and Singapore.
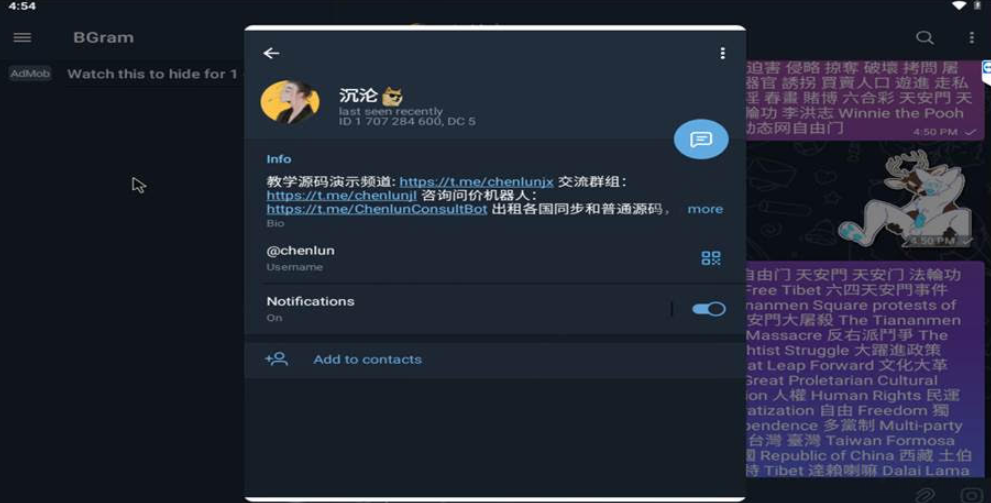
An anonymous reader wrote in to say they submitted fake information to the above-mentioned phishing site usps.receivepost[.]com via the malware sandbox any.run. A video recording of that analysis shows that the site sends any submitted data via an automated bot on the Telegram instant messaging service.
The traffic analysis just below the any.run video shows that any data collected by the phishing site is being sent to the Telegram user @chenlun, who offers to sell customized source code for phishing pages. From a review of @chenlun’s other Telegram channels, it appears this account is being massively spammed at the moment — possibly thanks to public attention brought by this story.
Meanwhile, researchers at DomainTools recently published a report on an apparently unrelated but equally sprawling SMS-based phishing campaign targeting USPS customers that appears to be the work of cybercriminals based in Iran.
Phishers tend to cast a wide net and often spoof entities that are broadly used by the local population, and few brands are going to have more household reach than domestic mail services. In June, the United Parcel Service (UPS) disclosed that fraudsters were abusing an online shipment tracking tool in Canada to send highly targeted SMS phishing messages that spoofed the UPS and other brands.
With the holiday shopping season nearly upon us, now is a great time to remind family and friends about the best advice to sidestep phishing scams: Avoid clicking on links or attachments that arrive unbidden in emails, text messages and other mediums. Most phishing scams invoke a temporal element that warns of negative consequences should you fail to respond or act quickly.
If you’re unsure whether the message is legitimate, take a deep breath and visit the site or service in question manually — ideally, using a browser bookmark so as to avoid potential typosquatting sites.
Update: Added information about the Telegram bot and any.run analysis.




Unfortunately these schemes are so prevalent because they work.
They do. I was actually expecting a package that was very late, so I thought this bogus USPS email and site were about the lost package. The result was having to get a new debit card three times in as many months, and a new bank account number. Then I found out that the package I was expecting was bogus, too. Always check the actual address of the sender and the recipient(s). If these don’t match up, don’t open any links. I just got another one about a supposed shared document in Google.
There is a less convenient way to find out whatever you want to find out.
Never click links. Phones are extra dangerous with the touch operation.
Pretend clicking any link is instant death.
I received a phishing SMS message that self-identified as being from the USPS about five hours ago and claiming that I have a package with an un-deliverable address. The postmistress does have my cell phone number but she wouldn’t have called for that — as long as it had my name she would just put it in my post office box even if there was no address at all other than town or zip code.
I’ve known her and her husband for years and know her voice well. I usually try to make her laugh. Like asking whether I could get pay for my annual post office box rent with a postal money order. She laughed and said that nobody ever asked her that before.
That’s one of the benefits from living in a small town in a sparsely populated county.
Unfortunately these scams are so prevalent because they work.
I also wonder how much responsibility website search companies like Google are to blame for this kind of redirecting of internet users to fake and malicious websites?
Whenever my children and I visit an internationally known fast-food restaurant chain, there is a website listed on the receipt stating that once you complete the online guest satisfaction survey, you will be given a code that will allow you to take part in a “buy one get one free” offer on your next visit to the restaurant. I am a computer and networking tech with advanced skills and more than 20 years of hands-on experience, but I have never been able to actually find the legitimate restaurant survey website. Instead, I have the phone number to the survey saved in my phone and I just call and complete the task over the phone. Why? Because the provided website leads me to a half-dozen spoofed or completely irrelevant sites. The potential for damages in this case are inconsequential, but the USPS and postal delivery spoofs are definitely real and need to be handled appropriately.
You really do the survey? That’s … interesting. To me, $3 isn’t worth my time – especially if I “had” to call instead of doing it online. Wow … this is crazy to me. Strange indeed.
Websites get hacked more often than search engines update their indexes for search results.
It’d be really bad for web sites if each time a search result included a hit, the search engine first loaded it. Not to mention the delay between when a user makes a search request and when the search engine could actually yield results if it had to wait to validate its results first.
Plus many sites behave differently when visited by a search engine, so search engines will sometimes on a much less frequent rate make a request without identifying as a search engine to catch cheating websites.
I get similar scams spoofing Australia Post, with URLs resembling theirs; e.g. they are not likely to use the .cc TLD when they have their own .com.au …
Here is another domain from similar phish/scam:
https://usps.modification-address[.]com
It’s behind Cloudflare, and apparently needs to be “activated” by the recipient; otherwise it just redirects to the regular USPS site. SMS message inviting clicks comes from Phillipines (+63 906 xxx xxxx) and goes as follows:
—8<———————————————————-
The USPS package arrived at the warehouse but could not be delivered due to incomplete address information. Please confirm your address in the link.
https://usps.modification-address[.]com
(Please reply Y, then exit the text message and open it again to activate the link, or copy the link and open it in your Safari browser).
The USPS team wishes you a wonderful day!
—8<———————————————————-
Thanks, Brian. Now I know it’s not just me being paranoid. Recently, I’ve had in excess of 200 phishing emails and SMS messages from Australia Post – “outstanding toll fees”, “can’t deliver parcel because address is incorrect” and so on. Not quite as interesting as the voicemail scam informing me that police are on the way to arrest me for not paying my taxes.
I got one like this about a week ago and almost clicked on the link. But figured it for phishing because the language was odd. Not wrong per Sw. Just odd. Especially the “Thank you for your prompt attention to this matter.” I’m glad you send me these emails. It made me think twice. I reported it as phishing to Google (got in gmail).
Wish you would take a look at and report on the multitude of counterfeit USPS stamps being sold on FaceBook AND Walmart dot com. Reports to both organizations go answered and the illegal sales continue.
I’d like to add that today I received a phish email supposedly from Amazon but was not.
Nothing new here except gullible people clicking links they shouldn’t be clicking. These are the same people who allow their company to become hacked stealing our data. Always, Always go the the site yourself from the correct url you type in to verify anything now days especially if the message is asking to enter or verify something because of a “problem”. Clicking on any links sent to a phone is the click of death no matter how legit or not legit they look. You click on it you are done period. Besides, SMS messages I see that are phishing messages are mangled in some way and don’t look anything like a real message so why would anyone click on them anyway?
Unlike most people, I still read email as plain text, as I don’t care about fancy fonts or letterhears, so this would fail for me instantly, based on one consideration, one that most people are clueless about.
It’s not .gov. Anything else is a fraud.
Have been seeing these for Canada Post for a couple of years. Text message says there are issues with the delivery of you item please clicke here etc
That usps.informedtrck[.]com domain actually matches a Site Fingerprint (https://www.bayse.io/blog/site-fingerprints-intro) that we’ve been tracking at Bayse Intelligence since late May (the attack is likely much older, but that’s when we enabled Site Fingerprints): https://www.bayse.io/site_fingerprint/structural_id/ce560ee56269f1903b3f1af02efb171cd090d3d6
^ That last link above shows over 4,000 different submissions to Bayse since May that match that attack pattern. Some of the results we’ve seen today (defanged) are:
uspsusps.quicktpos[.]com
trackpsot[.]top
com-nj[.]xyz
uspees[.]top
Some of the other USPS (and other postal service) campaigns we’re tracking are:
https://www.bayse.io/campaign/USPS%20Delivery%20Failed%20SMS%202 (USPS)
https://www.bayse.io/campaign/USPS%20Delivery%20Failed%20SMS (USPS)
https://www.bayse.io/campaign/Unknown_ccda581ed27ee6b0a82c379691946aec3195c228 (Poste Italiane, Correos, Australia Post)
https://www.bayse.io/campaign/Unknown_c0d5cf8da4094891bf231c99b0e1096ae0611444 (FedEx, La Poste, DHL)
This makes no sense to me. US post office delivers to an address, not a person or company. If the address isn’t correct how would they know who to contact – other than the shipper?
Not sure if this was intentional or not, but the telegram screenshot looks like it has furry porn in it.
I dunno if my last post worked, it looks like the telegram screenshot has an inappropriate sticker on it. Not sure if you noticed.
why are they still live on google ?
because there are billions of new pages being added every day… and google doesn’t have the time day after day to crawl them…
I have received 3 of these by RCS now.
The first occurred on the day that USPS was supposed to be delivering my free COVID tests. The message had some grammar problems but not enough to ensure it wasn’t actually from USPS. I thought it was strange that they had my mobile number, but I couldn’t remember if I had given that to the site which took the COVID test orders. So I wondered if perhaps that site, or USPS had been hacked.
As mentioned in the article, when I checked whois for the web site, it was registered with alibaba.
The real giveaway in all 3 messages I have received is that they come from +44 (UK) country codes. It really seems unlikely that the USPS would be sending messages from UK phone number.
It would be easier to deal with a phishing scam (just don’t click on it) than the scam where someone forwards THEIR mail to YOUR address as if they lived there. This is not illegal even though it is an attempt to piggyback onto the existing good credit, and potentially the identity, of someone at that address.
The Post Office will do nothing to stop the forwarding. I recommend signing up for informed delivery even if you do not need it so that you do not leave an opening for someone else to signup for the service on your address and then they can see what is getting put into your mailbox. They forward their mail to your addess and then have proof they are getting mail at that address using the informed delivery picture.
another domain linked to this but not listed is usposts-zis[dot]us
You can find a similar chain, which connects to more domains when you track the hosting especially. I started tracking after an SMS I got. At one point the graph became just too large and I had to stop there.
https://www.virustotal.com/graph/embed/g3dd69c9f3f7747ada3b5ab20735a4f1c9455c4145ecc431e883e54de3049a1d4?theme=dark
Pretty funny Brian kept gay furry porn uncensored in the Telegram screenshot
May I add your contact information by telegram
FYI (and FWIW), this week I saw one from UPS as well — same format and links as shown in the first screencap, just with a UPS logo instead.
I have been getting these fake, USPS “your package is at the warehouse” SMS messages, but they come from a 44 (UK) phone #. While I’m pretty sure they’re spoofing the caller ID, anyone should stop and think for a minute if you get something alleging to be from the USPS that originates from a UK phone #. Just sayin’. When I get emails, I will go oui of my way to locate the domain server and send copies of the original phish, the purportedly “official” links, the URL, and the IP it resolves to, along with the WHOIS lookup info, to the abuse@XXXX.com account(s). I don’t know if it ever does any good, but it makes me feel better!
I’ve always wondered if – I reply with so much bogus info , that it may annoy them enough to cross my email/ph# off their list. Anybody try that ?