The U.S. Department of Justice (DOJ) today said they arrested the alleged operator of 911 S5, a ten-year-old online anonymity service that was powered by what the director of the FBI called “likely the world’s largest botnet ever.” The arrest coincided with the seizure of the 911 S5 website and supporting infrastructure, which the government says turned computers running various “free VPN” products into Internet traffic relays that facilitated billions of dollars in online fraud and cybercrime.
The Cloud Router homepage, which was seized by the FBI this past weekend. Cloud Router was previously called 911 S5.
On May 24, authorities in Singapore arrested the alleged creator and operator of 911 S5, a 35-year-old Chinese national named YunHe Wang. In a statement on his arrest today, the DOJ said 911 S5 enabled cybercriminals to bypass financial fraud detection systems and steal billions of dollars from financial institutions, credit card issuers, and federal lending programs.
For example, the government estimates that 560,000 fraudulent unemployment insurance claims originated from compromised Internet addresses, resulting in a confirmed fraudulent loss exceeding $5.9 billion.
“Additionally, in evaluating suspected fraud loss to the Economic Injury Disaster Loan (EIDL) program, the United States estimates that more than 47,000 EIDL applications originated from IP addresses compromised by 911 S5,” the DOJ wrote. “Millions of dollars more were similarly identified by financial institutions in the United States as loss originating from IP addresses compromised by 911 S5.”
From 2015 to July 2022, 911 S5 sold access to hundreds of thousands of Microsoft Windows computers daily, as “proxies” that allowed customers to route their Internet traffic through PCs in virtually any country or city around the globe — but predominantly in the United States.

911 S5 built its proxy network mainly by offering “free” virtual private networking (VPN) services. 911’s VPN performed largely as advertised for the user — allowing them to surf the web anonymously — but it also quietly turned the user’s computer into a traffic relay for paying 911 S5 customers.
911 S5’s reliability and extremely low prices quickly made it one of the most popular services among denizens of the cybercrime underground, and the service became almost shorthand for connecting to that “last mile” of cybercrime. Namely, the ability to route one’s malicious traffic through a computer that is geographically close to the consumer whose stolen credit card is about to be used, or whose bank account is about to be emptied.
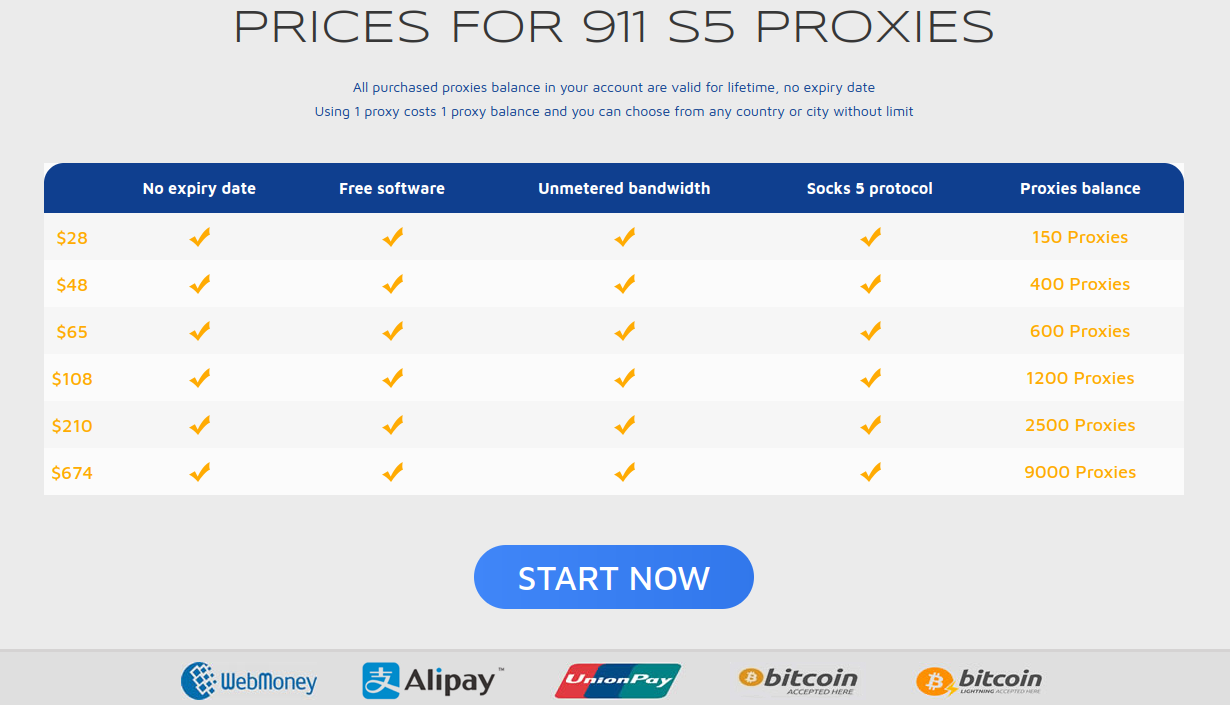
The prices page for 911 S5, circa July 2022. $28 would let users cycle through 150 proxies on this popular service.
KrebsOnSecurity first identified Mr. Wang as the proprietor of the popular service in a deep dive on 911 S5 published in July 2022. That story showed that 911 S5 had a history of paying people to install its software by secretly bundling it with other software — including fake security updates for common programs like Flash Player, and “cracked” or pirated commercial software distributed on file-sharing networks.
Ten days later, 911 S5 closed up shop, claiming it had been hacked. But experts soon tracked the reemergence of the proxy network by another name: Cloud Router.
The announcement of Wang’s arrest came less than 24 hours after the U.S. Department of the Treasury sanctioned Wang and two associates, as well as several companies the men allegedly used to launder the nearly $100 million in proceeds from 911 S5 and Cloud Router customers.
Cloud Router’s homepage now features a notice saying the domain has been seized by the U.S. government. In addition, the DOJ says it worked with authorities in Singapore, Thailand and Germany to search residences tied to the defendant, and seized approximately $30 million in assets.

The Cloud Router homepage now features a seizure notice from the FBI in multiple languages.
Those assets included a 2022 Ferrari F8 Spider S-A, a BMW i8, a BMW X7 M50d, a Rolls Royce, more than a dozen domestic and international bank accounts, over two dozen cryptocurrency wallets, several luxury wristwatches, and 21 residential or investment properties.
The government says Wang is charged with conspiracy to commit computer fraud, substantive computer fraud, conspiracy to commit wire fraud, and conspiracy to commit money laundering. If convicted on all counts, he faces a maximum penalty of 65 years in prison.
Brett Leatherman, deputy assistant director of the FBI’s Cyber Division, said the DOJ is working with the Singaporean government on extraditing Wang to face charges in the United States.
Leatherman encouraged Internet users to visit a new FBI webpage that can help people determine whether their computers may be part of the 911 S5 botnet, which the government says spanned more than 19 million individual computers in at least 190 countries.
Leatherman said 911 S5 and Cloud Router used several “free VPN” brands to lure consumers into installing the proxy service, including MaskVPN, DewVPN, PaladinVPN, Proxygate, Shield VPN, and ShineVPN.
“American citizens who didn’t know that their IP space was being utilized to attack US businesses or defraud the U.S. government, they were unaware,” Leatherman said. “But these kind of operations breed that awareness.”




The FBI page = “search for these 6 VPN clients on your machine and uninstall them, duh”
yet having “FooVPN.exe” right there in task manager visible to userland… come on folks.
Not exactly stealthy.
Wow! I always suspected free software and particularly free VPNs. But this was more mega-scale long-term than I expected. Thank you for reporting this will all the relevant details and links.
Great article. Given that it was so successful for 10 years, won’t another one pop up in its place?
Wow
I’d like to see how a VPN helps to steal millions of dollars. Can anyone explain how that works?
“911 S5’s reliability and extremely low prices quickly made it one of the most popular services among denizens of the cybercrime underground, and the service became almost shorthand for connecting to that “last mile” of cybercrime. Namely, the ability to route one’s malicious traffic through a computer that is geographically close to the consumer whose stolen credit card is about to be used, or whose bank account is about to be emptied.”
also…”For example, the government estimates that 560,000 fraudulent unemployment insurance claims originated from compromised Internet addresses, resulting in a confirmed fraudulent loss exceeding $5.9 billion.
“Additionally, in evaluating suspected fraud loss to the Economic Injury Disaster Loan (EIDL) program, the United States estimates that more than 47,000 EIDL applications originated from IP addresses compromised by 911 S5,” the DOJ wrote. “Millions of dollars more were similarly identified by financial institutions in the United States as loss originating from IP addresses compromised by 911 S5.””
Really? If you don’t already know then dont worry about it, the grownups have it all figured out lol
In addition to jail time, I hope the government seizes as much money as possible through the various corporate entities that he controls.
I wonder why the FBI implicitly advices to use the uninstall option that came with the malware:
“If the application doesn’t contain an uninstall option, then”
Are they sure, that it is not a secure re-installer ?
I’m here via following links from sans.org’s newsbytes newsletter.
I always use Revo Uninstaller but I’m sure the FBI wouldn’t endorse it. It runs
the app’s uninstaller first, then cleans up further, in almost every case it finds
something left behind. In the most notable case, uninstalling iTunes left behind
hundreds of files that Revo then deleted. Thank you Apple geniuses.
Revo has a version that doesn’t need to be installed, I run that version from a thumb
drive or a network drive if I can, I even have it on a CD.
Let’s hope the Pi-Hole folks add Cloud Router IP addresses and the anti-virus
companies add the executables to their products.
great sir beneficial article thanks for sharing