More than a million domain names — including many registered by Fortune 100 firms and brand protection companies — are vulnerable to takeover by cybercriminals thanks to authentication weaknesses at a number of large web hosting providers and domain registrars, new research finds.
Image: Shutterstock.
Your Web browser knows how to find a site like example.com thanks to the global Domain Name System (DNS), which serves as a kind of phone book for the Internet by translating human-friendly website names (example.com) into numeric Internet addresses.
When someone registers a domain name, the registrar will typically provide two sets of DNS records that the customer then needs to assign to their domain. Those records are crucial because they allow Web browsers to find the Internet address of the hosting provider that is serving that domain.
But potential problems can arise when a domain’s DNS records are “lame,” meaning the authoritative name server does not have enough information about the domain and can’t resolve queries to find it. A domain can become lame in a variety of ways, such as when it is not assigned an Internet address, or because the name servers in the domain’s authoritative record are misconfigured or missing.
The reason lame domains are problematic is that a number of Web hosting and DNS providers allow users to claim control over a domain without accessing the true owner’s account at their DNS provider or registrar.
If this threat sounds familiar, that’s because it is hardly new. Back in 2019, KrebsOnSecurity wrote about thieves employing this method to seize control over thousands of domains registered at GoDaddy, and using those to send bomb threats and sextortion emails (GoDaddy says they fixed that weakness in their systems not long after that 2019 story).
In the 2019 campaign, the spammers created accounts on GoDaddy and were able to take over vulnerable domains simply by registering a free account at GoDaddy and being assigned the same DNS servers as the hijacked domain.
Three years before that, the same pervasive weakness was described in a blog post by security researcher Matthew Bryant, who showed how one could commandeer at least 120,000 domains via DNS weaknesses at some of the world’s largest hosting providers.
Incredibly, new research jointly released today by security experts at Infoblox and Eclypsium finds this same authentication weakness is still present at a number of large hosting and DNS providers.
“It’s easy to exploit, very hard to detect, and it’s entirely preventable,” said Dave Mitchell, principal threat researcher at Infoblox. “Free services make it easier [to exploit] at scale. And the bulk of these are at a handful of DNS providers.”
SITTING DUCKS
Infoblox’s report found there are multiple cybercriminal groups abusing these stolen domains as a globally dispersed “traffic distribution system,” which can be used to mask the true source or destination of web traffic and to funnel Web users to malicious or phishous websites.
Commandeering domains this way also can allow thieves to impersonate trusted brands and abuse their positive or at least neutral reputation when sending email from those domains, as we saw in 2019 with the GoDaddy attacks.
“Hijacked domains have been used directly in phishing attacks and scams, as well as large spam systems,” reads the Infoblox report, which refers to lame domains as “Sitting Ducks.” “There is evidence that some domains were used for Cobalt Strike and other malware command and control (C2). Other attacks have used hijacked domains in targeted phishing attacks by creating lookalike subdomains. A few actors have stockpiled hijacked domains for an unknown purpose.”
Eclypsium researchers estimate there are currently about one million Sitting Duck domains, and that at least 30,000 of them have been hijacked for malicious use since 2019.
“As of the time of writing, numerous DNS providers enable this through weak or nonexistent verification of domain ownership for a given account,” Eclypsium wrote.
The security firms said they found a number of compromised Sitting Duck domains were originally registered by brand protection companies that specialize in defensive domain registrations (reserving look-alike domains for top brands before those names can be grabbed by scammers) and combating trademark infringement.
For example, Infoblox found cybercriminal groups using a Sitting Duck domain called clickermediacorp[.]com, which was a CBS Interactive Inc. domain initially registered in 2009 at GoDaddy. However, in 2010 the DNS was updated to DNSMadeEasy.com servers, and in 2012 the domain was transferred to MarkMonitor.
Another hijacked Sitting Duck domain — anti-phishing[.]org — was registered in 2003 by the Anti-Phishing Working Group (APWG), a cybersecurity not-for-profit organization that closely tracks phishing attacks.
In many cases, the researchers discovered Sitting Duck domains that appear to have been configured to auto-renew at the registrar, but the authoritative DNS or hosting services were not renewed.
The researchers say Sitting Duck domains all possess three attributes that makes them vulnerable to takeover:
1) the domain uses or delegates authoritative DNS services to a different provider than the domain registrar;
2) the authoritative name server(s) for the domain does not have information about the Internet address the domain should point to;
3) the authoritative DNS provider is “exploitable,” i.e. an attacker can claim the domain at the provider and set up DNS records without access to the valid domain owner’s account at the domain registrar.
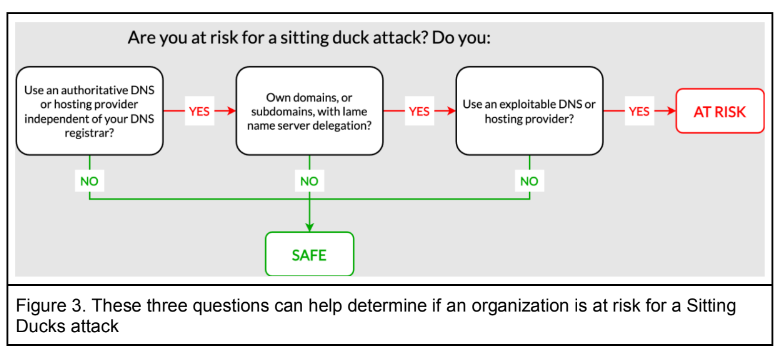
Image: Infoblox.
How does one know whether a DNS provider is exploitable? There is a frequently updated list published on GitHub called “Can I take over DNS,” which has been documenting exploitability by DNS provider over the past several years. The list includes examples for each of the named DNS providers.
In the case of the aforementioned Sitting Duck domain clickermediacorp[.]com, the domain appears to have been hijacked by scammers by claiming it at the web hosting firm DNSMadeEasy, which is owned by Digicert, one of the industry’s largest issuers of digital certificates (SSL/TLS certificates).
In an interview with KrebsOnSecurity, DNSMadeEasy founder and senior vice president Steve Job said the problem isn’t really his company’s to solve, noting that DNS providers who are also not domain registrars have no real way of validating whether a given customer legitimately owns the domain being claimed.
“We do shut down abusive accounts when we find them,” Job said. “But it’s my belief that the onus needs to be on the [domain registrants] themselves. If you’re going to buy something and point it somewhere you have no control over, we can’t prevent that.”
Infoblox, Eclypsium, and the DNS wiki listing at Github all say that web hosting giant Digital Ocean is among the vulnerable hosting firms. In response to questions, Digital Ocean said it was exploring options for mitigating such activity.
“The DigitalOcean DNS service is not authoritative, and we are not a domain registrar,” Digital Ocean wrote in an emailed response. “Where a domain owner has delegated authority to our DNS infrastructure with their registrar, and they have allowed their ownership of that DNS record in our infrastructure to lapse, that becomes a ‘lame delegation’ under this hijack model. We believe the root cause, ultimately, is poor management of domain name configuration by the owner, akin to leaving your keys in your unlocked car, but we acknowledge the opportunity to adjust our non-authoritative DNS service guardrails in an effort to help minimize the impact of a lapse in hygiene at the authoritative DNS level. We’re connected with the research teams to explore additional mitigation options.”
In a statement provided to KrebsOnSecurity, the hosting provider and registrar Hostinger said they were working to implement a solution to prevent lame duck attacks in the “upcoming weeks.”
“We are working on implementing an SOA-based domain verification system,” Hostinger wrote. “Custom nameservers with a Start of Authority (SOA) record will be used to verify whether the domain truly belongs to the customer. We aim to launch this user-friendly solution by the end of August. The final step is to deprecate preview domains, a functionality sometimes used by customers with malicious intents. Preview domains will be deprecated by the end of September. Legitimate users will be able to use randomly generated temporary subdomains instead.”
What did DNS providers that have struggled with this issue in the past do to address these authentication challenges? The security firms said that to claim a domain name, the best practice providers gave the account holder random name servers that required a change at the registrar before the domains could go live. They also found the best practice providers used various mechanisms to ensure that the newly assigned name server hosts did not match previous name server assignments.
[Side note: Infoblox observed that many of the hijacked domains were being hosted at Stark Industries Solutions, a sprawling hosting provider that appeared two weeks before Russia invaded Ukraine and has become the epicenter of countless cyberattacks against enemies of Russia].
Both Infoblox and Eclypsium said that without more cooperation and less finger-pointing by all stakeholders in the global DNS, attacks on sitting duck domains will continue to rise, with domain registrants and regular Internet users caught in the middle.
“Government organizations, regulators, and standards bodies should consider long-term solutions to vulnerabilities in the DNS management attack surface,” the Infoblox report concludes.



“phishous”
Looking to set up a photography site, not that computer literate, could I assume that going to “Can I take over DNS,” link and using one of the Not Vulnerable companies, I would be safe?
Robert – if you set up your domain at a DNS hosting provider and don’t remove the domain, you will not be vulnerable to this approach. It only becomes a problem if you set up your domain to be “routed” (what’s called “delegated”, in the DNS world) to a DNS hosting provider, but don’t set that domain up at the DNS hosting provider you’ve delegated to.
A DNS provider is not always synonymous with a registrar. In the case of clickermediacorp[.]com, the registrar is Markmonitor but the DNS/host is DNS Made Easy. Markmonitor is a corporate-only registrar who does provide authoritative hosting to its clients, but this domain is not using Markmonitor hosting.
The whole current setup was inspired by a network setup which served academics who all knew each other. The current system has not caught up with nobody knowing each other and massive numbers of players which must be automated, yet with some friction. It is seldom really necessary to make everything happen immediately.
It seems like a simple email to every contact including previous ones when a change is made would smoke out the bad actors.
I’m shocked, it seems a simple fix. For example, google passwords requires you to verify your the site owner by inserting simple html meta header code, why can’t the same be applied for verification of DNS?
So, how does that work when the reason you’re changing nameserver delegations is because your DNS is down?
How does it work when you’re registering a new domain using external nameservers and the website doesn’t exist yet?
How would it work on an email only or non-web domain?
How would it work of the domain is aliased to a third party app over which you have no control over the html meta headers?
A well-researched article! In terms of transparent actions that the non-registrar provider can facilitate: require customer/registrant proof before taking publicly-visible actions related to domain names. I like the CA/Browser Forum’s (CABF) certificate validation approach for a DNS TXT record containing a randomly-generated value. The flow in this case:
Customers authenticate into the management console of their chosen secondary DNS provider, enter the domain name (such as example[.]com) for which they want to provide DNS, and then receive instructions to add to their primary DNS zone file, including a random value.
Type: TXT
Name: _domain-challenge.example.com
Value: 123456789abcdef
Once this is in place, the secondary DNS provider validates that record before allowing them to create the zone file.
This is not about secondary DNS though, this is about lame delegation (lame duck, sitting duck, get it 🙂 ). There is no authoritative DNS configured and because of that there are no records you can look up.
Your suggestion would be fine (from a lookup perspective) for adding delegations to secondary DNS because then there is already a primary DNS provider, but it wouldn’t add anything in terms of security because the primary dns should be configured to not allow zone transfers to just anyone (using TSIG or an ACL).
DNS delegation, registration and authoritative and recursive DNS are all things that play together, but they’re not the same.
É a verdadeira caça aos tubarões. Cibersegurança não é lugar para economia!
This is neither news nor new. There have been prior panics around this “water is wet” type issue going back at least a decade.
(Search up “Floating Domains – Taking Over 20K DigitalOcean Domains via a Lax Domain Import System” – and others).
I also wrote about this on CircleID from the DNS operator’s perspective (“Nameserver Operators Need the Ability to “Disavow” Domains”) – after this same issue was used to DDoS attack another DNS provider by delegating a domain to their DNS servers without having setup an account there, and then doing a DNS reflection attack on that domain. That was *over* ten years ago.
The fact that people can delegate their own domains to somebody else’s nameservers without ever properly setting up a zone on those nameservers, or ever keeping track of where THEIR OWN DOMAINS point is 100% the responsibility of the domain owner – and to varying degrees a function of their REGISTRAR – who is the only entity that has any control over it.
It’s a weird flex for corporate registrars who purport to be “high touch” and exclusive, to simply shrug their shoulders and turn a blind eye to their own clients’ obviously broken and vulnerable nameserver delegations.
For our part this is specifically one of things we actively monitor and alert our clients about.
But the answer to that is simple. The hint is in the post by Samuel above. It’s “corporate”, so economics is the only thing that matters. We have the IT security environment in America that we do because of that, IMHO.
I had the exact opposite problem, the top level administrator of that particular registry is a single person, and only does work on it after hours, and only for an hour or so at a time. As the ISP holding the DNS closed, and there was no way to transfer out DNS, I lost control, and now it is a zombie, still in my name, but pointing to nowhere.
I recently experienced a related, but slightly different issue. Years ago someone owned a domain and DNS was setup through a popular provider. They let the domain expire. Later, I picked up the domain having no idea it had previously been in use. Coincidentally, I assigned nameservers at the registrar to the same DNS provider where it had been years before. When I went to create the DNS zone it wouldn’t let me as the previous owner of the domain still had the zone setup in their account.
At this point the previous owner could have caused all sorts of damage. The error creating the zone was ambiguous and it took the DNS provider a bit of time to figure out the odd scenario.
Perhaps a difficult scenario to exploit… register a bunch of domains, assign nameservers, let the domains expire and hope someone else picks up the domain and assigns the same nameservers.
This can all be avoided by not using a DNS provider, and instead running the resolvers yourself on hosts that you control.
Great article per usual. Funny how so many of these providers just pawn one problem off on another, and its just a circular blame game cause its to expensive to fix. Never knew this. thanks for the info Mr Krebs
“In the case of the aforementioned Sitting Duck domain clickermediacorp[.]com, the domain was originally registered by _______”
Missing info.
Thanks, fixed. It was just extraneous wordage.
Brian,
The truth that is the cure to all the lives and preventable suffering and death is life is most important in life is the most important truth in life.
You have been given instant enlightenment and are now baptized in the fire of the Holy Spirit, the very truth of the Importance of Life itself, and must either share the cure or judge yourself guilty of betraying all life on earth by withholding the distribution of the cure while simultaneously claiming to represent life’s truthful interests.
Please choose well Brian. There are no do-overs ever possible.
Thank you,
Why is this brainless babble allowed to pollute this discussion?
Very much agree, it doesn’t apply and just looks like it could have been a bot as it just doesnt make a single ounce of sense even for what had been said previously and what they said in the message was just religious word salad. Nothing against religious topics but this was baffling.
My thoughts exactly, this made absolutely no sense for the article. May be a bot may not be but either way it just doesn’t belong
Oops, thought my last comment didn’t post, apologies!
Will they fix it by the end of the month? Will Russia or Iran or whatever have us at complete war before then and completely exploit all of the stolen domains tontake down critical infrastructure?
If it is not getting fixed today then these people are not doing their job well enough and should get fired and released before 12am.
Hi Brian
Great reporting, as always. Article needs an edit.
“In the case of the aforementoned Sitting Duck domain clickermediacorp[.]com, the domain was originally registered
by , but it appears to have been hijacked by scammers by claiming it at the web hosting firm DNSMadeEasy, which is owned by Digicert,
Thanks, Mike. I think that extraneous wordage was fixed in an update earlier today. Probably you’re seeing a cached version of the story.
Compared to most commenters, I do not qualify as even being a novice, but for over 4 years I have had a problem with the GlassWire subscription for a firewall and network monitoring software package. All of their charges go through a London outfit called Cleverbridge which handles a large number of billing accounts for many software sellers, especially from Europe and to American subscribers via credit card.
My purpose was to detect hacking and phishing attacks, and I do not have a website.
The billing problem is that I keep getting billed twice a year, for at least the past 4 years, no matter how often I dispute the second charge, try to work with my bank (Wells Fargo) to dispute and prevent the second charge around six months after a renewal payment, and so forth.
Is GlassWire legitimate? How about Cleverbridge, which has changed owners at least twice over the last 4 years? Within that period Cleverbridge has established an American office, perhaps due to the pressure of software customers, which acta as billing agent and collector for the software companies.
There has been a repeating pattern of double charges over the years, with respect to two different Email accounts and two different credit card companies which I have used.
One thing to note is that on the Help page and elsewhere for GlassWire, there are a number of URL references to Cleverbridge under helpful icons like “Support” claiming to function something like : “support at Cleverbridge” that “resolve”, when the pointer icon is placed over the reference presented in simple English as something like “for help go to Support at Cleverbridge”, or “Support”, are actually used as support.cleverbridge.com rather than support@cleverbridge.com
In other words, they become an address to nowhere, like this:
https:suppport.cleverbridge.com/hc/en-us/requests/new#
With billing questions and complaints that magically disappear, has someone snuck into the Cleverbridge billing system or what? Please advise.
Puzzled