Federal authorities have arrested and indicted a 20-year-old U.S. Army soldier on suspicion of being Kiberphant0m, a cybercriminal who has been selling and leaking sensitive customer call records stolen earlier this year from AT&T and Verizon. As first reported by KrebsOnSecurity last month, the accused is a communications specialist who was recently stationed in South Korea.

One of several selfies on the Facebook page of Cameron Wagenius.
Cameron John Wagenius was arrested near the Army base in Fort Hood, Texas on Dec. 20, after being indicted on two criminal counts of unlawful transfer of confidential phone records.
The sparse, two-page indictment (PDF) doesn’t reference specific victims or hacking activity, nor does it include any personal details about the accused. But a conversation with Wagenius’ mother — Minnesota native Alicia Roen — filled in the gaps.
Roen said that prior to her son’s arrest he’d acknowledged being associated with Connor Riley Moucka, a.k.a. “Judische,” a prolific cybercriminal from Canada who was arrested in late October for stealing data from and extorting dozens of companies that stored data at the cloud service Snowflake.
In an interview with KrebsOnSecurity, Judische said he had no interest in selling the data he’d stolen from Snowflake customers and telecom providers, and that he preferred to outsource that to Kiberphant0m and others. Meanwhile, Kiberphant0m claimed in posts on Telegram that he was responsible for hacking into at least 15 telecommunications firms, including AT&T and Verizon.
On November 26, KrebsOnSecurity published a story that followed a trail of clues left behind by Kiberphantom indicating he was a U.S. Army soldier stationed in South Korea.
Ms. Roen said Cameron worked on radio signals and network communications at an Army base in South Korea for the past two years, returning to the United States periodically. She said Cameron was always good with computers, but that she had no idea he might have been involved in criminal hacking.
“I never was aware he was into hacking,” Roen said. “It was definitely a shock to me when we found this stuff out.”
Ms. Roen said Cameron joined the Army as soon as he was of age, following in his older brother’s footsteps.
“He and his brother when they were like 6 and 7 years old would ask for MREs from other countries,” she recalled, referring to military-issued “meals ready to eat” food rations. “They both always wanted to be in the Army. I’m not sure where things went wrong.”
Immediately after news broke of Moucka’s arrest, Kiberphant0m posted on the hacker community BreachForums what they claimed were the AT&T call logs for President-elect Donald J. Trump and for Vice President Kamala Harris.
“In the event you do not reach out to us @ATNT all presidential government call logs will be leaked,” Kiberphant0m threatened, signing their post with multiple “#FREEWAIFU” tags. “You don’t think we don’t have plans in the event of an arrest? Think again.”
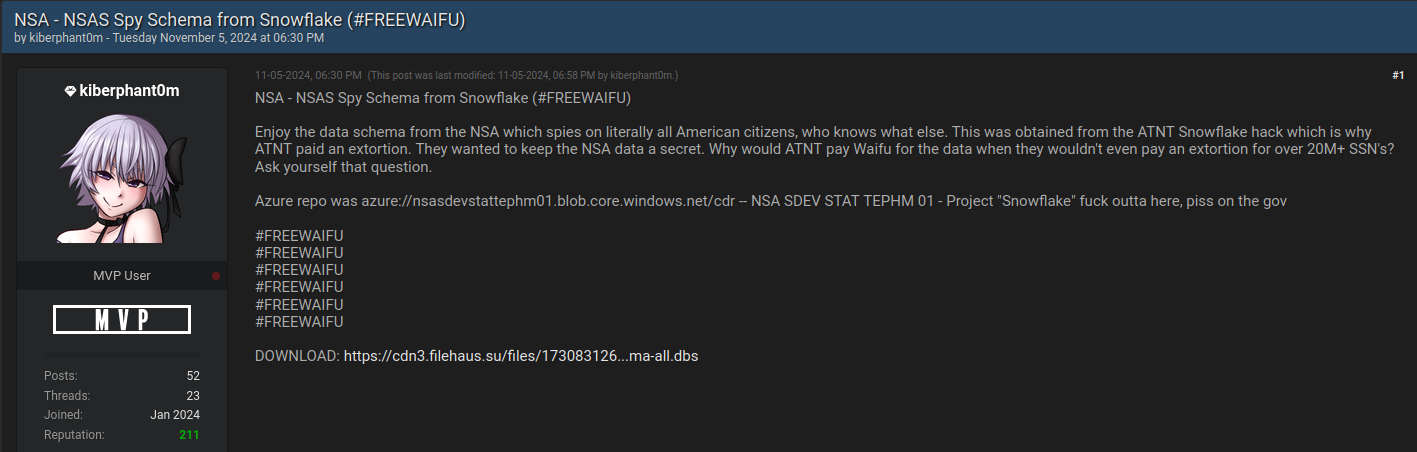
Kiberphant0m posting what he claimed was a “data schema” stolen from the NSA via AT&T.
On that same day, Kiberphant0m posted what they claimed was the “data schema” from the U.S. National Security Agency.
On Nov. 5, Kiberphant0m offered call logs stolen from Verizon’s push-to-talk (PTT) customers — mainly U.S. government agencies and emergency first responders. On Nov. 9, Kiberphant0m posted a sales thread on BreachForums offering a “SIM-swapping” service targeting Verizon PTT customers. In a SIM-swap, fraudsters use credentials that are phished or stolen from mobile phone company employees to divert a target’s phone calls and text messages to a device they control.
The profile photo on Wagenius’ Facebook page was deleted within hours of my Nov. 26 story identifying Kiberphant0m as a likely U.S. Army soldier. Still, many of his original profile photos remain, including several that show Wagenius in uniform while holding various Army-issued weapons.
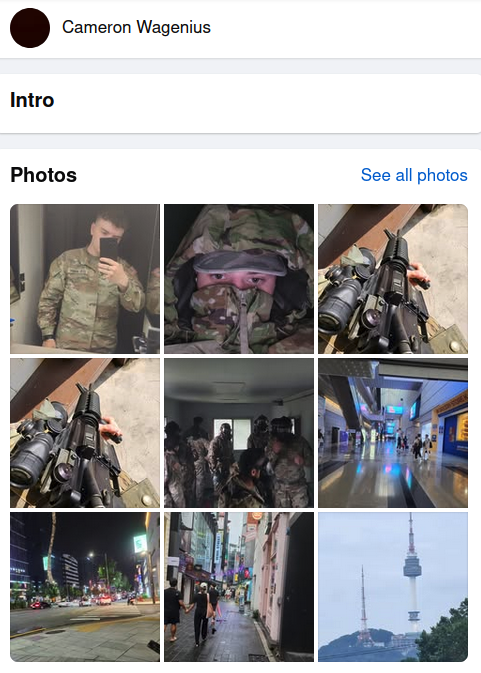
Several profile photos visible on the Facebook page of Cameron Wagenius.
November’s story on Kiberphant0m cited his own Telegram messages saying he maintained a large botnet that was used for distributed denial-of-service (DDoS) attacks to knock websites, users and networks offline. In 2023, Kiberphant0m sold remote access credentials for a major U.S. defense contractor.
Allison Nixon, chief research officer at the New York-based cybersecurity firm Unit 221B, helped track down Kiberphant0m’s real life identity. Nixon was among several security researchers who faced harassment and specific threats of violence from Judische and his associates.
“Anonymously extorting the President and VP as a member of the military is a bad idea, but it’s an even worse idea to harass people who specialize in de-anonymizing cybercriminals,” Nixon told KrebsOnSecurity. She said the investigation into Kiberphant0m shows that law enforcement is getting better and faster at going after cybercriminals — especially those who are actually living in the United States.
“Between when we, and an anonymous colleague, found his opsec mistake on November 10th to his last Telegram activity on December 6, law enforcement set the speed record for the fastest turnaround time for an American federal cyber case that I have witnessed in my career,” she said.
Nixon asked to share a message for all the other Kiberphant0ms out there who think they can’t be found and arrested.
“I know that young people involved in cybercrime will read these articles,” Nixon said. “You need to stop doing stupid shit and get a lawyer. Law enforcement wants to put all of you in prison for a long time.”
The indictment against Wagenius was filed in Texas, but the case has been transferred to the U.S. District Court for the Western District of Washington in Seattle.




Nice job Brian. Thank you on behalf of all Americans.
FWIW, the DEI crowd renamed Fort Hood to be Fort Cavazos.
Uniform Code of Military Justice
§915. Art. 115. Communicating threats
(a) Communicating Threats Generally.-Any person subject to this chapter who wrongfully communicates a threat to injure the person, property, or reputation of another shall be punished as a court-martial may direct.
Has nothing to do with DEI.
“Cavazos was the first Hispanic American to earn the rank of four-star general in the U.S. Army. He served as the commander of Fort Hood and III Corps from 1980 to 1982. He also served in the Korean War and Vietnam.”
Are saying that naming a base after a Vietnam vet is worse than naming it after a Confederate general?
Nothing wrong with a Confederate general.
plenty wrong with treason and mutiny. On top of that, they lost the war 😉
Exactly! Gone are the day we honor traitors! Despite Trumpostinking who has threatened to change the names again! But he is only there for 4 years! We’ll change them back!
Hi – the confederates were democrats.
Hi – have you ever read a history book?
You are spreading negative History due to your own ignorance, I guess.
He’s not entirely wrong. The Southern Democrats became the modern Republican party. Early Democrats were racist. The parties more or less switched places on key issues, not all but many. By playing this out of context without explanation he’s created grief for others. His objective is complete thus whether or not you continue to respond, which of course he would prefer you to.
You’re so brainwashed. History is written by the victors. If the Confederacy had won, they’d have written the history books claiming the other side was treason, and you’d be here like a clacking duck repeating the mantra, because you’re a good little duck, quack, quack.
Stupid is as stupid does, mailkel should recognize its opinion means nothing.
Thank you. Sedition and reason are in-American
Stupid is as stupid does, hick should recognize its opinion means nothing.
> Nothing wrong with a Confederate general.
Besides them being traitors and fighting for the right to keep slaves?
Silly comment
“I like winners.” – Huge Loser
WRONG. But thanks for playing the democracy game.
Impressed to see previous article validated.
several comments here regarding John Bell Hood and the Civil War and the reason for naming bases after some Confederate generals shows the dismal state of American education. Read a book about the war and the reasons for it. It wasnt about slavery.
Susan, perhaps you should follow your own advice and read some of the history of that period, including the source documents (by Confederate leadership) that clearly confirms that the Civil War and the attempt to secede from the Union was entirely driven by the desire to preserve the Southern institution of chattel slavery.
No matter how many times you people screech that it was about ” States Rats”, that lie is proven false by the documented statements of Confederate leadership.
Read the declarations of secession, which all give the preservation of slavery as the primary reason for secession. The fight over slavery was not “just” about slavery but also about the preservation of the corrupting influence of the wealth of the enslavers.
Is “American education” an oxymoron?
The modern state of affairs is that both sides claim their own set of facts.
How can you educate without agreeing on base concepts of epistemology?
Logic is a literal fallacy. Go vice signal back in your think tank with the rest of the brasshat cronies and clout chasing gov’t cucks.
Oh, logic is the problem? Got it. Sure Elon.
Haha! “… the first Hispanic…” Your response actually admits it was the DEI-crowd that renamed Ft. Hood.
so it is DEI driven the base was already named and youre crying about it what a clown joe
I thought they renamed it because Fort Hood was getting so many scandals that they needed to rebrand
Fort Hood has been renamed some time ago to Fort Cavazos.
slaves that the jews brought here on their jew owned slave ships then blamed on whites
Wow, what a stupid lie. You can read Eli Faber’s book about the slave trade, but jews played almost no role. From 1715-1765, 3,986 slaves arrived in New York City. Only 32 arrived on ships owned by jews and 345 arrived on ships that were part-owned by a jew.
Wow. Was this guy that dumb? Anyone residing in a Western country and doing this shady stuff is a walking perp. It’s just the matter of time before he gets caught. And blackmailing the president on top of that, while serving in the military is the next level dumb.
When will they learn? You need to move to Russia or to North Korea to get away with all that.
His mother being an open book speaks for itself lel
TIL LEL
I am his mother and I am not an open book, I was asked general questions about my sons age and if he was a solider! That is all I said and Krebs already had this information. I never knew my son was involved in any of this or involved with others until I read Krebs 1st article following my sons arrest, which was all new news to me! Do you really think a child would ever tell his parents he was involved in criminal activity?
your son was a no a hacker, just someone who claimed responsibility for the exploits of others and spread malware coded by others. there is nothing special other than the fact that he befriended someone bad and instead of doing good, he did bad. i’m sure you didn’t know he was a traitor to his country, but would you have really reported any of it if you did?
This woman has done nothing wrong but is now going through hell. Stop being a jerk.
OTOH, she’s the mother of a scam artist. Of course family members of prolific infamous criminal types get “some guff” from the outspoken opinions of our online society, as whether or not personally responsible they are still related to the party. Jerks are going to be jerks, it’s inevitable. However the OP asks one question that I think is valid : If she knew “something” about his exploits would she have turned him into the FBI knowing he’d probably end up in prison for decades? That’s a fair ball. Some would, some would not. We’ll have to take her at her word that she knew nothing, and though I personally believe her and agree people shouldn’t be jerks, society is going to do what society always does, all the time. There are no consequences for being a jerk online anonymously. Paradoxically there are (*rhetorical, one hopes) “consequences” for admitting you are related to a criminal and de-anonymizing yourself online. It takes a pretty thick skin to have an opinion or make an public admission online tied to your real-life personae. I respect her speaking up and setting the record straight as she sees it despite that.
This woman has done nothing wrong but is now going through hell. Stop being a jerk.
You might wanna loosen the straps on that gimp suit, or hurry up and bust before your brain’s remaining blood vessels do. Obviously Dunce Cap Dan couldn’t land a paper airplane on a mile-wide attack surface, let alone captain his own ‘bate team.
I wonder – what value do you add to this discussion, or any discussion? It seems like you’re very upset about something completely unrelated. Good luck with that.
Alicia, Ignore these idiots. They would argue whether water is actually wet. This crap reminds me why I left social media many years ago – unproductive idiots with too much time on their hands arguing about anything.
Nice detrace from kyber
This incident underscores the need for robust internal security measures to prevent insider threats. At GoldShield Cyber, we specialize in protecting businesses from both external and internal cybersecurity risks.
While robust internal security measures are indeed important for preventing insider threats, it’s essential to recognize that a comprehensive cybersecurity strategy goes beyond just focusing on insider risks. A disproportionate emphasis on internal threats might divert resources from addressing equally critical external vulnerabilities, such as sophisticated phishing attacks, ransomware, and supply chain compromises.
– Dritan
At very frequent intervals we read of a big company – here AT&T and Verizon – which should have enough money and common sense to staff a competent cyber-defense department being cyber-ransacked by hackers. This drum-roll of corporate cyber-bungling goes on and on. Is there no hope of change ?
No, no hope of change. They don’t care about their customers. When major corporations have a breach, what happens to them? Nothing.
Apparently you’ve never had to work with AT&T support services.
Please explain.
It’s not that simple. I’ve been in IT security R&D since the days of the Morris Worm, and in fact a great deal *has* changed. A couple of anecdotes from the mid-1990s: I was installing software at a major military IT center, and the sysadmins revealed that the machines were all on the public Internet, no firewalls, no security beyond classic UNIX mechanisms, manual and ad hoc monitoring. But they assured me that was fine, because those machines didn’t have A records in public DNS. (Note nmap was released in 1997.) And then there was the major financial institution with UNIX servers, again exposed on the Internet, where the root password was the company’s name lightly l33t-speak transformed. At most organizations, things are substantially better than they were 30 years ago, or even 10 years ago.
On the other hand, it’s certainly true that 1) major corporations keep falling to the same damn attacks; 2) we have all sorts of new attack-surface elements; 3) defenders (IT incident response teams) are under-resourced, overloaded, and generally not given sufficient authority; and 4) losses and penalties are treated as costs of business and these organizations face no major adverse consequences. Unless and until the economics change, that last point will dominate the results. Frankly, I don’t think things will get sufficiently better until there are strong regulatory consequences for failure to institute adequate security measures, including “piercing the corporate veil” and holding executives and board members to account.
@ Michael W,
Your comments from “OTH” forward make my point.
I’m NOT an IT guy(hence my name), but I’m going by what I read here and on Bruce Schneier’s page(and elsewhere) from people who say they are IT folks and make the same points you do perhaps especially #4. Thanks for your time.
None of this is remotely a result of technical incompetence. It’s too easy to convince people that “regulation = bad, deregulation = good” is valid without exception. Every large company hires freshly educated people who have the right personal contacts for their most important management positions, at the same time more appropriate and competent choices may be already exist in the company, but they’ll never be promoted because it would be more difficult to replace them. When the freshly educated people make poor choices (which the more experienced person would recognize as trouble), the price is paid by the boots on the ground and the people who they directly serve. Ethical, qualified people end up with the choice to do their best to do the right thing as long as the can, or go elsewhere. They talk big about agility but incompetent people in important positions feel the threat from their subordinates who are more qualified, so they continue to talk the talk and fail upwards. Even if the CIO is competent and ethical, as long as the CEO and/or shareholders think they know better, the CIO doesn’t stand a chance from day one until they day they are pushed out or voluntarily leave. Bottom line – where it’s easier to reward incompetence than it is to do the right thing, failure is the most likely possible outcome, and that can only be changed from the top.
There’s nothing about comprehensive cybersecurity that provides instant gratification, and that runs directly opposite from the standard operation of a for-profit company. Why would we possibly expect any other outcome?
LOL… “they’ll never be promoted because it would be more difficult to replace them” and owners and upper manage have no idea, or don’t care, or don’t have time to figure IT sec out.
1. too difficult to replace
2. too difficult to understand
3. too lazy to secure their own jobs
4. don’t care just want things fixed
Add all four together and what do you get.. TTTAAAAA DAAAAA …. horrRRAAAYYY “CLUster FOOKer!!!”
WELOME to corp AMERICA!
Just remember young whipper snappers.. it’s what you learn in the process to help you live onto to the next day.
YOYO… 100% no joke.
TIL LEL
the punishment for treason is death
Only in wartime, but yeah.
It’s obvious that “kiberphantom” had a James-bond-ease visions for himself. When I was a teenager decades ago, I had same grandiose hacking ambitions. He clearly was an amateur and a young idiot. I don’t condone hacking anymore but if you spend a lot of time talking game, you’re eventually going to get caught due to your ego.
he was 20 lol so still a teenager basically
Have fun at Ft. Leavenworth!
Yep. Nothing like a DD and a one-way trip to Leavenworth.
That’s not going to eff you for life. /s
I wonder what Leavenworth’s new name will be.
As someone who once walked the line as a black hat and an insider threat, let me put it this way: this guy is beyond fucked. He’s not destined to become anyone’s “hero,” and won’t be getting much so-called “fan mail” through the grim reality of prison life. His ambition was his undoing—it seems apparent that he craved recognition, validation from his peers, and the kind of notoriety that leaves a mark. But in his quest to make a name for himself, he let his ego take the wheel. That fatal misstep stripped him of the anonymity that once protected him. He probably thinks he’s got a bargaining chip or a get-out-of-jail-free card. But the feds are just going to take whatever he thinks he has, turn around, and lock his ass up. Then he will be yesterday’s news.
I called it! On your previous post I said the military bragging of his was an opsec mistake and that the claims about it being a joke were an attempt to cover it up. People didn’t believe me. Remember the hacking deadly sins. Pride is one of them and these loser’s inability to stop bragging is frequently their downfall.
Last name more like Wadummy
This is the comment I was looking for, nicely done
Of course there is money behind the matter or did he want to take the risk for nothing?
How much did verison & att pay Kiberphant0m to release data so it could be sold to others impending the release?
And yet they can’t seem to find the car warranty, the your son needs bail, or the IRS gift card scammers….
The scambaiter community on YouTube has been lobbying Congress to redirect LE away from investigating them.
Hope it was worth it!
And don’t pick up the soap in the shower, whatever they tell you
Just occurred to me: is that photo backwards? The logo is flipped, his top opens like a woman’s, but the US flag is the right way around. Que?
It’s a photo of a mirror (which is why you can see the camera in the photo). As for the flag, it’s because it’s displayed “backwards” on military uniforms when the patch is on the right shoulder, so it is flying correctly (think of how it would drape if they were marching forwards).
Dummies didn’t know that Telegram does not use end-to-end encryption by default for all messages. Instead, it relies on server-client encryption for its standard chats. This means that while messages are encrypted between your device and Telegram’s servers, Telegram still has the ability to decrypt and read them. This approach is fundamentally different from the more secure end-to-end encryption used by other messaging apps like Signal and WhatsApp, where even the service provider cannot read the messages.
The only thing end-to-end encrypted only between two parties is the Telegram direct secret chat and VoIP voice/video chat. But that likely changed since the CEO of Telegram was arrested when he landed in France and was detained. They were going to charge him with all the crimes being allowed on Telegram. All of a sudden, Telegram started cooperating. I also wouldn’t fully trust WhatsApp. But Signal, that looks legit and open source and has been reviewed many times over by experts. Their encryption is top notch.
They were extremely careless with their OpsSec considering the evidence, sounds like a case of grandiose narcissism. I AM INVINCIBLE! ~ Boris Grishenko (GoldenEye 1995)
These cyberpunks (I refuse to call them hackers) are now facing serious hard time with additional charges likely to be filed in court.Wagenius, since he’s active duty will likely end up in the United States Disciplinary Barracks (USDB), the military maximun-security penal facility on Fort Leavenworth about 4 miles from FCI Leavenworth civilian prison.
Don’t read too much into why a sociopath does things. They are 2% of the population everywhere
I refuse to have a battle of wits with an unarmed person. From reading the comments here I see a whole lot of unarmed people.
Mostly armless.
kiberphant0m was a good guy at heart and doesn’t deserve the treason charges hes abt to get hit with. Please kill yourself #HeilHitler
Hey look everyone it’s a real life smooth brain in action. Why don’t you go back to watching My Little Pony and leave the conversation here to the grown-ups. #DariusLuvsPinkyPie
We need to do a better job in having corporation security teams protecting our information from any possible threat.