Many successful phishing attacks result in a financial loss or malware infection. But falling for some phishing scams, like those currently targeting Russians searching online for organizations that are fighting the Kremlin war machine, can cost you your freedom or your life.

The real website of the Ukrainian paramilitary group “Freedom of Russia” legion. The text has been machine-translated from Russian.
Researchers at the security firm Silent Push mapped a network of several dozen phishing domains that spoof the recruitment websites of Ukrainian paramilitary groups, as well as Ukrainian government intelligence sites.
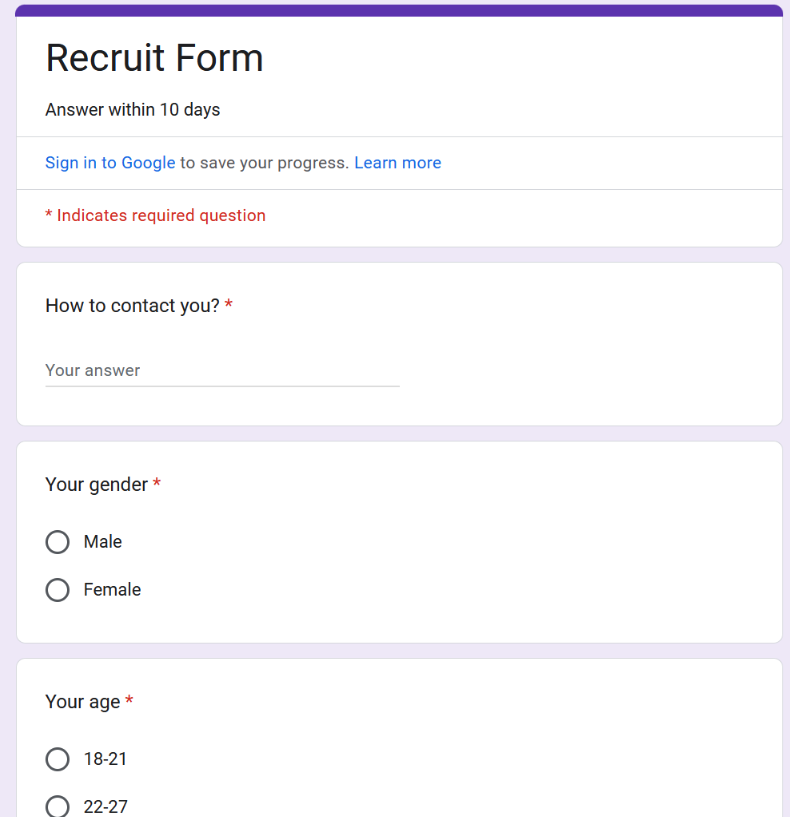
The website legiohliberty[.]army features a carbon copy of the homepage for the Freedom of Russia Legion (a.k.a. “Free Russia Legion”), a three-year-old Ukraine-based paramilitary unit made up of Russian citizens who oppose Vladimir Putin and his invasion of Ukraine.
The phony version of that website copies the legitimate site — legionliberty[.]army — providing an interactive Google Form where interested applicants can share their contact and personal details. The form asks visitors to provide their name, gender, age, email address and/or Telegram handle, country, citizenship, experience in the armed forces; political views; motivations for joining; and any bad habits.
“Participation in such anti-war actions is considered illegal in the Russian Federation, and participating citizens are regularly charged and arrested,” Silent Push wrote in a report released today. “All observed campaigns had similar traits and shared a common objective: collecting personal information from site-visiting victims. Our team believes it is likely that this campaign is the work of either Russian Intelligence Services or a threat actor with similarly aligned motives.”
Silent Push’s Zach Edwards said the fake Legion Liberty site shared multiple connections with rusvolcorps[.]net. That domain mimics the recruitment page for a Ukrainian far-right paramilitary group called the Russian Volunteer Corps (rusvolcorps[.]com), and uses a similar Google Forms page to collect information from would-be members.
Other domains Silent Push connected to the phishing scheme include: ciagov[.]icu, which mirrors the content on the official website of the U.S. Central Intelligence Agency; and hochuzhitlife[.]com, which spoofs the Ministry of Defense of Ukraine & General Directorate of Intelligence (whose actual domain is hochuzhit[.]com).
According to Edwards, there are no signs that these phishing sites are being advertised via email. Rather, it appears those responsible are promoting them by manipulating the search engine results shown when someone searches for one of these anti-Putin organizations.
In August 2024, security researcher Artem Tamoian posted on Twitter/X about how he received startlingly different results when he searched for “Freedom of Russia legion” in Russia’s largest domestic search engine Yandex versus Google.com. The top result returned by Google was the legion’s actual website, while the first result on Yandex was a phishing page targeting the group.
“I think at least some of them are surely promoted via search,” Tamoian said of the phishing domains. “My first thread on that accuses Yandex, but apart from Yandex those websites are consistently ranked above legitimate in DuckDuckGo and Bing. Initially, I didn’t realize the scale of it. They keep appearing to this day.”
Tamoian, a native Russian who left the country in 2019, is the founder of the cyber investigation platform malfors.com. He recently discovered two other sites impersonating the Ukrainian paramilitary groups — legionliberty[.]world and rusvolcorps[.]ru — and reported both to Cloudflare. When Cloudflare responded by blocking the sites with a phishing warning, the real Internet address of these sites was exposed as belonging to a known “bulletproof hosting” network called Stark Industries Solutions Ltd.
Stark Industries Solutions appeared two weeks before Russia invaded Ukraine in February 2022, materializing out of nowhere with hundreds of thousands of Internet addresses in its stable — many of them originally assigned to Russian government organizations. In May 2024, KrebsOnSecurity published a deep dive on Stark, which has repeatedly been used to host infrastructure for distributed denial-of-service (DDoS) attacks, phishing, malware and disinformation campaigns from Russian intelligence agencies and pro-Kremlin hacker groups.
In March 2023, Russia’s Supreme Court designated the Freedom of Russia legion as a terrorist organization, meaning that Russians caught communicating with the group could face between 10 and 20 years in prison.
Tamoian said those searching online for information about these paramilitary groups have become easy prey for Russian security services.
“I started looking into those phishing websites, because I kept stumbling upon news that someone gets arrested for trying to join [the] Ukrainian Army or for trying to help them,” Tamoian told KrebsOnSecurity. “I have also seen reports [of] FSB contacting people impersonating Ukrainian officers, as well as using fake Telegram bots, so I thought fake websites might be an option as well.”
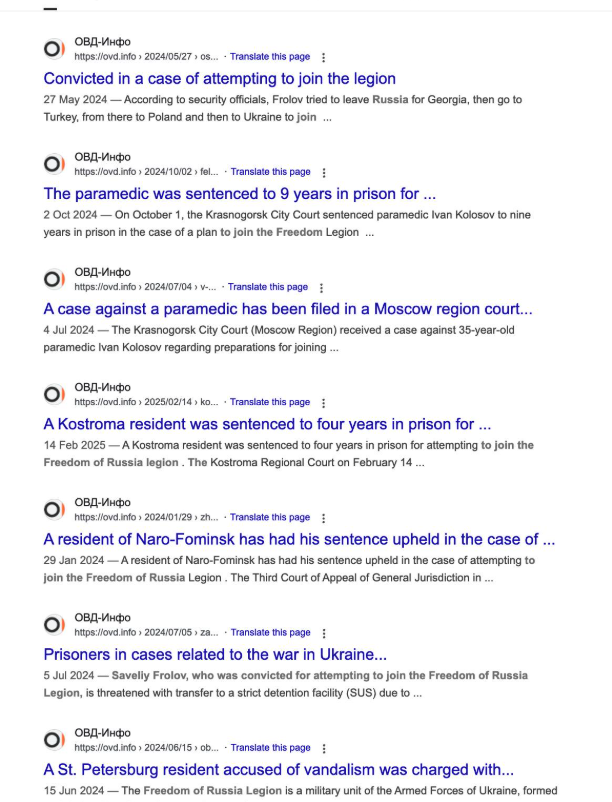
Search results showing news articles about people in Russia being sentenced to lengthy prison terms for attempting to aid Ukrainian paramilitary groups.
Tamoian said reports surface regularly in Russia about people being arrested for trying carry out an action requested by a “Ukrainian recruiter,” with the courts unfailingly imposing harsh sentences regardless of the defendant’s age.
“This keeps happening regularly, but usually there are no details about how exactly the person gets caught,” he said. “All cases related to state treason [and] terrorism are classified, so there are barely any details.”
Tamoian said while he has no direct evidence linking any of the reported arrests and convictions to these phishing sites, he is certain the sites are part of a larger campaign by the Russian government.
“Considering that they keep them alive and keep spawning more, I assume it might be an efficient thing,” he said. “They are on top of DuckDuckGo and Yandex, so it unfortunately works.”
Further reading: Silent Push report, Russian Intelligence Targeting its Citizens and Informants.




In the article “Getting Phished puts you in mortal danger” there’s a quote at the very end “they are on top of DuckDuckGo and Yandex, so it unfortunately works”. Does this mean the DDgo is not as secure as it claims?
Steve Dirkx
Dallas
Duckduckgo is just a filtered semi-distributed front-end to Bing (essentially), so it just means Bing (along with everyone else) isn’t flagging them as fake, and that whatever SEO they’re using is effective. Nothing to do with the security model of DDG.
I’d more lean on browser-specific security plugins that are updated and verify malicious sites ‘actively’ as their sole job, rather than Goog or DDG or anyone else being well-combed for (Russian, for this example, or other national) new/concatenated trojan sites. DDG may be safer that Goog on average but that doesn’t make it “secure” in the empirical sense of the word. They secure you from “some things”, like all security products. I’d call that claim ‘ok’ in the scheme of advertised claims FWIW, there are worse stretches. (I use DDG, sometimes Goog, Bing sucks, Yandex GFY, etc, I do not blindly click search results, and I don’t join the national army of an adversary at war with my own current country over the internet, whether relying on search result ranking or not. The local Russian search engine may be the precisely wrong tool for that job, but I digress, security is hard and people are not always as hard.)
‘browser-specific security plugins’
I have been using NoScript for a while now and can highly recommend it for anyone who wants more granular control over the permissions you give websites when you visit them. Yes, it breaks websites and makes them unviewable, but that is the whole point. It is a learning curve at first, until you train it to trust certain domains and not others. I couldn’t do without it now that it is setup for sites I visit regularly. Try The Daily Mail versus BBC versus Krebs On Security websites for instance. There is world of difference between the three in terms of backend tracking and undesirable autoscripts; I will let you guess which one is the cleanest. 😉
Absolutely Noscript + competent adblocker at a minimum. WebRTC blocking not a bad idea either. Anti-mal companies put out plugins to intercept known-bad URLs and whatnot, eset, malwarebytes, bitdefender, all the names. It definitely slows down page transitions noticeably, but that’s the choice in a trade-off. The few # of times I’ve tripped a popup in pointing at a ‘risky’ site, I’ve been glad to have it rather than a drive by download attempt, etc.
The DuckDuckGo screenshot shows results for the legitimate site: legionliberty[.]army (rather than legiohliberty.army). But the caption says it is a phishing domain. Am I missing something?
How long before activists turn the tables and use the sites to send swatting attacks against pro-Kremlin supporters?
How long before something similar starts here? Or am I too late asking?
It’s not too late. If South Korea can turn back a coup, so can the US of A. It will just take a critical mass of stupid and hopefully we reach that before too many more people get hurt.
Click here for more information. Or just post Name/DOB/address and your last 4 and someone will contact you.
> reported both to Cloudflare. When Cloudflare responded by blocking the sites with a phishing warning
Better response than I ever got when I bothered to report phishing sites to Cloudflare. All they did is respond that they aren’t hosting the site and would forward my complaint (presumably with all my info I had submitted sort of doxxing me) to the phishing site. They didn’t take down anything. I soon quit reporting.
https://hackread.com/twitter-x-of-2-8-billion-data-leak-an-insider-job/