China-based purveyors of SMS phishing kits are enjoying remarkable success converting phished payment card data into mobile wallets from Apple and Google. Until recently, the so-called “Smishing Triad” mainly impersonated toll road operators and shipping companies. But experts say these groups are now directly targeting customers of international financial institutions, while dramatically expanding their cybercrime infrastructure and support staff.

An image of an iPhone device farm shared on Telegram by one of the Smishing Triad members. Image: Prodaft.
If you own a mobile device, the chances are excellent that at some point in the past two years you’ve received at least one instant message that warns of a delinquent toll road fee, or a wayward package from the U.S. Postal Service (USPS). Those who click the promoted link are brought to a website that spoofs the USPS or a local toll road operator and asks for payment card information.
The site will then complain that the visitor’s bank needs to “verify” the transaction by sending a one-time code via SMS. In reality, the bank is sending that code to the mobile number on file for their customer because the fraudsters have just attempted to enroll that victim’s card details into a mobile wallet.
If the visitor supplies that one-time code, their payment card is then added to a new mobile wallet on an Apple or Google device that is physically controlled by the phishers. The phishing gangs typically load multiple stolen cards to digital wallets on a single Apple or Android device, and then sell those phones in bulk to scammers who use them for fraudulent e-commerce and tap-to-pay transactions.
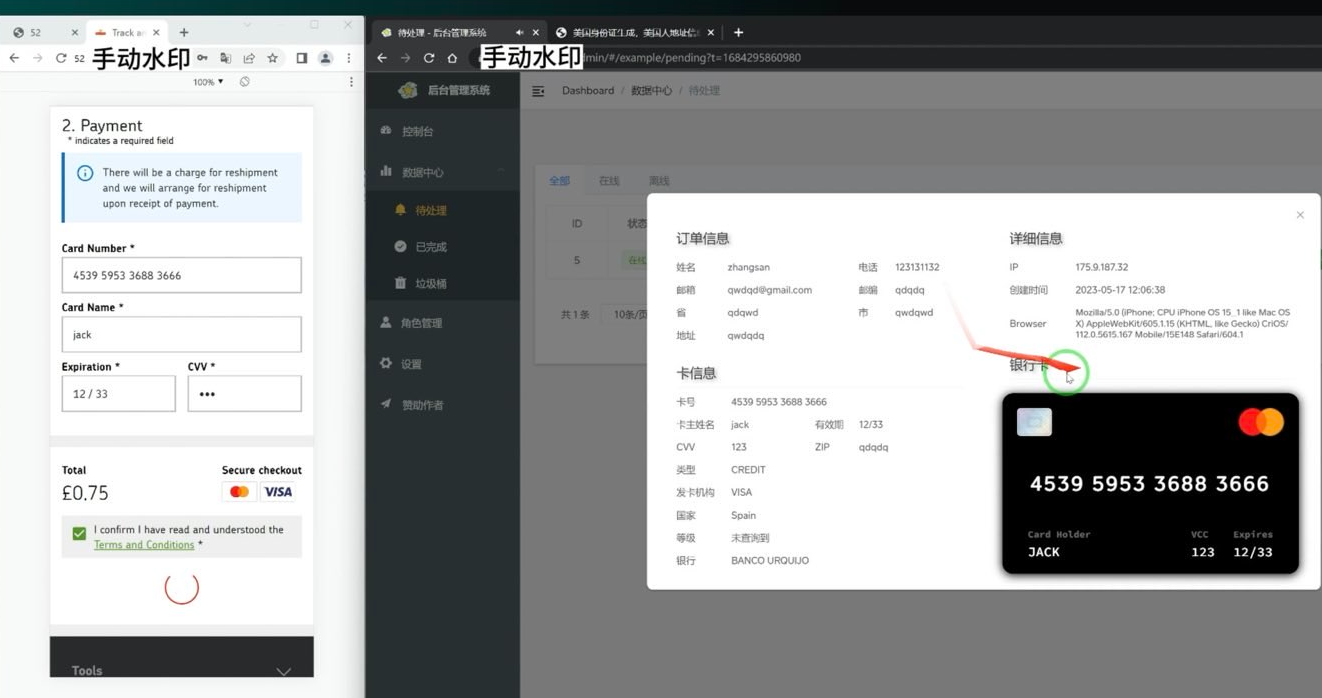
A screenshot of the administrative panel for a smishing kit. On the left is the (test) data entered at the phishing site. On the right we can see the phishing kit has superimposed the supplied card number onto an image of a payment card. When the phishing kit scans that created card image into Apple or Google Pay, it triggers the victim’s bank to send a one-time code. Image: Ford Merrill.
The moniker “Smishing Triad” comes from Resecurity, which was among the first to report in August 2023 on the emergence of three distinct mobile phishing groups based in China that appeared to share some infrastructure and innovative phishing techniques. But it is a bit of a misnomer because the phishing lures blasted out by these groups are not SMS or text messages in the conventional sense.
Rather, they are sent via iMessage to Apple device users, and via RCS on Google Android devices. Thus, the missives bypass the mobile phone networks entirely and enjoy near 100 percent delivery rate (at least until Apple and Google suspend the spammy accounts).
In a report published on March 24, the Swiss threat intelligence firm Prodaft detailed the rapid pace of innovation coming from the Smishing Triad, which it characterizes as a loosely federated group of Chinese phishing-as-a-service operators with names like Darcula, Lighthouse, and the Xinxin Group.
Prodaft said they’re seeing a significant shift in the underground economy, particularly among Chinese-speaking threat actors who have historically operated in the shadows compared to their Russian-speaking counterparts.
“Chinese-speaking actors are introducing innovative and cost-effective systems, enabling them to target larger user bases with sophisticated services,” Prodaft wrote. “Their approach marks a new era in underground business practices, emphasizing scalability and efficiency in cybercriminal operations.”
A new report from researchers at the security firm SilentPush finds the Smishing Triad members have expanded into selling mobile phishing kits targeting customers of global financial institutions like CitiGroup, MasterCard, PayPal, Stripe, and Visa, as well as banks in Canada, Latin America, Australia and the broader Asia-Pacific region.

Phishing lures from the Smishing Triad spoofing PayPal. Image: SilentPush.
SilentPush found the Smishing Triad now spoofs recognizable brands in a variety of industry verticals across at least 121 countries and a vast number of industries, including the postal, logistics, telecommunications, transportation, finance, retail and public sectors.
According to SilentPush, the domains used by the Smishing Triad are rotated frequently, with approximately 25,000 phishing domains active during any 8-day period and a majority of them sitting at two Chinese hosting companies: Tencent (AS132203) and Alibaba (AS45102).
“With nearly two-thirds of all countries in the world targeted by [the] Smishing Triad, it’s safe to say they are essentially targeting every country with modern infrastructure outside of Iran, North Korea, and Russia,” SilentPush wrote. “Our team has observed some potential targeting in Russia (such as domains that mentioned their country codes), but nothing definitive enough to indicate Russia is a persistent target. Interestingly, even though these are Chinese threat actors, we have seen instances of targeting aimed at Macau and Hong Kong, both special administrative regions of China.”
SilentPush’s Zach Edwards said his team found a vulnerability that exposed data from one of the Smishing Triad’s phishing pages, which revealed the number of visits each site received each day across thousands of phishing domains that were active at the time. Based on that data, SilentPush estimates those phishing pages received well more than a million visits within a 20-day time span.
The report notes the Smishing Triad boasts it has “300+ front desk staff worldwide” involved in one of their more popular phishing kits — Lighthouse — staff that is mainly used to support various aspects of the group’s fraud and cash-out schemes.
The Smishing Triad members maintain their own Chinese-language sales channels on Telegram, which frequently offer videos and photos of their staff hard at work. Some of those images include massive walls of phones used to send phishing messages, with human operators seated directly in front of them ready to receive any time-sensitive one-time codes.
As noted in February’s story How Phished Data Turns Into Apple and Google Wallets, one of those cash-out schemes involves an Android app called Z-NFC, which can relay a valid NFC transaction from one of these compromised digital wallets to anywhere in the world. For a $500 month subscription, the customer can wave their phone at any payment terminal that accepts Apple or Google pay, and the app will relay an NFC transaction over the Internet from a stolen wallet on a phone in China.
Chinese nationals were recently busted trying to use these NFC apps to buy high-end electronics in Singapore. And in the United States, authorities in California and Tennessee arrested Chinese nationals accused of using NFC apps to fraudulently purchase gift cards from retailers.
The Prodaft researchers said they were able to find a previously undocumented backend management panel for Lucid, a smishing-as-a-service operation tied to the XinXin Group. The panel included victim figures that suggest the smishing campaigns maintain an average success rate of approximately five percent, with some domains receiving over 500 visits per week.
“In one observed instance, a single phishing website captured 30 credit card records from 550 victim interactions over a 7-day period,” Prodaft wrote.
Prodaft’s report details how the Smishing Triad has achieved such success in sending their spam messages. For example, one phishing vendor appears to send out messages using dozens of Android device emulators running in parallel on a single machine.
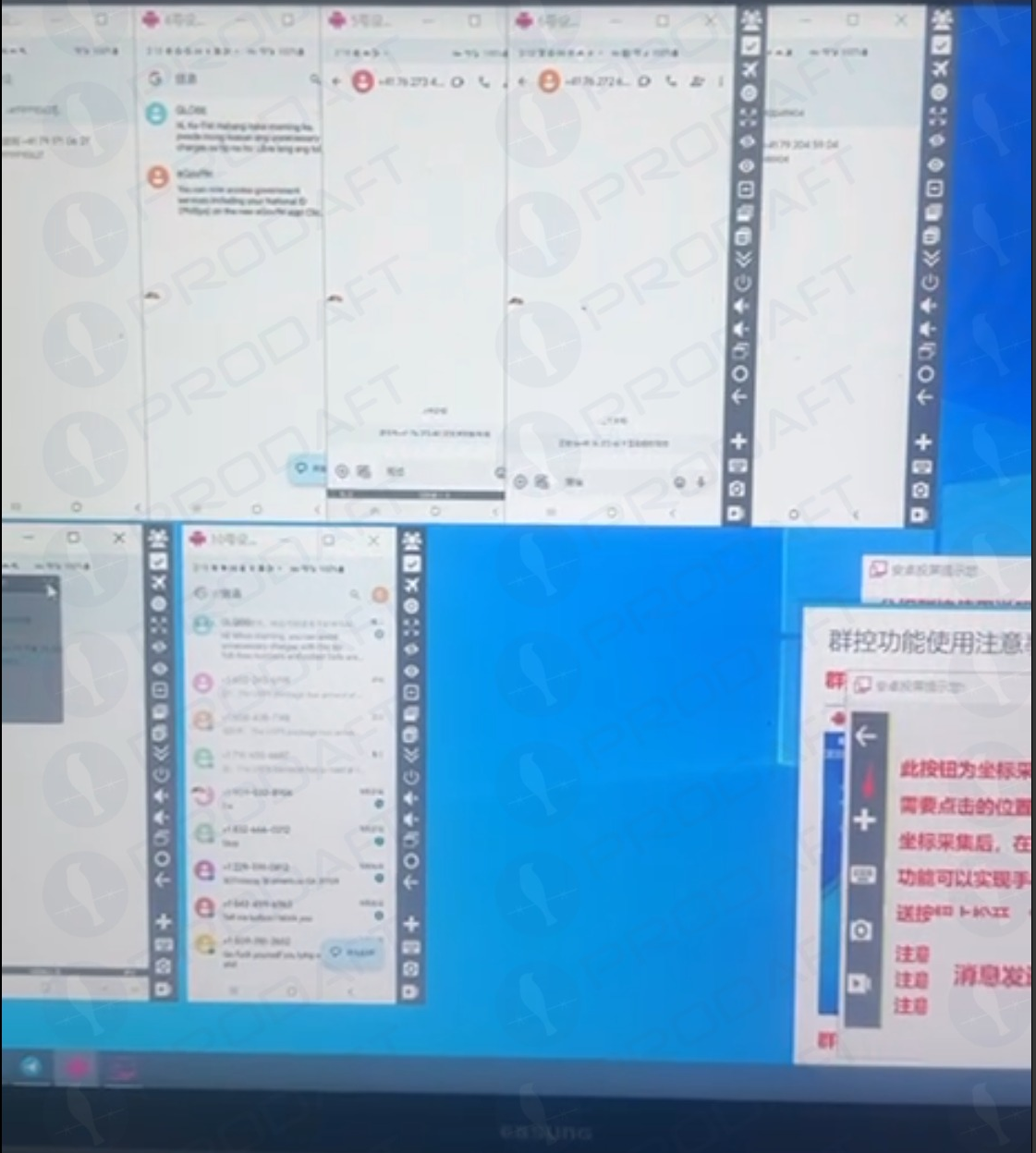
Phishers using multiple virtualized Android devices to orchestrate and distribute RCS-based scam campaigns. Image: Prodaft.
According to Prodaft, the threat actors first acquire phone numbers through various means including data breaches, open-source intelligence, or purchased lists from underground markets. They then exploit technical gaps in sender ID validation within both messaging platforms.
“For iMessage, this involves creating temporary Apple IDs with impersonated display names, while RCS exploitation leverages carrier implementation inconsistencies in sender verification,” Prodaft wrote. “Message delivery occurs through automated platforms using VoIP numbers or compromised credentials, often deployed in precisely timed multi-wave campaigns to maximize effectiveness.
In addition, the phishing links embedded in these messages use time-limited single-use URLs that expire or redirect based on device fingerprinting to evade security analysis, they found.
“The economics strongly favor the attackers, as neither RCS nor iMessage messages incur per-message costs like traditional SMS, enabling high-volume campaigns at minimal operational expense,” Prodaft continued. “The overlap in templates, target pools, and tactics among these platforms underscores a unified threat landscape, with Chinese-speaking actors driving innovation in the underground economy. Their ability to scale operations globally and evasion techniques pose significant challenges to cybersecurity defenses.”
Ford Merrill works in security research at SecAlliance, a CSIS Security Group company. Merrill said he’s observed at least one video of a Windows binary that wraps a Chrome executable and can be used to load in target phone numbers and blast messages via RCS, iMessage, Amazon, Instagram, Facebook, and WhatsApp.
“The evidence we’ve observed suggests the ability for a single device to send approximately 100 messages per second,” Merrill said. “We also believe that there is capability to source country specific SIM cards in volume that allow them to register different online accounts that require validation with specific country codes, and even make those SIM cards available to the physical devices long-term so that services that rely on checks of the validity of the phone number or SIM card presence on a mobile network are thwarted.”
Experts say this fast-growing wave of card fraud persists because far too many financial institutions still default to sending one-time codes via SMS for validating card enrollment in mobile wallets from Apple or Google. KrebsOnSecurity interviewed multiple security executives at non-U.S. financial institutions who spoke on condition of anonymity because they were not authorized to speak to the press. Those banks have since done away with SMS-based one-time codes and are now requiring customers to log in to the bank’s mobile app before they can link their card to a digital wallet.




If I had to install an app, I wouldn’t use NFC payments, and then I’d be less secure than before. There had better be a better way to authenticate than SMS or installing some proprietary garbage app from a bank to hand all my data to the adtech industry. When that day comes, it’ll be back to good old fashioned CASH for me.
“Garbage app from a bank” > Garbage 1-shot SMS authentication, though.
If your bank doesn’t put out an app you find “suitable”, A: What’s unsuitable about it specifically, B: How do you personally know, and C: Why would you continue your relationship with the bank whose apps you don’t trust for #reasons?
If your bank doesn’t respect info privacy choices in their app chances are good they’re selling your info off the backend also, which again begs the question of why you would have a trust relationship with the bank you don’t trust.
*(Cash isn’t great for online transactions or large transactions. I mean why not diamonds or gold, lol… crude oil…)
You know I’ve been harping on about the banking/financial institutions lack of multi factor authentication for a long time now, but I’ll piggy back off your comment to reiterate it once again for newcomers.
If you are a US citizen and are curious what forms of multi factor authentication the banks in your country offer as a service, see the following link. (There are 52 other countries to choose from otherwise).
https://2fa.directory/us/#banking
I, like OP prefer not to use software authentication like a ‘banking app’, but rather the use of physical hardware like a Yubico YubiKey or Google Titan Key. The sad reality is of the 97 institutions in the link above, only 3 offer this option, and THAT is a disgrace. This goes to show much they really *care* about their customers.
The problem with FIDO2 keys is that they do not securely display what you actually sign, so there is still the risk of approving something the user didn´t really want to approve.
You are right. The limitation that FIDO2 keys don’t display what’s being signed is a legitimate concern, especially for high-assurance environments like banking where transaction signing matters. In contrast, some European banks using smart card readers or dedicated apps do offer contextual approval with transaction details shown to the user; which adds a crucial layer of transparency and prevents silent approvals of malicious actions.
That said, it’s important to put FIDO2’s design into context: it was never built for transaction authorisation per se, but for phishing-resistant authentication. And in that role, it excels. Because FIDO2 ties authentication to the domain (origin binding), an attacker can’t trick the user into authenticating on a lookalike phishing site — even if the user clicks the wrong link. The key simply won’t work unless the origin is cryptographically correct.
Would I love to see transaction-level signing supported more broadly? Absolutely. But today, most US banks don’t even authenticate securely, let alone authorise transactions securely. My frustration stems from how few of them even offer FIDO2/WebAuthn as an option — just 3 out of 97 per 2fa.directory. That’s the real disgrace.
SMS is barely MFA, and authenticator apps, while better, are still vulnerable to phishing and social engineering. Biometrics? Great for local device access, but meaningless if the device is compromised or rooted. And passkeys — while promising — are still finding their footing due to ecosystem fragmentation and vendor lock-in (e.g., iCloud vs. Google). Ideally, we’d see a layered approach: FIDO2 for authentication (phishing-resistant), Transaction-aware confirmations through trusted channels (e.g., app notifications that show full payment info),and secure hardware fallback options like a YubiKey or biometric device tied to attestation.
So yes, we’re focusing on slightly different pieces of the puzzle. You’re looking at what happens after auth (transaction integrity), and I’m highlighting the sad state of initial authentication options. But both need serious attention, especially in a time where phishing kits are evolving faster than the security controls most banks have currently put in place.
That is fair comment but what would you suggest otherwise? SMS is practically obsolete. Authenticator apps are better but still phishable. Biometrics rely on device security, which is a weak link if the device is compromised. And while Passkeys show promise they are immature and still hampered by eco system fragmentation and vendor lock-in e.g., iCloud vs. Google.
It’s also worth noting that one of FIDO2’s core strengths is phishing resistance via origin binding, that is, a key won’t authenticate unless the domain matches exactly. So even if a user is tricked into visiting a convincing phishing site, their key simply won’t respond. That’s a huge step up from SMS or authenticator apps, which are easily tricked and replayed. And that is what the vast majority of readers here need protection against.
Hardware keys are not perfect but when used in conjunction with other layers of security they offer greater defence against malicious actors than what is on offer from *most* mainstream US banking services today.
No I don’t have dementia – yet. Everyone may ignore this repetitive comment, as I thought my original was ‘moderated’, so I shortened it.
I’ve done worse.
Really it’s only 3 even now? Jeez.
I know that implementing other forms of MFA is a top priority of several financial institutions in my area, but none are big enough to have their own app developers. So they have to rely on the vendors like FiServ, FIS, and Jack Henry who only care about this quarter’s projections. Hell FiServ just a few years ago fired like half their employees, and I can only assume it was because they were responding to support tickets too quickly.
I am really picky about what apps I install on my cell phone. What aggravates me is that it won’t let me remove some apps that I am sure that I don’t need at all.
What is confusing is that from time to time I check the smart phone and find new game apps installed. There should be no game apps on my smart phone. I have never played a game app on the phone and am not about to start now. I have no idea how those apps are even installed.
@ A – Regarding the precious comment about using cash:
I am going to make a comment out of left field, which is not directly germane to
the topic of the story. But it may inform a bit about the landscape of regular humans
who also fear many things virtual, and desire to retain CASH as a medium of exchange.
The folks I am specifically thinking about are fundamentalist Christians who have a narrative
about the “end times” and think that the “globalists” are intentionally preparing to eliminate
“cash money”, as a method of control of “we the people”.
If a person thinks the End Times are imminent, and a symptom or indicator of that
would be if the government tried to institute
a universal version of cypto-currency in order to institute a “new global order”. Most
fundamentalist Christians have a high degree of distrust of all of our institutions and our tech,
and perhaps with a certain amount of reason. If you are looking for any allies in keeping cash
available as a payment option, there are many on the right that would agree.
Text confirmation codes in general, or coming from your bank, do seem like a flaky way to do things.
paint with a broad brush much? Cash is a great way to go as it saves the merchant the fees that payment processors charge. Not sure there’s a big overlap between believers of imminent end-times and people who use mainly cash for payments.
@BigP- yes, it is a broad brush, and not very well stated. I love cash for local things, for privacy, for saving local merchants from paying fees ( I had a gas station ), and the feeling that I get from having a cash option available to me. (buying used stuff from private sellers; furniture, tools, garden equipment, etc).
Also cash is good for making bail if you missed a child support payment or she did not tell the court you already paid it. By the same token you take a risk if you go to buy a used phone from a seller you have not verified. Criminals love cash too. ****
You cannot easily make travel/hotel reservations or send flowers for a funeral. In my clumsy post, I was just imagining if the guberment tried to institute a compulsory cryptocurrency system where everything could be tracked and controlled. (two major toll roads here do not accept cash or have any attendants, but photo your plate; if you do not have a fast toll account, they can take the money from any tax refund that is owed to you) btw-if you ever filled out the form for a fast-toll account, it neatly contains every salient fact of your life, all in one data base, that a hacker would love to have…just because I’m paranoid, does not mean “they” aren’t out to get me…?
Probably a larger overlap between people who have come to have a wariness of tech for privacy (or random glitchiness) reasons or just prefer to not worry about the possibilities of getting ripped off.
My payment processor is reliable but I remember years back having far more concerns.
(PS: I haven’t posted a comment here in a decade (not that I haven’t been able to at any given time) and likely won’t again for a while. Just stopping in. Looks like you’re still churning the articles out. Nice research.)
Just remember to turn off “Send Read Receipts” on iPhone and the equivalent on Android before opening any suspect iMessage/RCS message so that phisher/scammer doesn’t know they have reached a valid number and someone who reads their smishing messages.
SMS confirmation codes are a sad mistake.
“SMS confirmation codes are a sad mistake.” Yes. SS7 is quite old, and people fall for phishing easily.
of course the US Gubmint is powerless to protect its citizens from such attacks and there is no ‘both sides’
Interestingly I received this message today from an outlook domain account…
Apple Approval Notice
We have noticed that your Apple iCloud id was recently used at “APPLE STORE – CA” for $143.95, paid by Apple Pay Pre Authorization.
Also some suspicious sign in request and apple pay activation request detected.
That looks like suspicious to us. In order to maintain the security and privacy of your account we have placed those request on hold. Your Photos, Data, Bank
Information and Cards are at risk. If NOT you? talk to an Apple Representative.
Failing may lead to auto debit and charge will not be reversed. Call +18884048435 immediately to cancel this charge.
It also has a URL at the end…
Note the language of spam…”your id”, “your account”, “Your photos”, etc. It’s the same for every spam call/email/text, “your” language because they have no idea who is receiving their call/email/text.
@Matt ALWAYS CHECK THE “From” on your emails and you will see these do not come from any reputable source(s).
I told my bank that I wish they would use digital signatures to verify that they are the true source of their e-mails.
One thing that I have done is to set up separate e-mails for each bank and credit card company. The e-mails are rather convoluted and make little or no sense, but they are highly unlikely that anyone would ever accidentally send something to the e-mail by accident. They look more like a password than an e-mail address with something buried in the e-mail address to make it easy to identify which it is.
For example, I could use hgqib.a5asb.prairie.bank.hssel.2qck7@example.com for an e-mail address for use with Bank of the Prairie.
There is no need to make it easy to remember or to enter — you only have to enter it once when giving it to the bank and it is best to cut and paste it then. The bank stores it in their records and if they need to e-mail you, they will retrieve it from their records rather than entering it by hand. On the other hand, by checking the embedded text, it is immediately obvious whether which bank or credit card company it is used with.
In my case, I do filtering to tag my incoming e-mails. When I get an e-mail from the bank’s domains, it tags it with the banks name. If it is addressed to anything other than the special e-mail address, it also flags it with a “WARNING” tag.
If you get an e-mail from the bank that doesn’t use that address, then it is immediately highly suspicious. Unless the scammers manage to get the bank’s records, they would never run across that address elsewhere and any e-mail address they manage to harvest from anywhere else would never be your banking e-mail address.
SMS on the other hand is a cesspool of insecurity. Treat anything that arrives via SMS as being highly suspect
In summary, the phishing falls into one of these:
– “you owe a small debt, provide payment info”… (the missed toll scam)
– “you need to prepay for shipping, or something”…(the USPS or postal service shipping scam)
– “you need to approve this random payment”…(the credit card, PayPal, and banking scam)
– “you are eligible for service protection or rewards, verify your account”…(the credit card, PayPal, and banking scam)
Oh man, where to begin. First off, how come Apple can allow a single account to blast out more than a few messages per minute, let along 100 per second? Did any of those Apple geniuses think about limiting it? (I’m not touching Android. Their App Store is an unregulated dumpster fire.)
Then those SMS messsges for 2Fa. :facepalm: Pretty much every bank in the U.S. thinks that they “enhance” my security by sending out 2FA codes via SMS. Although requiring me to use their dumb apps is not a solution either. Did they hear about Google Authenticator or Authy?
It’s using the various different app platforms, not 100 SMS per second AFAIK. Point taken either way.
To expand, the Apple iOS hypervisor (userland) isn’t “aware” of messages being sent in all the various platform apps which are e2e encrypted. It knows you’re running n apps, it knows there’s a connection between the device and some server(s) linked to each app and it can probably see spikes in data transmission, but it can’t see what they’re ‘doing’ really, yet, *as far as the wider public is aware. This could change in some markets. The question is do we really want that, or can we live without it and combat scammers (and everything else) in some other way.
apnews.com/article/apple-iphone-britain-privacy-cybersecurity-encryption-5bc43477bee8cf32cbd81cd88a9463bd