A critical resource that cybersecurity professionals worldwide rely on to identify, mitigate and fix security vulnerabilities in software and hardware is in danger of breaking down. The federally funded, non-profit research and development organization MITRE warned today that its contract to maintain the Common Vulnerabilities and Exposures (CVE) program — which is traditionally funded each year by the Department of Homeland Security — expires on April 16.

A letter from MITRE vice president Yosry Barsoum, warning that the funding for the CVE program will expire on April 16, 2025.
Tens of thousands of security flaws in software are found and reported every year, and these vulnerabilities are eventually assigned their own unique CVE tracking number (e.g. CVE-2024-43573, which is a Microsoft Windows bug that Redmond patched last year).
There are hundreds of organizations — known as CVE Numbering Authorities (CNAs) — that are authorized by MITRE to bestow these CVE numbers on newly reported flaws. Many of these CNAs are country and government-specific, or tied to individual software vendors or vulnerability disclosure platforms (a.k.a. bug bounty programs).
Put simply, MITRE is a critical, widely-used resource for centralizing and standardizing information on software vulnerabilities. That means the pipeline of information it supplies is plugged into an array of cybersecurity tools and services that help organizations identify and patch security holes — ideally before malware or malcontents can wriggle through them.
“What the CVE lists really provide is a standardized way to describe the severity of that defect, and a centralized repository listing which versions of which products are defective and need to be updated,” said Matt Tait, chief operating officer of Corellium, a cybersecurity firm that sells phone-virtualization software for finding security flaws.
In a letter sent today to the CVE board, MITRE Vice President Yosry Barsoum warned that on April 16, 2025, “the current contracting pathway for MITRE to develop, operate and modernize CVE and several other related programs will expire.”
“If a break in service were to occur, we anticipate multiple impacts to CVE, including deterioration of national vulnerability databases and advisories, tool vendors, incident response operations, and all manner of critical infrastructure,” Barsoum wrote.
MITRE told KrebsOnSecurity the CVE website listing vulnerabilities will remain up after the funding expires, but that new CVEs won’t be added after April 16.
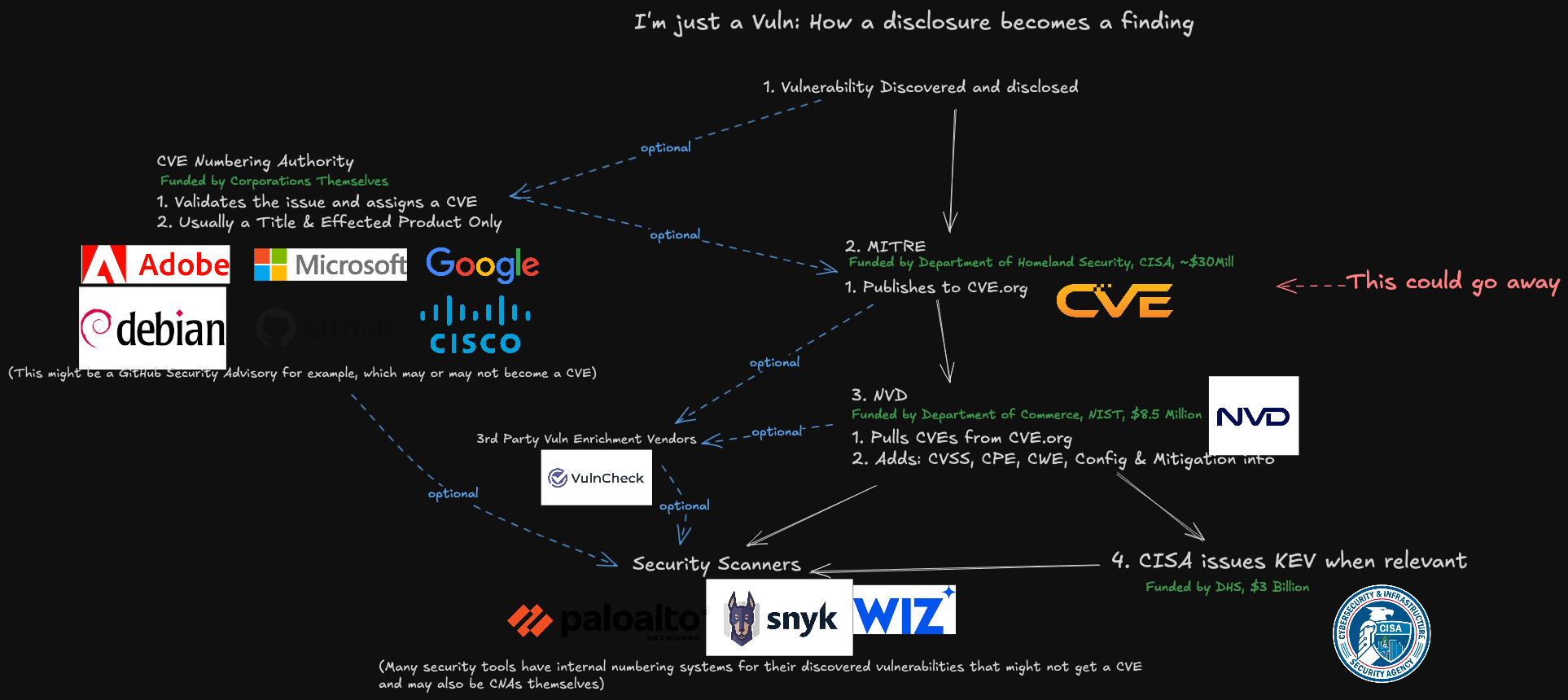
A representation of how a vulnerability becomes a CVE, and how that information is consumed. Image: James Berthoty, Latio Tech, via LinkedIn.
DHS officials did not immediately respond to a request for comment. The program is funded through DHS’s Cybersecurity & Infrastructure Security Agency (CISA), which is currently facing deep budget and staffing cuts by the Trump administration. The CVE contract available at USAspending.gov says the project was awarded approximately $40 million last year.
Former CISA Director Jen Easterly said the CVE program is a bit like the Dewey Decimal System, but for cybersecurity.
“It’s the global catalog that helps everyone—security teams, software vendors, researchers, governments—organize and talk about vulnerabilities using the same reference system,” Easterly said in a post on LinkedIn. “Without it, everyone is using a different catalog or no catalog at all, no one knows if they’re talking about the same problem, defenders waste precious time figuring out what’s wrong, and worst of all, threat actors take advantage of the confusion.”
John Hammond, principal security researcher at the managed security firm Huntress, told Reuters he swore out loud when he heard the news that CVE’s funding was in jeopardy, and that losing the CVE program would be like losing “the language and lingo we used to address problems in cybersecurity.”
“I really can’t help but think this is just going to hurt,” said Hammond, who posted a Youtube video to vent about the situation and alert others.
Several people close to the matter told KrebsOnSecurity this is not the first time the CVE program’s budget has been left in funding limbo until the last minute. Barsoum’s letter, which was apparently leaked, sounded a hopeful note, saying the government is making “considerable efforts to continue MITRE’s role in support of the program.”
Tait said that without the CVE program, risk managers inside companies would need to continuously monitor many other places for information about new vulnerabilities that may jeopardize the security of their IT networks. Meaning, it may become more common that software updates get mis-prioritized, with companies having hackable software deployed for longer than they otherwise would, he said.
“Hopefully they will resolve this, but otherwise the list will rapidly fall out of date and stop being useful,” he said.
Update, April 16, 11:00 a.m. ET: The CVE board today announced the creation of non-profit entity called The CVE Foundation that will continue the program’s work under a new, unspecified funding mechanism and organizational structure.
“Since its inception, the CVE Program has operated as a U.S. government-funded initiative, with oversight and management provided under contract,” the press release reads. “While this structure has supported the program’s growth, it has also raised longstanding concerns among members of the CVE Board about the sustainability and neutrality of a globally relied-upon resource being tied to a single government sponsor.”
The organization’s website, thecvefoundation.org, is less than a day old and currently hosts no content other than the press release heralding its creation. The announcement said the foundation would release more information about its structure and transition planning in the coming days.
Update, April 16, 4:26 p.m. ET: MITRE issued a statement today saying it “identified incremental funding to keep the programs operational. We appreciate the overwhelming support for these programs that have been expressed by the global cyber community, industry and government over the last 24 hours. The government continues to make considerable efforts to support MITRE’s role in the program and MITRE remains committed to CVE and CWE as global resources.”




this step good for internate or social media user,s
Does Big Balls know this? Hopefully it wasn’t his idea.
nextgov.com/cybersecurity/2025/04/user-russian-ip-address-tried-log-nlrb-systems-following-doge-access-whistleblower-says/404574/
Either one of them is rooted or they’re giving it away intentionally. I’d say both are equally likely.
Sweet baby Jesus. 80+ years of US soft power going down the drain in mere months.
Has anyone reached out to European institutions to fund and host this?
Not that I disagree, and this is a very rational question in a sea of panic (thank you!), but IMO it should be the corporations primarily responsible for funding this through and independent self-regulating body. Kind of like how FINRA oversees brokers/dealers, levies fines for non-compliance with rules, and recommends criminal investigation to the SEC when appropriate. Just replace FINRA with an organization like CIS (no exactly CIS, but like CIS) and the SEC with CISA\DHS\NIST.
“Yes! Let The Marketplace Decide!” (Reaganomics, 1980’s)
MEGA
I’ve kind of lost it. This is so absurd I’m laughing. Ah yes! No more cybersecurity for anybody! HAHAHAHA
It may be an idea to not use a single point of failure authority, but expend this to 3 authorities based in 3 different geolocation..
Hey, we need that money to fund weekend golf trips to Florida every weekend. That ain’t cheap.
In addition to https://vulnerability.circl.lu, we launched today https://gcve.eu which is a decentralized approach to vulnerability identification and numbering, designed to improve flexibility, scalability, and autonomy for participating entities. GCVE is compatible with the traditional CVE system, but adds increased flexibility, scalability, and autonomy for organizations involved in vulnerability management.
Vulnerability-Lookup (https://vulnerability.circl.lu) facilitates quick correlation of vulnerabilities from various sources, independent of vulnerability IDs, and streamlines the management of Coordinated Vulnerability Disclosure (CVD), and is the first software to fully support GCVE.
well in addition EU also just lunched: https://euvd.enisa.europa.eu/ – rest will be interesting to see how this moves forward… but for now; some helpful settings
To complete the circle: EUVD is querying vulnerability-lookup 😉
(https://euvd.enisa.europa.eu/faq)
Bravo! Chuffed to see the Europeans have come to the dance party.
The grandpa does know what MITRE is. “It’s all computer!”
Oh yes, “do not bring politics to security blog” group is silent here.
Glad to see EU picking up the slack there with https://gcve.eu
As a long time subscriber and reader, thank you for keeping the community well informed. This is insanity!!!
Whitehouse news release on May 16; “Under Trump’s leadership, the number of CVE’s has been reduced in the last month. The United States is now more secure than ever”.
/s
How much funding do they get? I can’t find a number anywhere just “the CVE program is minor and “won’t break the bank”.
Anyone have any idea how much it takes to run?
CSO Online is reporting that over $28 million in contracts with MITRE have been cancelled, which included funding for the CVE program. For the most accurate and up-to-date information regarding the CVE program’s funding, you’d have to consider submitting a FOIA request to DHS or consulting official government budget documents. But considering Leon’s ‘USG Gutting Program’ I don’t think you’ll have much luck there.
What happens when rank amateurs are put in charge.
So the US taxpayer is funding a program that every one benefits from, but aren’t contributing to? Here’s a crazy idea. How about getting “big tech” to part with some of their billions to help fund this?
Like that’s gonna happen. It’s Big Tech’s sugar daddy the Pestilent Orange Pox that is responsible for this clusterf*ck.
The US taxpayer is funding a program that helps the US taxpayer. All of this stuff benefits us.
It also benefits others, but so what?
Yes, this is what taxes are for.
Bingo.
OK let me get this straight…
So Big Tech that literally makes BILLIONS annually (and pays minimal in any tax to boot) is actually the source of all the vulnerabilities & bugs being found at my taxpaying expense…(that’s some great QC by the way) and for just what reason aren’t they paying for this critical work?!?!?
Sheesh, the money found in their employee lounges couches would cover the cost…
I wonder just how many of said vulnerabilities & bugs are specifically from Microsoft?
Seeings how they are so many that there is a Microsoft Patch Tuesday that’s been going on for years now…typically featuring 50-150 patches each…https://krebsonsecurity.com/?s=Microsoft+Patch+Tuesday
MITRE should launch a campaign at GoFundMe lest a lots of security companies or programs suffer. Hope God forgive this.
Update Apr. 16 at 08:20 EST: In an eleventh hour turnaround, the U.S. Cybersecurity and Infrastructure Security Agency said it had extended the contract with MITRE.
https://www.forbes.com/sites/kateoflahertyuk/2025/04/16/cve-program-funding-cut-what-it-means-and-what-to-do-next/
Sweet $DEITY people. Stop defaulting to everything being a US .gov problem.
This is exactly the kind of thing that should NOT be a US federally funded program. There’s a long, working, history of critical computer services in the private sector. Kicking this out into the decentralized world for its users to support and update will ultimately benefit everyone.
Respectfully disagree. The US government has funded this for 25 years. You can’t just quit funding suddenly and not expect fallout.
This is the problem with this administration is that they just randomly cut funding effective immediately. At least schedule some time so everyone can prepare.
“This is exactly the kind of thing that should NOT be a US federally funded program”
Okay, I assume you mean because you think the US government might hold back on CVE classifications for vulns they are actively using or hoping to use themselves for offensive attacks? That’s not entirely unreasonable to think about, but otherwise you’re saying a national vuln database/catalogue effort is not in the larger national interest entirely? That’s literally ‘the’ role of a Federal government – to provide security for the larger endeavor, including the private sector. Yes there is partnering with vendors and contracting and whatnot, but expecting each private sector market to look after and mind all of this individually in this evolving attack environment is like expecting elephants to herd themselves to safety over the Alps. ‘Someone’ needs to fund and maintain it for the general security welfare, not limit and sell access to it for private profit as the private sector _already does_ in every direction. Security is layers. Responsibility is concentric.
I don’t have an opinion on incentives behind the data itself. I’m only pointing out that humanity can, and should, do important things without government entanglements. Rockets are better without NASA. This system will be better with less US bureaucracy as well.
Based on the article updates, others have come to the same conclusion.
“humanity can, and should, do important things without government entanglements.”
Okay so feel free to have a comprehensive CVE database that you can demonstrate is as good as the one “the eebil gubmint” puts out, make it available to everyone for free (beer style) and maintain it indefinitely for the good of mankind. Solved.
Until you do that, however, people living under the eebil gubmints do benefit from having it even though it costs taxpayer money to do so – this is our system; taxation, representation, hopefully some useful action. Up until very recently this was seen by most as a good investment, albeit a small one.
Relying on the goodwill of mankind to keep our *.* secure sounds great though, so just wake me when you’ve gone and done that. We can take the $40 million and just blow it all on shoes.
“This system will be better with less US bureaucracy as well.” – How so? Be specific. How well do you know this system, and how exactly is UN bureaucracy impacting it in your estimation? If you’ve got things to point out, well, point them out rather than just implying all things government-touching are useless. *(It’s called Libertarianism and it’s often confused as a form of governance, where it’s actually an ideological opposite of that idea.)
^*US bureaucracy, not UN… (~all human systems have bureaucracy…)
“Rockets are better without NASA.”
If you like explosions, surely. Rocket companies wouldn’t exist in current form without NASA though.
You didn’t build that.
World War III is virtually underway imho. Our information security, privacy and ultimately our freedom and wealth are being taken away through vitual warfare and social engineering. Our legal system is like bringing a knife to a gun fight and we need to rise up with a new warplan. (on Signal lol)
Would love to know how much the Maintaining this actually costs. Right now I have seen $2million, $28million and $40million here and in different places. How much and what exactly does it cover. When was the last time it was competitively bid out?
It is a valuable resource but I am wondering if other things ae in the contract as well.
There is a link to the most recent contract from DHS/CISA. It shows the allocated amount as ~$40M.
https://www.usaspending.gov/award/CONT_AWD_70RCSJ24FR0000019_7001_70RSAT20D00000001_7001
My city gov spent more than that on traffic lights for 2 intersections. Not even complicated ones.
FYI, the link is slightly incorrect and therefore the dollar amount. Here is a link to the correct contract action:
https://www.usaspending.gov/award/CONT_AWD_70RCSJ24FR0000018_7001_70RSAT20D00000001_7001
The contract action is incorrect, it should be: https://www.usaspending.gov/award/CONT_AWD_70RCSJ24FR0000018_7001_70RSAT20D00000001_7001
The “thecvefoundation.org” domain was created 2025-04-15 23:41:47 UTC. For some reason, I can’t shake the burning feeling in my gut …
The domain “thecvefoundation.org” was created 2025-04-15 23:41:47 UTC. For some reason, I have a very sour feeling in my gut …
https://www.meritalk.com/articles/cisa-extends-cve-program-contract-at-11th-hour-averting-disruption/
The contract has been extended
https://www.meritalk.com/articles/cisa-extends-cve-program-contract-at-11th-hour-averting-disruption/
Here is another one for temporary email address – https://tempmails.in
P*ss off with your SPAM/SCAM would you, it is not wanted here.
https://www.reuters.com/world/us/us-agency-extends-support-last-minute-cyber-vulnerability-database-2025-04-16/
To the C-Suite Executives & Cybersecurity Professionals,
Since the Morris Worm incident in 1988, the responsibility for vulnerability enumeration has evolved from Carnegie Mellon University to MITRE, with the Common Vulnerabilities and Exposures (CVE) system becoming the global standard. However, persistent underfunding and shifting priorities have caused significant delays and backlogs in vulnerability processing. It may be time to consider transitioning the management of the CVE program to a dedicated non-profit organization focused on operational continuity and transparency—while allowing Federally Funded Research and Development Centers (FFRDCs) to focus on innovation and strategic research.
I agree that the current reprieve may provide a brief period when transitioning the CVE system to a dedicated non-profit organiztion with community funding may be a good idea. (Listenting, multi-billion-$ tech firms?) We should be aware that industry funding is not a panacea. It is subject to mergers and aquisitions as well as corporate priority shifts and atrophy. Private money is also, sadly, as vulnerable to ideological capture as federal grants. (Both the Linux and Mozilla foundations now actively expell voluntary contributors for having the ‘wrong’ political views.) Tech needs to be as vigilant about the neutrality of its institutions as it was during the birth of the internet. (Opinion of a dinosaur who remembers transitioning a regional IBM SNA network to TCP/IP)
“We should be aware that industry funding is not a panacea.” – Monsanto says hi.
“Private money is also, sadly, as vulnerable to ideological capture as federal grants.”
Ok but private money is private money, pretty different from Federal grants in almost all respects… I can think of…
“(Both the Linux and Mozilla foundations now actively expell voluntary contributors for having the ‘wrong’ political views.)” – And what exactly did they contribute, and how did those “wrong” political views manifest exactly? If we’re going to point to specific instances of something let’s actually point to specific cases. Linus may be a bit of a tyrant and Mozilla makes some odd choices to be sure, but I don’t think either organization seeks out Conservatives to kick out of their roles “for that” really… unless there’s some kind of chat meltdown/incident/controversy that brings it all to a head. (I’d be happy to hear any details that show me that I’m wrong, that those organizations actively target people of a certain political party for individual exile based on that alone.) I certainly welcome big-C conservative perspectives, but to me the issue is that what has supplanted and usurped that role from (true?) Conservatism in our politics is decidedly NOT Conservative nor even a self-validated political opinion, but Nihilism. Big-N Nihilism. The opposite of epistemology and debate, of knowledge, in favor of self-validation by fiat. Trumpism, to be blunt. Nihilism walking. Nothing is true and nothing matters unless he says it. That’s not a “political choice” really, at this point. You (can..) know it’s false rhetoric yourself, but you’ve just become convinced you can hide behind the word “politics” as if it makes all claims plausible. It doesn’t do that.
Just as Mozilla and Linus aren’t actively investigating people’s voting records to kick them out of the computer club. Or, say, advocating that people they don’t agree with politically be randomly accused of thought crimes, stripped of legal due process under our Constitution and their very citizenship and sent off to an undetermined 3rd world gulag indefinitely, for no other reason than literally voicing dissent. That’s not happening to you, is it.
So it’s important to keep comparisons apt, was my point.
This feels like the foundation of my patching program is about to go away. Help me understand how critical this is to tools like Tenable NESSUS and Microsoft Update and Defender ATP..
We simply keep yielding our soft power away.
Or perhaps is to have as many vulnerablilities out there (including in cyber but not only) so it is just easier to steel. You can’t follow all the news