In what experts are calling a novel legal outcome, the 22-year-old former administrator of the cybercrime community Breachforums will forfeit nearly $700,000 to settle a civil lawsuit from a health insurance company whose customer data was posted for sale on the forum in 2023. Conor Brian Fitzpatrick, a.k.a. “Pompompurin,” is slated for resentencing next month after pleading guilty to access device fraud and possession of child sexual abuse material (CSAM).
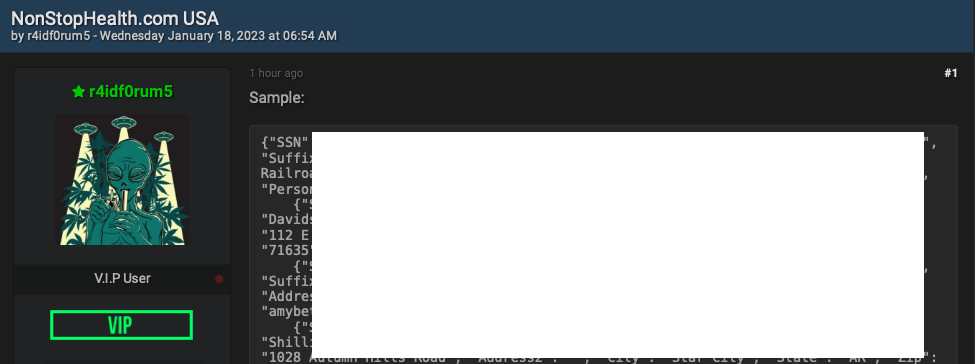
A redacted screenshot of the Breachforums sales thread. Image: Ke-la.com.
On January 18, 2023, denizens of Breachforums posted for sale tens of thousands of records — including Social Security numbers, dates of birth, addresses, and phone numbers — stolen from Nonstop Health, an insurance provider based in Concord, Calif.
Class-action attorneys sued Nonstop Health, which added Fitzpatrick as a third-party defendant to the civil litigation in November 2023, several months after he was arrested by the FBI and criminally charged with access device fraud and CSAM possession. In January 2025, Nonstop agreed to pay $1.5 million to settle the class action.
Jill Fertel is a former prosecutor who runs the cyber litigation practice at Cipriani & Werner, the law firm that represented Nonstop Health. Fertel told KrebsOnSecurity this is the first and only case where a cybercriminal or anyone related to the security incident was actually named in civil litigation.
“Civil plaintiffs are not at all likely to see money seized from threat actors involved in the incident to be made available to people impacted by the breach,” Fertel said. “The best we could do was make this money available to the class, but it’s still incumbent on the members of the class who are impacted to make that claim.”
Mark Rasch is a former federal prosecutor who now represents Unit 221B, a cybersecurity firm based in New York City. Rasch said he doesn’t doubt that the civil settlement involving Fitzpatrick’s criminal activity is a novel legal development.
“It is rare in these civil cases that you know the threat actor involved in the breach, and it’s also rare that you catch them with sufficient resources to be able to pay a claim,” Rasch said.
Despite admitting to possessing more than 600 CSAM images and personally operating Breachforums, Fitzpatrick was sentenced in January 2024 to time served and 20 years of supervised release. Federal prosecutors objected, arguing that his punishment failed to adequately reflect the seriousness of his crimes or serve as a deterrent.
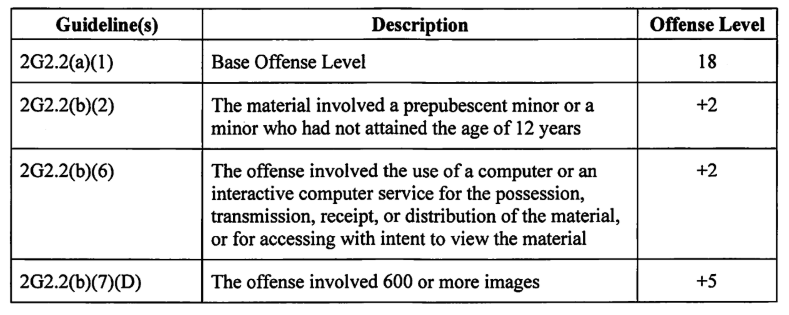
An excerpt from a pre-sentencing report for Fitzpatrick indicates he had more than 600 CSAM images on his devices.
Indeed, the same month he was sentenced Fitzpatrick was rearrested (PDF) for violating the terms of his release, which forbade him from using a computer that didn’t have court-required monitoring software installed.
Federal prosecutors said Fitzpatrick went on Discord following his guilty plea and professed innocence to the very crimes to which he’d pleaded guilty, stating that his plea deal was “so BS” and that he had “wanted to fight it.” The feds said Fitzpatrick also joked with his friends about selling data to foreign governments, exhorting one user to “become a foreign asset to china or russia,” and to “sell government secrets.”
In January 2025, a federal appeals court agreed with the government’s assessment, vacating Fitzpatrick’s sentence and ordering him to be resentenced on June 3, 2025.
Fitzpatrick launched BreachForums in March 2022 to replace RaidForums, a similarly popular crime forum that was infiltrated and shut down by the FBI the previous month. As administrator, his alter ego Pompompurin served as the middleman, personally reviewing all databases for sale on the forum and offering an escrow service to those interested in buying stolen data.

A yearbook photo of Fitzpatrick unearthed by the Yonkers Times.
The new site quickly attracted more than 300,000 users, and facilitated the sale of databases stolen from hundreds of hacking victims, including some of the largest consumer data breaches in recent history. In May 2024, a reincarnation of Breachforums was seized by the FBI and international partners. Still more relaunches of the forum occurred after that, with the most recent disruption last month.
As KrebsOnSecurity reported last year in The Dark Nexus Between Harm Groups and The Com, it is increasingly common for federal investigators to find CSAM material when searching devices seized from cybercriminal suspects. While the mere possession of CSAM is a serious federal crime, not all of those caught with CSAM are necessarily creators or distributors of it. Fertel said some cybercriminal communities have been known to require new entrants to share CSAM material as a way of proving that they are not a federal investigator.
“If you’re going to the darkest corners of Internet, that’s how you prove you’re not law enforcement,” Fertel said. “Law enforcement would never share that material. It would be criminal for me as a prosecutor, if I obtained and possessed those types of images.”
Further reading: The settlement between Fitzpatrick and Nonstop (PDF).




Hmmm … “novel legal outcome” is right.
I wonder how this news is being greeted at DOGE ?
Glad to hear that this little prick is being resentenced. He may be big boy topside in the breach world and on Telegram, but on the inside he’s currency. He’ll be walking wrong after one night in GenPop and every night thereafter.
>Fertel said some cybercriminal communities have been known to require new entrants to share CSAM material as a way of proving that they are not a federal investigator.
The opposite of testing suspected North Korean workers by badmouthing Kim Jong Un
I hope cybercriminals adopt this idea and get destroyed by the police
he should have applied for a job at DOGE in time, that way with a bit of luck he might just have gotten his record clean.
This case highlights the increasing sophistication of cybercriminal networks and the urgent need for organizations to proactively test their security infrastructure. One effective way to do that is through Breach & Attack Simulation (BAS), which mimics real-world cyberattacks to uncover vulnerabilities before threat actors exploit them.
At CyberNX, we’ve developed a Breach & Attack Simulation Cybersecurity Toolkit that helps businesses strengthen their defense posture by identifying and addressing gaps in their systems. It’s a practical resource for security teams looking to stay ahead of evolving threats through continuous testing and actionable insights.
You can explore the toolkit and download the full guide here:
Full URL is here :
http-sans-s://wwwww.Crickets.edu
This is a well-researched and eye-opening article. The legal outcome around the BreachForums case and the evolving tactics of cybercriminals are a strong reminder of how critical it is for organizations to stay one step ahead. Kudos to the author for shedding light on both the legal and technical implications involved.
In today’s threat landscape, it’s no longer enough to react after an attack—businesses need to continuously test their defenses. That’s why at CyberNX, we’ve created a Breach & Attack Simulation Cybersecurity Toolkit to help organizations simulate real-world cyberattacks and identify hidden vulnerabilities before they’re exploited.
This free guide offers practical insights and tools for IT teams, CISOs, and compliance officers to strengthen their cybersecurity framework.
“ChatGPT, generate me some meaningless marketing fluff I can spam into blog comments to promote my dodgy business”
“Fertel told KrebsOnSecurity this is the first and only case where a cybercriminal or anyone related to the security incident was actually named in civil litigation.”
Spit take, what?
And you would think they could agree on something other than CSAM to prove they’re not Feds…
if they wanted to.
You can all DROP dead.
May you all be cursed with a thirst you cannot quench and an itch you cannot scratch.
If raising PomPomPurin was your magnum opus, then maybe she should’ve patched the vulnerabilities at home before he started exploiting them online.
Take accountability for what you created. And I’m not talking about the talentless collages.
MaryAnn, you do know that this site is absolutely the last location on the planet that you should be airing your grievances, particularly if you were expecting any sort of empathy or support. In fact, all you have achieved, is to open the floodgates and you may find you will not appreciate the attention your are about to receive from this audience.
Let us be very clear, right hear, right now. Conor is NO victim. He has left a deluge of REAL victims in his wake and shown absolutely NO remorse. If you wish to come here and defend his actions, you WILL be treated with the utter contempt both of you deserve.
Do better.
Maybe he thinks he’s speaking to the cyber-goofs, not the forum readers? Unclear.
“Law enforcement would never share that material. It would be criminal for me as a prosecutor, if I obtained and possessed those types of images.”
Yeah, except prosecutors have absolute immunity, full discretion when it comes to seeking indictments, and a vested interest in allowing LE to operate how they wish. Qualified immunity covers civil liability. CSAM is also a broad enough appellation that creates the mismatched federalism issue where a state’s age of consent is frequently below the federal one, and as possession is a strict liability offense – no intent requirement needed, meaning that you don’t need to know that you have CSAM to be convicted of possessing it – a lot of these kids are capable of creating CSAM by taking selfies, but certainly almost none have the ability to definitively determine the age of anyone depicted on first glance if they are post-pubescent.
The first amended indictment mentioning CSAM was suspicious in its specificity as to the age of the victims depicted since to know the specific age, the material would be known and documented in an LE database and its veracity confirmed typically via a previous prosecution. While researchers are typically only allowed access to MD5 hashes – and defense is frequently told that the determination is a hash based match, because it’s trivial to obtain a jury verdict to convict, it’s essentially an always available backstop in computer crime cases (like how wire fraud is the catch-all for all financial crime cases). LE had to be warned off of using the Tanner scale by the creator of the scale itself in matching how doctors determine developmental stages during adolescence – doctors are less concerned about chronological age and more about the physiological age to begin with, after all, since any hard age limit is effectively arbitrary anyway. But of course, LE and prosecutors know that no competent defense attorney would risk taking such a charge to trial because of how easy it is to obtain a conviction, you pretty much have to be the producer of faux-CSAM to even challenge such a charge. But prosecutors would simply not press charges in those circumstances. In any case, the only people who really possess and can view CSAM in large quantities with little consequence ARE exactly LE and prosecutors. Saying that it’s illegal is a deliberate misdirection. We all know that LE plants evidence to bolster cases and prosecutors allow them to do so. Scandals involving planted evidence abound from the federal down to the municipal across the country. But even when defense knows the evidence is planted, since it requires a burden shift (as it becomes an affirmative defense) that doesn’t even clear the client of the crime necessarily, there’s no real way to fight the charge when brought, and will always result in a plea. Much like how the sex offender registry creates conditions that concentrates sex offenders – ranging from the truly predatory to the far more typical “slightly older boy in high school dating someone slightly younger that the parents disapprove”, when CSAM is brought up in an indictment in a computer crime case that is otherwise unrelated and is noted not in the initial indictment but an amended one and has specific ages attached, the actual subtext is that the merits of the primary case isn’t strong enough to go to trial on but prosecutors want to obtain a guaranteed plea. It relies on moral panics and pleas to authority, and should always be viewed with suspicion as to the state’s case. After all, legality only matters if charges are going to be brought. Testilying is still a term openly used by LE, why should these cases be any different? It mostly serves to absolve companies of terrible data security practices and the snake oil sold as solutions in the business.
Firstly you are missing the whole point of the article, this is a Cyber Security blog first and foremost.
Why this case is so ground-breaking, and hence BK’s coverage, is primarily because it shows that a private entity can successfully hold a cyber-criminal civilly liable for their actions, something long thought to be only possible in theory. A legal innovation, the forfeiture of $700,000 to settle a civil lawsuit, that is being framed as a first-of-its-kind outcome. It creates a potential precedent for civil plaintiffs to go after threat actors directly — a theoretical strategy that previously seemed impractical, due to the difficulty of attribution and asset recovery. And the regulars of this site I guarantee, will be applauding that result with glee.
The next point I wish to address is not so celebratory.
I find your comment deeply offensive and, frankly, abhorrent. There is a difference between critically examining prosecutorial discretion and minimising the harm of child sexual abuse — and your comment crosses that line.
You’re absolutely right that the legal system has flaws. Prosecutorial immunity, the challenges of mounting a defence in strict liability cases, and issues around digital evidence — all of these deserve serious, reasoned discussion. The law should always be held to account, especially in its ability to serve justice equitably and transparently.
But none of those structural critiques justify the implicit downplaying of what it means to possess, traffic in, or create CSAM. In this specific case, the individual in question admitted to possessing over 600 CSAM files — not ambiguous selfies or gray-area teen content, but known images of real children, many of whom were likely victims of long-term, documented abuse. These aren’t hypothetical legal abstractions. They are real people whose trauma is perpetually re-lived every time that material is traded or viewed.
And that’s what’s so often missing in comments like YOURS: the voice of the victims. They don’t get to file motions. They don’t get plea deals. They carry the consequences for the rest of their lives.
When you imply that CSAM charges are just a prosecutorial “backstop” or that they’re equivalent to a catch-all like wire fraud, you are doing more than speculating — you’re helping to normalise a narrative that trivialises abuse. Worse still, suggesting that law enforcement “plants” CSAM in cases where they can’t win a hacking charge is an accusation of breathtaking proportions — can that be backed up with clear, documented evidence. Otherwise, I call bullsh*t.
The fact that law enforcement is required to handle such material in the course of investigations doesn’t absolve them of scrutiny — but it’s an entirely different conversation from the one you seem to be having. You’re conflating legal process with moral equivalence, and that’s not just misleading — it’s f*ucking dangerous.
In Cybersecurity, we are entrusted with an enormous responsibility: to protect people, especially the most vulnerable, from exploitation. Who are you protecting? If we can’t even name and denounce the sexual abuse of children without caveats, then we’ve lost our moral compass. You, however, I am unsure where you even stand on all this morally? What is your angle? Or are just using this platform to air your grievance with justice system on behalf of the Fitzpatrick family? … At the expense of victims who don’t have the luxury of defending themselves in comment sections.
One thing I can tell you Bobby, is some things are NOT up for rhetorical debate and CHILD SEXUAL ABUSE is one of them.
Just to be clear as per the PDF. The agreement was to not challenge what Non stop asked for in restitution in his sentencing This was not a 700K settlement. It is what the prosecutors are asking for in victims compensation. He agreed not to challenge this:
Fitzpatrick hereby agrees that he will not object to Plaintiffs’ pursuit of restitution or Plaintiffs’
pursuit of Fitzpatrick’s forfeited property that is presently under control of the federal
government in the matter United States v. Fitzpatrick, No. 23-cr-00119 (E.D. Va.). For the
avoidance of doubt, this Agreement does not require, contemplate or permit any further
forfeiture or other payment by Fitzpatrick, or any waiver or other limitation of Fitzpatrick’s
rights in any civil or criminal proceeding other than this one, including without limitation U.S. v.
Fitzpatrick, No. 23-cr-00119 (E.D. Va.)
Mark, you can f*ck right off with your Fitzpatrick family whataboutism. RIGHT NOW!
And just to be clear, as per the article above, Conor Brian Fitzpatrick is NOT a victim in this set of events and NEVER will be recognised as such on this platform EVER.
Do the crime, do the time. Simple. Get over it.
Now take your whiney arse rhetorical fallacy and shove it where the sun don’t shine.
Hold up, I think he might be saying it’s not a settlement “per se” and is victim restitution in a criminal case as opposed to a settlement of a future civil case…. maybe? IDK how accurate that is but it seems plausible to observe without “per se” supporting Pompom?
mealy, stop pussy footing around the issue. I know what Mark is trying to say and it is not the point. All THEY are trying to do is hijack the narrative with noise.
Restitution or Settlement, who cares? It makes not one iota of difference to the victims of where the compensation comes from or what it is legally titled. All they want is recognition of their suffering. This is all just semantics, is it not?
Remember the Nonstop “settlement” is only related to the the Nonstop data breach victims. And they were the lucky ones to actually see a payday – $50 to $5000.00 – if you can call it that. Court documents indicate that BreachForums hosted nearly 900 stolen databases comprising over 14 billion individual victim records!! What about the CSAM victims? And he got time served. Seriously?
Oh, and for the record, I myself am also on the spectrum. And of all the f*ck ups I have endured throughout my life, not ONCE have I ever blamed it on my condition. EVER. This is all just a sad case of bad parenting – pure and simple. They all need to MAN UP and take RESPONSIBILITY.
“Restitution or Settlement, who cares?” Just noting they are not the same is all.
You are right, I know. I just get frustrated with smoke and mirrors behaviour.
Sorry for chewing you out; it wasn’t really aimed at you, rather those preceding you. I think you already know I would stand up for victim survivors right up to my last breath.
Salute.
I get it. Cheers.