Aisuru, the botnet responsible for a series of record-smashing distributed denial-of-service (DDoS) attacks this year, recently was overhauled to support a more low-key, lucrative and sustainable business: Renting hundreds of thousands of infected Internet of Things (IoT) devices to proxy services that help cybercriminals anonymize their traffic. Experts say a glut of proxies from Aisuru and other sources is fueling large-scale data harvesting efforts tied to various artificial intelligence (AI) projects, helping content scrapers evade detection by routing their traffic through residential connections that appear to be regular Internet users.
First identified in August 2024, Aisuru has spread to at least 700,000 IoT systems, such as poorly secured Internet routers and security cameras. Aisuru’s overlords have used their massive botnet to clobber targets with headline-grabbing DDoS attacks, flooding targeted hosts with blasts of junk requests from all infected systems simultaneously.
In June, Aisuru hit KrebsOnSecurity.com with a DDoS clocking at 6.3 terabits per second — the biggest attack that Google had ever mitigated at the time. In the weeks and months that followed, Aisuru’s operators demonstrated DDoS capabilities of nearly 30 terabits of data per second — well beyond the attack mitigation capabilities of most Internet destinations.
These digital sieges have been particularly disruptive this year for U.S.-based Internet service providers (ISPs), in part because Aisuru recently succeeded in taking over a large number of IoT devices in the United States. And when Aisuru launches attacks, the volume of outgoing traffic from infected systems on these ISPs is often so high that it can disrupt or degrade Internet service for adjacent (non-botted) customers of the ISPs.
“Multiple broadband access network operators have experienced significant operational impact due to outbound DDoS attacks in excess of 1.5Tb/sec launched from Aisuru botnet nodes residing on end-customer premises,” wrote Roland Dobbins, principal engineer at Netscout, in a recent executive summary on Aisuru. “Outbound/crossbound attack traffic exceeding 1Tb/sec from compromised customer premise equipment (CPE) devices has caused significant disruption to wireline and wireless broadband access networks. High-throughput attacks have caused chassis-based router line card failures.”
The incessant attacks from Aisuru have caught the attention of federal authorities in the United States and Europe (many of Aisuru’s victims are customers of ISPs and hosting providers based in Europe). Quite recently, some of the world’s largest ISPs have started informally sharing block lists identifying the rapidly shifting locations of the servers that the attackers use to control the activities of the botnet.
Experts say the Aisuru botmasters recently updated their malware so that compromised devices can more easily be rented to so-called “residential proxy” providers. These proxy services allow paying customers to route their Internet communications through someone else’s device, providing anonymity and the ability to appear as a regular Internet user in almost any major city worldwide.

From a website’s perspective, the IP traffic of a residential proxy network user appears to originate from the rented residential IP address, not from the proxy service customer. Proxy services can be used in a legitimate manner for several business purposes — such as price comparisons or sales intelligence. But they are massively abused for hiding cybercrime activity (think advertising fraud, credential stuffing) because they can make it difficult to trace malicious traffic to its original source.
And as we’ll see in a moment, this entire shadowy industry appears to be shifting its focus toward enabling aggressive content scraping activity that continuously feeds raw data into large language models (LLMs) built to support various AI projects.
‘INSANE’ GROWTH
Riley Kilmer is co-founder of spur.us, a service that tracks proxy networks. Kilmer said all of the top proxy services have grown substantially over the past six months.
“I just checked, and in the last 90 days we’ve seen 250 million unique residential proxy IPs,” Kilmer said. “That is insane. That is so high of a number, it’s unheard of. These proxies are absolutely everywhere now.”
Today, Spur says it is tracking an unprecedented spike in available proxies across all providers, including;
LUMINATI_PROXY 11,856,421
NETNUT_PROXY 10,982,458
ABCPROXY_PROXY 9,294,419
OXYLABS_PROXY 6,754,790
IPIDEA_PROXY 3,209,313
EARNFM_PROXY 2,659,913
NODEMAVEN_PROXY 2,627,851
INFATICA_PROXY 2,335,194
IPROYAL_PROXY 2,032,027
YILU_PROXY 1,549,155
Reached for comment about the apparent rapid growth in their proxy network, Oxylabs (#4 on Spur’s list) said while their proxy pool did grow recently, it did so at nowhere near the rate cited by Spur.
“We don’t systematically track other providers’ figures, and we’re not aware of any instances of 10× or 100× growth, especially when it comes to a few bigger companies that are legitimate businesses,” the company said in a written statement.
Bright Data was formerly known as Luminati Networks, the name that is currently at the top of Spur’s list of the biggest residential proxy networks. Bright Data likewise told KrebsOnSecurity that Spur’s current estimates of its proxy network are dramatically overstated and inaccurate.
“We did not actively initiate nor do we see any 10x or 100x expansion of our network, which leads me to believe that someone might be presenting these IPs as Bright Data’s in some way,” said Rony Shalit, Bright Data’s chief compliance and ethics officer. “In many cases in the past, due to us being the leading data collection proxy provider, IPs were falsely tagged as being part of our network, or while being used by other proxy providers for malicious activity.”
“Our network is only sourced from verified IP providers and a robust opt-in only residential peers, which we work hard and in complete transparency to obtain,” Shalit continued. “Every DC, ISP or SDK partner is reviewed and approved, and every residential peer must actively opt in to be part of our network.”
HK NETWORK
Even Spur acknowledges that Luminati and Oxylabs are unlike most other proxy services on their top proxy providers list, in that these providers actually adhere to “know-your-customer” policies, such as requiring video calls with all customers, and strictly blocking customers from reselling access.
Benjamin Brundage is founder of Synthient, a startup that helps companies detect proxy networks. Brundage said if there is increasing confusion around which proxy networks are the most worrisome, it’s because nearly all of these lesser-known proxy services have evolved into highly incestuous bandwidth resellers. What’s more, he said, some proxy providers do not appreciate being tracked and have been known to take aggressive steps to confuse systems that scan the Internet for residential proxy nodes.
Brundage said most proxy services today have created their own software development kit or SDK that other app developers can bundle with their code to earn revenue. These SDKs quietly modify the user’s device so that some portion of their bandwidth can be used to forward traffic from proxy service customers.
“Proxy providers have pools of constantly churning IP addresses,” he said. “These IP addresses are sourced through various means, such as bandwidth-sharing apps, botnets, Android SDKs, and more. These providers will often either directly approach resellers or offer a reseller program that allows users to resell bandwidth through their platform.”
Many SDK providers say they require full consent before allowing their software to be installed on end-user devices. Still, those opt-in agreements and consent checkboxes may be little more than a formality for cybercriminals like the Aisuru botmasters, who can earn a commission each time one of their infected devices is forced to install some SDK that enables one or more of these proxy services.
Depending on its structure, a single provider may operate hundreds of different proxy pools at a time — all maintained through other means, Brundage said.
“Often, you’ll see resellers maintaining their own proxy pool in addition to an upstream provider,” he said. “It allows them to market a proxy pool to high-value clients and offer an unlimited bandwidth plan for cheap reduce their own costs.”
Some proxy providers appear to be directly in league with botmasters. Brundage identified one proxy seller that was aggressively advertising cheap and plentiful bandwidth to content scraping companies. After scanning that provider’s pool of available proxies, Brundage said he found a one-to-one match with IP addresses he’d previously mapped to the Aisuru botnet.
Brundage says that by almost any measurement, the world’s largest residential proxy service is IPidea, a China-based proxy network. IPidea is #5 on Spur’s Top 10, and Brundage said its brands include ABCProxy (#3), Roxlabs, LunaProxy, PIA S5 Proxy, PyProxy, 922Proxy, 360Proxy, IP2World, and Cherry Proxy. Spur’s Kilmer said they also track Yilu Proxy (#10) as IPidea.
Brundage said all of these providers operate under a corporate umbrella known on the cybercrime forums as “HK Network.”
“The way it works is there’s this whole reseller ecosystem, where IPidea will be incredibly aggressive and approach all these proxy providers with the offer, ‘Hey, if you guys buy bandwidth from us, we’ll give you these amazing reseller prices,'” Brundage explained. “But they’re also very aggressive in recruiting resellers for their apps.”
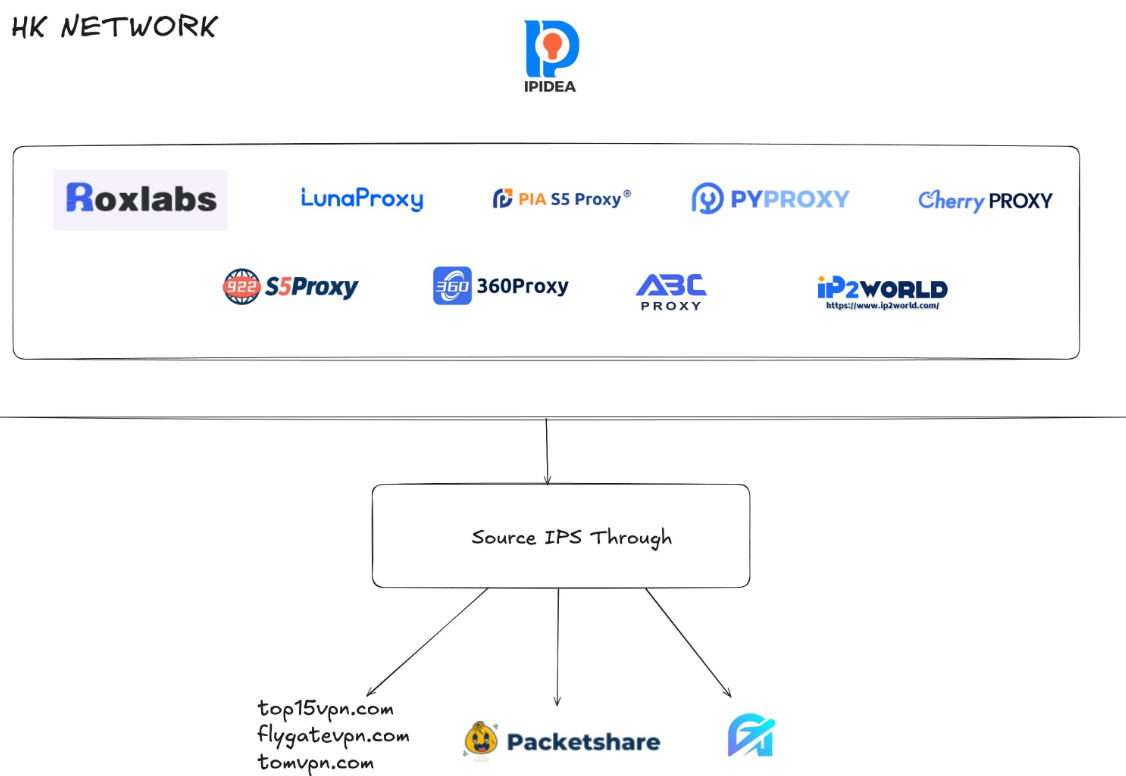
A graphic depicting the relationship between proxy providers that Synthient found are white labeling IPidea proxies. Image: Synthient.com.
Those apps include a range of low-cost and “free” virtual private networking (VPN) services that indeed allow users to enjoy a free VPN, but which also turn the user’s device into a traffic relay that can be rented to cybercriminals, or else parceled out to countless other proxy networks.
“They have all this bandwidth to offload,” Brundage said of IPidea and its sister networks. “And they can do it through their own platforms, or they go get resellers to do it for them by advertising on sketchy hacker forums to reach more people.”
One of IPidea’s core brands is 922S5Proxy, which is a not-so-subtle nod to the 911S5Proxy service that was hugely popular between 2015 and 2022. In July 2022, KrebsOnSecurity published a deep dive into 911S5Proxy’s origins and apparent owners in China. Less than a week later, 911S5Proxy announced it was closing down after the company’s servers were massively hacked.
That 2022 story named Yunhe Wang from Beijing as the apparent owner and/or manager of the 911S5 proxy service. In May 2024, the U.S. Department of Justice arrested Mr Wang, alleging that his network was used to steal billions of dollars from financial institutions, credit card issuers, and federal lending programs. At the same time, the U.S. Treasury Department announced sanctions against Wang and two other Chinese nationals for operating 911S5Proxy.
The website for 922Proxy.
DATA SCRAPING FOR AI
In recent months, multiple experts who track botnet and proxy activity have shared that a great deal of content scraping which ultimately benefits AI companies is now leveraging these proxy networks to further obfuscate their aggressive data-slurping activity. That’s because by routing it through residential IP addresses, content scraping firms can make their traffic far trickier to filter out.
“It’s really difficult to block, because there’s a risk of blocking real people,” Spur’s Kilmer said of the LLM scraping activity that is fed through individual residential IP addresses, which are often shared by multiple customers at once.
Kilmer says the AI industry has brought a veneer of legitimacy to residential proxy business, which has heretofore mostly been associated with sketchy affiliate money making programs, automated abuse, and unwanted Internet traffic.
“Web crawling and scraping has always been a thing, but AI made it like a commodity, data that had to be collected,” Kilmer said. “Everybody wanted to monetize their own data pots, and how they monetize that is different across the board.”
Kilmer said many LLM-related scrapers rely on residential proxies in cases where the content provider has restricted access to their platform in some way, such as forcing interaction through an app, or keeping all content behind a login page with multi-factor authentication.
“Where the cost of data is out of reach — there is some exclusivity or reason they can’t access the data — they’ll turn to residential proxies so they look like a real person accessing that data,” Kilmer said of the content scraping efforts.
Aggressive AI crawlers increasingly are overloading community-maintained infrastructure, causing what amounts to persistent DDoS attacks on vital public resources. A report earlier this year from LibreNews found some open-source projects now see as much as 97 percent of their traffic originating from AI company bots, dramatically increasing bandwidth costs, service instability, and burdening already stretched-thin maintainers.
Cloudflare is now experimenting with tools that will allow content creators to charge a fee to AI crawlers to scrape their websites. The company’s “pay-per-crawl” feature is currently in a private beta, and it lets publishers set their own prices that bots must pay before scraping content.
On October 22, the social media and news network Reddit sued Oxylabs (PDF) and several other proxy providers, alleging that their systems enabled the mass-scraping of Reddit user content even though Reddit had taken steps to block such activity.
“Recognizing that Reddit denies scrapers like them access to its site, Defendants scrape the data from Google’s search results instead,” the lawsuit alleges. “They do so by masking their identities, hiding their locations, and disguising their web scrapers as regular people (among other techniques) to circumvent or bypass the security restrictions meant to stop them.”
Denas Grybauskas, chief governance and strategy officer at Oxylabs, said the company was shocked and disappointed by the lawsuit.
“Reddit has made no attempt to speak with us directly or communicate any potential concerns,” Grybauskas said in a written statement. “Oxylabs has always been and will continue to be a pioneer and an industry leader in public data collection, and it will not hesitate to defend itself against these allegations. Oxylabs’ position is that no company should claim ownership of public data that does not belong to them. It is possible that it is just an attempt to sell the same public data at an inflated price.”
As big and powerful as Aisuru may be, it is hardly the only botnet that is contributing to the overall broad availability of residential proxies. For example, on June 5 the FBI’s Internet Crime Complaint Center warned that an IoT malware threat dubbed BADBOX 2.0 had compromised millions of smart-TV boxes, digital projectors, vehicle infotainment units, picture frames, and other IoT devices.
In July, Google filed a lawsuit in New York federal court against the Badbox botnet’s alleged perpetrators. Google said the Badbox 2.0 botnet “compromised more than 10 million uncertified devices running Android’s open-source software, which lacks Google’s security protections. Cybercriminals infected these devices with pre-installed malware and exploited them to conduct large-scale ad fraud and other digital crimes.”
A FAMILIAR DOMAIN NAME
Brundage said the Aisuru botmasters have their own SDK, and for some reason part of its code tells many newly-infected systems to query the domain name fuckbriankrebs[.]com. This may be little more than an elaborate “screw you” to this site’s author: One of the botnet’s alleged partners goes by the handle “Forky,” and was identified in June by KrebsOnSecurity as a young man from Sao Paulo, Brazil.
Brundage noted that only systems infected with Aisuru’s Android SDK will be forced to resolve the domain. Initially, there was some discussion about whether the domain might have some utility as a “kill switch” capable of disrupting the botnet’s operations, although Brundage and others interviewed for this story say that is unlikely.
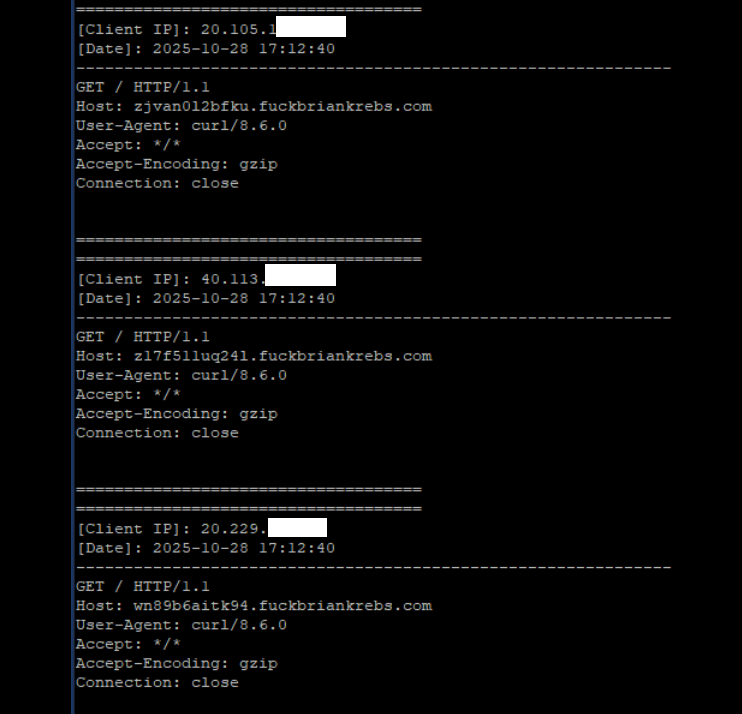
A tiny sample of the traffic after a DNS server was enabled on the newly registered domain fuckbriankrebs dot com. Each unique IP address requested its own unique subdomain. Image: Seralys.
For one thing, they said, if the domain was somehow critical to the operation of the botnet, why was it still unregistered and actively for-sale? Why indeed, we asked. Happily, the domain name was deftly snatched up last week by Philippe Caturegli, “chief hacking officer” for the security intelligence company Seralys.
Caturegli enabled a passive DNS server on that domain and within a few hours received more than 700,000 requests for unique subdomains on fuckbriankrebs[.]com.
But even with that visibility into Aisuru, it is difficult to use this domain check-in feature to measure its true size, Brundage said. After all, he said, the systems that are phoning home to the domain are only a small portion of the overall botnet.
“The bots are hardcoded to just spam lookups on the subdomains,” he said. “So anytime an infection occurs or it runs in the background, it will do one of those DNS queries.”

Caturegli briefly configured all subdomains on fuckbriankrebs dot com to display this ASCII art image to visiting systems today.
The domain fuckbriankrebs[.]com has a storied history. On its initial launch in 2009, it was used to spread malicious software by the Cutwail spam botnet. In 2011, the domain was involved in a notable DDoS against this website from a botnet powered by Russkill (a.k.a. “Dirt Jumper”).
Domaintools.com finds that in 2015, fuckbriankrebs[.]com was registered to an email address attributed to David “Abdilo” Crees, a 27-year-old Australian man sentenced in May 2025 to time served for cybercrime convictions related to the Lizard Squad hacking group.
Update, Nov. 1, 2025, 10:25 a.m. ET: An earlier version of this story erroneously cited Spur’s proxy numbers from earlier this year; Spur said those numbers conflated residential proxies — which are rotating and attached to real end-user devices — with “ISP proxies” located at AT&T. ISP proxies, Spur said, involve tricking an ISP into routing a large number of IP addresses that are resold as far more static datacenter proxies.




This may be a naive comment, but if it is so easy for the Black Hats to identify and control so many IOT devices for their purposes, would it be possible for a White Hat organization to secure/control IOT devices in a way that they are no longer available to the Black Hats?
It is possible for the good folks to provide more security on their devices. It would cost them money and TBH, have little material ROI. The motivation for them to spend on security simply isn’t there, while the “rush to market” motivation is strong. Example: The article mentions internet connected security cameras. Today there are actually THOUSANDs of competing products in this space listed on Amazon. This is a highly competitive market, if you want to sell, you must be cheap and have a laundry list of new features that your competitors don’t. I’m talking about internet connected devices that retail for less than TEN dollars. How much security did the provider bake into a $8.97 internet connected secure camera? Probably not as much as the same device listed for $139, but which is the consumer that needs a camera buying?
“Probably not as much as the same device listed for $139” – I’d say maybe.
A lot of those run the same underlying HW under various sub-brands. The $139 one will put a shiny interface package on top and call that the security measure but it has the potential to open as many new holes as it might block. More dollars does not necessarily translate to more secure.
$139 is absolutely the new 67.
velvetdogs.com/i/gHOh39
Not sure that I’d define someone as a white hat if they control devices without owners permission. If they do that really stupidly they could even get prosecuted or be found liable for consequences if say their action bricks it, and the function failing to be performed had expensive consequences.
Note that government agencies have more ability to gain legal protection to perform non white hat acts, but even then they’d more likely seize c2 servers than access devices, so their actions generally have minimal risk of further harming a compromised device.
what we really need is more viewings of Spielberg movies to help locate the old Disney ‘model neighborhood’ we destroyed in the 80s and really add more trauma programs for William Sargent.
bad news. no new heirs.
I meant, cost of Wachovia in 2008.
Apparently Punxatawnie thinks the money spent last night will return tonight.
Whatta gal.
Short answer: not in a global, “flip-a-switch” way—and definitely not legally by taking over people’s devices. But there are white-hat ways to make huge swaths of IoT gear useless to attackers. Remotely accessing or altering devices you don’t own is illegal in most jurisdictions (even to patch them). IoT is wildly heterogeneous; many devices can’t be patched safely (fragile firmware, no rollback, no space).Ownership & liability: if a defensive worm bricks cameras or pacers, who pays?
IOT and AI what could possibly go wrong?
IOT with no network connection and smoke alarms: What could possibly go wrong?
This reminds me the time I found a bunch of people bouncing off of inflatable breast and gay porn sex stores when I contracted for an undisclosed security vendor in the Netherlands. Apparently nobody thought anything of the ramifications of that either until their sentencing. I don’t think that hacking case was ever publicized though. It was in 2007/2008, if I recall. Some of the gay spam coming out of that botnet was horrendous.
All spam is horrendous. Gay spam is gay horrendous.
yo, mealy, I got a joke for you:
Malware walks into a bar, bartender says, ‘what’ll you have?’ Malware says, ‘my usual, but four of ‘em, and make em doubles, then I’m gonna crash.’ Bartender goes, ‘you alright man? that’s more than you usually have.’ Malware says to the bartender, ‘dude, I just saw my shrink and got diagnosed with a conversion disorder.’
bwahahaha.
wikipedia.org/wiki/Conversion_disorder
(had to look it up)
“I see what you did there.” – Hellen Keller, deadpan
Out of curiosity, how much do these residential proxy companies pay for connections?
Someone who considers himself to be an elite hacker tried to talk me into leasing out some of our IP addresses on our network about three months ago and gave me some pie in the sky type of estimate on how much we could bring in, but I don’t believe his figures at all. He seemed to think that we could get $10 to $20 per IP address per month.
My guess is that they would want a whole lot more bandwidth than we would be willing to make available to them assuming that they would want to use them non-stop. With our normal traffic, I wouldn’t be willing to give them more than 2 or 3 megabits per second per IP — I doubt that anyone would pay for that.
I don’t have a good understanding of that world but I think 2 or 3 megabits per second could be fine for some uses. Proxies with good reputation seem to be useful for all kinds of things: buying tickets, scraping websites, credential stuffing, carding, you name it.
Its ai(assistive Intellect) there is no Synthetic intelligence to it; period.
That being said, a voracious collection of scrapers, hungry for data;
dispatched in batches to feed some LLM; what did you expect.
Sadly the truth is a flat playing field acres of data exposed by consumer-grade TEK,
especially at the residence level where setup is a major production,
and updates/security are a hoped-for nothing.
Its good companies finally force password set@install; …..now.
But a vast generation of ‘home routers’ lingers on, and still fertile.
Watching some of the for-free websites that list bad IP addresses shows
the trends of mischief and unrest, same decades old approach.
Yet notwithstanding some really staggering DDOS,
its a credit to the growing and expanding Internet(s).
The old Users wondered if we’d get here; we did.
The younger surfer, marvel at the vast array of services.
After looking at the chaos some in the federal legislature will abide,
we shouldn’t be amazed in cyberspace we should catch breathe at the perilous conditions.
if nothing else; the amount of Data taken in this latest harvest,
and its use; [direct or resale] to advertising funding sources; is stunning.
The harvest, storage, vectorization, and chat-ends, is worryingly amazing.
but it facilitates data-sharing, no one really signed on for.
We’re confronted with having wisdoms need to catch up with discovery,
angel and ministers of grace, indeed.
should make us realize
Many industries are responsible, to varying degrees, for the safety/reliability of their products post-sale. Products are routinely recalled and manufacturers are routinely sued. Why are IOT manufacturers not held to similar standards given the degree of collective damage their insecure out-of-the-box products have and will cause? Where is the enterprising class-action law firm whose suits will prompt IOT manufacturers to ship products that must be secured before they can be put into production and connected to the Internet proper?
> Why are IOT manufacturers not held to similar standards given the degree of collective damage their insecure out-of-the-box products have and will cause?
It is a mistake to focus on just IoT devices, when there are computers and smart phones that can just as easily be made part of a botnet via hacking or trojan apps/libraries or shady browser extensions (and more, like the discussed *intentional* proxy services people run to make an extra buck). The problem fundamentally is that ISPs are unwilling to deal with customers on their network that are the source of abuse (whatever the cause). Nor do they seem to be willing to de-peer any other networks that do not police their abusers. If they simply did that, botnets would naturally start to dwindle in size rather than keep growing.
In short, the “standards” you have in mind are not held by *anyone* in a position to take action. That’s best illustrated in Brian’s article where Roland Dobbins notes a lack of concern about any of this growing DDoS activity until an ISPs own *internal* operations are impacted. Even then, you’re not reading any headlines about them actually dealing with the customers that are the source of the problem. Instead, what you’ll often see is ISPs refusing to host the *target* of said attacks. Up is down.
Correct. There is no internet police.
drone.
troll.
I’d beg to differ. Just ask Terminator 2 about the ‘big jump’ scene with woofie.
Since Ddos and proxy are becoming such a nuisance in the hacking platform if you really want to be so comfortable with AI put it to good use Maximize AI’s functionality for good. Let it pick up on unauthorized users and force them to an open platform to be monitored and surveyed until cleared by an individual agent. Otherwise let AI toss them out not allowing any proxy to intervene if not properly tracked.
Would you really want to trust any form of ai to such a thing? Didn’t sci-fi warn you enough of the inherent dangers? Maybe you should consider the dangers of what ai, itself, would consider an ‘open platform’. You don’t want them policing you. Trust me.
AI currently runs a lot of endpoint detection regimes that determine what gets blocked.
But I agree with you – you don’t want that, nobody really does at the current state.
Good advice, Thanks Jim Carrey.
Not real sure what this means: “Cybercriminals infected these devices with pre-installed malware”. Did the criminals sneak an exploit into Android’s open-source code/SDK? Or did they have agents at the device manufacturer that pre-installed something?
I agree, exact you that typed the above comment. It’s time for YOU to lose YOUR plug. It’s an imperative.
and tell fake Ratched her dad needs her back in the 60s to finally figure out the Einstein-Rosen bridge wasn’t for her to find all those buttons either.
synovitis was awesome. daisy printers went out long ago.
Since we claimed sesame seeds shouldn’t we have bugs walking on us too?
I mean, if the deal is 2002. I mean terminator I had on my old computer in 1998/1999.
Any idea what DNS servers/services/IP ranges the Aisaurus is using?
How can I get access to CloudFlare betas, please?
bad news, half a bottle of water is neither a ‘lake house’ nor a burgeoning water distributer.
kinda too bad for Jamaica though.
making a list, checking it twice, making sure I get every party this time, so we can all have favors.
I heard Nvidia is backdoored. Happened during the Citrix conference. Is this true?
Sure it’s true, you heard it.
All these proxy servers are so evil. They were meant only to cyber criminals. All these proxy services operators, VPN services operators, TOR node operators, privacy advocates and crypto enthusiasts they should all go to JAIL! If you are an honest person like Mister respectable owner of this blog then you have nothing to hide! You do not need to use proxy servers, VPN servers and TOR! You can send your ID to verify yourself and prove that you are honest person like respectable owner of this blog! F*CK FORKY! Why we can’t make new tariffs to that ridiculous Brazilian country??? That should put FORKY in Jail for many, many, many years!
Can anyone remove this clearly AI generated incoherent screeching from this comments section?
kthxbai
I upvote this.
It’s so funny to see an American crying over a Brazilian who pays 120% in taxes, lacks healthcare, education, and security, and lives in an underdeveloped country. Imagine if that Brazilian were from a first-world country? He would have devoured the USA.
“in that these providers actually adhere to “know-your-customer” policies, such as requiring video calls with all customers, and strictly blocking customers from reselling access.”
I have a bad feeling about this and I bet you can guess why.
I perused this article wondering if I could learn how to check my home router to see if it was infected. I can look at the traffic stats from the router to all my devices (shows one number). But I don’t believe traffic stats would show traffic only on the internet side of the router.
Anyone know how to do this?
Correction, the stats on my router does show the internet side. However, I have no idea how much traffic I would see if this router is infected. Still wondering how to see if the router is infected.
You can look up router model/firmware version and see if it comes up on any CVEs. If so, probably safe to assume it’s infected
A vuln’s mere existence is not evidence of compromise. That takes more.
Classic adversary economics: when DDoS profits drop or become noisy, criminals move to stealthier, recurring revenue — residential proxies. Fixing this won’t be one-gadget or one-law; it’ll take hardened IoT defaults, smarter ISP cooperation, and demand-side accountability from companies buying scraped data.
it mentions a lot of these proxies are from botnets, but actually the major provider LUMINATI thats mentioned there (now omegaproxy afaik) i think uses something, that’s ‘like a botnet’ rather than straightup owning boxes.
They run all sorts of ‘secure messaging & calling’ apps. The users form a peer-to-peer network to relay eachothers traffic like ToR. The users all sign licence agreement to allow that. These apps are available and mass downloaded on appstores for all platforms, but mostly android prevalence.
Now they have big peer-to-peer proxy / relay networks what can they do:
-offer more apps, VPN services this time, making use of same peer-to-peer network.
-residential proxy services.
ddos for hire and others likely not excluded, but i’d assume more ‘noisy’ things would not go via these app-users to ensure they don’t get blocked, IoT devices dont have active users and often don’t need to connect to all sorts of places so they are less bad to get blocked.
Just wanna put that out there in case ppl think all these 250 million ips (likely less… but ok) are really IoT devices or ‘infected’ machines.
They are infected by playstore apps that tout privacy and security (which they likely actually give…) and their owners even take ad revenue…..