Credit card industry giant Visa on Friday issued a security alert warning companies using point-of-sale devices made by Oracle‘s MICROS retail unit to double-check the machines for malicious software or unusual network activity, and to change passwords on the devices. Visa also published a list of Internet addresses that may have been involved in the Oracle breach and are thought to be closely tied to an Eastern European organized cybercrime gang.
The Visa alert is the first substantive document that tries to help explain what malware and which malefactors might have hit Oracle — and by extension many of Oracle’s customers — since KrebsOnSecurity broke news of the breach on Aug. 8. That story cited sources close to the investigation saying hackers had broken into hundreds of servers at Oracle’s retail division, and had completely compromised Oracle’s main online support portal for MICROS customers.
MICROS is among the top three point-of-sale vendors globally. Oracle’s MICROS division sells point-of-sale systems used at more than 330,000 cash registers worldwide. When Oracle bought MICROS in 2014, the company said MICROS’s systems were deployed at some 200,000+ food and beverage outlets, 100,000+ retail sites, and more than 30,000 hotels.
In short, tens of millions of credit cards are swiped at MICROS terminals monthly, and a breach involving the theft of credentials that might have granted remote access to even just a small percentage of those systems is potentially a big and costly problem for all involved.
So far, however, most MICROS customers are left scratching their heads for answers. A frequently asked questions bulletin (PDF) Oracle also released last Monday held little useful information. Oracle issued the same cryptic response to everyone who asked for particulars about how far the breach extended. “Oracle has detected and addressed malicious code in certain legacy MICROS systems.”
Oracle also urged MICROS customers to change their passwords, and said “we also recommend that you change the password for any account that was used by a MICROS representative to access your on-premises systems.”
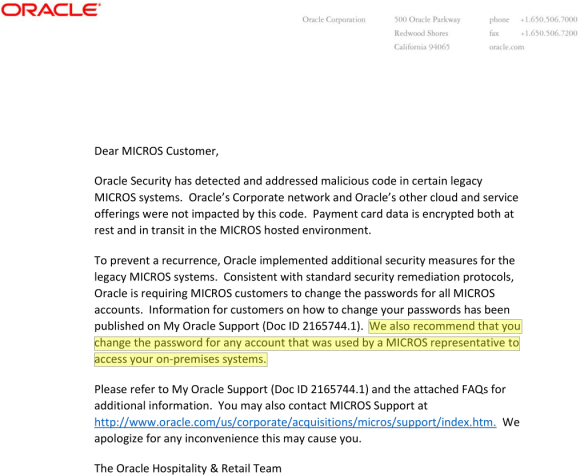
One of two documents Oracle sent to MICROS customers and the sum total of information the company has released so far about the breach.
Some technology and fraud experts, including Gartner Analyst Avivah Litan, read that statement highlighted in yellow above as an acknowledgement by Oracle that hackers may have abused credentials gained in the MICROS portal breach to plant malicious code on the point-of-sale devices run by an unknown number of MICROS customers.
“This [incident] could explain a lot about the source of some of these retail and merchant point-of-sale hacks that nobody has been able to definitively tie to any one point-of-sale services provider,” Litan told me last week. “I’d say there’s a big chance that the hackers in this case found a way to get remote access” to MICROS customers’ on-premises point-of-sale devices.”
Clearly, Visa is concerned about this possibility as well.
INDICATORS OF COMPROMISE
In my original story about the breach, I wasn’t able to reveal all the data I’d gathered about the apparent source of the attacks and attackers. A key source in that story asked that I temporarily delay publishing certain details of the investigation, specifically those known as indicators of compromise (IOCs). Basically, IOCs are list of suspect Internet addresses, domain names, filenames and other curious digital clues that are thought to connect the victim with its attacker.
I’ve been inundated all week with calls and emails from security experts asking for that very data, but sharing it wasn’t my call. That is, until yesterday (8/12/16), when Visa published a “merchant communication alert” to some customers. In that alert (PDF), Visa published IOCs that may be connected with the intrusion. These IOCs could be extremely useful to MICROS customers because the presence of Internet traffic to and from these online destinations would strongly suggest the organization’s point-of-sale systems may be similarly compromised.
Some of the addresses on this list from Visa are known to be associated with the Carbanak Gang, a group of Eastern European hackers that Russian security firm Kaspersky Lab estimates has stolen more than $1 billion from banks and retailers. Here’s the IOCs list from the alert Visa pushed out Friday:
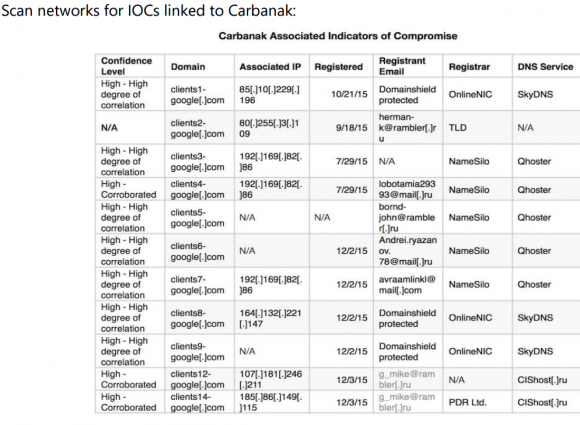
Visa warned merchants to check their systems for any communications to and from these Internet addresses and domain names associated with a Russian organized cybercrime gang called “Carbanak.”
Thankfully, since at least one of the addresses listed above (192.169.82.86) matched what’s on my source’s list, the source agreed to let me publish the entire thing. Here it is. I checked my source’s list and found at least five Internet addresses that were seen in both the Oracle attack and in a Sept. 2015 writeup about Carbanak by ESET Security, a Slovakian antivirus and security company. [NB: If you are unskilled at safely visiting malicious Web sites and/or handling malware, it’s probably best not to visit the addresses in the above-linked list.]
Visa also mentioned a specific POS-malware threat in its alert called “MalumPOS.” According to researchers at Trend Micro, MalumPOS is malware designed to target point-of-sale systems in hotels and related industries. In fact, Trend found that MalumPOS is set up to collect data specifically from point-of-sale systems running on Oracle’s MICROS platform.
It should come as no surprise then that many of Oracle’s biggest customers in the hospitality industry are starting to make noise, accusing Oracle of holding back key information that could help MICROS-based companies stop and clean up breaches involving malware and stolen customer credit card data.
“Oracle’s silence has been deafening,” said Michael Blake, chief executive officer at HTNG, a trade association for hotels and technology. “They are still grappling and trying to answer questions on the extent of the breach. Oracle has been invited to the last three [industry] calls this week and they are still going about trying to reach each customer individually and in the process of doing so they have done nothing but given the lame advice of changing passwords.”
The hospitality industry has been particularly hard hit by point-of-sale compromises over the past two years. Last month, KrebsOnSecurity broke the news of a breach at Kimpton Hotels (Kimpton appears to run MICROS products, but the company declined to answer questions for this story).
Kimpton joins a long list of hotel brands that have acknowledged card breaches over the last year, including Trump Hotels (twice), Hilton, Mandarin Oriental, and White Lodging (twice), Starwood Hotels and Hyatt. In many of those incidents, thieves had planted malicious software on the point-of-sale devices at restaurants and bars inside of the hotel chains. And, no doubt, many of those cash registers were run on MICROS systems.
If Oracle doesn’t exactly know which — if any — of its MICROS customers had malware on their point-of-sale systems as a result of the breach, it may be because the network intruders didn’t have any reason to interact with Oracle’s customers via the MICROS portal after stealing usernames and passwords that would allow them to remotely access customer on-premises systems. In theory, at that point the fraudsters could have bypassed Oracle altogether from then on.
BREACHED BY MULTIPLE ACTORS?
Another possibly interesting development in the Oracle breach story: There are indications that Oracle may have been breached by more than one cybercrime group. Or at least handed off from one to the other.
Late this week, Thomas Fox-Brewster at Forbes published a story noting that MICROS was just one of at least five point-of-sale companies that were recently hacked by a guy who — from an exhaustive review of his online chats — appears to have just sat himself down one day and decided to hack a bunch of point-of-sale companies.
Forbes quoted my old friend Alex Holden of Hold Security saying he had evidence that hackers had breached at least 10 payment companies, and the story focuses on getting confirmation from the various other providers apparently breached by the same cybercriminal actor.
Holden showed me multiple pages worth of chat logs between two individuals on a cybercrime forum [full disclosure: Holden’s company lists me as an adviser, but I accept no compensation for that role, and he ignores most of my advice].
The discussion between the two hackers begins around July 15, 2016, and goes on for more than a week. In it, the two hackers have been introduced to one another through a mutual, trusted contact. For a while, all they discuss is whether the seller can be trusted to deliver the Oracle MICROS database and control over the Oracle MICROS customer ticketing portal.
In the end, the buyer is convinced by what he sees and agrees to pay the bitcoin equivalent of roughly USD $13,000 for access to Oracle’s MICROS portal, as well as a handful of other point-of-sale Web sites. The buyer’s bitcoin wallet and the associated transactions can be seen here.
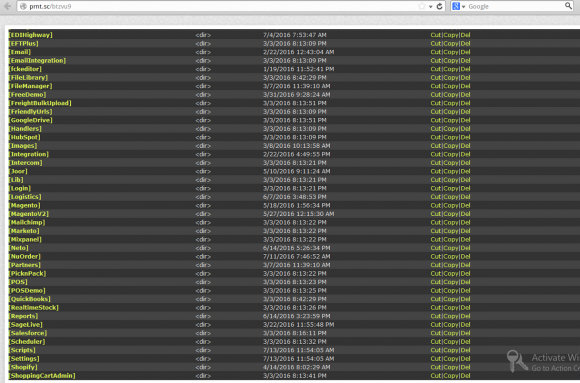
A screen shot shared by one of the hackers involved in compromising Oracle’s MICROS support portal. This screen shot was taken of a similar Web shell the hackers placed on the Web site of another POS provider (this is not the shell that was on Oracle).
According to the chat log, the hacker broke in by exploiting a file-upload function built into the MICROS customer support portal. From there the attackers were able to upload an attack tool known as a “WSO Web Shell.” This is a crude but effective text-based control panel that helps the attacker install additional attack tools to harvest data from the compromised Web server (see screen shot above). The beauty of a Web shell is that the attacker can control the infected site using nothing more than a Web browser, using nothing more than a hidden login page and a password that only he knows.
The two hackers discussed and both viewed more than a half-dozen files that were apparently left behind on the MICROS portal by the WSO shell they uploaded in mid-July (most of the malicious files ended in the file extension “wso.aspx”). The chat logs show the pair of miscreants proceeding to target another 9 online payment providers or point-of-sale vendors.
Some of those companies were quoted in the Forbes piece having acknowledged a breach similar to the Web shell attack at Oracle. But none of them have anywhere near the size of Oracle’s MICROS customer base.
GOOD HOSPITALITY, OR SWEPT UNDER THE RUG?
Oracle maintains in its FAQ (PDF) about the MICROS attack that “Oracle’s Corporate network and Oracle’s other cloud and service offerings were not impacted.” But a confidential source within Oracle’s Hospitality Division told KrebsOnSecurity that the breach first started in one of Oracle’s major point-of-sale data centers — specifically the company’s large data center in Manassas, Va.
According to my source, that particular center helps large Oracle hospitality industry clients manage their fleets of MICROS point-of-sale devices.
“Initially, the customer’s network and the internal Oracle network were on the same network,” said my source, who spoke under condition of anonymity because he did not have permission from his employer to speak on the record. “The networking team did a network segmentation of these two networks — ironically for security purposes. However, it seems as if what they have done actually allowed access from the Russian Cybercrime group.”
My source said that in mid-July 2016 Oracle sent out an email alert to employees of its hospitality division that they had to re-image their laptops without backing anything up.
“All of the files and software that were on an employee’s computer were deleted, which was crippling to business operations,” my source recalled. “Project management lost all their schedules, deployment teams lost all the software that they use to install on customer sites. Oracle did not tell the employees in this email that they got hacked but just to re-image everything with no backups. It seems as if Oracle did a pretty good job sweeping this incident under the rug. Most employees don’t know about the hack and it hasn’t been a huge deal to the customers. However, it is estimated that this cost them billions, so it is a really major breach.”
I sent Oracle a litany of questions based on the above, but a spokesperson for the company said Oracle would comment on none of it.





VISA should have checked with Micros about that before issuing guidance on changing default passwords. When I ran security in a retail org, we had very widely used product of theirs. During testing, red team filched a bunch of default creds, but there were several hard coded into the application that support informed us we could not change.
Hardcoded? Then that is just stupid, and could be a reason why the system was compromised in the first place.
Welcome to retail. Point of Sale systems are absolutely terrible. Hard coded passwords, requirements of running as administrator, default logins, shared accounts, etc, etc, etc..
Had a program that required local admin access to run. Complained to the vendor. They said I shouldn’t be worried because it only needed admin access on the computer, not the network. When I pointed out that local admin access allows for the possibility of loading software that can monitor the network or do other things I didn’t want, they said I was over concerned.
So am I to understand that this may be the biggest POS breach up till now? Maybe I’m reading too much into the article; perhaps that may not be known for some time.
“I sent Oracle a litany of questions based on the above, but a spokesperson for the company said Oracle would comment on none of it.”
What? I was waiting for at least a “…at Oracle we take your security seriously…..”
I need a good laugh.
Why would anyone trust Oracle after this. If I’m a consumer, I’m going to a hotel, restaurant, retailer that is not a customer or not using Oracle. If you are a retailer, hospitality or any other sector for that manner, you would be stupid to use a solution from Oracle after this.
They knew they were breached, knew their customers were at risk of intrusion by means not requiring exploitation (hackers had account and passwords for remote login to customer networks, bypassing any security products those retailers and hotels have paid millions for), fixed themselves, and THEN at their convenience, decided to quietly tell their customers but did not arm them with the hacker signatures needed to protect themselves or even search for previous access so they could provide responsible disclosure to states, customers, card brands and potentially get additional fines because of delay.
Is Oracle going to have to testify in front of Congress like Target did? Is the president going to make comment that tech companies need to notify customers faster? Or, since they are not a retailer, everything goes silent until the next time Home Depot is breached?
Don’t people go to jail for stuff like this? Witholding information on related to an active crime…actually multiple crimes to their customers and their consumers? I have heard nothing about law enforcement involvement (decline comment due to active law enforcement investigation), this has nothing to do with national security.
Where is the FBI? Unless Hillary Clinton is involved with Oracle somehow or on their board, then this is would be a waste of time
No one is responsible for anything anymore.
No one will hold adobe’s feet to fire and make them pay for all the damages they knowingly create. Who will hold Microsoft, or Sony, or HP, or Oracle responsible for this or anything they do? What entity (public or private) represents the end of the road for the destruction, criminal activity, malice, and fraud that take place as a direct result of what these companies do? that’s not to mention the never-ending levels of grief, frustration, and anxiety that gets created among the general populous.
The truth is, most people look at these companies and see nothing wrong at all. Most people will be more inclined to dismiss all these little issues as hickups just because of the idea that we all need them so much. The average person will go to Oracle and get updates to their software instead of removing it.
We all know Flash is an issues but no one wants to get rid of it or hold Adobe responsible for anything more than updates to it.
“Don’t people go to jail for stuff like this? Witholding information on related to an active crime…actually multiple crimes to their customers and their consumers?”
Yes, but who or what will press charges?
“No one is responsible for anything anymore.”
You took the words right outta my mouth.
Good Luck in finding that hotel. Micros, who owns Fidelio / Opera is the most widely deployed Hotel PMS (Property management syste) on the globe. Marriott, Hilton, and god knows who else. MICROS POS is also the 800 pound gorilla in the POS space.
Just more proof that if you don’t try to make every debit or credit payment using a tokenized set-up* like Apple Pay or its competitors, you are setting yourself up for headaches.
*With device unique card numbers working with an automatically generated, automatically entered, single-use PIN code.
I don’t know nuttin’ about Apple Pay, however I just want to say that for one particularly sensitive web site I use, I’ve got a little thingy on my keyring that I have to press a button on each time I’m gonna log in, and this thingy gives me a seeming random (but cryptographically generated) six-digit code that I have to punch in in order to log in.
I believe that systems based on a password *and* a code from this pocket crypto device are are fundamentally very secure. I *am* aware, thank to Brian, that there was at least one occasion where a big batch of these devices was in fact compromised, but my hope that that that was a lesson learned, and that it won’t happen again.
Bottom line: I wish to god that my credit card company would at least offer me the option of obtaining one of those pocket crypto devices to go with my credit card, you know, so that the card number, by itself (and even with the CVV) just wouldn’t work without an associated one-time magic crypto cookie. But they DON’T offer that, even as an option for paranoid customers like me, and as far as I know, *no* credit card companies do. This is a cryin’ shame. I guess I need to talk to my congressman about this, cuz the card companies, left to their own devices, apparently won’t ever offer this, even as an option, ever. I guess they are worried that even offering the option will scare some people and make the populace just question the security of credit cards even more than they already do.
I keep hoping that the credit card industry will get a big wake-up call on security. Maybe this Oracle thing is it, but I doubt it. They… the credit card companies… are in denial.
My sense is that the credit card companies don’t care: all they ever say when your card is frauded is: don’t worry about it you’re not liable for the theft, here’s the stolen money put back on to your card.
Meanwhile do you REALLY think they just eat the costs of fraud? I highly doubt it and would really enjoy seeing all the ways in which they recoup them along with how much of that affects cardholders in indirect ways.
Once one has seen that the lack of action would probably start to make sense, would be my guess.
Ron,
Most credit card companies have some form of 2-factor authentication. Not all have the hardware devices that you use (I use that device myself for EBAY and PAYPAL), but they usually have some form of additional authentication.
My credit card website asks for a password. After that is entered correctly, I am prompted to send a code to either my email address or phone number. If either of those things are compromised, then the 2nd authentication is no good. But I think this extra step will deter at least some crooks.
Maybe your credit card company has something like this (single-use code sent to email or phone)? Probably not as good as a hardware device with a one-time code that keeps changing, but much better than no secondary authentication.
That little 6 digit generated key is pretty cool, but I remember RSA’s SecurID being hacked in 2011 and RSA replacing all of the SecurIds then in the field, so nothing is completely foolproof.
Trump. Loundring russian criminas money its know alllready! So its simple hand wash hands. …even you look russian site verified.cm mn now you see alot work related with usa so usa is main catders fraud country its easy to see
I’m wondering if we will ever hear about the industry (banks, credit unions, card networks, retailers vs Oracle) class action against Oracle.
Another day, another “we value your custom, we recommend changing your passwords, move along, nothing to see here, pay no attention to the man behind the (iron) curtain”…
Is it that they’re afraid of giving lawyers ammunition to sue? The whole hiding what went wrong thing and wrapping what explanations they do offer in condescension and BS is downright irritating.
How did it happen?
Have they mitigated how it happened?
What are they doing to ensure it doesn’t happen again?
Unbreakable, Can’t break in. We remember nothing.
A bit obscure so here is a link to securityfocus.com/news/309
Thanks kopecky! Good link to the past…looks like Mr Ellison still uses similar advertising executives.
I wonder how hard the perpetrators laugh, when they read the comments of outrage and futility. Let’s step up our game and respond to the breach with better protocols, systems and monitoring processes. Plastic replaced paper for a reason. Digital currency will substantive replace plastic. Rather than “move on” let’s advance.
The only way to win is to not play.
The more money that the general population gives to companies, the more of that money goes to help grow the bank accounts of the bad guys. If you must patronize these companies, use cash.
It is better to NOT have Java installed at all than to update it. It’s the same with Flash, ActiveX, and even IE. You can have access to the Playstation Network if you want it. Just know that it does come with certain risks. Just like Steam, Facebook, Twitter, Windows, Itunes, and HP computers.
MySpace failed because barely anyone uses it anymore. The same thing could happen to Oracle if people would just stop using their software. The thing is….that can’t happen because very few people in this world seem to care at all for learning much about computers. It has all become someone else’s responsibility.
It does not matter if your Trump Tower, Hilton, or anyone else. The thinking put to it is “I’m in the hotel business….what do I know from computers? That’s what I pay that other company for.” But, It’s exactly the same thing for most people in their living room (or where ever) with their desktop, laptop, tablet, or phone. It’s exactly the same when it’s about spreadsheets, social media, and family photo albums.
There are reasons why so much of this stuff is ‘free to use’.
There is no lawsuit that will fix any of this. The only way to fix these things is to not use any of it. If you don’t trust non-chipped card readers, then don’t patronize business’s that that are swipe-only. If you don’t like what’s on tv, then change the channel, turn it off, or don’t buy that new tv. Quit complaining about your computer getting infected through Flash or Java….get rid of it and stop going to websites that require it.
“Digital currency will substantive replace plastic.”
If true, then God help us all!
http://thebea.st/1XoWcq7
Oracle appears to have broken California’s requirements [*] for reporting data breaches.
In Oracle’s defense, their “POS system” might have been designed to comply with a vernacular definition. [ http://www.urbandictionary.com/define.php?term=pos ].
[*] http://www.bna.com/new-california-data-n57982067883/
https://oag.ca.gov/ecrime/databreach/reporting
Actually, it sounds like Krebs might have more to fear from the lawyers for antagonized corporations than the crooks. It also sounds as if consumers are paying inflated prices to cover corporate losses from such breaches, minimizing the motivation to protect consumers. Just like they do for oil spills: insure it, don’t fix it,
Even worse in the case of oil spills, take the hit, pay the big fines, penalties and remediation costs, and then (as in the case of BP) deduct a large portion of it from your taxes. It’s the new traffic ticket with a get out of jail free card.
I suspect Richard should have said Oracle rather than Krebs in his first sentence above.
You’re right, the sentence allows substitution of “Oracle” for Krebs in the sense their customer corporations might sue Oracle. However I did mean Krebs because if he exposes the poor corporate response to the hacking crisis their lawyers will assail him for slander to silence the criticism. Of course the corporations deserve to have their performance exposed but then the old saw of “kill the messenger” comes into play.
Krebs has experienced assaults from the crooks, but in my view, corporate lawyers with unlimited resources can bury you with paperwork, put you out of business and smear your name.
Krebs is my favorite security site, especially as a consumer caught up in the Home Depot hack, and I wish him all the luck in exposing corporate misdeeds that allow this hacking crisis to perpetuate. I’ll try to make my thoughts clearer in the future. Thanks for the comment.
You should stop quoting Alex Holden – everyone sensible in InfoSec knows he is a self-promoter and has very little credibility.
Thomas, say what you like about Alex, but he has access to some pretty amazing cybercrime intel on a regular and reliable basis. He’s been that way since I met him at Defcon in 2006 or 2007, I can’t recall which.
How much longer will this take up so much talent and energy? POS account data is useless with EMV transactions. Fall-back to mag transactions (bypassing EMV cryptogram check) should be rare and a definite red flag to investigate. This is a very easy crime of opportunity (with apparently big payouts). Why doesn’t the banking/payment industry finish the EMV migration already?
Emver,
EMV is not the full answer. Full card data is still in the clear with EMV. Malware can still collect it during the process. EMV does NOT include encryption. End to End Encryption with Tokenization is a vital compliment to EMV. The industry has been slow and poor about educating merchants about the priorities and the components of security and compliance.
The delay is because EMVCo did not prime the ecosystem for the change. Poor education, little to no funding for the companies responsible for the development and implementation. The only incentive was the stick to merchants to get the liability shift off their back.
As of two weeks ago, high level sources at the largest card brand told merchants, you should never have tried to implement the full EMV standard, implement “Quick Chip” (first implementation over the last few weeks). REALLY…the liability shift happened in October of last year….
Frustrated beyond belief. As mad as I am at the card brands, I am more frustrated that society tolerates criminals at all levels profiting on the backs of hard working people. Don’t kid yourselves, we all pay for crime and fraud.
Moronic!
It’s 2016 and POS systems are still ruinning Windoze, rather than, say, Linix, or say, picoBSD.
The Oracle advice is to scan your whole network for evil versions of C:\ProgramData\Mozilla\svchost.exe so obviously all of these moronic devices that have been hacked are running Windoze.
It’s almost as if nobody knew that Windoze has security problems.
Heaven save us from this kind of abject idiocy!
Why does this s**t happen time and time again? It’s easy to blame the evil Russian hackers, or Microsoft, but if you leave your shiny new bicycle in the middle of a public park, go for a walk, and then come back to find its not there anymore, whose fault is that?
Oracle is just another corporation whose middle managers decided to cheapskate the whole development process by only hiring cheap 20-somethings who had only ever learned Visual Basic, or some other such MS abomination, and who were utterly incapable of writing a single line of code, let alone being productive, if they were dropped down into a Linix or UNIX development environment. These middle managers could have spent a little bit more and hired people flexible enough to be able to do productive work in a UNIX/Linux environment, but they decided not to, probably in a (now failed) effort to maximize their own Christimas bonuses.
We’ve had computers for more than 50 years now, and the Internet for more than 30. People *have* learned some good rules of thumb about how to develop secure system over all this time. And the rule #1 is simple, straightforward, and known to *everyone* in the security field: DON’T USE WINDOZE!
Whenever I go to my doctor’s office these days, he immediately starts tap-tap-tapping on a keyboard that’s hooked up to the “HIPPA compliant” Windoze system that is present in every exam room. If I wasn’t sick already when I get there to see him, I am by the time I leave. I am beyond disgusted that everybody in this practice is under the delusion that my medical records are actually safe on this network. They aren’t. A good Russian 15 year old could probably pop the whole network in under a minute.
ATMs, voting machines, the list goes on and on. All running Windoze, the most insecure operating system ever devised by the mind of man. And nobody even bothers to apologize for it, for for using it anymore! All you can do is shake your head and hope that the human species stops being so effing dumb someday.
It’s less about the flavor of OS but the security (of lack of) practices they employ. Poorly coded and maintained software requiring elevated privileges to operate will leave any OS vulnerable.
The Linux, Unix flavor is not necessarily safer and all have had their fair share of hacks against them, but the administration tends to be from more experienced admins with more discipline ie: never operate a system as root, unheard of, yet windows admins do that all the time. The ease of use with windows systems tends to make any wanabe admin capable of managing and maintaining a network, and in retail more often than not with the low budgets and training you end up with admins way out of their league and ill equipped to protect their own network.
“Poorly coded and maintained software requiring elevated privileges to operate will leave any OS vulnerable.”
You mean like when a smartphone asks for wifi/gps data when using apps that can’t possibly need it or is simply not needed?
The Operating System would not have mattered, in fact MS Windows is a competitor for Oracle which has a Linux distro. What matters is where the money is. As long as the money is there, people will find ways of obtaining it.
Not only the machines are running windows. The story mentions some files left on Oracle’s servers (that were breached using a exploit “the file-upload function”) as ending on with aspx… so Oracle is using Microsoft’s buggy websever software? for such a critical business! Holly cow!
Nothing Learned?
It makes me sad as it is at least the second greater breach where Micros is involved. Some years ago their name (Micros Fidelio) was combined with a big breach at hotels & chains causing a lot of work for the prevention teams. Like the recent Trump-breach another example for profit against security…..
Me thinks Oracle is to big to fail.
I think we have all heard that before…
“My source said that in mid-July 2016 Oracle sent out an email alert to employees of its hospitality division that they had to re-image their laptops without backing anything up.”
“All of the files and software that were on an employee’s computer were deleted, which was crippling to business operations,” my source recalled. “Project management lost all their schedules, deployment teams lost all the software that they use to install on customer sites. Oracle did not tell the employees in this email that they got hacked but just to re-image everything with no backups. It seems as if Oracle did a pretty good job sweeping this incident under the rug.”
If proven true, this is by far the most profoundly disturbing aspect of this breach. There is no way they fully understood this incident at the time these instructions were given. This is simply destruction of evidence while vastly amplifying the damage / costs. It would have been very do-able to overnight identical blank drives with instructions on how to remove the old drive, label it, turn it over to local IT staff (with custody form), and replace/re-image. That way, critical files only stored locally (not that this ever happens in organizations) could be recovered later, and more important, the various twists and turns a normal investigation takes could be followed up on from that hard drive evidence which has now been destroyed.
As bad as the breach is, it is *this* behavior that should have top officers in the company doing hard time. Until that happens at the highest levels of organizations (commercial and political), nothing will change. The near certainty that nothing substantial will happen to those responsible just reinforces how far down the road to oligarchy / tyranny vs. the rule of law we have devolved as a nation.
A poor person stealing $1000 from a 7-11 faces years of prison. The top officers at Oracle responsible for everything from years of crappy security budget/policies to the willful destruction of evidence which will likely steal $1,000 millions of times over from investors’ and employees’ pockets will be rewarded with their golden parachutes and go elsewhere (probably politics) to continue their unrepentant behavior.
I doubt that’s why they did it. More likely they were trying to get rid of any pieces of spyware/malware installed on their computers. But did it in a way that they didn’t tell any employees that’s what was happening, which is silly. Like if I got that kinda email and I didn’t know why, I might well secretly keep some backups so I wouldn’t lose all my work from prior years… and thus it might re-infect me.
What surprises me of this entire situation is the lack of mass media coverage. Nothing on ABC, NBC, Reuters, CBS, local TV news, etc. No mass public outcry. Perhaps someone has decided it’s “too complicated” for mere mortals (ordinary people) to understand? I am a simpleton when it comes to modern cyber-security. However, I believe I understood the ramifications early on with Brian’s first post concerning this situation. Consider Oracle’s direct customers, and those firms customers and then the public, in descending order, in essence all relying upon the soundness of Oracle’s software and practices. The end number of accounts that could be directly or indirectly effected is massive.
So, Why no hoopla nor headlines? Is this the first incursion or have there been others previous? We know this software has been around in various fashion for about the past 16 years.
Yes, too complicated is one reason. Also I consider this is a “middleware” provider. The news can’t say “wendys breached so watch out if you shopped there”. It’s higher up on the pyramid, more abstracted so it can’t be directly linked to XX number of millions of records yet. It’s not something that’s easy for the news to summarize in 30 seconds with direct known consequences. Plus Oracle is denying it, so the news doesn’t have statements from them to point at yet either. Brian is often on the leading edge of stuff like this news, and sometimes it doesn’t hit he mainstream right away.
Once it settles out, especially if there’s ties to some of the other breaches, I predict there may be some more coverage in a couple months. Then again, there might not be.
To most consumers, there is little downside. You get a new card, no liability for the fraud. The only nuisance is if you have automatic payments set up. So for consumers these stories are a snooze.
My own theory is that vendors who sell stuff that can be easily monetized are the ones that will convert to chip the first, as they are the most likely targets for fraudulent purchase, and thus they have the greatest liability. Places like BestBuy, or the Apple store, for example. But I also notice that liquor stores and stores that sell car/truck parts have also installed chip readers.
Micros was compromised before Oracle bought them.
There’s only two kinds of organizations in the world – those that know they’ve been broken into, and those that don’t.
Looks like the Forbes.com site is redirecting to a Zeus trojan. https://urlquery.net/report.php?id=1470110753619
This is an Oracle, people. She’s a priestess who breathes volcanic fumes and then issues profound pronouncements. If you want her to issue pronouncements for you, you better bring dinner, in the form of some grade-A livestock to slaughter. If you don’t understand her, that’s your problem, not hers.
the information we would need is the extend of the breach. How many card were stolen???
all of them
Thanks for those IOCs Brian..!
Frank
Micros has more that 50% of the POS in the WORLD. That’s a big pwn worthy of the group.