A New Mexico man is facing federal hacking charges for allegedly using the now defunct attack-for-hire service vDOS to launch damaging digital assaults aimed at knocking his former employer’s Web site offline. Prosecutors were able to bring the case in part because vDOS got massively hacked last year, and its customer database of payments and targets leaked to this author and to the FBI.
Prosecutors in Minnesota have charged John Kelsey Gammell, 46, with using vDOS and other online attack services to hurl a year’s worth of attack traffic at the Web sites associated with Washburn Computer Group, a Minnesota-based company where Gammell used to work.
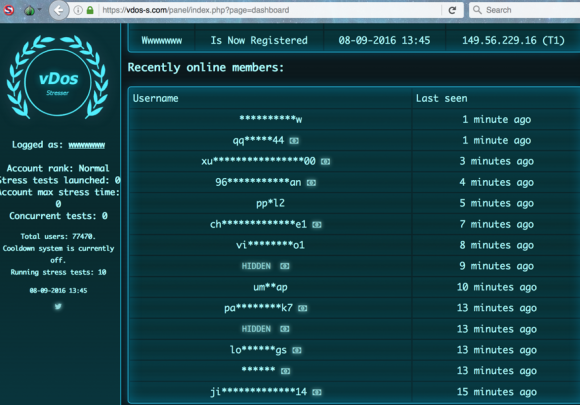
vDOS as it existed on Sept. 8, 2016.
vDOS existed for nearly four years, and was known as one of the most powerful and effective pay-to-play tools for launching distributed denial-of-service (DDoS) attacks. The vDOS owners used a variety of methods to power their service, including at least one massive botnet consisting of tens of thousands of hacked Internet of Things (IoT) devices, such as compromised Internet routers and security cameras. vDOS also was used in numerous DDoS attacks against this site.
Investigators allege that although Gammell used various methods to hide his identity, email addresses traced back to him were found in the hacked user and target databases from vDOS.
More importantly, prosecutors say, someone began taunting Washburn via Yahoo and Gmail messages while the attacks were underway, asking how everything was going at the company and whether the IT department needed any help.
“Also attached to this second email was an image of a mouse laughing,” the Justice Department indictment (PDF) alleges. “Grand jury subpoenas for subscriber information were subsequently served on Google…and Yahoo. Analysis of the results showed information connecting both accounts to an individual named John Gammell. Both email addresses were created using the cell phone number 612-205-8609.”
The complaint notes that the government subpoenaed AT&T for subscriber information and traced that back to Gammell as well, but phone number also is currently listed as the recovery number for a Facebook account tied to John K. Gammell.
That Facebook account features numerous references to the hacker collective known as Anonymous. This is notable because according to the government Gammell used two different accounts at vDOS: One named “AnonCunnilingus” and another called “anonrooster.” The email addresses this user supplied when signing up at vDOS (jkgammell@gmail.com and jkgammell@icloud.com) include other addresses quite clearly tied to multiple accounts for John K. Gammell.
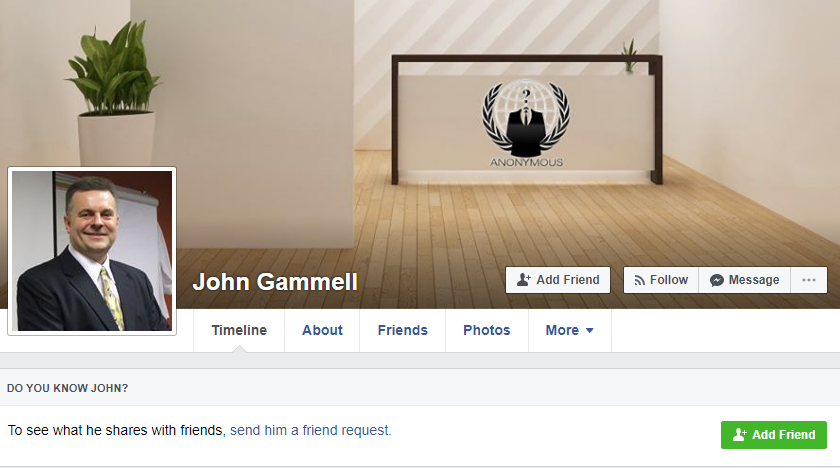
John K. Gammell’s Facebook account.
Below is a snippet from a customer service ticket that the AnonCunnilingus account filed in Aug. 2015
“Dear Colleagues, this is Mr. Cunnilingus. You underestimate your capabilities. Contrary to your statement of “Notice!” It appears from our review that you are trying to stress test a DDoS protected host, vDOS stresser is not capable of taking DDoS protected hosts down which means you will not be able to drop this hosting using vDOS stresser…As they do not have my consent to use my internet, after their site being down for two days, they changed their IP and used rackspace DDoS mitigation and must now be removed from cyberspace. Verified by downbyeveryone. We will do much business. Thank you for your outstanding product 🙂 We Are Anonymous USA.”
Gammell has pleaded not guilty to the charges. He has not responded to requests for comment. The indictment states that Gammell allegedly attacked at least a half-dozen other companies over a year-long period between mid-2015 and July 2016, including several banks and two other companies at which he either previously worked or with whom he’d interviewed for a job.
In late July 2016, an anonymous security researcher reached out to KrebsOnSecurity to share a copy of the vDOS databases. The databases showed that vDOS made more than $600,000 in just two of the four years it was in operation, helping to launch more than 150,000 DDoS attacks.
Since then, two alleged co-owners of vDOS — two 19-year-old Israeli men — have been arrested and charged with operating an attack-for-hire service. Aside from Gammell’s case, I am not aware of any other public cases involving the prosecution of people who allegedly used vDOS to conduct attacks.
But that will hopefully change soon, as there are countless clues about the identities of other high-volume vDOS users and their targets. Identifying the perpetrators in those cases should not be difficult because at some point vDOS stopped allowing users to log in to the service using a VPN, meaning many users likely logged into vDOS using an Internet address that can be traced back to them either via a home Internet or wireless account.
According to a review of the vDOS database, both accounts allegedly tied to Gammell were banned by vDOS administrators — either because he shared his vDOS username and password with another person, or because he logged on to the accounts with a VPN. Here’s a copy of a notice vDOS sent to AnonCunnilingus on July 28, 2015:
“Dear AnonCunnilingus , We have recently reviewed your account activity, and determined that you are in violation of vDos’s Terms of Service, It appears from our review that you have shared your account (or accessed vDos stresser from several locations and platforms) which is against our Terms of Services. Please refer to the following logs and terms:\n- AnonCunnilingus logged in using the following IPs: 64.145.76.110 (US), 85.10.210.199 (XX) date: 06-08-2015 18:05\n\n- 8) You are not allowed to access vDos stresser using a VPN/VPS/Proxy/RDP/Server Tunnelling and such.\n- 3) You may not share your account, if you will, your account will be closed without a warning or a refund!”
What’s most likely limiting prosecutors from pursuing more vDOS users is a lack of DDoS victims coming forward. In an advisory issued last month, the FBI urged DDoS victims to report the attacks.
The FBI requests DDoS victims contact their local FBI field office and/or file a complaint with the Internet Crime Complaint Center (IC3), regardless of dollar loss or timing of incident. Field office contacts can be identified at www.fbi.gov/contact-us/field. IC3 complaints should be filed at www.ic3.govwith the following details (if applicable):
- Traffic protocol used by the DDoS (DNS, NTP, SYN flood, etc)
- Attempt to preserve netflow and/or packet capture of the attack
- Any extortion/threats pertaining to the DDoS attack
- Save any such correspondence in its original, unforwarded format
- Victim information
- Overall losses associated with the DDoS attack
- If a ransom associated with the attack was paid, provide transaction details, the subject’s email address, and/or crypto currency wallet address
- Victim impact statement (e.g., impacted services/operations)
- IP addresses used in the DDoS attack
Related reading:




I just checked out his FB page, funny how he claims anonymous but is a Trump supporter ..LOL
I know Anonymous split from 4chan long ago, but 4chan pretty heavily supported Trump during the election. What I find more amusing is that the thinks hiring a DDoS service makes him a 1337 hacker.
It was 9gag all along. Do not toy with him, else you will be h4x0r3d h4h4h4
9gag wishes, it was ebaumsworld.
The IP address 85.10.210.199 is a Tor exit node. So I very much assume that his account wasn’t shared, he simply accessed it via Tor which got him banned.
He is really good at soldering, too.
http://www.solderingtraining.com/
https://www.youtube.com/user/jkgamm041/videos
That’s actually very impressive soldering. At first, I thought you said “Soldiering”. Like Army Soldiers, Weekend Warrior stuff. Oh well. Smart guy but acted like shunned girlfriend. Accept your firing and/or rejections and move on. Christ.
“shunned girlfriend”?
C’mon man.
Okay…he acted more like a “dumped and humiliated ex-girlfriend who decided to get a little high-tech payback instead of keying the side of his vehicle” — close enough?
He didn’t get fired, he actually resigned, maybe you should read the indictment.
John Kelsey Gammell =/= Walter White…
Do these takedowns of places offering the DDOS “service” provide any opportunity to discover, and disable, the underlying botnets that they use?
Just finished reading the indictment. Either he was setup by someone that carefully planned everything or he’s a fucking idiot.
Being that the most simple explanation is most often the correct one, my money is on him just being a nitwit.
I agree with Dave, which is also supported by Matt’s observations.
Can you explain more what he did that made it easy to follow his trail? I can see that using Gmail and Yahoo were poor choices as they are US email providers and are required to provide user information when subpoenas are issued. Using the same cell phone for all accounts was also a bad idea. What did I miss?
That is in reality extremely amazing patching. At in the first place, I thought you said “Soldiering”. Like Army Soldiers, Weekend Warrior stuff. Such is life. Keen person however acted like avoided sweetheart. Acknowledge your terminating and additionally dismissals and proceed onward. Christ.
A few errors here: hacking => hacked, such => such as
and missing space in http://www.ic3.govwith
AnonCunnilingus ! with that anonymous name he should have been caught
Was attempt comment on reaper post as my network and devices are spreading can’t get any helpvdue to the havoc it plays taken over my domains on 1,and 1 too
paypal email to bootyou.net
email=bmznn1@outlook.com
facebook linked to email
id=100022305553470
MAKE SURE THE FEDS KNOW.
For someone who thought he was a pro, he made a lot of rookie mistakes….
GREETINGS EVERYONE, are you looking for a LEGIT and Trustworthy HACKERS with 100% Guarantee and you want to get your job done urgently withing one Hour or you are face with delay and unnecessary excuses and error on your job?. Then Worry no more because easyhackingguru@gmail.com are the Best Bet in any hacking Services. They are ready to render and attend to your job with swift response and No delay at all.
Their services are outlined as follows:
. LONG TIME LOAN GIVING
. PROFESSIONAL in SCHOOL GRADE hanging
. WHATSAPP Hack
. FACBOOK hack
. PROFESSIONAL in any BANK ACCOUNTS TRANSFER
. TWITTERS hack
. EMAIL,YAHOOMAIL and HOTMAIL ACCOUNTS hack
. WEBSITE CRASHED hack
. SERVER CRASHED hack
. SALES OF SPYWARE and KEYLOGGER SOFTWARE
. RETRIVAL OF LOST FILES and DOCUMENTS
. ERASE and EXPUNGE of CRIMINAL RECORDS
. DATABASE hack
. SALES of ATM CARDS in WHITE
. SKYPE hack
. PAYPAL hack
. DROPBOX ACCOUNT hack and Lots more……….
CONTACT: their services at easyhackingguru@gmail.com and you will be glad you did
whatsApp contact- +12182085613
I wonder how serious the FBI is about wanting reports this time?
I was part of a DDoS attack back in Nov. 2000, when my home-brewed and unpatched DNS server ended up being part of a DDoS campaign against the government of Brazil. I called the FBI and had to explain what the Internet was to the dispatcher on the phone. She didn’t believe me.
In 2011, somebody tried to charge more than $14k against one of my credit cards. The US Bank Fraud department and I chased down every single fraudulent transaction and even talked to the people in Florida at one store where the fraudsters tried to run up my credit card. I packaged it all up for the FBI and…nothing.
I have a hunch the FBI doesn’t have any DDoS attack reports now because they’ve earned a reputation for not following up.
Maybe that’s why the link http://www.fbi.gov/contact-us/field provided in Krebs’ blog says “Page not found”.
Our tax dollars at work. 🙂
I have noticed you don’t monetize your website, don’t waste your
traffic, you can earn extra cash every month because you’ve got high quality content.
If you want to know how to make extra bucks, search for: Boorfe’s tips best adsense alternative
The article starts by stating that former employee attacks the website of former employer. There are many cases of disgruntled employees taking measures of vengeance against their former employers. In an increasingly sophisticated and overwhelming IT world, it is important to work on building good human relations in addition to implementing technological security measures for organizational IT infrastructure. There are far too many ways to breach security systems, human beings should not be forgotten at the expense of hardware and software.
Your full loyalty lies with the betrayer of your trust. Initially, I thought I was just feeling insecure when my husband would just be on his phone at odd hours, until I decided to take a chance to know, knowing is better than self doubts and it was exactly what happened when I employed the services of this particular group I came across by chance to help check his phone out intoto. Now I know when he’s telling the truth and how to curtail him, I think it is not a drastic step if it’ll make you feel better. My life got better, I stopped using my precious time to bother about his indiscretions and channelled my energy positively. Their services includes: phone calls, messages, contacts, social media(viber, whatsapp,facebook,kik e.t.c), emails, any kind of manipulations ,Geo location tracking, all other hacking and web hacking issues.
You can reach them via:
Nullantrax2017@outlook.com