Authorities in the United States this week brought criminal hacking charges against three men as part of an unprecedented, international takedown targeting 15 different “booter” or “stresser” sites — attack-for-hire services that helped paying customers launch tens of thousands of digital sieges capable of knocking Web sites and entire network providers offline.
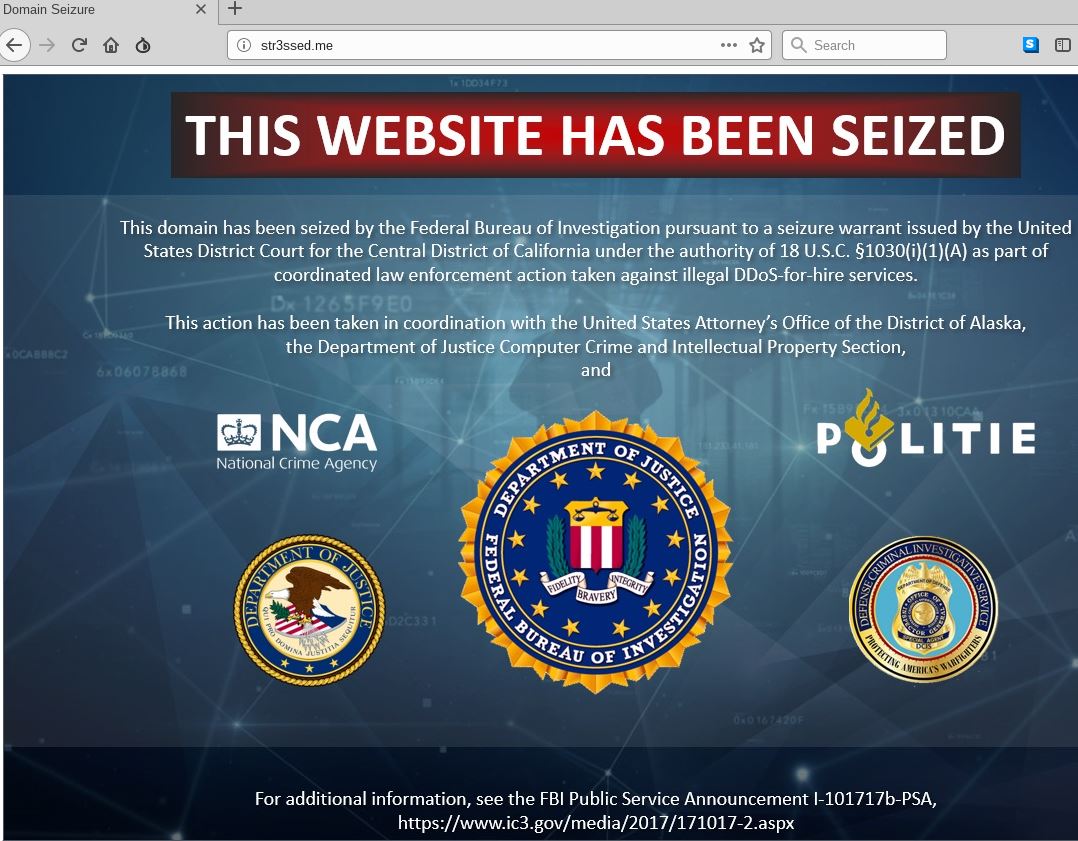
The seizure notice appearing on the homepage this week of more than a dozen popular “booter” or “stresser” DDoS-for-hire Web sites.
As of Thursday morning, a seizure notice featuring the seals of the U.S. Justice Department, FBI and other law enforcement agencies appeared on the booter sites, including:
anonsecurityteam[.]com
booter[.]ninja
bullstresser[.]net
critical-boot[.]com
defcon[.]pro
defianceprotocol[.]com
downthem[.]org
layer7-stresser[.]xyz
netstress[.]org
quantumstress[.]net
ragebooter[.]com
request[.]rip
str3ssed[.]me
torsecurityteam[.]org
vbooter[.]org
Booter sites are dangerous because they help lower the barriers to cybercrime, allowing even complete novices to launch sophisticated and crippling attacks with the click of a button.
Cameron Schroeder, assistant U.S. attorney for the Central District of California, called this week’s action the largest simultaneous seizure of booter service domains ever.
“This is the biggest action U.S. law enforcement has taken against booter services, and we’re doing this in cooperation with a large number of industry and foreign law enforcement partners,” Schroeder said.
Booter services are typically advertised through a variety of methods, including Dark Web forums, chat platforms and even youtube.com. They accept payment via PayPal, Google Wallet, and/or cryptocurrencies, and subscriptions can range in price from just a few dollars to several hundred per month. The services are priced according to the volume of traffic to be hurled at the target, the duration of each attack, and the number of concurrent attacks allowed.
Purveyors of stressers and booters claim they are not responsible for how customers use their services, and that they aren’t breaking the law because — like most security tools — stresser services can be used for good or bad purposes. For example, all of the above-mentioned booter sites contained wordy “terms of use” agreements that required customers to agree they will only stress-test their own networks — and that they won’t use the service to attack others.
But experts say today’s announcement shreds that virtual fig leaf, and marks several important strategic shifts in how authorities intend to prosecute booter service operators going forward.
“This action is predicated on the fact that running a booter service itself is illegal,” said Allison Nixon, director of security research at Flashpoint, a security firm based in New York City. “That’s a slightly different legal argument than has been made in the past against other booter owners.”
For one thing, the booter services targeted in this takedown advertised the ability to “resolve” or determine the true Internet address of a target. This is especially useful for customers seeking to harm targets whose real address is hidden behind mitigation services like Cloudflare (ironically, the same provider used by some of these booter services to withstand attacks by competing booter services).
Some resolvers also allowed customers to determine the Internet address of a target using nothing more than the target’s Skype username.
“You don’t need to use a Skype resolver just to attack yourself,” assistant U.S. Attorney Schroeder said. “Clearly, the people running these booter services know their services are being used not by people targeting their own infrastructure, and have built in capabilities that specifically allow customers to attack others.”
Another important distinction between this week’s coordinated action and past booter site takedowns was that the government actually tested each service it dismantled to validate claims about attack firepower and to learn more about how each service conducted assaults.
In a complaint unsealed today, the Justice Department said that although FBI agents identified at least 60 different booter services operating between June and December 2018, they discovered not all were fully operational and capable of launching attacks. Hence, the 15 services seized this week represent those that the government was able to use to conduct successful, high-volume attacks against their own test sites.
“This is intended to send a very clear message to all booter operators that they’re not going to be allowed to operate openly anymore,” Nixon said. “The message is that if you’re running a DDoS-for-hire service that can attack an Internet address in such a way that the FBI can purchase an attack against their own test servers, you’re probably going to get in trouble.”
DOWN THEM ALL
Charged in a Los Angeles federal court this week were the alleged operators of “Downthem” — a booter service the government says helped some 2,000 customers launch debilitating digital assaults at more than 200,000 targets, including many government, banking, university and gaming Web sites.
Prosecutors say that in addition to running and marketing Downthem, defendants Matthew Gatrel from St. Charles, Ill., and Juan Martinez of Pasadena, Calif. sold huge, continuously updated lists of Internet addresses tied to devices that could be used by other booter services to make attacks far more powerful and effective.
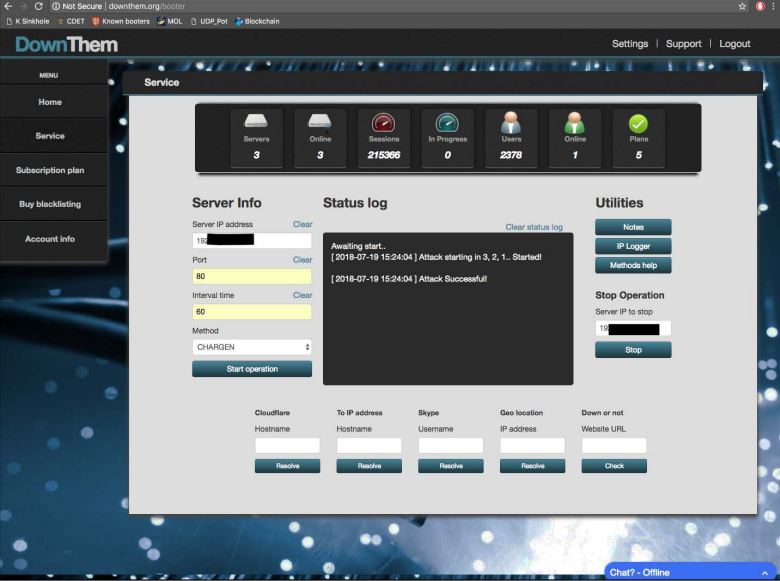
The user interface for Downthem[.]org, one of 15 booter sites seized by the feds today.
Booter and stresser services let customers pick from among a variety of attack methods, but almost universally the most powerful of these methods involves what’s known as a “reflective amplification attack.” In such assaults, the perpetrators leverage unmanaged Domain Name Servers (DNS) or other devices on the Web to create huge traffic floods.
Ideally, DNS servers only provide services to machines within a trusted domain — such as translating an Internet address from a series of numbers into a domain name, like example.com. But DNS reflection attacks rely on consumer and business routers and other devices equipped with DNS servers that are (mis)configured to accept queries from anywhere on the Web.
Attackers can send spoofed DNS queries to these DNS servers, forging the request so that it appears to come from the target’s network. That way, when the DNS servers respond, they reply to the spoofed (target) address.
The bad guys also can amplify a reflective attack by crafting DNS queries so that the responses are much bigger than the requests. For example, an attacker could compose a DNS request of less than 100 bytes, prompting a response that is 60-70 times as large. This “amplification” effect is especially pronounced if the perpetrators query dozens of DNS servers with these spoofed requests simultaneously.
The government alleges that Gatrel and Martinez constantly scanned the Internet for these misconfigured devices, and then sold lists of Internet addresses tied to these devices to other booter service operators.
Schroeder said the government is arguing that the use of these third-party servers in reflective amplification attacks can be prosecuted under existing wire fraud and computer trespass laws.
“Certainly [booter service operators] don’t have permission from all of those other devices owners to use the devices and their bandwidth to direct these attacks,” she said. “We look at it as a wire fraud violation because essentially they’re stealing property from upstream providers and using their resources to conduct these attacks. There are also multiple ways we can show this is pretty clearly not lawful under the Computer Fraud and Abuse Act.”
Prosecutors further allege Gatrel resold his booter services to other booter operators, including Quantum Stresser — one of the 15 services seized by the government this week. The alleged operator of that service, Pennsylvania resident David Bukoski, was charged in the District of Alaska this week for aiding and abetting computer intrusions.
Investigators say Bukoski’s booter service was among the longest running services targeted by the FBI, operating since at least 2012. An indictment against Bukoski unsealed this week maintains Quantum Stresser had over 80,000 customer subscriptions, and that during 2018 the service was used to conduct over 50,000 actual or attempted attacks targeting people and networks worldwide.
Adam Alexander, assistant U.S. attorney for the District of Alaska, said additional prosecutions against booter service operators will be forthcoming.
“We are becoming more experienced, thanks to the growing expertise and shoe-leather investigative work required to attribute, identify and prosecute individuals responsible for these services,” Alexander said. “Actions like this one demonstrate our capabilities are increasing as well.”
According to the government, the use of booter and stresser services to conduct attacks is punishable under both wire fraud laws and the Computer Fraud and Abuse Act (18 U.S.C. § 1030), and may result in arrest and prosecution; seizure of computers or other electronics; significant prison sentences; a penalty or fine.
Schroeder said the government understands this week’s takedowns aren’t going to solve the booter problem once and for all, and that other booter services will likely spring up in the wake of those dismantled this week. But she said the arrests and seizures have helped build a template that the government can use in tandem with its industry partners to shorten the lifespan of new booter services and to bring those responsible to justice.
“We certainly don’t expect this problem to go away after this,” Schroeder said. “But this is an attempt to build a strategic approach to this problem, to look at it in a more systemic way and deal with it on a much larger scale.”
The Justice Department’s press release about this action is here.
This is a developing story and may be updated throughout the day. Any substantive updates will be noted here with a timestamp.
Update, 2:42 p.m. ET: Added link to DOJ press release.
Update, 7:59 p.m. ET: Added comment from AUSA Adam Alexander.




More script-kiddies locked up and their lives ruined
Good.
And here I thought this was the type of story you wanted to see more of, Sunshine?
“Winning”
Good news for the holidays!
I know this has been brought up before but why does Cloudflare continue to hide behind the shield of claim that they are not responsible for how customers use their services, and that they aren’t breaking the law because — like most security tools — stresser services can be used for good or bad purposes.
It is rather obvious which customers are booter/stresser sites.
@PaulK
I can think of a few reasons,
1) Cloudflare is cooperating with LE authorities to bring down the bad guys, who think they are invulnerable hiding behind the Cloudflare “wall”. Meanwhile the feds are gathering strategic technical information and sufficient evidence to bring down the bad guys when the time is right. The booter boys could actually be indavertently helping the US determine its own weaknesses if subjected to an all out cyberattack from a nation-state adversary.
2) Cloudflare does not want to be required to monitor all their thousands (million+ ?)customers for “improper” and/or illegal activity. That just pulls resources away from the bottom line. They have caved in some instances wrt far right groups, which appears inconsistent, including to CF employees.
or maybe #3
They make money on both ends of the equation. Protecting legit sites from these actors on one end. The other, they take money from these jokers which only drive up demand for more CF services.
Seems it would be trivial for them to find these actors and root them out if they really wanted to.
Hum.
“1) Cloudflare is cooperating with LE authorities to bring down the bad guys, who think they are invulnerable hiding behind the Cloudflare “wall”. Meanwhile the feds are gathering strategic technical information and sufficient evidence to bring down the bad guys… 2) Cloudflare does not want to be required to monitor all their thousands (million+ ?)customers for “improper” and/or illegal activity…”-Quid
Interesting take Quid. Basically Cloudflare is a big honey pot for the Feds?
“..3 They make money on both ends of the equation…” -orion242
That is entirely possible. I don’t know what to make of Cloudflare.
My observation of the disconnect between accurate DNS records-Domain records, and true IPv4 blocks is adding to the “booter” problem.
It appears that certain companies own list of DNS and Domains that don’t match public lists for the average Joe to use. The same goes for IPv4 blocks and accurate ownership lists for the average Joe to use.
There is no solid connection to proper DNS look ups to IP numbers for the average Joe. I don’t know how to solve the problem. It seems to be an worldwide problem with no simple answer.
Cloudflare’s reluctance to pick a side is good business strategy.
Exercising editorial control over content puts a company in the same basket as publishers, meaning they can be held liable for libel and incitement. Libel and tort laws currently give a pass regarding content on “platforms” that don’t edit content.
(Eventually, Facebook, Patreon, and Twitter will be recognized as publishers, instead of platforms. That will be a devastating day for their stock prices, as they become personally responsible for inciting violence and spreading libel.)
It’s also better for a business to provide services to all, rather than discriminate among potential customers. Cloudflare certainly has better ways to manage its revenue stream than to waste money to investigate its users, monitor their content, and get caught in legal battles.
Err, what? First of all, who’s suggesting that they need to exercise editorial control over content? That’s not how most service providers respond to abuse complaints (rather, they just shut down the offending account) – why would that be any different for CloudFlare?
Second, your rationale seems quite similar to posts I used to see on NANAE back in the day, from spammers/spam apologists who insisted that they should be permitted to bombard people with unwanted advertisements because of “frea speach.” If what you say is actually true, then where are all the legal judgements against hosting providers for booting spammers off their networks? Perhaps it has something to do with those clauses that almost all online service providers have in their contracts/TOS/AUP agreements? Ya know, the ones that say “service provider reserves the right to modify or discontinue service at any time, for any reason, at our sole discretion.”
CloudFlare uses the “we’re not a hosting provider” cop-out as their stock excuse for turning a blind eye to all the types of illegal/abusive online activity they facilitate – distributing malware, phishing scams/fraud, websites of terrorist organizations, and garden variety spamvertised websites. Their failure to take responsibility for abuse committed with/enabled by their services is by NO means limited to booter/stresser sites.
Send any kind of abuse complaint to CloudFlare, and the boilerplate auto-reply you get back is practically nothing but weaselly attempts to dodge responsibility for the use of their services. The “we’re not a hosting provider” excuse, which is irrelevant because they clearly ARE acting as hosting providers for the sites using CloudFlare: their servers are the ones that receive the HTTP(s) requests & send back content in response to them. That excuse is just as ridiculous as Telsa trying to claim that their vehicles shouldn’t be as cars, because they don’t have internal combustion engines.
And they follow that up with the “we have no ability to modify the content of sites that we provide service to” – which is also a lazy dodge & a red herring, since there a plenty of situations where a traditional hosting provider may not have access to modify content of sites they host (co-located/dedicated servers that they don’t have root access to). And yet that doesn’t stop actual responsible service providers from appropriately responding to abuse complaints – because if you have the ability to shut down the offending account (or disable it at the network level), then WHY would you need access to modify the content in the FIRST place? Not only is unnecessary, it’s not even a particularly effective way to deal with the issue.
CloudFlare is no different from other large service providers like OVH & NameCheap, who are opposed to spam & other network abuse in official policy – but in actual practice, they will bend over backwards to avoid losing revenue from the spammers & other criminals that they knowingly provide service to. At this point, they show no interest in doing anything about it – unless/until the problem reaches the point where some major browser vendor flags CloudFlare’s entire IP space as “unsafe.”
No mention of what the feds will do with the 80k customer subscriptions of A-holes who hired these services. Methinks a $10,000 fine to each one of them for hiring a criminal to do criminal work. Of course they can let off the 3 people who actually wanted to stress their own sites.
Unfortunately, pragmatically, it isn’t possible to prosecute 80,000 people. It just isn’t There’s aren’t enough lawyers and agents in the entire DoJ to be able to do this. Not even close. Add to that the fact that there may not even be any documents or records available, even after/if the relevant servers were seized, to support such prosecutions. How many account holders never even paid for -any- DDoS? How many account holders -only- paid to “stress test” their own networks? It would be a logistical nightmare to sort this all out, even if it is possible to do at all.
That having been said, yes, the DoJ quite certainly *should* pick out at least a handful of the actual -customers- of these services, and then make examples of them, prosecuting them to the fullest extent of the law. The messages MUST be sent that you DO NOT have a get out of jail free card if you are “only” a customer of one of these services, and that just by being a customer, you also face substantial legal jeopardy.
Domains are siezed. Amazing. Most of them will register new domains like coolstresserbooter.ru and continue their operations.
Honestly i think this is a good thing, as the us can give these skilled minorities a second chance by allowing them to work for them in exchange for no or lesser charge to help better the united states’ cyber security. good work guys 🙂
I don’t think the US Cyber Security program has any need for script kiddies.
Its not just script kiddies running stresser sites, that is a myth. The guys running vDos for example, were trained by the Israeli military.
Since military service is compulsory in Israel… that means they can still be script kiddies and have served minimum years in one of the many, many non-cyber units.
What is wrong with our society that poor innocent waifs are led into such destructive behavior? Computer, just like guns, are horribly evil, irresistibly tempting children to commit a crime. Maybe we should ban all computers, except in the hands of government. Now for an innocent prank, their lives are ruined. After all, couldn’t those 50,000 targeted systems have just hit delete and gotten on with their lives?
/Sarcasm Mode OFF
Sunshine is probably a script kiddie, and now is hiding in his mother’s basement, quivering in fear each time someone knocks on the door.
All but one of these domains use CloudFlare nameservers. The quantumnstress.net has no nameservers, which leads me to believe that you have a typo (there’s a quantumstress.net that uses CloudFlare if you take out the “n”).
I think it’s time for krebsonsecurity to shine its spotlight a bit more on CloudFlare, which it hasn’t done for several years now.
Daniel, I know you are on a crusade but as someone who is part of that list of companies thanked by DOJ today, Cloudflare is doing a lot and have been a vital partner in this fight. All the details will never become public so you may never be convinced.
Thank you Cloudflare you had a huge part in our victory today.
I’m sorry, but I just can’t let this go by. This is such utter horsepoo.
Cloudflare is playing both sides against the middle. Their business model unambiguously thrives and prospers due to the continued existence of the exact type of DDoS attacks and attackers that you now claim that they are helping the Feds to catch. (And by the way, how much are they being PAID by the Feds for their helpfulness? Do you even know? I’ll bet you don’t.)
To even suggest that they are not utterly and completely conflicted is tantamount to suggesting that Donald Trump wasn’t utterly conflicted as he tried to negotiate for a Moscow Trump Tower even as he was running for the Presidency of the United States.
Even leaving aside the whole issue of the aid and comfort they have given and are giving, on a daily basis, to all manner of thieves, crooks, charlatans, and yes, the odd occasional terrorist organization, I have another beef with than, and with you, that goes beyond all this, which is that you guys are all relying on a provably demented model of Internet security in which ONLY those with badges, and/or the few that they allow into their inner circle, like you, do 100% of the work to keep people safe from online criminal and/or terrorist organizations. YOU,
(continued) I’m sorry, but I just can’t let this go by. This is such utter horsepoo.
Cloudflare is playing both sides against the middle. Their business model unambiguously thrives and prospers due to the continued existence of the exact type of DDoS attacks and attackers that you now claim that they are helping the Feds to catch. (And by the way, how much are they being PAID by the Feds for their helpfulness? Do you even know? I’ll bet you don’t.)
To even suggest that they are not utterly and completely conflicted is tantamount to suggesting that Donald Trump wasn’t utterly conflicted as he tried to negotiate for a Moscow Trump Tower even as he was running for the Presidency of the United States.
Even leaving aside the whole issue of the aid and comfort they have given and are giving, on a daily basis, to all manner of thieves, crooks, charlatans, and yes, the odd occasional terrorist organization, I have another beef with than, and with you, that goes beyond all this, which is that you guys are all relying on a provably demented model of Internet security in which ONLY those with badges, and/or the few that they allow into their inner circle, like you, do 100% of the work to keep people safe from online criminal and/or terrorist organizations.
… (continued) YOU SIR ARE AN ELITIST! You completely discount the value and importance of so-called “citizen journalists”, *and* people like Brian Krebs, *and* people like me, who are independent investigators who DO do good work on behalf of the Internet-using public but who DO NOT get to peek behind the Cloudflare curtain, because we don’t happen to have badges.
*IF* Cloudflare wanted, earnestly, to do what it does, i.e. to protect sites from DDoS attacks (and act as a kind of poor-mans CDN) yet still help independent security researchers, at least a little, then they could do the following simple thing as a show of good faith, SO WHY DON’T THEY?
For every web site they are proxying, that is to say for every such domain name, they could take the domain name, then take the corresponding REAL (back end) IP address that it is hosted on, concatenate that IP address with some secret string that only Cloudflare knows, run an SHA hash on the concatenated pair, and then publish or otherwise make available (maybe via a simple WHOIS server) the resulting hash for each domain name they are proxying. That way, at least us folks who DON’T get to peek behind the Cloudflare veil could at least be able to determine for ourselves that, for example, evildomain1.com and evildomain2.com are actually both hosted on the exact same (back end) IP address, even though we would have no way of knowing what that IP address was.
These kinds of correlations have been VITAL to many of the investigations that Brian and others have done over the years, so what is Cloudflare’s excuse for NOT providing this kind of data? The only plausible excuse is that Cloudflare is knowingly, and with malice aforethought, PROTECTING every last minuscule iota of data about their many crooked customers, even from legitimate security researchers. This isn’t about DDoS protection. This is about Cloudflare deliberately hiding the ball. End of story.
That moment when you know the owners of over half the websites in this list…
Like this is a real deterrent… I mean, spending 5 minutes registering another domain and pointing it to their server again will surely stop those script kiddies in their tracks.
Its hard to register a new domain from prison
Maybe you’re unaware that prisoners have access to smartphones through smuggling by their friends or coercion of guards.
They’ve run some pretty big crimes with smartphones. Here’s an example from last month:
https://www.marketwatch.com/story/sextortion-by-prison-inmates-cheats-soldiers-out-of-nearly-600k-prosecutors-say-2018-11-29
Thats still not easy. A script kiddie in a federal penitentiary isnt going to be able to just say hey I want some illegal contraband to commit federal offenses from my cell and then just magically get provided with that cell phone. They’re going to have to work for it, theyre going to have to pay for it, and if the heavies who run things think it will bring any heat on them, or those providing said contraband, they will likely just refuse to provide them what they need. Just because its possible and has happened before does not mean just any old inmate with zero connections can do it.
Don’t be silly. Phones are not just sneaked in by guards and visitors.
Phones get thrown over the wall.
https://www.bbc.com/news/uk-36259746
Phones get brought in on fishing poles.
https://nypost.com/2018/09/26/inmates-busted-reeling-in-contraband-from-jail-windows/
Well… all I can say is RIP RageBooter.net… Regardless of what you guys think. But I’m glad its gone. The owner Alexander Check passed away October 8th of this year… He will be missed by many.
Good luck Brian in all your endeavors.
Kind Regards,
Justin
Justin, is this really you? If so, I’m sorry to hear about your friend Alex.
https://krebsonsecurity.com/2013/05/ragebooter-legit-ddos-service-or-fed-backdoor/
Yea it’s really me.. If you want you can message me on facebook.
What I’m puzzled about is that DNS amplification requires the ability to spoof the source IP address, doesn’t it? This should not be possible in a normal ISP-run network.
So where are these guys getting the machines to send the original DNS packets from? Are they renting them? That sure seems costly. Are they hacking network gear, or specifically machines in unprotected networks? Or is it sufficient to target just the IoT devices and Internet Explorer running at some third-world ISPs without IP spoofing prevention?
Any bozo can drop 5k on a decent router and buy a few super micro 1u servers and enable ip header modification under the vnet settings.
Philipp, it would be nice if ISPs ran egress ACLs as I’m sure you learned in some class, but that’s not reality. ISP configurations are mostly concerned with ease of maintenance, e.g., minimization of expense.
When you send a TCP/IP packet to another server it includes the return address so it knows who to send the data to. Spoofing the return address means the packet reaches the destination and then it sends the data back to the spoofed address instead of your address.
The only real way to defeat this is to configure each network’s edge router, or the edge router at the colo/datacenter, to only accept return addresses from networks that are valid from within that subnet. So if I send an IP to 1.1.1.1 with a return of 9.9.9.9 it could hit the first or second hop and then that router would check the return address for all addresses that are valid behind that router and drop it if it’s not in the list. By and large ISPs don’t do this, although any decent network or systems administrator should do this on the router(s) they control to stop it before it hits the ISP since for them its a trivially simple rule.
The reason providers don’t do this is because every time they add or remove a subnet from a particular site or center they would also need to remember to modify that rule on the router. It’s a big headache for providers that are run with a hyper-fixation on costs for everything except executive compensation. High turnover and understaffed IT mean simplistic is the only way to make their businesses run short of axing everyone whose title starts with C.
I think the core problem is that ISPs and others expect entities to have random IP addresses lumped together — because this is what happened with IPv4.
In theory, the design of IPv6 should result in less of this problem.
Consider Google Compute IP addresses:
https://gist.github.com/n0531m/f3714f6ad6ef738a3b0a
A router out of the box wants to “work”, i.e. let traffic be routed. And most users won’t know the full range of legal IP traffic on either side, which makes it very hard for routers to be able to be configured with anything other than “all IPs are legal on all sides”.
And it isn’t going to be just one IP range. Our network for a while had at least: public, 10, 172.20, 192.168.
Often criminals will hack other computers, take them over, and use them to start the process.
Thus, it’s something like:
[T] trouble-maker
[S] DDoS server
[H] Hacked computers
[P] Poorly configured DNS servers
[A] Answering DNS Server
[V] DNS Victim
T->S “please send data to V”
S->H*1000 “please send request for X to V”
[1000*]H->P*1000 “I’m V, I’d like to know about X”
[1000*1000*]P->A “what’s X.A?”
A->P “X is … … … … … … … … … … … … … …”
P->V “X is … … … … … … … … … … … … … …”
Note that the request packets are tiny, and fast to send, and sent a lot, the response packets are much larger. And are sent by computers that are a couple of hops removed from T and S.
Great investigation and write up.
Did anyone noticed : 8/14 registered using… NAMECHEAP
How surprising 😉
FYI should remove the N after Quantum
This is a welcome tactical victory. The feds won this battle.
But the war continues. It’s asymmetric. The feds are like the English redcoats in Concord Mass. They’re disciplined and organized. But it’s an asymmetric guerrilla war.
These recent law enforcement victories raise the question: Will stiff prison terms deter wannabe guerrillas? Or are they energized by the notoriety? What’s the tradeoff?
Brian, I know it flies in the face of honest journalism, but might it make sense to conceal or obfuscate the names / handles / locations of these miscreants?
Why would I obfuscate the names of the accused when they’ve already been publicly named?
wow. How many years have we seen this DDOS stuff and yet it continues b/c perhaps sharper minds pick apart the garbage that ambitious greedy mediocre type ceo’s want lesser talent for lesser money for their fatter bonuses? Which results in lacky rulesets which essentially say “let us put out our junk at increasing prices and let the retail suckers get injured and instead of getting real talent we’ll just hang those who exploit our failures.”. This is getting old.
I don’t know. Who is more selfish, the relentless exploiters or the ceo’s who NEVER get charged with near fraud?
There is a fallacy in there somewhere, but a better mind than mine will have to point it out.
Brian,Nice write up as usual.If i may ask,is this the same tool being deployed for ATM Cash OUTS?
After reading through the comments posted at this point, I find it interesting how many of us have differing opinions . My brother is a lawyer up in DC and we frequently have discussions about law and politics regarding computers. He and I both believe that one of the greatest threats facing avid computer users, weather you be a programmer, security researcher, sys admin, etc, is the shear lack of knowledge of computers and technology in our political representatives and as a result the poorly constructed laws and policies.
I do believe that the book should be thrown at these individuals. However, I also believe the book may have been made a bit heavier and thicker simply because of ignorance. I know our community can be very suspicious of the government, and I think we should be. But I think a lot of good could be done by reaching out, educating, and having meaningful discussions with our state reps. Extending a cautiously helpful hand to assist in shaping the way our government approaches the web.
After reading through all the comments posted so far, I find all the differing opinions interesting. I personally feel the book should be thrown at the site operators. However I do think ignorance in our law and policy makers may have made the book “heavier” then it should be.
This might be an indicator that we need to extend a cautiously helpful hand to our representatives. Our community can be very distrusting of the government, and with good cause, but it cant hurt to try and educate and advise them in making better laws and policies.
All this complex it talk booters stresser ddos and so.
Its too complicated, before use to be much easier words.
Like, drops, cash out, bank transfers.
I think nowdays fraud and cyber crimes takes more to know about it techicall things… As we know every frausder use cryptocurrency… When i first saw the btc, i was thinking wtf is this??… I use to think that criminals are some bad looking guys who smokes sigarets and drink alchol… My parents use to teach. Me that criminals you can see they have bad looking.. But now i see they are very educated.
This whole thing so complicated i wonder… Why those guys dont work in some good jobs?
With this complex it tech skills many big good companies can hire them.
Criminal activity is only for people who got no education and no hope.
I think the world is going to be to complicated.
All this couse of this high it teck and so.
Real social interactions replaced with bubbles and group think that goes to the extremes and doesn’t get challenged, along with easy access to information and tools, all the while having the shield of anonymity.
The internet is good but easily abused.
Great. The people that run these DDoS/botnet services aren’t just people trying to make a buck, they’re usually really horrible individuals (some kids) who will waste their life harassing you if you upset them. I have had to deal with two individuals that run a botnet service (still online, unfortunately!) attacking my websites, harassing me, threatening me, spamming me for months because I caught them using my services for illegal purposes nearly a year ago. It’s incredible how these people can dedicate so much of their time trying to ruin other peoples day.
At the end of the day, they might be nice people if you know them in person, but they are criminals and do nothing but try to harm people.
Where this evil come from??
Is just money greed?
Or they have something really missing in their lifes and try to compensate this to make other people life also bad??
Second… Where they learn that bad stuff?
My brain melted a bit with the explanation of DNS amplification. It’s not BK’s fault; this technical stuff always puzzles me.
What also puzzles me is the awful overreach of government to punish these annoying people. The CFAA and wire fraud statutes were never intended for this crap.
Um, “annoying people”?
These are CRIMINALS, plain and simple. White-collar crime, to be sure, but crime nonetheless.
Law enforcement uses every means necessary to arrest, and incarcerate poor people (especially people of color) for relatively minor infractions, such as drug possession. But typically, IMO, it does far too little to combat white-collar crime, which is far more devastating to society.
Perhaps wire fraud and CFAA weren’t originally intended for this use. But this is all fairly new stuff. Should LE simply wait until the law catches up with the new reality? I say theft is theft—and this is big time major theft.
These are NOT just poor undereducated kids with no other options. These are not some one-off mistakes by a misguided youth. They are technically skilled (at least somewhat) and engaged in an ongoing massive criminal enterprise.
Fiori,
“Should LE simply wait until the law catches up with the new reality?”
Yes!
Prosecutors should not invent crimes through LE and the justice system which have not been defined by the people’s representatives in legislation. This prosecution is clearly an attempt to circumvent the meaning and purpose of laws.
And really, WTF is the nexus to the District of Alaska? It’s an obvious forum-shopping to drag the defendants far from their families and lawyers, to pressure them to plead guilty to a non-crime. It’s an abuse of prosecutorial power.
“… This is big time major theft.”
No, it’s not. Theft is defined as taking property with the intent to permanently deprive the owner of its use. (1)
This is the temporary misuse of property with intent to annoy. There is no harm from this stuff. No one is deprived of the use of property. And nothing is actually taken.
It’s not fraud, either. These services deliver the result that they advertise. There’s no misrepresentation and no customer complaints.
(1) https://criminal.findlaw.com/criminal-charges/theft-overview.html
Whether or not you believe this behavior is “theft” (I do), based on your explanation you clearly believe it is illegal. For “borrowing” without permission IS a crime in this country. If you take a car, intending on returning it, it is a crime. In some states it is car theft, and not in others. If you damage the car, or cause any financial loss to the owner, the “borrower” is liable. It CAN be a felony.
Now, if you have an interstate conspiracy to systematically “borrow” cars, you have a felony.
But if you still object, then simply think of whatever sentence these miscreants are assessed not as punishment. Not as a loss of years of their life. But simply as “borrowing” some time from them and “annoying” them for a few years.
So, a long time ago, there were a couple of catalog based merchants (Sears, Lands End).
You could write to them requesting a catalog.
Let’s pick a year: 1992. Imagine that you wrote on a postcard [1] for 19¢[2] with your return address:
{your address}
Sears Catalog Requests
Sears, Hoffman Estates, Illionois
Sears sends you a catalog, which probably costs more to send [3] than a postcard. But, let’s ignore the “cost” that you pay for the stamp or Sears pays for the postage — pretending it’s “free” (that’s what most people do on the Internet) and just look at the size of the packet request (postcards are tiny: 5.0 x 3.5 x 0.007 in = 0.1225 in³) and packet response (catalogs are big, perhaps 8.5 x 11 x 1 in* = 93.5 in³) that’s a 760x magnification for a single request — it’s bigger than what we’re talking about w/ DNS.
OK, but that’s not very interesting, you wanted a catalog, you sent a request for a catalog, the catalog vendor sent you a catalog.
But! What if you instead made 1000 postcards and instead of using your return address, you used someone else’s?
1600 Pennsylvania Avenue
Sears Catalog Requests
Sears, Hoffman Estates, Illinois
You could leave all 1000 in your mailbox (they’re 7 inches, that’d probably fit in your mailbox). But if you do that, someone might get wise about it.
Instead, you drop off each postcard or bundle of 10 postcards into a different outbox spread across some area.
Each postcard is picked up by a postal worker and delivered. Sears receives each one, and dutifully processes it, and responds with a catalog.
They send 1000 catalogs to 1600 Pennsylvania Avenue.
That’s what a DNS amplification attack looks like.
And it’s a good way to think about how traffic on the Internet works. For some reason, people assume that conversations on the Internet are like two people sitting next to each other and talking directly where each party can see the other party. But, it really isn’t like that at all. It’s much closer to a series of postcards, each sender can write whatever return address they wish in the return address field.
If they don’t use their own return address, in general, they won’t get the response delivered to them. Although, not always — it depends. If you write a postcard saying “I’ll be in staying at 9641 Sunset Blvd, Beverly Hills, CA 90210, USA next week, please deliver a dozen roses their, bill to my credit card” and have a return address of “223 Front St, Nome, AK 99762, USA” because that’s where you are then, the fact that you won’t be where the return address is in a week when the roses are delivered to the requested destination won’t bother you.
In general, spoofed return addresses are not good things, and ideally routers wouldn’t accept them, but if you look at postal mail, return addresses are ignored 99.99% of the time, we usually only care about the content, and only check the return address when something goes wrong.
[1] https://en.wikipedia.org/wiki/Sears#Mail_order_catalog
[2] http://www.costofstamps.net/historical_us_postcard_rates.php
[3] http://www.costofstamps.net/historical_us_postage_stamp_rates.php
[4] http://www.searsarchives.com/catalogs/history.htm
[5] http://www.searsarchives.com/catalogs/chronology.htm
[6] https://www.papersizes.org/postcard-sizes.htm
* I can’t find sizes for the catalog, but my memory is that it was the size of a phonebook. I’m not using a phonebook as an example because people probably don’t remember them.
Any country should NOT wait to new laws to make this illegal. This is illegal activity to most of western democracies already, is US lacks behind? , sorry for you.
Example here, where I live, even TRYING to DOS something is illegal, so is nmap to find possible ways to attack.
And ALSO, even temporary taking someones property under control, that is also illegal (includes snow from street to owned land movement)
Is running nmap against your own server illegal? (Please specify your country.)
In general, writing additional laws is not the right solution. Laws are like code, there will be bugs. It’s better to rely on well established and litigated laws than new ones.
I’m impressed that the FBI has finally managed to piece together a fairly cogent use of extant laws (wire fraud, computer trespass laws, …) instead of throwing up their hands and saying “oh, our laws haven’t been updated in the last 20 years, so we can’t do anything”.
I feel personally it looks good news at long holiday time Nice
About time, though these booters never did their due diligence to verify their customers in did own and have permission from everyone affected from their attacks, so their terms of service ‘protection’ could never hold any water in court.