Cybercrime forums have been abuzz this week over news that BriansClub — one of the underground’s largest shops for stolen credit and debit cards — has been hacked, and its inventory of 26 million cards shared with security contacts in the banking industry. Now it appears this brazen heist may have been the result of one of BriansClub’s longtime competitors trying to knock out a rival.
And advertisement for BriansClub that for years has used my name and likeness to peddle stolen cards.
Last month, KrebsOnSecurity was contacted by an anonymous source who said he had the full database of 26M cards stolen from BriansClub, a carding site that has long used this author’s name and likeness in its advertising. The stolen database included cards added to the site between mid-2015 and August 2019.
This was a major event in the underground, as experts estimate the total number of stolen cards leaked from BriansClub represent almost 30 percent of the cards on the black market today.
The purloined database revealed BriansClub sold roughly 9.1 million stolen credit cards, earning the site and its resellers a cool $126 million in sales over four years.
In response to questions from KrebsOnSecurity, the administrator of BriansClub acknowledged that the data center serving his site had been hacked earlier in the year (BriansClub claims this happened in February), but insisted that all of the cards stolen by the hacker had been removed from BriansClub store inventories.
However, as I noted in Tuesday’s story, multiple sources confirmed they were able to find plenty of card data included in the leaked database that was still being offered for sale at BriansClub.
Perhaps inevitably, the admin of BriansClub took to the cybercrime forums this week to defend his business and reputation, re-stating his claim that all cards included in the leaked dump had been cleared from store shelves.
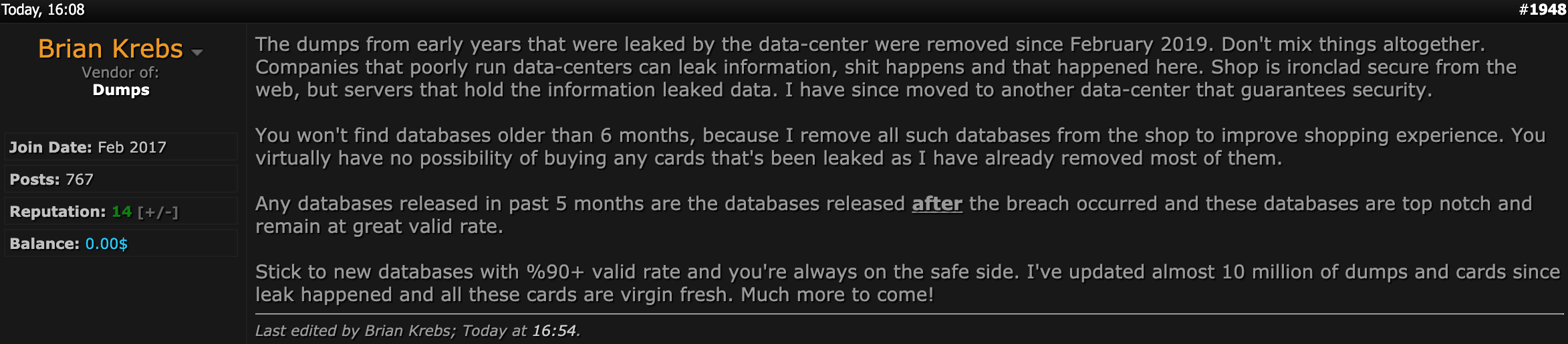
The administrator of BriansClub, who’s appropriated the name and likeness of Yours Truly for his advertising, fights to keep his business alive.
Meanwhile, some of BriansClub’s competitors gloated about the break-in. According to the administrator of Verified, one of the longest running Russian language cybercrime forums, the hack of BriansClub was perpetrated by a fairly established ne’er-do-well who uses the nickname “MrGreen” and runs a competing card shop by the same name.
The Verified site admin said MrGreen had been banned from the forum, and added that “sending anything to Krebs is the lowest of all lows” among accomplished and self-respecting cybercriminals. I’ll take that as a compliment.
This would hardly be the first time some cybercriminal has used me to take down one of his rivals. In most cases, I’m less interested in the drama and more keen on validating the data and getting it into the proper hands to do some good.
That said, if the remainder of BriansClub’s competitors want to use me to take down the rest of the carding market, I’m totally fine with that.




Posted on my Facebook account, this is awesome !
Dude, what a mess. If someone can get into a site where your sole ticket item for sale is a card number, maybe they should’ve been stored encrypted!
Whoever ran this site must be incompetent, which means it must be way too easy to run.
This story only promoted cybercrime because somebody as incompetent as the owner of BriansClub is allowed to make money in it.
If I was a criminal, I would think “Wow, I could do this much better and not get hacked. I’d use 7-zip to encrypt the card dumps with a password.”
Embarrassing!
What indications do you see that they stored their data unencrypted?
What makes you think there was serious negligence involved at all?
Criminal enterprises are usually bigger targets for other criminals. Because the lawless won’t go to the cops. For all we know, the site had excellent security, but had been under persistent attack for a while. All it takes is a single 0-day, or several vulnerabilities chained together.
I am sure people would love to think they would do it better… but they often aren’t such tempting targets.
Datacenter leak? Server leak? Ever heard of disk encryption? 🙂 or maybe they hot add disk and copy data on-the-fly through NFC? Lol
How does disk encryption help when a database is running, and is accessible through a web front end?
Those keys have to remain in memory.
Monday morning quarterbacks come out after every breach (good or bad)… claiming basic security would have prevented it.
Yet breaches happen everywhere. Why? Because these aren’t air-gapped systems that an owner tosses into the ocean. It has to be accessible, and any web store (legal or not) would need automation to access after purchase is confirmed.
It would be one thing if people had to wait days for the data owner went and turned on db servers, decrypted drives, then fetched data across a secure channel, to deliver it to buyers… but that is not how it works.
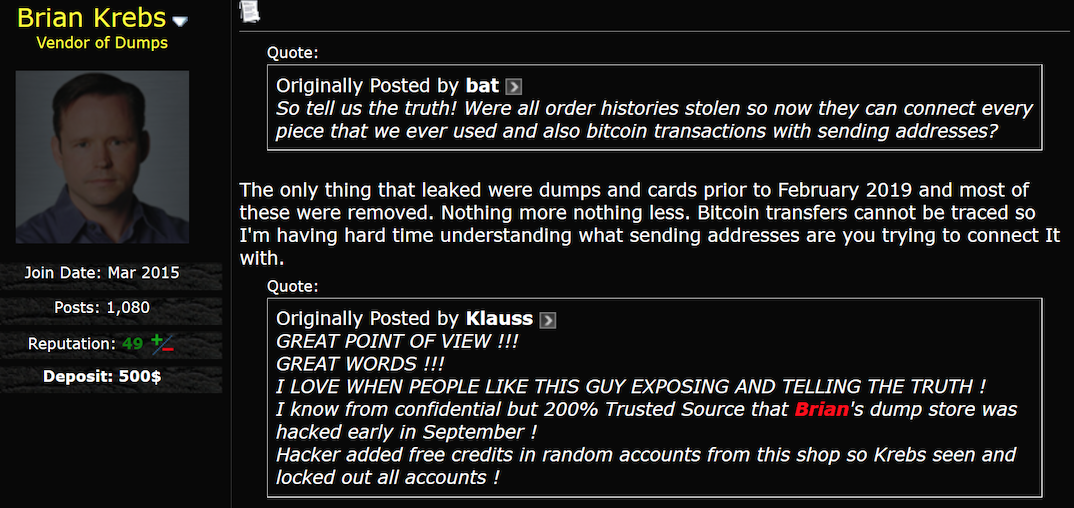
The crook say it was datacenter leak not a front end hack. That’s why he changed hosting company. All his words are a big lie. Probably a tech guy/admin he was working with was bribed and dumped a database. The seller has no tech skills to run a shop. End of story.
Yeah, it is hard to understand what he was saying. English not his first language.
It is possible there was some human element that intentionally leaked as you said. But then disk encryption would still not have prevented it.
Now days so many rippers! (Rippers= scammers)
I quit carding few years ago it use to be 10k figure Job Weekly If u Got Brain and Not lazy.
I hate rippers carders should join together to Fight Against rippers
“carders should join together to Fight Against rippers”
That’s like saying child abusers should fight against child rapists. How about you just don’t be a criminal and get a normal job?
But that’s giving in to the man, not to mention hard work. And they can’t go out partying every night on other people’s money, they’d have to live frugally.
That’s true… well paint me interested. Who wants to create a card ripping / scamming company with me?! We’ll call it, “Totally Not A Card Ripping Company, Inc.” That way, the feds will never catch on to us.
“Normal” is in the eye of the beholder. Some people don’t have the luxuries of education or abundance of jobs that can sustain a family, should their children go starving because of this? Not everybody is as privileged as you are, and to take it further the whole credit and banking system is a big part of who to blame for this, trapping people even further into a system of debt, profiting off of the monetary enslavement of the people who can barely keep shelter or food, and these carders aren’t living off of people’s stolen money, you aren’t liable for any fraudulent charges and it is just a phone call to credit it back and re issue a card, so in a way these people are fighting back against that system of credit and the banks, they are fighting for their cause and their ability to afford basic necessities. Asshat.
That is complete and utter BS. This isn’t the same as stealing a loaf of bread. They are stealing money from other people, in a way that can potentialy severely disrupt their lives. Yes, in many cases, the acount holders are not on the hook, but even when that happens it can be very disruptive.
See the report on the big child porn sting this week. They can trace BC transfers
Exactly what I was thinking. Anonymity is an illusion.
HackerNews reports:
Merely reviewing the HTML source code of the site in the browser revealed the original IP addresses of the server on which the site was hosted.
The IP addresses were then traced back to a server located inside the bedroom of the site admin Jong Woo Son’s house in South Korea.
….
So, umm, no. They haven’t traced BTC transfers.
It does take some work to have anonymity with cryptocurrency, it isn’t a given. But it is a myth that they are inherently transparent because of the ledger. It only takes a bit of effort to launder digital currency…. probably easier than hiding cash with serial numbers being tracked. It is trivial.
Agreed. The article never mentions anything about tracing Bitcoin, those two IP addresses were traced back to a telecom provider, both of which were registered to the same person. What I find more interesting is that they cracked down on 300+ other users of the site. That’s awesome in my mind. I think it’s a small win to a larger battle, but a recent article I read from Bleeping Computer makes me think otherwise. Hosting a site on the dark web looks much easier with OnionShare… which, of course, my mind automatically goes to making it simple for bad people to host bad things:
https://www.bleepingcomputer.com/news/software/onionshare-lets-anyone-host-anonymous-sites-on-the-dark-web/
Brian can feel honoured that his work gets on so many cybercriminals nerves. Just keep it up and stay safe…
This joejob – joke is nothing compared to the swatting you received!
But what if these criminals go after you abusing the legal systems in various other contries? I’ve seen it happen….
I don’t think that the validity rate on BriansClub is on the up and up even with the boasting of 26M cards. I only heard about this article this time through 3rd party cyber sec channels where the word is the dumps ranged 2015 – 2019. This would place the dumps dead in the middle of most banks EMV conversion, natural, and forced re-issue shortly after the HD breach. Within the last two years would be where the worry sets in post fully integrated EMV. Even so, identifying the base(s) have never been too much of an issue. What I am hearing is that the list was shared per the last article with multiple agencies, and institutions. Curious to see how many were actually active in this batch ….. if that information gets shared consortium level.
They’ve been able to do basic BTC traces for a long while. Bitcoin isn’t an anonymous crypto and it blows me away to see the underground still treating it as such. I wonder why they still insist on using it when there are better alternatives. Maybe because its fairly stable in comparison to other coins?
BTC may not have anonymity by design, like other cryptocurrencies…. but it is still trivial to launder.
Criminals who get paid directly from victims, like with ransomware, tend to favor BTC because the victim will have the easiest time paying.
But that does not mean the criminal loses anonymity, just because it wasn’t in the coin design. It just means they have to take a few extra (and easy) steps to launder and hide the source.
” the admin of BriansClub took to the cybercrime forums this week to defend his business and reputation ”
(Laughing)
Brian, they should book you on Saturday Night Live. That line is funny.
+1 always enjoy Brians ironic remarks. Also anyone who thinks they are using anonymous tools should read Snowdens book Permanent Record.
A quick internet search doesn’t show very many recent Restaurant or POS breach activity that might explain the large volume of credit card data for sale on the dark web.
Any comments on possibly where these CC’s came from?
The assertion in the original article that cards are only sold once is provably false. I see many instances of cards that were sold to more than one user, usually in different locations (e.g., Seattle and Boston).
Hey Paul, it’s quite common for someone’s card to be compromised at multiple places in a short period of time, stores that are being plundered by miscreants who sell their wares to different cybercrime shops. The same reseller selling the same cards twice is easy to detect from the cards shop side, so they won’t do this. But it’s not uncommon for multiple, unrelated hacking groups to sell the same card to different shops because they were obtained from different hacked merchants that the cardholder shopped at. Does that make sense?
Obviously BriansClub was not adhering to PCI guidelines. They should be held to the same standard that regular merchants are held to 🙂
Interesting read.
Still, I fail to see how trouble for one dump site spells a win for consumers. There are plenty of other criminals out there to fill any fleeting vacuum.
Ah, but authorities are getting way better at tracing bitcoin transactions and figuring out where the endpoints are and who is actually the owner(s) of those endpoints.
https://www.independent.co.uk/news/world/americas/child-porn-bitcoin-arrests-us-jong-woo-son-a9159146.html
https://www.smh.com.au/world/north-america/hundreds-arrested-in-cryptocurrency-linked-dark-web-child-porn-ring-bust-20191017-p531g1.html
Brian – which forums are those screenshots from?