Carding — the underground business of stealing, selling and swiping stolen payment card data — has long been the dominion of Russia-based hackers. Happily, the broad deployment of more secure chip-based payment cards in the United States has weakened the carding market. But a flurry of innovation from cybercrime groups in China is breathing new life into the carding industry, by turning phished card data into mobile wallets that can be used online and at main street stores.
An image from one Chinese phishing group’s Telegram channel shows various toll road phish kits available.
If you own a mobile phone, the chances are excellent that at some point in the past two years it has received at least one phishing message that spoofs the U.S. Postal Service to supposedly collect some outstanding delivery fee, or an SMS that pretends to be a local toll road operator warning of a delinquent toll fee.
These messages are being sent through sophisticated phishing kits sold by several cybercriminals based in mainland China. And they are not traditional SMS phishing or “smishing” messages, as they bypass the mobile networks entirely. Rather, the missives are sent through the Apple iMessage service and through RCS, the functionally equivalent technology on Google phones.
People who enter their payment card data at one of these sites will be told their financial institution needs to verify the small transaction by sending a one-time passcode to the customer’s mobile device. In reality, that code will be sent by the victim’s financial institution to verify that the user indeed wishes to link their card information to a mobile wallet.
If the victim then provides that one-time code, the phishers will link the card data to a new mobile wallet from Apple or Google, loading the wallet onto a mobile phone that the scammers control.
CARDING REINVENTED
Ford Merrill works in security research at SecAlliance, a CSIS Security Group company. Merrill has been studying the evolution of several China-based smishing gangs, and found that most of them feature helpful and informative video tutorials in their sales accounts on Telegram. Those videos show the thieves are loading multiple stolen digital wallets on a single mobile device, and then selling those phones in bulk for hundreds of dollars apiece.
“Who says carding is dead?,” said Merrill, who presented about his findings at the M3AAWG security conference in Lisbon earlier today. “This is the best mag stripe cloning device ever. This threat actor is saying you need to buy at least 10 phones, and they’ll air ship them to you.”
One promotional video shows stacks of milk crates stuffed full of phones for sale. A closer inspection reveals that each phone is affixed with a handwritten notation that typically references the date its mobile wallets were added, the number of wallets on the device, and the initials of the seller.
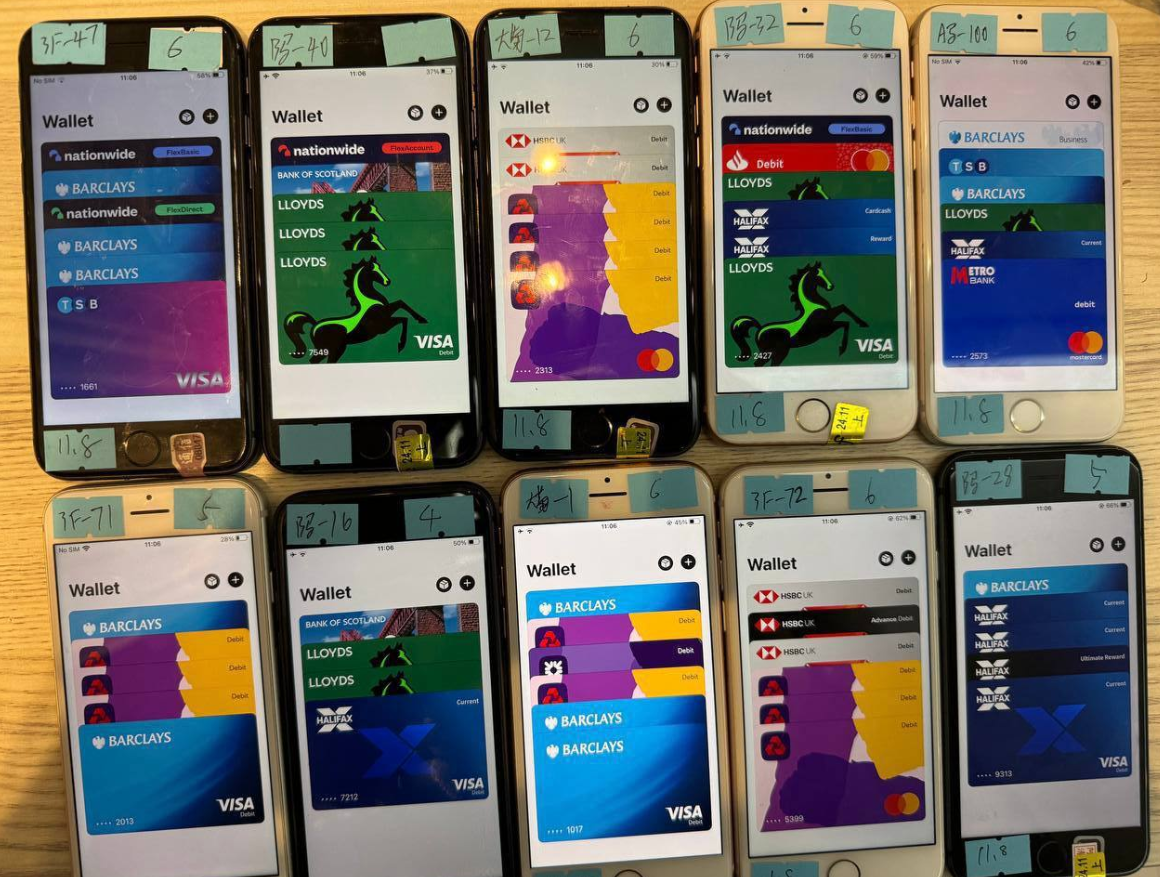
An image from the Telegram channel for a popular Chinese smishing kit vendor shows 10 mobile phones for sale, each loaded with 4-6 digital wallets from different UK financial institutions.
Merrill said one common way criminal groups in China are cashing out with these stolen mobile wallets involves setting up fake e-commerce businesses on Stripe or Zelle and running transactions through those entities — often for amounts totaling between $100 and $500.
Merrill said that when these phishing groups first began operating in earnest two years ago, they would wait between 60 to 90 days before selling the phones or using them for fraud. But these days that waiting period is more like just seven to ten days, he said.
“When they first installed this, the actors were very patient,” he said. “Nowadays, they only wait like 10 days before [the wallets] are hit hard and fast.”
GHOST TAP
Criminals also can cash out mobile wallets by obtaining real point-of-sale terminals and using tap-to-pay on phone after phone. But they also offer a more cutting-edge mobile fraud technology: Merrill found that at least one of the Chinese phishing groups sells an Android app called “ZNFC” that can relay a valid NFC transaction to anywhere in the world. The user simply waves their phone at a local payment terminal that accepts Apple or Google pay, and the app relays an NFC transaction over the Internet from a phone in China.
“The software can work from anywhere in the world,” Merrill said. “These guys provide the software for $500 a month, and it can relay both NFC enabled tap-to-pay as well as any digital wallet. They even have 24-hour support.”
The rise of so-called “ghost tap” mobile software was first documented in November 2024 by security experts at ThreatFabric. Andy Chandler, the company’s chief commercial officer, said their researchers have since identified a number of criminal groups from different regions of the world latching on to this scheme.
Chandler said those include organized crime gangs in Europe that are using similar mobile wallet and NFC attacks to take money out of ATMs made to work with smartphones.
“No one is talking about it, but we’re now seeing ten different methodologies using the same modus operandi, and none of them are doing it the same,” Chandler said. “This is much bigger than the banks are prepared to say.”
A November 2024 story in the Singapore daily The Straits Times reported authorities there arrested three foreign men who were recruited in their home countries via social messaging platforms, and given ghost tap apps with which to purchase expensive items from retailers, including mobile phones, jewelry, and gold bars.
“Since Nov 4, at least 10 victims who had fallen for e-commerce scams have reported unauthorised transactions totaling more than $100,000 on their credit cards for purchases such as electronic products, like iPhones and chargers, and jewelry in Singapore,” The Straits Times wrote, noting that in another case with a similar modus operandi, the police arrested a Malaysian man and woman on Nov 8.

Three individuals charged with using ghost tap software at an electronics store in Singapore. Image: The Straits Times.
ADVANCED PHISHING TECHNIQUES
According to Merrill, the phishing pages that spoof the USPS and various toll road operators are powered by several innovations designed to maximize the extraction of victim data.
For example, a would-be smishing victim might enter their personal and financial information, but then decide the whole thing is scam before actually submitting the data. In this case, anything typed into the data fields of the phishing page will be captured in real time, regardless of whether the visitor actually clicks the “submit” button.
Merrill said people who submit payment card data to these phishing sites often are then told their card can’t be processed, and urged to use a different card. This technique, he said, sometimes allows the phishers to steal more than one mobile wallet per victim.
Many phishing websites expose victim data by storing the stolen information directly on the phishing domain. But Merrill said these Chinese phishing kits will forward all victim data to a back-end database operated by the phishing kit vendors. That way, even when the smishing sites get taken down for fraud, the stolen data is still safe and secure.
Another important innovation is the use of mass-created Apple and Google user accounts through which these phishers send their spam messages. One of the Chinese phishing groups posted images on their Telegram sales channels showing how these robot Apple and Google accounts are loaded onto Apple and Google phones, and arranged snugly next to each other in an expansive, multi-tiered rack that sits directly in front of the phishing service operator.

The ashtray says: You’ve been phishing all night.
In other words, the smishing websites are powered by real human operators as long as new messages are being sent. Merrill said the criminals appear to send only a few dozen messages at a time, likely because completing the scam takes manual work by the human operators in China. After all, most one-time codes used for mobile wallet provisioning are generally only good for a few minutes before they expire.
Notably, none of the phishing sites spoofing the toll operators or postal services will load in a regular Web browser; they will only render if they detect that a visitor is coming from a mobile device.
“One of the reasons they want you to be on a mobile device is they want you to be on the same device that is going to receive the one-time code,” Merrill said. “They also want to minimize the chances you will leave. And if they want to get that mobile tokenization and grab your one-time code, they need a live operator.”
Merrill found the Chinese phishing kits feature another innovation that makes it simple for customers to turn stolen card details into a mobile wallet: They programmatically take the card data supplied by the phishing victim and convert it into a digital image of a real payment card that matches that victim’s financial institution. That way, attempting to enroll a stolen card into Apple Pay, for example, becomes as easy as scanning the fabricated card image with an iPhone.
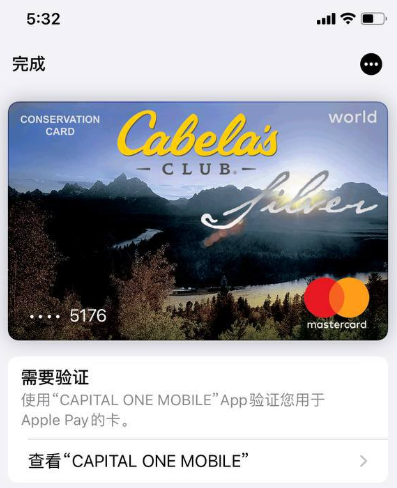
An ad from a Chinese SMS phishing group’s Telegram channel showing how the service converts stolen card data into an image of the stolen card.
“The phone isn’t smart enough to know whether it’s a real card or just an image,” Merrill said. “So it scans the card into Apple Pay, which says okay we need to verify that you’re the owner of the card by sending a one-time code.”
PROFITS
How profitable are these mobile phishing kits? The best guess so far comes from data gathered by other security researchers who’ve been tracking these advanced Chinese phishing vendors.
In August 2023, the security firm Resecurity discovered a vulnerability in one popular Chinese phish kit vendor’s platform that exposed the personal and financial data of phishing victims. Resecurity dubbed the group the Smishing Triad, and found the gang had harvested 108,044 payment cards across 31 phishing domains (3,485 cards per domain).
In August 2024, security researcher Grant Smith gave a presentation at the DEFCON security conference about tracking down the Smishing Triad after scammers spoofing the U.S. Postal Service duped his wife. By identifying a different vulnerability in the gang’s phishing kit, Smith said he was able to see that people entered 438,669 unique credit cards in 1,133 phishing domains (387 cards per domain).
Based on his research, Merrill said it’s reasonable to expect between $100 and $500 in losses on each card that is turned into a mobile wallet. Merrill said they observed nearly 33,000 unique domains tied to these Chinese smishing groups during the year between the publication of Resecurity’s research and Smith’s DEFCON talk.
Using a median number of 1,935 cards per domain and a conservative loss of $250 per card, that comes out to about $15 billion in fraudulent charges over a year.
Merrill was reluctant to say whether he’d identified additional security vulnerabilities in any of the phishing kits sold by the Chinese groups, noting that the phishers quickly fixed the vulnerabilities that were detailed publicly by Resecurity and Smith.
FIGHTING BACK
Adoption of touchless payments took off in the United States after the Coronavirus pandemic emerged, and many financial institutions in the United States were eager to make it simple for customers to link payment cards to mobile wallets. Thus, the authentication requirement for doing so defaulted to sending the customer a one-time code via SMS.
Experts say the continued reliance on one-time codes for onboarding mobile wallets has fostered this new wave of carding. KrebsOnSecurity interviewed a security executive from a large European financial institution who spoke on condition of anonymity because they were not authorized to speak to the press.
That expert said the lag between the phishing of victim card data and its eventual use for fraud has left many financial institutions struggling to correlate the causes of their losses.
“That’s part of why the industry as a whole has been caught by surprise,” the expert said. “A lot of people are asking, how this is possible now that we’ve tokenized a plaintext process. We’ve never seen the volume of sending and people responding that we’re seeing with these phishers.”
To improve the security of digital wallet provisioning, some banks in Europe and Asia require customers to log in to the bank’s mobile app before they can link a digital wallet to their device.
Addressing the ghost tap threat may require updates to contactless payment terminals, to better identify NFC transactions that are being relayed from another device. But experts say it’s unrealistic to expect retailers will be eager to replace existing payment terminals before their expected lifespans expire.
And of course Apple and Google have an increased role to play as well, given that their accounts are being created en masse and used to blast out these smishing messages. Both companies could easily tell which of their devices suddenly have 7-10 different mobile wallets added from 7-10 different people around the world. They could also recommend that financial institutions use more secure authentication methods for mobile wallet provisioning.
Neither Apple nor Google responded to requests for comment on this story.



Sounds like if person has no digital wallet = safe from this scam.
I suspect they can make wallets as a victim with just a card by setting up a new phone account as them. :/
I didn’t get that from the article. The attacker is the one setting up the wallet and linking it to the card. They are triggering 2-factor and the victim gets a message and provides the 2nd factor for the attacker to link the card to the attacker’s wallet.
Not so much – the bad guys will still go after your CC details to use in card not present fraud transactions. This is no different than other scams that have been around forever going for CNP fraud. The wallet stuffing is brilliant and their preferred outcome, but they’ll take anything they can get and monetize it.
One more reason I’m glad I only use a basic “flip phone”. Someday, I may get the rotary dial one!
Least base r/dumbphone user.
Many of the telecom companies are switching to VoIP calls. There are few places that are still on landline but eventually it is “going to the dodo.”
Many of the telecom companies are switching to VoIP calls. There are few places that are still on landline but eventually it is “going to the dodo.”
Nice touch with the Wilco reference:)
I’m glad someone got that!
Great article and good insights on how this is being done, and what people should look out for. However, I don’t get why the obvious smear campaign against Telegram (mentioned *5 times* in this article and captions), it’s just a great tool bad folks are abusing. But you paint it to your readers as if Telegram is somehow complicit in this fraud. Not cool.
Because they are complicit. Telegram is the biggest trash fire on earth. It enables so much criminal behavior and everyone with common sense knows it. Just because you can use it for non-crime stuff doesn’t mean it excuses the terrible and illegal abhorrent behavior on the platform. The reason they arrested Durov was because he didn’t co-operate with authorities, but I guess the threat of prison and bunking with Bubba changes your mind.
Gotta agree with Dave, here. Telegram is a cesspool. Best phrase I’ve heard is it’s like having the dark web in your pocket. But you would have to be insane as a security person and install Telegram on any mobile device you care about. You don’t have to go looking for trouble on Telegram, because it will find you just fine.
Hang on, Brian. Are you saying that even installing Telegram on your smartphone is bad. Can you explain?
Love an answer on this.
LMGTFY
forbes.com/sites/zakdoffman/2024/02/02/apple-iphone-google-pixel-and-samsung-galaxy-telegram-app-warning/
Telegram uses a unique encryption protocol called MTProto, which the company established for its proprietary use. The protocol was created specifically to meet mobile messaging needs and handle encrypted messages across different device types. MTProto uses a mix of cryptographic algorithms, including AES-256 encryption for messages, RSA 2048-bit encryption for cryptographic key exchanges, and Diffie-Hellman key exchange to establish secret chats over unsecured communication channels.
>>However, security researchers have criticized Telegram for using a relatively new protocol that has passed fewer rigorous security evaluations than the existing, widely accepted encryption protocols. Because MTProto is not an open-source protocol, independent security experts are restrained from continuously examining its security. As a result, this narrows the scope of security vulnerabilities search and detection.
And even that untested encryption isn’t on by default? Where do I sign? Oh, VK? Sure.
In one way, financial institutions brought this onto themselves. They KNEW that SMS isn’t sufficiently secure. But they don’t care. My banks – Capital One and Citi – both provide no way to add either a hardware or software authenticator. Only SMS verification. Nothing is totally foolproof, but linking a card to one’s phone would be much more secure if authenticator codes are used – rather than SMS codes.
Wouldn’t it help to just change the SMS text to something like this:
“You are about to link your Citi bank account with Apple Pay. Use code 149382 to continue.”
I know many companies don’t get that right (I’ve gotten so many OTP codes without any context information in the SMS text). And it also won’t provide full protection since quite some users just copy the code without reading the text – but at least it gives users another chance to detect the phishing and would make it less likely to succeed.
We saw this trend about 1-2 months ago, reported it up to our card vendor and started looking in to ways to reduce the risk, engaged our digital banking provider, etc.. Key as we see it is that we need to tie both the tokenization of the card AND the step up MFA method to the device that is requesting the tokenization, via as many means capable (geolocation, IMEI, etc..). Oh, and convincing the industry players this needs to be a requirement. IMHO it is a break in the PCI protection model, enough of a process is granted to “produce a card” but the boundary of protection to produce a card is extended way too far. Imagine if the process of instant issue is extended to any card printer on the planet, instead of the one in a locked and controlled area with a HSM server and etc.. This is effectively what is currently being permitted. Really needs to be buttoned down.
As mentioned in the article, one potential solution is to enable the authorization of adding a card to a wallet through the card issuer’s mobile app on the same device as the wallet.
I appreciated the Wilco lyric quote, and the article. Thanks!
Several of the “innovations” listed in this article are decades-old techniques.
Multiple decades old: mass-creation of accounts, storing web data in a “back-end” database, sending form input as it is typed.
At least a decade old: Using a large rack of mobile devices to commit fraud.
Using a generated image of a credit card to make it easier to scan with a wallet app I guess could count as an innovation, but not a very impressive one.
What is also semi-recent is the ability to e.g. share your wallet with friends and family. Thus the ability to spread the card as desired, once in the wallet.
I was seeing fraud purchases with synthesised card (and ID) images 15 years ago. The only novel thing here is the NFC relaying.
Thank you , Brian for posting this. The video was a shocker to me. It answered the question which I was looking for last 2 years. Contactless transaction from two countries located in different continents with in short time !!
It appears at least one of the phishing kits did not require mobile; after several minutes of trying to convince family member this was not from USPS (along with discussing how much USPS really cares ? 🙂 and/or even knows your cell number ), logged into urlscan.io with the link, saw a very convincing USPS webpage [I was not on a mobile device although I guess sometimes Chromebooks present as Android ? ]
“But Merrill said these Chinese phishing kits will forward all victim data to a back-end database operated by the phishing kit vendors. That way, even when the smishing sites get taken down for fraud, the stolen data is still safe and secure.”
They need to make sure that that backend database is not continuously connected to their main systems environment, less they become prey to a ransomware attack. /S
Thanks for posting this.
Great understanding on how they are doing it.
The real time capture of data as you type is what caught my eye
Peeking under the Peking curtain.
I wonder if Apple and Google can work with financial institutions to implement a mechanism to read and validate the card’s presence contactlessly using the phone ‘s NFC reader (like a POS card terminal would do in a sales transaction) during the mobile wallet card onboarding process (since obviously taking a photo of the card can’t guarantee physical card presence).
Correct me If I’m wrong, but for iPhone the wallet holding your card is protected and not shown/shared until you unlock your phone and double tap the power button. This means that you cant be ghosted, but you can still share your card to a fraudlet POS that does a MITM Attack and relay your CC information.
Yes. The banks can do more, in some countries like Sweden, the banks already require your identification to add your card to the wallet, preventing anyone else from adding your card.
Based on this, I’d say that having the card in your wallet and using NFC as a payment at a POS is more secure than walking around with your physical bank card at your backpocket, as that card can be ghosted by NFC without your knowledge, and that card can be photographed when shown.
A good tip, is to remove the CCV code from the card by just scratch it off and have it written down somewhare (securely)
I foolishly clicked a parking ticket SMS phishing link and clicked a box within the site. I didnt type any information in the website. I am concerned that I could have installed some sort of malware on my iphone. This was over 3 weeks ago that I did this. How long would it take for money to be missing from my account, if malware had stolen my banking information?
AFAIK, these phishing sites — while manned in real-time by cybercriminals — are not actively malicious. If you didn’t enter any information, you are at no risk from this scam. However, it’s a good idea to be far more cautious about visiting links that arrive in instant message.
The blocking of non-mobile browsers has another feature: Cloudflare’s abuse team doesn’t understand this and will deny abuse reports because they can’t verify that it’s a phishing site. I have even given explicit instructions to them to test using a mobile user agent and it goes ignored. I’m very frustrated at Cloudflare’s inability to do anything about these sites. (IMO willing inability, they are known to harbor criminal activity under the guise of “free speech”)