If you happen to stumble upon a Web site that freaks out your anti-virus program, chances are good that the page you’ve visited is part of a malicious or hacked site that has been outfitted with what’s known as an “exploit pack.” These are pre-packaged kits designed to probe the visitor’s browser for known security vulnerabilities, and then use the first one found as a vehicle to silently install malicious software.
Exploit packs have been around for years, and typically are sold on shadowy underground forums. A constant feature of exploit packs is a Web administration page (pictured above), which gives the attacker real-time statistics about victims, such as which browser exploits are working best, and which browsers and browser versions are most successfully attacked.
One of the most popular at the moment is a kit called “Eleonore,” and I’m writing about it here because it highlights the importance of remaining vigilant about patching. It’s also a reminder that sometimes the older exploits are more successful than the brand new variety that garner all of the headlines from the tech press.
 The screen captures in this blog post were taken a few weeks ago from a working Eleonore installation (version 1.3.2) that was linked to several adult Web sites. As we can see from the first image, this pack tries to exploit several vulnerabilities in Adobe Reader, including one that Adobe just patched this month. The kit also attacks at least two Internet Explorer vulnerabilities, and a Java bug. In addition, the pack also attacks two rather old Firefox vulnerabilities (from 2005 and 2006). For a partial list of the exploits included in this pack, skip to the bottom of this post.
The screen captures in this blog post were taken a few weeks ago from a working Eleonore installation (version 1.3.2) that was linked to several adult Web sites. As we can see from the first image, this pack tries to exploit several vulnerabilities in Adobe Reader, including one that Adobe just patched this month. The kit also attacks at least two Internet Explorer vulnerabilities, and a Java bug. In addition, the pack also attacks two rather old Firefox vulnerabilities (from 2005 and 2006). For a partial list of the exploits included in this pack, skip to the bottom of this post.
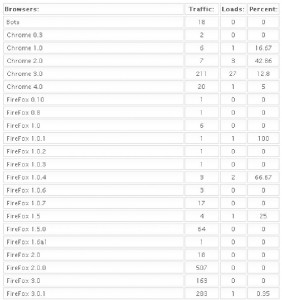
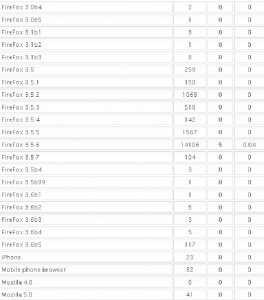
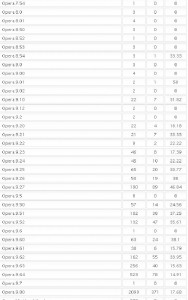
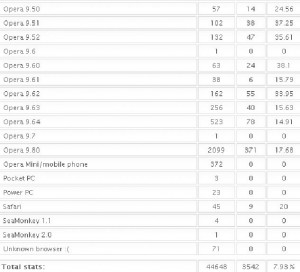
It’s important to keep in mind that some of these exploits are browser-agnostic: For example, with the PDF exploits, the vulnerability being exploited is the PDF Reader browser plug-in, not necessarily the browser itself. That probably explains the statistics in the images below, which shows a fairly high success rate against Opera, Safari, and Google Chrome users. In the screen shots below, the numbers beneath the “traffic” field indicate the number of visitors to the malicious site using that particular version of the browser, while the “loads” number corresponds to the number of visitors for that browser version that were found to be vulnerable to one or more of the vulnerabilities exploited by the Eleonore pack. The “percent” fields obviously indicate the percentage of visitors for each specific browser type that were successfully exploited (click for a larger version):
Just from observing some of these stats, it’s clear that some of the most successful exploits target vulnerabilities that were patched quite some time ago. In a few cases where I have highlighted the importance of patching Java vulnerabilities, for example, I received feedback from some readers who doubted whether anyone ever tried to attack Java flaws. As we can see from the second screenshot above, the Java exploit was the second most successful attack (behind an exploit pack that attacks at least three different Adobe Reader flaws).
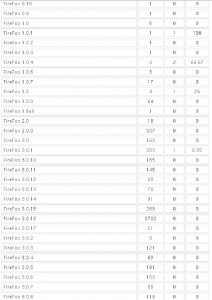
More Firefox stats (again, click for a larger version)
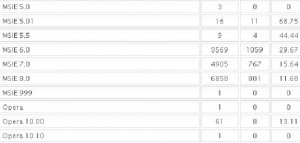
Here are the Internet Explorer breakdowns:
…and the Opera and Safari statistics:
Vulnerabilities exploited by this Eleonore pack include:
PDF pack
PDF Brand new PDF Exploit (12/2009)
PDF collab.getIcon (4/2009)
PDF Util.Printf (11/2008)
PDF collab.collectEmailInfo (2/2008)
MS Internet Explorer Exploits
MS09-002 (Internet Explorer 7 exploit 1/2009)
MDAC – ActiveX (Internet Explorer exploit, 3/2007)
Java
Javad0 (12/2008) – Java Calendar (Java Runtime Environment (JRE) for Sun JDK and JRE 6 Update 10 and earlier; JDK and JRE 5.0 Update 16 and earlier; and SDK and JRE 1.4.2_18 and earlier)
Firefox
compareTo – exploit for a Firefox vulnerability from 2005
jno – Exploit for Firefox version 1.5.x (2006)





…and thank you again for bringing these things to our attention. I have gotten more info from you about critical issues that need patching than from any other source.
Yes, good article. It didn’t occur to me that these exploits are being organized by someone in this manner. Another argument against allowing surfing at work.
Really? Against surfing at work? I don’t even know how I would do my job. That’d be like forbidding a mechanic from using a wrench. How about people just not be idiots and use some basic common sense? Including admins of networks at offices?
How can anyone mod the parent down 10+ times? There are people who think the security solution is not to use the Web at all? Please. Get a grip.
What exactly are you trying to say ??
Useful as always Brian – but a couple of thoughts.
1. It’s one thing for machines to get pwned by malware that exploits known vulnerabilities…but what about vulnerabilities that nobody except a few skilled bad guys know about? To quote the lovely Mr Rumsfeld “the unknown unknowns”. Perhaps a little article on this topic would be interesting.
2. On a related topic, your readers may want to know whether a 100% fully patched machine can be exploited by malware that exploits a particular vulnerability. Clearly, if unpatched, the machine can be exploited silently if the user opens, say, a malicious PDF. But what if they are working on a fully patched machine and are surfing the darker corners of the web and, for whatever reason, they click ‘yes’ when prompted to download and install a dodgy .exe. Will they still get ‘pwned’?
Enquiring minds may be interested in this…
thanks
Nick
>for whatever reason, they click ‘yes’ when prompted to download and install a dodgy .exe. Will they still get ‘pwned’?
Yes. A good example is the lure of videos with “You need to install this Flash Player upgrade to view”. I’ve seen knowledgeable computer users fall for this. The videos are anything from hot political topics to current news. The bad guys seeded the search engines with “Haiti Earthquake videos” before the legit sites – even if they had to recycle videos from previous earthquakes.
Contrary to popular belief, it’s not just those searching for pr-o-n that get bitten.
Yes, thank you for these helpful info!
For Firefox you can clearly see that the more updated the installation, the safer you are (ex.: 3.5.7 with 0% and 3.5.6 with 0,04%). Makes up a good slide for that awareness campaign…
Unfortunately, the stats won’t give any hint about the patch level for compromised IEs, just the main versions.
It can also be self selecting. The more current the patch level may also imply that the user is more paranoid about keeping bad software off their machine and less likely to be infected because of due diligence of their own rather than relying on the browser only to keep them safe.
Thank you, Brian, very interesting info. What I find strange however – why is the percentage of infected Firefox installations so extremely low? That’s ten Firefox infections out of thousands of visits, some with extremely outdated Firefox versions (and likely similarly outdated Java/Adobe Reader versions). Opera on the other hand has more than thousand infections despite not even being targeted directly. This sounds like the framework simply fails to run the exploits in Firefox most of the time, maybe a programming bug? At least I am not aware of any security mechanism that makes Firefox significantly different from Opera when it comes to plugin vulnerabilities.
Your guess is as good as mine, Wladimir. Here are a couple of guesses.
-Opera users don’t update as frequently. Opera has a notoriously clunky update process that involves manually downloading an updater and wholesale installing the program that way. I realize the attacks here are not (as far as I can see) Opera-specific, but that may explain things a bit if Opera users also are less inclined to update plugins for that browser.
-Also, two of the biggest drivers of exploit traffic tied to this particular eleonora installation were porn sites. It may be that people feel safer browsing these sites with an alternative browser like Opera, but never bother updating the plugins.
Brian: I would hazard a guess that noscript in Firefox is the difference. For example, many of the most powerful PDF attacks can be completely disabled by shutting down javascript. I don’t believe that, for example, Opera, has anything comparable to noscript. You can just turn off javascript in most browsers, but that can become painful pretty quickly; allowing selective activation of javascript is actually pretty painless.
I was wondering how long it would take before somebody comes up with this guess 🙂
No, NoScript certainly doesn’t make a difference here. The statistical data on addons.mozilla.org isn’t very exact but NoScript is definitely used by less than 1% of Firefox users. How likely is it that almost every user hitting that site had NoScript installed and had it configured correctly? Especially if you consider that the kind of users who knows how to use NoScript correctly usually wouldn’ t let his browser become that outdated (users with Firefox 3.5.2 haven’t updated their browser for half a year).
I use both Adblock Plus with ares2 Easy Privacy/List filter subs and NoScript it is a security marriage made in Heaven i would recommend to any Firefox user.
Opera has a way to bypass most internal means of content restriction. It has its own proxy network which Opera bills as “Turbo” offering 4x speedup of fetching pages because they compress the graphics. http://www.opera.com/media/b2b/Opera_Turbo_white_paper.pdf
People cruising for porn would turn to Opera for this “feature” alone to bypass locally deployed content filters like OpenDNS. If you have port 80 open Opera can reach its proxy caches.
FYI.. for those who want to have parental controls. You have to check and add if missing to your solution *.opera-mini.net to your banned list to stop Opera’s turbo service bypass. It’s been languishing to be approved as proxy in the OpenDNS system for several months now.
This may be true if you follow the security stance of content filtering from one end of the spectrum, however, rather than blocking certain sites that fall into various categories of questionable web surfing, why not only allow access to certain “approved” websites people need to do their job. Kind of a “deny-all” statement (for network admins) where if its not allowed, it’s denied… No web proxy, including Opera’s, can circumvent that type of security stance. 😉 Just my two cents. — Dallas
Opera’s major advantage for me in my recently jettisoned 128 RAM machine was its small size. The update fr/ 9.64 to 10.0 negated much of the advantage. My machine slowed immediately. I reverted back to 9.64 and maintained it until its last day. Wonder how many others didn’t update for similar reasons.
I somehow overlooked the country statistics, only noticed it now. Russia and Ukraine as top traffic sources for sure explains the high number of Opera users. I don’t think that many people changed browsers to protect themselves here, Opera simply is that popular over there.
I also just found this post on the Malware Intelligence Blog:
http://malwareint.blogspot.com/2010/01/state-of-art-in-eleonore-exploit-pack.html
…which seems to indicate that a version of Eleonore they’ve looked at actually includes a telnet exploit for Opera.
The malware intel post linked above says their copy of Eleonore has 13! exploits. I knew I wasn’t seeing all the exploits, which is why in my blog post I said “for a partial list of the exploits included in this pack”.
Weird, the only telnet vulnerability in Opera that I can find was fixed in 7.50. Also, the numbers of infections by exploit add up to 3539 – that’s only three less than the total number of infections by browser. They also make sense generally, I doubt that you are missing a significant piece of information somewhere.
As to updating plugins for browser – I think all users are notoriously lazy here, Java and Adobe Reader don’t make updating exactly easy. I would certainly not expect somebody using Firefox 3.5.2 to have most up-to-date plugins. Still – zero infections out of thousand visits.
In other words, a programming bug in the framework is still the most likely explanation to me. This programming bug could also be failing to receive notification on successful infection from Mozilla-based browsers. But that’s all just guessing of course.
My plugins for Firefox and its sister browser Seamonkey update themselves nearly daily. It happens automatically when I launch the programs. I think it’s the default setting.
Plugins and extensions are not the same thing. Adobe is only adding a useful auto-update for Adobe Reader now (finally), Java’s update mechanism was pretty broken until recently (left the old version on disk) and still isn’t exactly user-friendly (requires user action, tends to install crap if you aren’t careful).
Well, the bad guys need to do marketing too. So they list all kinds of stuff even though it might have been fixed years ago – all in an effort to make it look like they check for all sorts of vulnerabilities..
They actually do market very well and their target audiences are buying…You have to realize that they don’t need to sell the latest 0-day in their packs. They only need to have exploits that are recent enough where people haven’t patched to address the new vulns (which most outside of the infosec world dont)
Hi Brian! for default, the last version of Eleonore Exploit Pack have 14 exploits.
http://jorgemieresblog.blogspot.com/2010/02/eleonore-exploit-pack-y-su-evolucion-en.html
We obviously missed our calling. Who could have known people would insist on using such a daft unfit OS for so long? Thank goodness some of us know Russian.
Unfit OS? The issue is not the OS, the issue is applications – Adobe & Java.
The OS just magnifies the problem. Especially since most people still have XP machines or turn off UAC while running as admin accounts.
Barely a speed bump for any malicious code to escalate to SYSTEM level.
No. The OS is the ultimate issue. Your examples are only the attack surface. That’s where the malicious code breaks through. But once the code has broken through, it has to be able to do something. On secure systems there is not much to do except twiddle your thumbs. On Windows it’s the 4th of July, a veritable smorgasbord for the hackers. You’d better take that course in security your boss offered you. And try out some other OS just for the weekend, just for the fun of it. You might learn something.
Mac users will want to know whether these “browser agnostic” exploits are also platform agnostic? Safari, Java, and Adobe have PC and Mac versions, so presumably the exploits that target those three will also work on Macs. Then perhaps the more important question is: does the malware installed by Eleonore and its ilk run in OSX? Or is it specific to Windows PCs?
No, these exploits generally won’t work on Macs, because they’re targeting Windows-specific bugs and other issues. (For example, stack overwrite exploits depend on the exact way that stack frames are laid out, which is different for each OS.)
Also, Safari on Mac doesn’t use any Adobe software to display PDFs, rather Apple’s own PDF renderer. (Not sure about Firefox.) And on OS X 10.6, plugins like Flash are sandboxed in a separate process, so exploits shouldn’t be able to mess with anything outside that process, making them pretty much harmless. (The same applies to Chrome on all platforms.)
I find this questionable. I believe that Chrome has always run plugins out of process on Windows. Assuming this is correct, then how could the exploit kit *know* it succeeded unless it had some way of talking to the code it hoisted into the chrome plugin host?
It’d be pretty bad if the toolkit just claimed that a crashed process equaled a successful exploit. I’m assuming that Eleonore is successful because it’s reliable and doesn’t cheat. Sure it’s evil, but it’s a business and it presumably sells because it gives good results.
Ah. So, the designers of this exploit pack intentionally inflate their infection numbers in order to drive sales? Interesting theory, and a very plausible one.
Oh, no. I meant the opposite. I’m assuming that their exploits really are working against Chrome. Just because something is out of process doesn’t meant it’s protected.
It’s possible they are inflating, but I’m actually assuming that they are not lying and that their exploit really does work in the out of process host.
There is no honor among thieves as the saying goes.
Packing in more functions is at zero cost to the packager.
Back in olden days when floppies, then CDs were protected via various means, “copy packs” were common. They would always have the most obscure methods available as well as the common ones. It was zero cost to include, as the method was already heisted from another bootlegger. The only cost to the packager was loss of street cred or “trust” if the wrong warez team was crossed.
To the buyer it follows the all too human reaction, just 8oz more for a penny more. It induces envy and greed into the decision to purchase. Nothing really new here.
Even if Chrome runs plugins in a separate process – the exploit code will execute in that process then. It will most certainly be able to access the Internet meaning that the exploit pack will count this as a successful infection. The real question is whether this process will have sufficient privileges to store the exploit on user’s system. According to comments on my blog the plugins still run in a Chrome process with user privileges – meaning that this isn’t a sandbox (yet?) and won’t really help against exploits.
Chrome (like upcoming Firefox, and Safari on OS X for Flash) runs its plugins out-of-process, but not at reduced privilege — unfortunately most plugins for the NPAPI don’t function when running in low privilege mode, so there’s not much other choice.
Because of that, though, exploits are very likely to function just as effectively out-of-process as they do in-process. I doubt any go to the trouble of politely calling back into the browser to do their dirty work, rather than just running the shellcode directly.
Knocked my socks off with kolwnedge!
OK I’ve seen dumb but then I saw this. For an exploit to work, it has to have code specific to the OS and the processor. The same malicious code that wants to put a birthday greeting in C:\Windows\System32 is not going to be able to put the same code ready to run on a different OS with a different executable architecture in /usr/bin. Take that course you’ve been thinking about.
Uhhh … unless the exploit is written in Java, JavaScript, or some other cross-platform language.
Time to make noscript the default web browser plugin.
Specifically at work, I would filter websites and only allow scripts for trusted sites.
Please keep in mind that a “trusted” site today might be an exploited site tomorrow.
One of the problems with whitelists is that just because a page you visit is run by someone you know doesn’t mean that their hosting infrastructure is safe.
Worse, if the DNS path between you and them is bad and you don’t visit them exclusively over a properly established SSL channel, then you could one day trust an attacker who didn’t even need to attack the site, simply by visiting a dangerous WiFi access point.
There’s some work on a way to mark sites as ‘https only’, which would in theory help here, but that only protects against evil DNS, it doesn’t protect against the case where the site itself is hacked — and this happens. I’m sure you can find plenty of cases of this in reading Brian’s back issues, although I don’t think I’ve seen many specific writeups of this in krebsonsecurity.
As a reminder, the premise for the article is “If you happen to stumble upon a Web site”. That is more along the lines of “if you visit a site which should have been safe but your antivirus complains”, instead of “If you decide to go off into the scary part of the internet hunting for bad guys”. So the article is really talking about places where the server was somehow hacked.
Depends on what your goal is. If you want to annoy users – sure. If you want to make their browsing experience more secure – helping them to keep plugins updated would be the way to go (Firefox 3.6 made good progress towards this goal). Running plugins in a separate process might help as well – Chrome is doing that, Firefox nightlies are testing this feature as well (not switched on by default yet).
I agree, but patching only helps for preventing against known issues… Running plugins in a separate process sounds interesting.
One step at a time – right now the biggest problem is users who are not patched up. Zero-day exploits are rare and don’t usually get widespread before being patched. If we had most users patched up that would already change the landscape quite considerably. And then we could start worrying about protecting against unknown threats and whether requiring the user to know which sites to trust is the solution.
http://www.tcmagazine.com/forums/index.php?s=b335cbf7063ef7160e23ce729d02f4d0&showtopic=2662&st=0
Nice to see what I have been putting out for years now (many years, as far back as 1997-1998 in fact per the “wayback machine” -> http://web.archive.org/web/20010202174900/www.ntcompatible.com/article1.shtml & the original edition of my security guide of which the above is only the current “modern day” version & even NeoWin, the home of the “naysayers online” imo @ least, even rated it well in 2001 here -> http://www.neowin.net/news/apk-a-to-z-internet-speedup–security-text ) is only NOW making the “mainstream online press” say the same stuff years later…
OR?
Or, has Mr. Krebs here been reading slashdot lately, per point #3 in this post by myself there -> http://tech.slashdot.org/comments.pl?sid=1512306&threshold=-1&commentsort=0&mode=thread&cid=30782898
“Inquring minds want to know”…
(Imitation? Truly IS the sincerest form of flattery)
Alexander Peter Kowalski
apk
P.S.=> Of course, this type of thing is pretty much “common-sense” to anyone that really has an understanding of things “PC-Computing” also… & like the OUTER LIMITS episide, “THE FINAL EXAM” (see it, otherwise this point is lost)? Per its main protagonist SETH & his statement of
“When a Science is ready? It can’t help but make the next discovery”
In when he speaks of nuclear power’s originations…
So, COULD be either way, but the dates of my URL’s above do seriously tend to favor my statements here per my URL’s above as evidence to said facts & statements I have just made! apk
Brain,
Another good article. It is scary to think exploits are being organized and marketed in this manner.
Didn’t the last major update to Firefox check the local version of some common plugins upon first start, with a link to upgrade them? That may explain why few Firefox users are affected.
Looking at the Opera stats, I’m running 10.10, all of the numbers are for 9.X. So much for people upgrading.
Q: Are there any stats available by O/S?
You have to look at the IE graphic, that’s where Opera data starts – some people were using Opera 10. Not terribly many of them though. This could be partly because the data isn’t current, as Brian mentions this is a few weeks old. On the other hand, it cannot be *that* old, most Firefox users are on 3.6 which was released mid-December (Opera 10 was released in September). Generally – yes, Opera users aren’t exactly fast to update, this has been covered in media before. This will hopefully change now that Opera has an autoupdater.
I meant: “most Firefox users are on 3.5.6”
Opera versions 10.x identify as 9.8 because browser sniffing scripts were interpreting 10 as 1.
Opera also runs on NintendoDS and Wii supposedly supporting Opera 9 capabilities. Opera Mini runs on mobile devices. I don’t think these platforms are accounted for in the hack OS statistics or could be mixed in with PC users.
However this cross platform capacity of Opera opens up a new vector for attacks on privacy and security as these platforms are not hardened / managed to the same extent as PC’s.
Brian, great article, which I hope many many people will read (and then start patching !) – I certainly intend to spread it in my neck of the woods, even if I have to help people over the language barrier ! One slight error you might wish to correct – vulnerability statistics for Opera 10 and Opera 10.10 have been listed under those for Internet Explorer, rather than under those for Opera and Safari….
Henri
These guys aren’t inflating their numbers. They are literally playing the numbers game and blanketing their exploits. You have to realize the average home user is not updating their FF/IE/Opera/Adobe Reader. They will see an Adobe Update and select “Delete All” and not have it update. The problem is the vast masses do not understand the risks of having these out-dated software and no one is really telling them the risk. They believe that their 60-day trials of AV that came with their computers will protect them from future and current risks.
This is only half the story– how does this affect the underlying operating systems? Windows is notoriously porous and malware-friendly. What about OS X, Linux, the BSDs? Even in a plain-vanilla *nixish system with the old-style Unix file permissions, and none of this fancy new SELinux and sandboxing and all that stuff that foils privilege escalation– it seems that a browser exploit would be pretty toothless.
A few questions. The first is has anyone used this exploit package? If so, when it detects an exploit, does it automatically push out malware? Or is the user required to click something before hand?
My guess is that the user does not need to click anything, it just pushes the malware.
Your thoughts would be greatly appreciated.
Depends on the exploit used, how the computer is configured, and what vulnerable components you have. Most of these exploits are “browse and own”. The PDF exploits might require user-interaction depending how you have your web browser configured. Most systems I’ve seen are configured to automatically launch PDF files without user-interaction as opposed to prompt or save. Sun Java exploits do not require user-interaction and most people don’t upgrade to the latest Sun JRE or remove older vulnerable versions.
Brian, good article. I cannot find any statistics for Safari, either win or mac.
Are there any?
Thanks
David
yup. see this graphic, from the post above
https://www.krebsonsecurity.com/wp-content/uploads/2010/01/bot6.jpg
Norton caught this attack twice. If I have the IP address and the country of origin, is there anything I can do to stop these peeps?
good analysis Brian, any info on the actual obfuscation methods used by the pack.. any source that is either live / distributing malware. i need this for my research..
here is some attempts from my end over phoenix
http://tusharvartak.com/2010/09/28/underground-economy-3-phoenix-exploit-kit-fake-antivirus-and-live-cc-server/
Regards,
Tushar Vartak
I miss the Mcdonalds Arch Deluxe 🙁