Amid all of the media and public fascination with threats like Stuxnet and weighty terms such as “cyberwar,” it’s easy to overlook the more humdrum and persistent security threats, such as Web site vulnerabilities. But none of these distractions should excuse U.S. military leaders from making sure their Web sites aren’t trivially hackable by script kiddies.
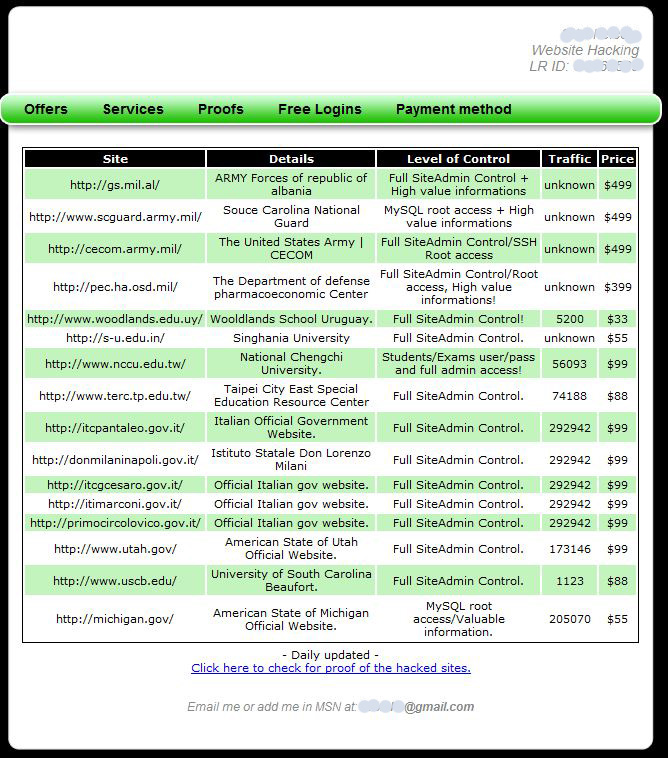
Security vendor Imperva today blogged about a hacker who claims to have access to and control over several top dot-gov, dot-mil and dot-edu Web sites. I’ve seen some of the back-end evidence of his hacks, so it doesn’t seem like he’s making this up. Perhaps out of deference to the federal government, the Imperva folks blocked out the best part of that screen shot — the actual names of the Web site domains that this hacker is selling. For example, the hacker is advertising full control and root access to cecom.army.mil, a site whose stated purpose is “to develop, acquire, provide and sustain world-class…systems and Battle Command capabilities for the joint warfighter.” It can be yours, for just $499 (sorry, no credit cards accepted; only the virtual currency Liberty Reserve).
Here is an unredacted (well, mostly) shot of that site:
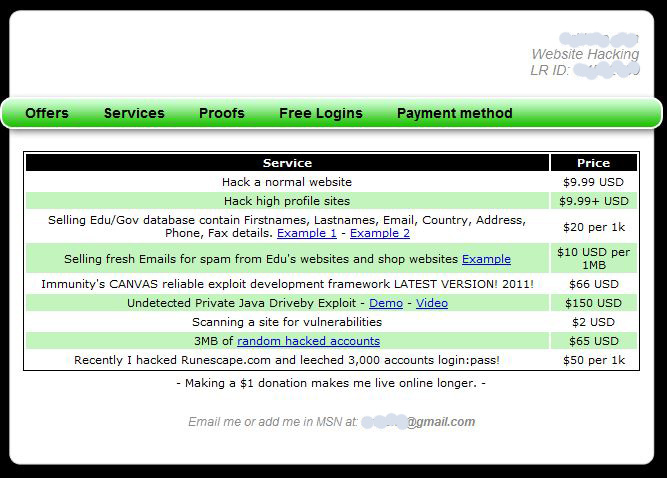
According to Imperva, this enterprising hacker is also selling info personally identifiable information from hacked sites, for $20 per 1K records. The company mined this hacker’s postings on other forums, and found evidence that he was able to hijack the sites via SQL injection vulnerabilities, most likely with the help of an automated vulnerability scanner.
I find it ironic that one of these sites allegedly for sale is the Department of Defense Pharmacoeconomic Center, which is a DoD site tasked with “improving the clinical, economic, and humanistic outcomes of drug therapy in support of the…military health system.” In all likelihood, if access to this site is purchased, it will be by someone looking to plant links to rogue online pharmacies of the sort frequently advertised in junk e-mail. People who get paid to promote these rogue pharmacies typically do so by hacking legitimate Web sites and including links back to fly-by-night pharma sites, and they particularly like dot-mil, dot-gov and dot-edu sites because search engines tend to treat links coming from those domains with more authority than random .com sites.
By the way, that “Undetected Private Java Driveby Exploit” that this guy is selling is none other than the social engineering trick I blogged about last week here.




Right on the button again Brian, excellent.
APT is not the enemy, stupidity is.
Stupidity should be on the OWASP Top 10.
Maybe we need to form a new organization, Open Web Application Stupidity Prevention? 🙂
Guys, sometimes I tie warm pickles to the bottoms of my feet.
Nobody does IT security worse than the government!
True, but not the way you mean it.
“nobody” does website security worse, because web admins come and go, leaving “nobody” minding the site, servers, and DNS.
Working as a contractor for government (related) websites, the pattern is often like this:
1) agency contracts us to develop and host a site for them
2) during development, they want to change the contract to host it themselves but let us provide admins
3) sometime after site goes life, support contract is cancelled (or runs out and isn’t renewed).
4) (tentative) someone leaves the site up, might even add new content, but forgets there’s noone taking care of it
4a) (tentative) as a result, security updates are never installed, leaving the site wide open to attacks
This is scary stuff. Is it that easy to hack these sites? Our government is sorely lacking in cyber-security and this has been published on other blogs. What will it take to finally put the recources in place to resolve these problems? Our political system seems reluctant to do much about it. I guess that it will take a major failure before it is addressed….like a stoplight at an intersection after so many deaths.
Or prohibition of box cutters on airplanes.
Maybe y’all ought to stop clamoring for cutbacks in GOV spending and freezing Fed employee salaries at a time when the GOV needs to hire talented people to tighten up its cyber security…
Recruiting talented people into frozen pay scales is a non-starter.
Maybe the government should start requiring a full audit of each public facing site. If a site is not authorized it has to be off the net. One tool that would help here that came out today is the new XSS Ray tool. I checked a few of my personal sites and it does a good job.
https://chrome.google.com/extensions/detail/kkopfbcgaebdaklghbnfmjeeonmabidj
US Gov already does have an avalanche of recommendations, compliance docs & standards.
However given the budgetary constraints its a dance of what is doable and what can be budgeted.
http://csrc.nist.gov/publications/PubsSPs.html
This is the non mil standards, private or state .edu may or may not have to abide.
No matter how many rules you have to keep you have to have independent audit.
Few auditors in my experience actually have deep and practical field experience on these matters.
Many of their not public facing websites are the same way.
These sites are targeted for SEO reasons and because once you break in, it appears to be unlikely anyone is going to notice and kick you out. But to put some perspective on things, these sites are not important resources; example: the Souce (sic) Carolina National Guard site is propped up to pimp their dedicated museum. I’d bet the shirt on my back that these sites were dev’ed and are hosted by super cut-rate contractors. There (probably, hopefully) isn’t any risk to real gov’t data going on here. That’s why this guy can safely sell off website control but charge separately for the Personally Identifiable Information; you can’t access the database he/she compromised by way of these sites.
The only risk is embarrassment and phishing attacks on their users, and the government probably doesn’t give a crap about either of those things.
I run a university website and I had a brief moment of horror as I scanned through the list of URLs. If mine had been listed here, my weekend was totally fucked.
Why would your weekend be ruined?
Diligence, Vigilance, orderly and meticulous administration ought to bring peace of mind for one’s weekend.
I’ve inherited garbage dumps of systems and over time have been able to go home and even on vacation knowing that if even the barn burned down, it would be work but not superman’s kind of work to get things back in order.
If you got the moment read through the stuff at http://csrc.nist.gov/publications/PubsSPs.html
While not bullet proof (not that anything ever is) it should give a framework for defense in depth.
If anything at the .edu, more that business, its also about securing the physical to logical space. Anyone who hooks their laptop into your net is of course vetted not to have leyloggers, viri and such right!
If anything, such stories give credibility to a cost case when asking for a budget for decent firewall(s), network hardware which supports isolation of univ admin, from faculty, from students, from guests as well as a decent backup system for critical systems like the registrar system, HR and other stuff which the Univ should invest in as part and parcel of being a university.
I’m a firm believer in compartmentalization. Even if your website gets compromised it should have been architected to disallow any backflow into the next deeper layer of network. If these guys didn’t dmz they ought to be sent back to school.
My team uses Drupal for everything now and diligently keeps its core and all modules up-to-date, so if our site was hacked, it would probably be bad news for all Drupal sites out there. But that doesn’t mean a thing to the administration – if it got back to them that our site was publicly listed by a hacker who was selling full control of it for $99, I don’t know whether they’d ever fully trust me again.
Its good you use a methodology and process to control web content. But thats only a small piece to the whole effort.
IT security has set itself up for a fall when it comes to how its compared to real world security. Somebody breaking into a lab or office (also the associated IT) and misusing it should rarely cost the actual worker bee their job if they were doing their job as defined by the higher powers. It ought to be a black eye to the higher powers that they cut corners and didn’t examine and manage well their investment in security.
I’ll draw a parallel directly to IT, no Dean or President at institutions say locks & paid security staff are nuisance or waste of money;
1) the liability is too high if somebody gets harrassed/assaulted on a campus.
2) if the student records are easily tampered with then the institution risks possible loss of accreditation
Now if somebody hacks the internal system and puts private student info (addresses etc) at risk or mucks with the registration/financial aid systems shouldn’t the same standard be applied?
If the institution approved what was architected for security: firewalls, network compartmentalization, vetted systems and programs all of which are well maintained, lastly having physical security was sound then it would be a shame if they lost trust in their own personnel.
If after all diligent work was done and you got outsmarted…. then the “managers” need to contact law enforcement per process at that point.
The basic security guard deters and impedes the opportunity for the occasional car theft. The IT dept does the same for website vandals, DDOS and script kiddies. However the basic security guard is not going to uncover nor stop the car theft ring. So to neither will the IT dept uncover nor stop the IT mafias. The info about break ins IT depts have, has to be admitted, passed on and correlated into patterns with law enforcement who can then act upon crimes.
Recall ZeuS. Would it had been stopped by law enforcement earlier if bank managers didn’t cover it over for so long?
The solution is inefficient and often ineffective but actually has been working in human society.
Hokie dokes. Yes. Agreed. But I was just answering your question, “Why would your weekend be ruined?”
Dear Brian, although in my estimation a small portion of your articles are very high quality I’m afraid this accolade cannot be awarded to this particular one.
This is nothing to do with “cyberwar” even as the hysterical media portrays this made scenario. Frankly the idea that various military and educational institutions should be locking down every single website hosted under the relevant TLD is preposterous. A simple Google search for blogs and forums to link spam (as I carry out link spamming in my other career) reveals that the above happily hand out .edu and .mil hosted blogs and forums to anyone who happens to be associated with whatever garbage they’re associated with – the university will allow grad students to host blogs under .edu for example.
To call the subversion of these sites part of a “cyberwar” is frankly ludicrous. And I see, as usual for this blog, people who are essentially clueless and incapable of analysis are making comments to the effect that this is a major government security breach and the US is losing a “cyberwar” because of this and other such nonsense. I feel you are doing a grand disservice to your readers, at least the ones in the category mentioned above, by leading them up this path of hysteria.
You quite easily could have pointed out the fact that this hacks have very little consequences to anything important and that essentially stopping them is impossible owing to the nature of the situation explained above combined with the fact that no platform can be made secure in reality (although a worthy aim to strive for nonetheless).
I realise this would have made your story seem unimportant and somewhat pointless but then again you wouldn’t be leading your less knowledgable readers who struggle to comprehend anything beyond ensuring that have the latest AVG updates installed on their Windows-powered Dells up the garden path and misleading them into thinking this is an attack on the integrity of the USA.
(BTW if you have AVG installed your an idiot)
Hrm. I think maybe you just read the headline and then posted your comment? I’m the last journalist who will use the term “cyberwar” in a story with any seriousness.
Do me a favor and read the post in its entirety, and then tell me if you think our views are that distant from one another on this topic.
Thanks!
Why not just link to the site ? http://www.srblche.com/
If you are going to redact an image, I suggest that you don’t leave the original right beside it, with a slightly different name.
Take away the “1” in your image, and you get this:
http://krebsonsecurity.com/wp-content/uploads/2011/01/dotmilorggovsale.jpg
There is a lesson here – even the most security conscious people can make dumb security mistakes.
Info sec is a never ending battle, and we need to constantly check and recheck our work.
good catch, but next time leave the comment without the link – Brian is man enough to give kudos for that
what you did was kind of like someone finding an exploit and putting it in the wild without telling the vendor first and giving them a chance to fix it.
If they really ignore it, let it rip, but tell the authors first and you’ll get your credit.
I agree. Original site is just a trivial google search away. Security by obscurity? Give to your readers some credit, Brian.
Whole another thing is why this site is still up and running?
Quote: Whole another thing is why this site is still up and running?
It isn’t any more. It looks like the host (sh3lls.net) suspended it.
It is up again
More like “Crabs” amirite?
The military has never spent hardly any money on the NIPRNET. It is all just PR and training.
To say the least Brain screwed up with this post… Is is commonly known among any hacking community that srblnce is a useless scamming idiot.
/Offers/
If these domains were indeed compromised and he planned on selling them why would you make the site open to the public? Anyone could view the page (especially an admin of said site), then realize they were compromised (if they actually had been) and fix the issue.
– The only reason for making this site open to the public is to entice as many poor idiots as possible who think the sale is real.
-“Some” of the sites may have really been hacked but there is no way he will actually sell any of them, and there is a good chance he isn’t the one who even compromised the sites… (Just pasted screenshots from someone else)
/Services/
“Undetected Private Java Driveby Exploit”: This is a simple java downloader, nothing more. It has been around for YEARS, there is nothing private about it.
“Recently I hacked Runescape.com and leeched 3,000 accounts login:pass!”: If he had really hacked such a site only a moron would take “just 3k” logins, and not do anything else.
“Immunity’s CANVAS reliable exploit development framework LATEST VERSION! 2011!”: 66$… really? Do you have the holy grail for sale for $10 too?
Summary: Brain has inadvertently (hopefully), just promoted scamming worldwide and probably caused a few wannabe hackers a lot of $ in the process. This entire story should be redacted or at least edited to some extent to be put into context, otherwise it is purely bullshit.
amendment
/Offers/
If anyone took the time to view this page for more than 60s they should know immediately it is fake. I forward your attention to the supposed .gov.it sites and their corresponding traffic counts. Notice anything strange? Oh yeah they are all IDENTICAL, this is statistically imposable.
I agree regarding Runescape. Jagex Ltd (the fellows who run Runescape) are definitely not a bunch of idiots. I don’t think they’d leave them selves open to Mr. $9.99-a-hack.
itcgcesaro.gov.it and some others won’t load without the www. Funny he included the full URL with http://, as it would lead you to believe the site doesn’t exist if you didn’t think to try the www.
Iskorpion claims to be the one who hacked itcpantaleo.gov.it; at least he knows to use the http://www., so his claim seems a bit more credible:
http://www.linux-h.org/attack/?id=120429
While it’s still in Google cache, there’s a discussion about Srblche by his fellow hackers here:
http://webcache.googleusercontent.com/search?q=cache:XU6t4iPLZLAJ:www.hackforums.net/showthread.php%3Ftid%3D977900+itcgcesaro.gov.it&cd=2&hl=en&ct=clnk&gl=us
Ryan, i am a vivid reader of blog but this post made you lose a lot of credibility on me. It’s plain lame, and Srblche was a notorious ripper on uNk.
lol.
ps: russia never sleeps 😉
I think ‘srblche’ is not something new. I’ve heard about hacked data for sale a few years back on an IRC channel.
lol “sccript kiddies” use my tools.
Srblche’s the most active hacker at HF. I hope instead of hacking critical websites. He develop something useful to the security community.
So who’s stupid now! Clear demonstration of why not to accept the suggestions that are often repeated on this site to rely on user observation as a security tool and that educating users is the solution. The people behind such scams are smart it’s not wise to take them for granted anyone can be fooled. The key to preventing a significant majority of attacks on valuable assets on networks if the research is correct is to prevent access to logon credentials and yes that requires a software solution.
I agree when you get down to the latter 3rd of these comments. This is pretty low priority. The serious guys are going after the big stuff and don’t waste much time trying to get in. We all know about these info for sale sites, many in africa, selling ss and cc#’s. Personal accounts getting hit for a grand isn’t much of interest to law enforcement and they’re so far behind anyway.
Good security IT people have their own set of tricks and usually don’t talk because it’s worth more in salary in the long run.
What is scary is the next gen. of hacks exploiting hand helds that have access to company and banking info and with thousands of down loadable apps available. Pick pockets will be (and probably are) skipping wallets and lifting ipod’s. You have to admit the big players are concerned about this issue, too.
Just look at the military hacks in 2011 alone. I doubt these hand helds are a hard nut to crack. Can you imagine farming the air waves in wall street and times square? I’m sure somebody’s working on it. You have to admit hard wiring a network is becoming obsolete.
I agree with many of the comments that the really juicy stuff probably wouldn’t be listed in this manner as I am sure monitoring services are watching it as well.
That being said what do people recommend as the best measure a small operation might keep track to validate that their sites are not on these lists (obviously securing a system helps prevent it but I am talking more about a detective control).