Stolen or easily-guessed passwords have long been the weakest link in security, leaving many Webmail accounts subject to hijacking by identity thieves, spammers and extortionists. To combat this threat on its platform, Google is announcing that starting today, users of Google’s Gmail service and other applications will have the option to beef up the security around these accounts by adding one-time pass codes sent to their mobile or land line phones.
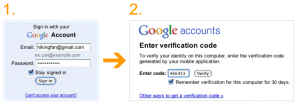 For several months, Google has been offering this option to business customers and to “hundreds of thousands” of regular users who lost control over their accounts due to password theft, said Nishit Shah, product Manager for Google Security. Today, Google will begin rolling this feature out to all users, although it may be available to all users immediately, Shah said.
For several months, Google has been offering this option to business customers and to “hundreds of thousands” of regular users who lost control over their accounts due to password theft, said Nishit Shah, product Manager for Google Security. Today, Google will begin rolling this feature out to all users, although it may be available to all users immediately, Shah said.
“It’s an extra step, but it’s one that significantly improves the security of your Google Account because it requires the powerful combination of both something you know—your username and password—and something that only you should have—your phone,” Shah wrote in a blog post published today. “A hacker would need access to both of these factors to gain access to your account. If you like, you can always choose a ‘Remember verification for this computer for 30 days’ option, and you won’t need to re-enter a code for another 30 days. You can also set up one-time application-specific passwords to sign in to your account from non-browser based applications that are designed to only ask for a password, and cannot prompt for the code.”
I set up the 2-step verification process for my Gmail account, and found the process to be quick and painless, if a little involved. I choose to set it up to call my Skype line and read the code aloud, and the call came in three seconds after I hit the submit button. The setup wizard then gave me 10 backup codes to use in cases when for whatever reason I don’t have access to my Skype account. Another setup page offered the ability to add a secondary backup phone to send the code via SMS/text message, or automated voice message.
A final page warned that “Google has detected that you need to create application-specific passwords” to use applications like mobile Gmail, desktop Picassa or AdWords editor. I skipped this step because I don’t use those services, but was confused by the prompt that said “Your two-step verification settings have not changed.” When I went back again and ran through all the setup options, Google’s system did not prompt me to add the application specific codes, but instead gave a page with a button to “turn on 2-step verification”, which signed me out of my Gmail and then called me with the one-time code. At the corresponding login page, the option to “Remember this computer for 30 days,” was pre-checked.
 This feature is undoubtedly a useful tool for securing accounts; the challenge will be making users aware of the option. For now, the option to enable it is tucked inside of the “user settings” panel in Gmail, an area into which many users probably never venture. And to be sure, many users probably will end up locking themselves out of their accounts, despite the availability of multiple means of obtaining a secondary code that Google has offered. On top of that, threats to mobile devices or cleverly-designed social engineering attacks could still trick users into giving away the codes.
This feature is undoubtedly a useful tool for securing accounts; the challenge will be making users aware of the option. For now, the option to enable it is tucked inside of the “user settings” panel in Gmail, an area into which many users probably never venture. And to be sure, many users probably will end up locking themselves out of their accounts, despite the availability of multiple means of obtaining a secondary code that Google has offered. On top of that, threats to mobile devices or cleverly-designed social engineering attacks could still trick users into giving away the codes.
Still, the 2-step verification process is more robust than many banks are offering their customers for online authentication these days. Given the epidemic of commercial and consumer e-banking account takeovers aided by password theft, it would be nice to see financial institutions taking a cue from Google’s offering.




Brian,
As you note it is an improvment in security over and above that that many banks offer.
And as some of your readers will know the use of a side channel for one time authentication is something I have been banging on about for well over ten years.
However there is a fly in the ointment which started around the time Nokia launched the first smart phone.
The security on these smartphone platforms is by no means what it could be and thus if the same phone is used for browsing as well as the sending of the authentication token it is potentialy game over.
That is the side channel nolonger exists.
I’ve been looking forward to this on my personal account ever since it was announced for business customers.
I wonder how it will work for accounts that use Google as an OpenID provider? Will they need to use 2-factor when those sites attempt to check-in to Google? Will I need to use 2-factor authentication when logging on to my Google OS laptop? Or when my Android phone syncs?
None of these would be horrible and I’m looking into figuring out how these will work.
I applaud Google for this implementation. Although interestingly, I was surprised to see 10 backup codes given by default. Are these codes somewhat permanent, in that they are usable for a long period of time? How are they transmitted? How are they stored? I understand the need for these, but I think I’ve also seen them used as the weakest link in other similiar OTP systems. Thoughts? I don’t think of security as binary, so any OTP use is better than none, but I’m starting to threat model a bit here.
the back up code is useable only one time so 10 codes u have, can be use 10 times only..
yo need to check n reply an important email and that time.
1) phone is out of network n not able to get the text.
2) Phone is off and no power line to put in for charging.
3) you’ve lost your phone somehow.
4) somehow everything is perfect but google fail to send u text msg over ur phone.
i think in these kind of time backup code is useable.
just save it in ur phone and computer u use in a place only u kno where to find it..
make text msg pasword protected. so if somehow someone kno ur email n password and gain assess to ur phone ur basic phone security may save ur google account.
I hope it helps 🙂
“Given the epidemic of commercial and consumer e-banking account takeovers aided by password theft, it would be nice to see financial institutions taking a cue from Google’s offering.”
As an Online Banking manager at a community bank, I can say that I would implement this in lieu of token authentication in a heartbeat if it were offered by our software provider. We coule eliminate the cost of tokens while improving security at the same time. Since the purchase price of the tokens is about 10 bucks even when buying in bulk, a bank with any number of customers would save hundreds of thousands of dollars easily by implementing this instead of tokens.
OTP systems aren’t the perfect solution. As with an authentication solution they can be bypassed. I’ve worked with a few Europeon banks that have been using OTP for years, and while it does cut down on losses, the bad guys have been getting around them for years. Usually they do it by compromising the end-users desktop, making a hidden change to the user’s transaction, using a hidden browser session, and then letting the user put in the OTP or code to approve the transaction. Unfortunately, what the user thinks is happening and what is happening (at the bank) is different, and neither side is aware. Of the bad guy changes the victim’s phone number to a new Skype one, so that the codes are sent to the bad guy instead. OTP helps prevent someone from pretending to be you from some other location, but does not prevent Man-In-The-Endpoint attacks. And if they get your OTP (or emergency backup codes), they can pretend to be the person from another location. OTP is good…can’t complain…but it’s not like the bad guys won’t see it as anything but another temporary bump in the road.
secret question: what is your favorite color?
answer: blue
JACKPOT!
I’m afraid a thief would be more likely to steal my cell phone than my password. If a cell phone has sufficient information on it for the thief to guess the gmail account of the owner, that’s another weak link.
So how does all of this play out for a g-mail account that is forwarded to a Blackberry then ???
I work for Microsoft full-time and I didn’t realize until just now that Live\Hotmail has had the same functionality (or near it) since May of last year. Right on the main logon screen is a ‘Get a single use code to sign in with’ option.
This is welcome step by Google to add multi-factor authentication to all its users. The problem as I see it, however, is that this solution is almost worthless if a user accesses Gmail from a mobile device and uses the browser to “remember” the password. Now the attacker (thief?) has both factors of authenticity: the credentials AND the mobile phone device.
(It’s also a fun coincidence that PhoneFactor–provider of two-factor authentication–is an advertiser on this site!)
I checked for this on my Gmail account and it is not yet available. It is apparently only being rolled out gradually as the message says it will be available on my account and others “soon.”
I need your opinion on a free download called CCleaner v3.04 it cleans up your computer and Added support for Windows 7 SP1.
Added Internet Explorer UserData cleaning and management.
Added Safari cookie management.
Added support for SongBird and Thunderbird embedded browsers.
Several big improvements to the Registry cleaner.
Added cleaning for Excel Viewer, FeedDemon, WinDiff and Last.FM,
Free Download Manager, Internet Download Accelerator
and Internet Download Manager
I heard that this is a spy ware software do you believe so?