The Federal Bureau of Investigation warned this week that cyber thieves have stolen approximately $20 million over the past year from small to mid-sized U.S. businesses through a series of fraudulent wire transfers sent to Chinese economic and trade companies located near the country’s border with Russia.
 The FBI said that between March 2010 and April 2011, it identified twenty incidents in which small to mid-sized organizations had fraudulent wire transfers to China after their online banking credentials were stolen by malicious software. The alert was sent out Tuesday in cooperation with the Internet Crime Complaint Center and the Financial Services Information Sharing and Analysis Center (FS-ISAC), an industry consortium. The alert notes that actual victim losses are $11 million, suggesting that victim banks were able to claw back some of the fraudulent transfers.
The FBI said that between March 2010 and April 2011, it identified twenty incidents in which small to mid-sized organizations had fraudulent wire transfers to China after their online banking credentials were stolen by malicious software. The alert was sent out Tuesday in cooperation with the Internet Crime Complaint Center and the Financial Services Information Sharing and Analysis Center (FS-ISAC), an industry consortium. The alert notes that actual victim losses are $11 million, suggesting that victim banks were able to claw back some of the fraudulent transfers.
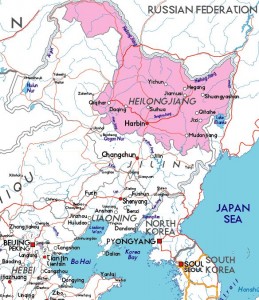
The FBI says it doesn’t know who is behind these fraudulent transfers, but that the intended recipients are companies based in the Heilongjiang province of the People’s Republic of China, and that these firms are registered in port cities that are located near the Russia-China border. The agency says the companies all use the name of a Chinese port city in their names, such as Raohe, Fuyuan, Jixi City, Xunke, Tongjiang, and Donging, and that the official name of the companies also include the words “economic and trade,” “trade,” and “LTD”. The recipient entities usually hold accounts with a the Agricultural Bank of China, the Industrial and Commercial Bank of China, and the Bank of China.
From the advisory (PDF):
“In a typical scenario, the computer of a person within a company who can initiate funds transfers on behalf of the U.S. business is compromised by either a phishing email or by visiting a malicious Web site. The malware harvests the user’s corporate online banking credentials. When the authorized user attempts to log in to the user’s bank Web site, the user is typically redirected to another Web page stating that the bank Web site is under maintenance or is unable to access the accounts. While the user is experiencing logon issues, malicious actors initiate the unauthorized transfers to commercial accounts held at intermediary banks typically located in New York. Account funds are then transferred to the Chinese economic and trade company bank account.”
The alert said the unauthorized wires range in value from $50,000 to $985,000. While most transfers tend to be toward the upper end of that spectrum, “the malicious actors have been more successful in receiving the funds when the unauthorized wire transfers were under $500,000.” In addition, the attackers initiated fraudulent automated clearing house (ACH) transfers to money mules in the United States within minutes of conducting the overseas wire transfers.
According to the alert, the thieves used a variety of malicious software to steal victim online banking credentials, including the ZeuS Trojan, backdoor.bot and Spybot, all malware families that let the crooks steal passwords and control infected systems remotely.
None of this should be news to anyone who has followed my reporting on this type of crime. I’ve written more than 70 stories over the past two years about these type of attacks. Earlier this year, victims at three Iowa banks lost about $2 million in a series of fraudulent wire transfers to Hong Kong. Last fall, thieves stole close to $1 million in a single fraudulent wire transfer from the University of Virginia to the Agricultural Bank of China.
It is vital for small business owners to understand the risks they face when banking online, and to get a sense of the sophistication of today’s attackers. Unlike consumers — businesses do not have the same protection against fraud that consumers enjoy. Indeed, most companies that get hit with this type of fraud quickly figure out that their banks are under no legal obligation to reimburse them. Small business owners wondering what they can do to protect themselves should read the tips at this post. One of the surest ways that business owners can avoid becoming the next victim is for the person handling the company’s books to bank online only from a dedicated machine — preferably one that is not Windows-based (since all of the malware used in the attacks to date won’t run on anything but Windows). Using a Mac or a Live CD approach may seem expensive or impractical, but losing hundreds of thousands of dollars because your PC got a virus infection isn’t so great either.




Thanks to krebsonsecurity.com for warning about this significant problem.
Krebs has been a great source that bridges the gap between nerds and “clueless users”.
The Clueless seem to have an unrealistic confidence that their computers are safe. I often wonder why this barrier is so hard to overcome.
Still, I wonder about the recommendation to use Apple or Linux as a safer alternative. Surely the amount of money involved would inspire criminals to attack those systems also.
The use of separate Administrator and User accounts would also provide protection against the vast majority of malware. This protection works on all systems, Windows Apple and Linux.
Separate Administrator and User accounts are not optional. This has been the standard use of computers for decades. It works.
But efforts to convince the Clueless to use separate Administrator and User accounts have also failed to cross the barrier.
I heard that sentiment all the time whenever I write about this topic: “Yeah, you just wait: As soon as more people start using Macs and these other approaches, the bad guys will start targeting those areas, too.”
This is almost certainly true. But until that happens, is it still not good advice? As a friend remarked recently, “It’s kind of like being in an open field and being shot at by snipers, and someone says well it doesn’t make much sense to duck and hide in the tall grass because they’ll just shoot there too.”
Your story made me think of some content on ITL’s site that I read through earlier today [http://theinvisiblethings.blogspot.com/].
I frequently get asked as to what the best practices are for accessing bank or other financial accounts. I’m beginning to think (thx to Joanna’s posts) that the Ubuntu/Linux recommendation isn’t enough, that LiveCD (as you suggest) or a dedicated, 99% of the time airgapped system is the way to go.
Perhaps fair to say that Linux grants you a large degree of immunity from automated attacks, but not necessarily the (albeit less probable) “manual” attacker.
It is good advice, to a point. While most of us do acknowledge the point that those systems aren’t attacked, it matters to the people to whom we are making the recommendation. It’ll take them a while to get up and running and feel comfortable with their new system. Nor will they take kindly to the “Well, it was bound to happen” excuse if/when they are attacked on the new platform.
The recommendation to move is railed against because is is an extension of security by obscurity. With the rise of the mobile platform, it does seem like that Windows will be displaced as the dominant OS in the near future. Even though it still controls the PC market.
Yeah, well. It’s a little like having to listen to all these harpies saying that you have to have the most and the latest softwares, keeping them all updated to the nines (and boy howdy how you have to keep all of them updated, right now, TODAY) to be safe. When really, you just have to know what your doing on your old softwares, and pay attention to what the bad guys might be doing. So who is really doing more work? Me, who just keeps doing what I’ve always done, or you, who keep jumping on the monkey to be sure you’re always up to date, right this very minute?
So which is more trouble? Monitoring all your software to make sure that it’s all “safe” and guaranteed to keep you from harm? (Nevermind that there’s always the zero-day that can hit you, and the software companies that can’t protect you from it.) Or just keep on doing what you’ve always done, and look out for the zero-days as best you can.
My money’s on knowing what you have, paying attention to what the bad guys can do, taking precautions against the worst that can happen, and living life to its fullest. Sure, maybe that won’t work for the clueless, but then does anything ever really work for them? Poor babies, they just have to accept whatever falls in their laps. Poor babies.
Well, it’s working for me, so far.
If you want to get a clue about how many people there are on the internet like me, you should read all 12 pages of comments to Arstechnia’s recent article: “Facebook shoots first, ignores questions later”
http://arstechnica.com/business/news/2011/04/facebook-shoots-first-ignores-questions-later-account-lock-out-attack-works.ars?comments=1&start=440
Honestly. In the old Wild West, they at least had the decency to ask questions – after they shot you. Are we really so much better and advanced in civility than they were? I don’t think so.
It’s a New World Order baby. Better get used to it.
I especially liked the Ars editor who posted the YouTube video in the comments about the honey badger – it just doesn’t give a shit – it’s hungry, so it eats – whatever it wants to.
Oh, ok. For those of you who still think this isn’t a dog-eat-dog world, her point was that she would stay on top of Facebook to rectify this injustice no matter what it takes, and in fact Arstechnia’s Facebook page has been restored – no explanation, no apology for the takedown, but if you ignore all that, things are sort of back to what they should be. Or are they?
Another diverse solution might be to get they new PC monitors with small built-in computers. This way you can browse the Internet on a dedicated device with less risk. I have not tried it but I see it as a very interesting solution since two ordinary PC’s for every employee is not feasible. Not only can you separate dangerous activities you could run these monitors on a separate Internet connection. Limiting your work PC connection. Even if the first generation of these devices don’t meet the requirement I think we should support this kind of development.
I think we’ve reached that point w/ OS X …
Of note, admin v. user separation probably doesn’t protect against most trojans.
The computer manufacterers are no help for the Cluelless. I recently unboxed and set up a mnew computer for a neighbor of litttle technical knowlledge. I walked her through every step of the manufacterer’s setup procedure, which created one user account, in her name, with administrative privileges. I renamed that account and created a limited user account in her name an
Oops. Maybe I’m too old to do thiks sort of thing.
The computer manufacterers are no help for the Cluelless. I recently unboxed and set up a mnew computer for a neighbor of litttle technical knowlledge. I walked her through every step of the manufacterer’s setup procedure, which created one user account, in her name, with administrative privileges. I renamed that account and created a limited user account in her name and passworded both accounts, and spent a lot of time explaing why this was a good idea, even demonstrating how a program ccould not be loaded from the limitede account. She wanted to do spreadsheets so I loaded OpoenOffice Calc (it wanted to load Java but why would you need Jave for a spreadsheet?).
My question why can’t the manufacturers take a little responsibility and tweak their setup procedeures to make their product a little more secure? What would it cost them?
Did you post anything regarding the Playstation network hack?
Yep, the post directly before this one on the blog, put up last night:
http://krebsonsecurity.com/2011/04/millions-of-passwords-credit-card-numbers-at-risk-in-breach-of-sony-playstation-network/
Apparently you’re more interested in asking than actually looking to see if he did. 😉
I’m a little disappointed in the FBI’s report, which indicates the investigators don’t know much about China or the Chinese language. To quote the report: “The official name of the companies also include the words “economic and trade,” “trade,” and “LTD.””
“LTD.” or “Ltd.” is short for “Limited.” The official English translation of most Chinese companies’ names ends with “Co., Ltd.” It’s just as common as “Co.” or “Inc.” in the US. The “Economic and Trade” or “Trade” seems more specific and relevant since these Chinese companies are presumably dealing with Russians, so their companies would need to be engaged in cross-border transactions that would cover for the transfers of stolen money.
Likewise, the Agricultural Bank of China, Industrial and Commercial Bank of China, and Bank of China are among the top 5 banks in China, so saying that most of the transactions went through them is no more noteworthy than saying most of the transactions went through Bank of America, Wachovia and Citibank.
What would be most interesting to see is whether the transactions tended to go to specific branches of those banks, because it might lead to the corrupt bank employees who are almost certainly a part of the criminals’ network. Chinese banks are extremely nitpicky and bureaucratic, especially about international transactions, so these transfers would not proceed unless they were very well disguised or going through corrupt bankers.
We took your advice and bought netbooks with Linux. The banks or ADP were not available on anything except Windows. We rolled back to Windows but the netbooks can only reach the bank and ADP sites and it is on a separate network segment. Our primary network segment can not reach the banking or ADP websites.
That’s odd–I would think that transactions between yourself and the bank would be via a secure web transaction; wouldn’t matter which OS, just as long as you had a browser open. As for ADP running on Unix/Linux, did ADP state that they may move that way in the future? Interestingly, ADP has job openings for Linux engineers.
I recently worked for a small business that used ADP and its payroll system was IE-only, as I recall.
William – Thanks! That cleared things up a bit. In this day and age, I’m surprised people are still using setups and modules that are one-browser-specific only.
“In this day and age, I’m surprised people are still using setups and modules that are one-browser-specific only.”
You should check out the companies handling your medical data — it’s mostly IE only, none of it IE9 (some require IE6), and if anything doesn’t work, they instruct their users to set security at the lowest level for all websites, not just “trusted zone.”
Adobe just came out with their sandboxing defense and is not fixing other vulnerabilities because that’s supposed to be sufficient, but one online electronic medical records company I deal with instructed all their clients to deactivate that security since their system wouldn’t work with it.
It might be tolerable if their clients never went on the internet for anything else or had dedicated machines that did nothing else, but the EMR firm didn’t even suggest that such a step might be wise.
I’ve worked for BANKS that still use IE4…
@gilbert wham;
Somehow – that doesn’t surprise me in the least! 🙂
Setting up a 2nd PC for your CFO to use for banking seems like an easy thing to me considering the risks.
I’m not certain if we’ve taken enough steps to protect our business accounts by
a) running Linux in a VM just used for banking
b) using Chromium as the browser
c) fully encrypting the VM container (doesn’t really help when the VM is running)
That VM is not used for any general purpose uses, just online banking through a web interface. The hostOS isn’t used for general purpose use at all either.
I’m certain there is more we could be doing, but this seems like the best trade-off between function and hassle.
Dedicating a PC for logging into online banking works unless you use a third-party software for payroll or accounting software with which you need to somehow connect to your online banking (i.e. uploading NACHA files for ACH transactions such as payroll).
You can load your file to media and put it on the computer, but then you may compromise the computer if the media is compromised. For this reason, a LiveCD is the best solution, and it’s even better if it’s on a dedicated PC, as well.
With that setup, you could boot from the LiveCD ont he dedicated PC, log into online banking, then load the media and upload the file. The order is important. If you load the media prior to logging in, you risk exposing the OS to malware prior to the login.
At any rate, LiveCD’s and dedicated PCs still fail to appeal to the small business owner for two reasons. The first is convenience. It’s just not convenient to use either one. And in the case of the dedicated PC, it’s not cheap enough for a small business owner to seriously consider it unless they truly understand that they are at risk.
From my experience, most small business owners do not fully appreciate the risks they take with online banking. If they did, they would be willing to invest the few hundred dollars and some time in finding a real solution.
However, I can tell you that none of this will fix the crux of the problem, which is the back-office side of transaction processing. Banks will need to step up their game to help bolster the security of their customers or risk losing a lot of money. Risk analyitics at the transaction level for ACH and wire processing will become commonplace in the next few years, and any bank not safeguarding their customers’ accounts in this way will lose a lot of customers as small business owners learn more about the threats they are facing.
Vendors such as Threatmetrix and Centrix are coming out with products which actually analyze ACH batches at the transaction level using historical data and several metrics. This type of software will become more important than software which validates the user at login or at the time of transaction.
Validate the transaction, not the person.
“Dedicating a PC for logging into online banking works unless you use a third-party software for payroll or accounting software with which you need to somehow connect to your online banking (i.e. uploading NACHA files for ACH transactions such as payroll).”
Sharing and legacy are always the biggest problems. The best strategy would be for banks to offer an API that doesn’t require a web browser, allowing the use of secure thin clients, diverse hardware/software and applications of low complexity. Assuming this won’t happen, I see two approaches that apply in different situations: files needing to be shared; specific applications on insecure browsers being required by banks.
For the first scenario, a dedicated PC can be used. The software should perform input validation on the file to be shared, with some sanity checks and maybe a virus scan. The rest could be done in a minimalist way that increases robustness.
The second scenario sucks. Virtualization, hardening, HIPS and a bunch of other approaches come to mind. I would probably put the software in a virtual machine on a dedicated, Linux PC. The Linux PC would have its firewall configured to only let the VM talk to the bank’s web site. The VMM could be used to restrict the software in such a way to contain common forms of attack or infection. The Windows system would be appropriately hardened and use a HISP like DefenseWall or AppGuard. It would be updated right after installation and snapshotted. The system would regularly be restored from clean snapshots just in case. This is a start.
I still stand by my claim that the best approach to this ACH problem requires better controls on the bank’s end and a simpler interface that allows for secure client software to be built. If they just did the latter, I could give them a nearly unhackable, affordable ACH appliance in under a year, certifiable to DO-178B or Common Criteria EAL5+ (Medium to High Assurance).
The bank I work for is currently looking to have far greater control over ACH transactions by analyzing all features of every transaction priot to them going out of the door. If a customer changes routing numbers or account numbers on a payroll file, for instance, the software would flag this and let us know so we can review it or, if necessary, contact the owner by phone to make sure it is legitimate.
Currently, we have a review system in process which utilizes ACH calendars and limits, but does not dig into the details of every transaction in every batch. We are looking at some sofware solutions which do this very well. That’s what I mean by validating the transaction rather than the user.
You can do everything in the world to remotely verify that the person logged in is who they say they are, but it can all be worked around by a skilled thief. To really be sure the money going out the door is what it should be, you have to look at the transactions. since it is too labor intensive to do this individually, we plan to utilize software which uses historical data and behavioral patterns combined with ACH calendars, limits, and rules we set up to find anomalies which may indicate fraud. We believe this is where the industry will be headed, and we want to be ahead of the curve on this.
We are also utilizing more advanced risk analysis on our new customers who plan to use ACH to mitigate our risk. While it won’t do much to protect existing customers from hackers, it is just as important to choose your customers carefully as it is to protect your existing customers from risk. Ultimately for us, it’s about the bank’s bottom line. Fewer compromises means less risk for us, as well.
Yar,
Is your bank more friendly/reasonable to the small businesses that may have problems vs what I have read is standard practice from Brian and others who report the problems?
It seems smaller businesses really have little protection vs what a lot of consumers have.
I can’t comment on specifics, but I will say that depending on the source of the fraud and what types of practices the customer was using, they may still end up holding the ball of wax, but we also have been known to split losses or even cover them in some instances, as well.
It boils down to the fact that there is no black and white for responsibility on this any more. A customer who is victimized is responsible for “reasonable” security on their accounts, but what does that mean? Does that mean they use only the security absolutely required by the bank, or that they utilize more extensive security measures to protect themselves?
In my opinion, any business who is careless when using their Online Banking should be held liable, but any bank who doesn’t take each case on individually and constantly reviewing their security policies is asking for a lawsuit and a lot of lost customers. The best thing a bank can do is educate their customers and supply them with the tools they need to protect themselves.
Beyond that, banks should constantly be looking for ways to protect their customers. Whatever happened to the phrase “As safe as if it were in the bank?” As a bank, IT IS YOUR JOB TO PROTECT YOUR CUSTOMER. Unfortunately, you sometimes can’t protect the customer who doesn’t protect himself.
…
Why Heilongjiang province? They might be very near the Russian border, but there’s almost nothing at all on the Russian side and a very big river in between. It would require some effort to travel from western Russia to this part of China.
Perhaps Wikipedia gives a clue – http://en.wikipedia.org/wiki/Borders_of_Russia#Border_with_China :
“The relaxation of border controls has resulted in a noticeable smuggling problem that is worth around three million dollars each year.[2] Traditional health products such as ginseng, Siberian tiger, sea cucumber, and reindeer antlers are smuggled along with weaponry and drugs. Illegal fishing is also common.”
Hey Brian
What might the reason be for the authorities encapsulating one year’s transgressions at the end of that year instead of a more steady flow of info during the year
Are they frightened of something?
Surely it is better to know as it goes and not well after the event
The Chinese govt are having problems collecting taxes. What chance of stopping this sort of fraud
“In my opinion, any future defense secretary who advises the president to again send a big American land army into Asia or into the Middle East or Africa should ‘have his head examined,’ as General MacArthur so delicately put it,”
Thus spoke Defense Secretary Robert Gates recently.
My corollary to Gates’ rule is that anybody who does _anything_ which either can or does involve the movement of money from one place to another, and who does it online, and who does it with a Windoze box should have his head examined.
Me personally? I don’t even trust Linux. It’s still too new, and hasn’t been fully shaken out yet. Anything I do online that involves money I do from a FreeBSD box using Firefox. FreeBSD, OpenBSD, and other such like are derived from _real_ UNIX… you know… the stuff that’s been around, been open source, and that has been getting debugged since the 1970’s.
So anyway, question for Brian: What happened to the other $9 million?
I am always curious about how crooks accomplish the magic trick of making money magically disappear entirely from the banking system so that it becomes untraceable. So, um, $20 mil goes from small USA companies to intermediary banks in NYC and thence is transferred to certain very specific banks in China. All of this is recorded meticulously of course. We live in an age of computers after all. Then later, $11 mil is recovered. Has the other $9 mil REALLY become untraceable? Or are the Chinese banks that received the money just flipping the bird at the FBI and the US banks when they try to get that other $9 mil back?
I really would like to know. I mean seriously, sometimes I wonder just what kinds of idiots we here in this country are. We let the Chinese into the WTO, why, exactly? So they could play criminal games like this, rip us off, and then when we ask for the money back they just shrug and say “Sorry Charlie!”
Ron money is removed from the system in a number of ways, it could be removed by cash though 9million is alot to move via cash (even in 500 euro notes the money launderers not of choice). You can fit 30,000 euros in a cigarette packets so 9million euros could be fit into 300 cigarette packets.
though getting hold of that many 500 euro notes would be pritty tough in remote china.
the other alternative could be to transfer it via an exchanger to liberty reserve or web money and then cash it out anonymously via a goldnow.st card or a similar anon atm card. (though 9mill would still take alot of time).
youve got to realise that alot of that 9million will be waste for paying off mules to paying off mule suppliers to mules who rip you off to exchange fees to paying people off.
once the money isnt hot anymore (though bear in mind that having 9million and no explination why is still hot) the money can be sieved into legit businesses. (ask any small business nicely and for the right cut they will put your cash through there system and write you an invoice, well most will).
you have to realise that although laws are in place the majority of people will overlook them if the reward is good enough 🙂
cool, you know
RSS isn’t working – just posting to follow the discussion.
RSS works for me (two different subscriptions, one for articles and one for comments to a particular article), but subscribing only gives me the past 10 comments preceding the time I subscribe.
The link for the feed page for the comments for this article is http://krebsonsecurity.com/2011/04/fbi-20m-in-fraudulent-wire-transfers-to-china/feed/ (same as the URL for the comments except replace “/#comments” with “/feed/”), then click the button to subscribe.
What RSS reader are you using?
Maybe I’m stupid?! Your link worked, why didn’t Brians link page?
I’m not using anything particular, because I’m completely ignorant about RSS! Point me to an RSS for dummies book! HA!
Thanks a bunch AlphaCentauri!
“Your link worked, why didn’t Brians link page?”
The RSS icon at the top of this page takes you to a feedburner.com page. Then you ignore all the stuff about news readers and just click on the little icon for “View Feed XML.” It took me a while to figure that out.
Seamonkey still puts the RSS icon in the browser address window to the right of the URL, but it only goes to the feedburner.com page, not directly to the subscription page. Once you subscribe, it automatically opens a mail window and downloads the last ten entries. Firefox now puts the link in the bookmarks menu instead, as if there wasn’t enough stuff in my bookmarks menu already. 🙁
Thanks AlphaC!!! The ignorant have been enlightened!!! That worked for me!
I really appreciate your trouble here, and the slings and arrows you suffer here at Krebs on Security!
I used to be able to hit the feed icon in the URL window before FireFox 4; maybe my RSS broke in the transition. I was using some ticker feed, that still works in the footer. But no deal on the rest of it.
“Using a Mac or a Live CD approach may seem expensive or impractical” – really expensive and impractical… Just use Linux
Yeah, the price of CDs is getting exorbitant! 😉 HA!
At the local golf club where I am treasurer (Sydney, Australia)
it only cost $A1000 for my techie to provide a dedicated box with a Linux stick embedded for banking only
No problems for staff and directorss and entirely safe
BTW, mule offer emails have been arriving down here over the past 6 months
The $1000 is cheap insurance
big kev anychance of posting up a mule email be curious as to what tatics they are using these days
Just going to bed right now
Try tomorrow
From: Brad McEvoy [mailto:brad@bradmcevoy.com]
Sent: Monday, January 24, 2011 7:19 AM
To: Kevin McEvoy
Subject: Fwd: Current Open Position _ id / 9N0P0U6…
Hi Dad,
Here’s another spam email trying to get money mules. Says to me our crooked friends are still in business!
Cheers,
Brad
——– Original Message ——–
Subject:
Current Open Position _ id / 9N0P0U6…
Date:
Sun, 23 Jan 2011 12:12:12 -0800 (PST)
From:
Xander Montgomery
Reply-To:
landolineenov@gmail.com
To:
tol_fuin@yahoo.com
Base pay: $ 3,000/month + bonus
Hi.
We would like to introduce to you the enterprise called «DCM Trade».
Our establishment reasonably holds leading positions in consulting services field for everybody. You can get consulting services regarding any enterprise’s activity. We provide all elemental guidance and present data related market condition.
After difficult assay of the bearings in economy we came to conclusion to expand our firm staff. Our firm’s large staff includes people of manifold ages, nations and lifestyles, which can be a guarantee to a versatile approach towards any kind of misleading. Our establishment is ready to provide you the client service manager workplace. Responsibilities and data related base pay and bonuses system of this vacancy are specified below.
customer service manager is responsible for obtaining and forwarding of financial funds. You will be receiving payments from our customers located in your country. Right after you receive the funds you will have to forward them to our head office with the help of any method that seems to be more advantageous for you. Paying taxes for these transactions is not your, but ours job. We will handle all the expenses.
You will have a decent wage working at this place, many kinds of benefits, depending on the size of transactions.
However we have a few obligations for the person applying for this job. First obligation is to be mature and steady. Second you should have positive communication skills. Regular access to the internet is also mandatory. You will receive all instructions and also you will have to work in an «online office».
Please feel free to contact us via email.
Had a minute
Here is one sent to my IT son in New Zealand
I would love to reply to most of these post but for reasons I cannot . But on one post I have just read I fully agree that banks should offer more security to there clients . But I will say this to the end the end user is totally responsible for there O.S. and how they secure it not the bank .
Banks should be protected on 100 %. The management of banks should be responsible for all.
The main point of the artcle is client security, or the lack thereof.
In this client-server relationship, the banks are the servers. The banks have little choice other than to comply with client instructions. Unfortunately, infected clients look just like healthy clients to the servers.
In these comments, there has been no discussion of securing the Automated Clearing House (ACH) system, also known as electronic transfers. As a business, I do not want to send money to unapproved destinations. From the banks point of view, they are obligated to send money anywhere the client directs.
How do I, as a client, instruct the bank to restrict ACH? If I have a list of known transfer destinations, then I do not want the bank to transfer money to the unknown. Ever. The banks do not provide a method of restricting ACH. This is bizarre.
Since I have a list of folks that I need to pay money to, then surely I do not want money sent to anyone else. If a new transfer destination needs to be approved, then the approval should be checked and double checked.
If ACH was restricted, then all of these scams would fail.
It seems to me that suppliers of security software to small to medium sized enterprises are somewhat to blame by not better advising their customers of the limitations of their security products and particularly in relation to potential internet banking fraud exposure and more importantly how to gaurd against that exposure
——– Original Message ——– Subject: Job opening ; (ID : 1297363450)…
Date: Thu, 10 Feb 2011 10:45:44 -0800 (PST)
From: Shaeleigh Gomez
To: brad@bradmcevoy.com
Greetings! At this time we have open position to offer.
If you’re seeking for a part-time or full-time highly paying position, please go on further and receive full package on how to apply and get involved.
Currently we offer great opportunity that will save you time and will provide you with solid income.
Position is called “Fund Courier”. Your duty is to receive and forward funds.
This is one of the most convenient opportunities you’ll find these days.
What could be better to work right from the comfort of your house.
You have to meet requirements before you can start:
– Have a stable Internet connection
– This vacancy is currently for Australia only
– Must have a cellphone number to reach you at
– Must have 2-3 hours a day Monday-Friday
– Must be 18+ years old
We will be more than happy to provide you with description and explanation of your position and how it works. For full info – please submit your request to: techteam.desk@gmail.com with subject “Vacancy info”, and one of our staff will respond back as soon as possible.
Hope to hear from you soon, have a great evening!
Sincerely,
Tech Finance Team LLC.
Another one received downunder