A picture may be worth a thousand words, but a single tainted digital image may be worth thousands of dollars for computer crooks who are using weaknesses in Google’s Image Search to foist malicious software on unsuspecting surfers.
For several weeks, some readers have complained that clicking on Google Images search results directed them to Web pages that pushed rogue anti-virus scareware via misleading security alerts and warnings. On Wednesday, the SANS Internet Storm Center posted a blog entry saying they, too, were receiving reports of Google Image searches leading to fake anti-virus sites. According to SANS, the attackers have compromised an unknown number of sites with malicious scripts that create Web pages filled with the top search terms from Google Trends. The malicious scripts also fetch images from third-party sites and include them in the junk pages alongside the relevant search terms, so that the automatically generated Web page contains legitimate-looking content.
Google’s Image Search bots eventually will index this bogus content. If users are searching for words or phrases that rank high in the current top search terms, it is likely that thumbnails from these malicious pages will be displayed beside other legitimate results.
As SANS handler Bojan Zdrnja explains, the exploit happens when a user clicks on one of these tainted thumbnails. “This is where the ‘vulnerability’ is,” Zdrnja wrote. “The user’s browser will automatically send a request to the bad page which runs the attacker’s script. This script checks the request’s referrer field and if it contains Google (meaning this was a click on the results page in Google), the script displays a small JavaScript script…[that] causes the browser to be redirected to another site that is serving FakeAV. Google is doing a relatively good job removing (or at least marking) links leading to malware in normal searches, however, Google’s image search seem to be plagued with malicious links.”
Denis Sinegubko, a Russian malware researcher who has been studying the fake anti-virus campaigns, called this tactic “the most efficient black hat trick ever,” and said it is exceedingly easy to set up. He said he’s received access logs from the owners of several hacked sites, and has used the data to estimate the traffic Google sends to these bogus image search pages. Sinegubko reckons that there are more than 5,000 hacked sites, and that the average site has been injected with about 1,000 of these bogus pages. The average page receives a visitor from Google approximately every 10 days, he said, which means Google is referring about a half million visits to fake anti-virus sites every day, or about 15 million visits each month.
For example, one of the hacked sites Sinegubko said he saw access logs for was in Croatia; It had a Google page rank of zero prior to being compromised with the phony image search scripts. The logs showed that the site had been hacked on Mar. 18, 2011, and that Google began indexing the tainted image pages the next day. “During the next 5 weeks it has indexed 27,200+ doorway pages on this site,” he wrote in a blog post on his findings. “During the same 5 weeks Google Image search has sent 140,000+ visitors to this small site.”
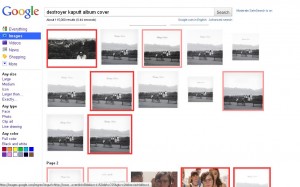
Sinegubko is developing an add-on for Firefox that can flag malicious Google Image search results by placing a red box around images that appear to link to hostile sites; Images with a pale pink box around them are hot-linked and may also be malicious, Sinegubko said. I tested the add-on (which is not ready for public release) searching for the cover art for the album “Kaputt” by the Canadian band Destroyer. As you can see from the image above, most of the images returned link to sites pushing fake anti-virus.
Sinegubko said his analysis of the malicious scripts that do all of the work indicates that the spammy pages are built when Google’s bots try to index them. Each bogus page targets specific keywords, in this case, the word “destroyer.” The script then requests Google’s autocomplete results for the word “destroyer,” and it is given 10 suggested keywords. The script then includes those new keywords in the spammy pages as links to “related searches” (for example, links to “23.php?q=destroyer-droid-start-wars”, and the results in the image above, “23.php?q=destroyer-kaputt-album-cover”. “When Googlebot follows those links, the script generates spammy pages for them, at the same time it inserts links to new suggested searches,” the researcher said in an instant message chat with KrebsOnSecurity. “This way Google suggests new keywords for spammy pages and automatically builds spam and indexes it.”
Several security experts have suggested specific steps that Google could take to cut down on scammers using Google Images, such as bumping sites that hot-link images to a much lower ranking in the search results for a given term.
Google spokesman Jay Nancarrow said the company was aware of the attacks and that it is making “active efforts to improve both the quality of the results and malware detection,” but declined to be more specific. “We’re improving, as are the people trying to put users at risk, and in the interests of those users it’s best if we don’t reveal everything that we’re doing about this.”
Rogue anti-virus scams almost invariably rely on malicious scripts that can be blocked by the excellent Noscript add-on for Firefox, which lets you decide which sites should be allowed to run scripts. If you happen to stumble upon one of these fake anti-virus security alerts, stay calm and avoid the urge to click your way out of it. Instead, simply hit Ctrl-Alt-Delete, select the browser process you are using (firefox.exe, iexplore.exe, etc.) and shut it down.




I’m still recommending people who don’t use noscript to stay away from google images. It’s been a week and I was hoping google may have started to get this under control. Has anyone heard anything?
As a collector of various images I use google alot to gather pics. After having some malware issues I started using Ablock Plus, Noscript with my browser and SpyBot SnD. Also I now use http://www.googleimageripper.com/ and haven’t noticed any problems since.
MBAM helps with any malicious IPs; if they are in fact known. It will block any downloads automatically if you have the real time protection.
SpywareBlaster has a pretty good host file and active X blocker, but this may not apply to this situation.
I searched “microRNA biogenesis pathway” to get an image for a term paper for a biology class and was way surprised that the very first image linked me to some scam site. Didn’t realize this was a new thing. I’ll use bing from now on
I’m now having malware issues and I think google images is the culprit. Im’ having to read this site now through a proxy because it is being blocked somehow. I’ve ran virus scanners and it’s not picked up anything as of yet. Know of a way I can get this crap off my machine? Thanks.
Reading the user reviews at CNET will get you the best malware solutions. In my experience, the free ones are actually the best. I can’t tell you how much money I’ve wasted testing supposedly reputable purchased software.
Even Web Of Trust(WOT) can help on some of these image problems. If they are red or gray, I just don’t click on them. It wouldn’t be as good as the solution Brian is testing of course.
One of the biggest problems with any solution right now is the varied landscape with the new HTML5 browsers. You are lucky if your favorite add-on works at all.
concerned,
I’m surprised malware would be blocking google. Usually malware doesn’t want you to know it’s there. If this is not some configuration error, this malware sounds particularly aggressive and confident that you cannot bypass it.
There’s a line with all malware where you have to decide whether you are better off trying to clean it live or whether you just have to wipe the drive and start from scratch.
I think wiping the drive is often overreacting, considering how much of a hassle it is to rebuild a system from scratch. However, without someone there to help you run the diagnostics and remedial steps, and given the sophisticated sounding nature of your problem, I’d strongly recommend you wipe your system and rebuild it from scratch.
On the other hand, I’ve only heard one symptom, which may not even be a primary effect of any malware. And you set up a proxy, so maybe you have the expertise to take this one on by the horns. Maybe start by checking for configuration errors. Have there been any changes to your software or drivers recently that might have caused internet problems?
If you run online with restricted rights, most of these things will disappear with one CCleaner scan(if you set it up right).
On Vista/Win7 they are called standard accounts.
Well I’m browsing krebsonsecurity.com by proxy and that’s the only way it will load. I’m sorry if I confused you. This is a fresh install and has decent malware protection enabled. The only recent changes that I have made is updating to IE9, installing malwarebytes, norton360, and spybot. Like I said this was a fresh install and I was reading while everything else was installing. I’m not sure really what is going on at all. I’ve went into safemode and scanned too, but found nothing at all. I’m confused. It is only happening with krebsonsecurity and it might have happened after looking at an external link on this site and not google images. I was reading a few articles on here that interested me and boom, it started blocking the site.
I’ve had many clients experience malware like activity, when the only problem was the Microsoft updates not installing correctly. You might check you update history and see if all were successful.
One of my clients had to use the Microsoft Baseline Security Analyzer to find the mistakes in her updates. Then it is simply a matter of reinstalling the update or restoring to a time before it was installed.
For .NET updates I have been having better success doing a clean boot and installing them separately.
You may have to reinstall some drivers and AV/AM solutions afterward also.
Hmm,
I’m willing to bet you didn’t run anything you didn’t know what it did, and it seems unlikely to me that you hit a drive by download if you fully patched the system right as you built it.
It’s possible, if your scans are coming up clean and you are just having some browsing trouble, that one of your security measures is over-aggressively blocking something.
That’s what I meant by configuration errors, this sounds like it might not be a malware thing. I mean, we’re on a security site, so everything’s going to look a bit like a trojan, but maybe this is one of your programs overaggressively protecting you.
That is what I honestly thought this was, a silent drive-by but I don’t notice anything at all that I can see abnormal besides the blocking issue. The only problem I have is why then am I able to view the site via HTTP proxy and not directly?
I’m guessing you hit a blocklist. You need to figure out what’s blocking the site, the application, your security software, your firewall, or some sort of corporate firewall.
I’d try to view the site from Chrome or Firefox, or ping it. I’m not familiar with those security programs enough to know what sort of live website blocking they use. You can pull up Windows Firewall and see what rules it created fairly easily. (On Win7, winkey,’firew’ gets it to the top of the list for me, then the rules are on the main page that comes up). Only you will know what sort of corporate or country blocking you might be facing, though I’m not sure why they would ‘only’ block krebs.
Maybe one of those security programs saw a discussion on here about a trojan, and thought the site was hosting malware.
MBAM uses IP blocking, but you will see it pop-up with the address being blocked. However, this is sometimes attributable to malware on-board causing MBAM to prevent such “re-directs”, for lack of a better term; sometimes just running CCleaner will clean up the connection and you can reach the page requested just fine.
Spybot S&D uses “immunization” which is a BHO that blocks bad scripts I believe, but some sites react by not displaying at all. Sometimes disabling all the immunizing and re-enabling it will clear the log jam. I haven’t used the newest version yet, but clients report to me that it is still functioning the same way it used to.
I had many pages that just wouldn’t load until I put AdAware with AdWatch enabled back on my PC. Apparently AdAware clips unwarranted communications between servers, ad servers, and any temp files or cookies that control them. My browsing performance was greatly enhanced. Right now I’m getting the best performance I’ve even had. This is on Vista x64, with the 32bit browsers: FF/IE9/Chrome
I’m sorry Brian if I cluttered your blog but it seems something is indeed blocking it because firefox w/ noscript and wot loads your site just find. Thanks Thomas and I’ll have to spend sometime looking into what is blocking it in IE9. 🙂
I was lkoinog everywhere and this popped up like nothing!
I do however know malwarebytes often blocks domains on certain subnet ranges. I’m not so sure if Krebsonsecurity falls into that category. Maybe some external source is, I dunno but thank you for your time.
As previously related – it (MBAM)will block the malware, which in turn blocks the site you want. Cleanup the malware and it will be fine.
My computer got infected when I searched for images for “centrum semiovale” (a brain region). Suddently my computer was showing me convincing Microsoft trademark logos showing the number of files on my hard drive that were infected and what I should do about it. I kept trying to run through the steps but nothing happened. At some point a message said words to the effect, “You’re boss will not like it if you do nothing,” and then I realized this was a scam to get me to buy worthless software. Nothing is safe! It took my IT person much of the afternoon to reverse the damage. Restoring a set point was not good enough.
@VM;
All that should have been requied was to end the task in the task manager and clean up your temporary files and cookies. CCleaner does this fine for me, but your IT guy should know better.
Restore does not get rid of malware, it only reverses update progression, and driver installations, if one is lucky.
I think bing should remove all google image related searches
I would like to mention a problem I am having with Google image search.
It seems that some spammers are using Blogger or Blog*Spot pages to redirect people from looking at my photos, which show up on Google image search, to their spam websites.
On Google search my vintage car photos will appear with the number two in the top left hand corner. Click on my photo and you are redirected
to another site, then another, and another. Some of these sites are pornographic.
Do you have any suggestions on how to deal with this?
Any help would be appreciated.