T-Mobile disclosed last week that some 15 million customers had their Social Security numbers and other personal data stolen thanks to a breach at Experian, the largest of the big American consumer credit bureaus. But this actually wasn’t the first time that a hacking incident at Experian exposed sensitive T-Mobile customer data, and that previous breach may hold important clues about what went wrong more recently.

Experian’s offices in Nottingham, UK. Source: Wikipedia.
On Dec. 30, 2013, T-Mobile said it notified a “relatively small” number of customers that unauthorized access to a file stored on servers owned by Experian had exposed Social Security numbers and driver’s license numbers. The mobile provider identified the breached vendor as Decisioning Solutions, an identity-proofing and authentication company that was acquired by Experian in April 2013. We’ll revisit this acquisition in a few moments.
Over the past week, KrebsOnSecurity has interviewed a half-dozen security experts who said they recently left Experian to find more rewarding and less frustrating work at other corporations. Nearly all described Experian as a company fixated on acquiring companies in the data broker and analytics technology space, even as it has stymied efforts to improve security and accountability at the Costa Mesa, Calif. based firm.
Jasun Tate worked for a year until April 2014 as a chief information security officer delegate and risk consultant at Experian’s government services and e-marketing business units. Tate said he and several of his colleagues left last year after repeatedly running into problems getting buy-in or follow-up support for major projects to beef up security around Experian’s growing stable of companies handling sensitive consumer and government data.
“What the board of directors at Experian wanted security-wise and the security capabilities on the ground were two completely different things,” Tate said. “Senior leadership there said they were pursuing a very aggressive growth-by-acquisition campaign. The acquisition team would have a very strict protocol on how they assess whether a business may be viable to buy, but the subsequent integration of the business into our core security architecture was just a black box of magic in terms of how it was to be implemented. And I’m not saying successful magic at all.”
Another recent former security employee at Experian who agreed to talk on condition of anonymity said it was clear that the company’s board was not well-informed about the true state of security within the company’s various business units.
“When I was there, the board was very big on security and wanting to invest in it and make sure we were doing what we needed to do in order to avoid situations just like this,” the source said. “In my opinion, there’s no way the board was told the whole story, because if they had been then things wouldn’t be where they are are now. We wouldn’t be talking about this. Some things had to have been hidden or spun in a way to look positive somehow.”
BLACK BOX MAGIC
Not long after it acquired the above-mentioned Decisioning Solutions in April 2013, Experian folded the company into its Decision Analytics platform — a unit which provides credit and noncredit data, customer analytics and fraud detection to lenders, cable and satellite companies, telecommunications firms, third-party debt collectors, utilities and to state and federal government entities.
Within hours of the latest T-Mobile breach news hitting the wires, KrebsOnSecurity was contacted by an anonymous source who sent this author a Web link that, when clicked, opened up a support ticket within that Decision Analytics platform in the United Kingdom — with absolutely no authentication needed. That support ticket I viewed appears to have been filed by someone in an office cube at Experian’s data center in Costa Rica who was requesting hardware support for a component of the company’s Global Technology Services division.
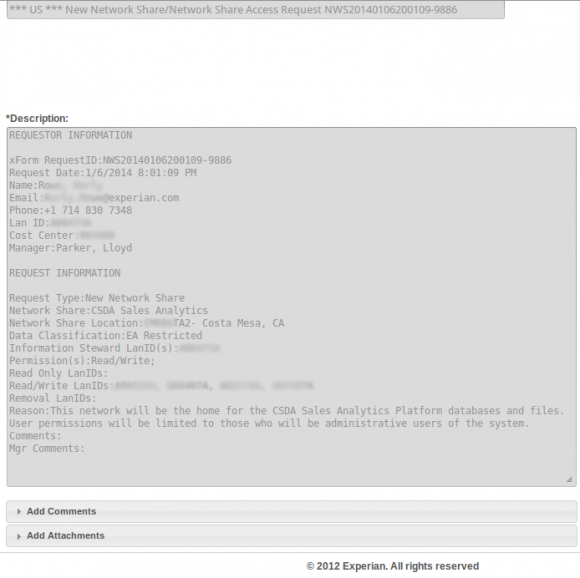
Countless internal support requests for access to Experian’s Decision Analytics credit information platform were exposed to the Internet without authentication until earlier this week.
That particular support ticket was relatively uninteresting, but according to my source anyone could view countless other support tickets filed via the support portal for Experian’s Decision Analytics platform.
The same source demonstrated how modifying just one or two numbers at the tail end of that link revealed requests for access to networked file shares from across a range of Experian’s business units. The requests included specific names of network shares, usernames, userIDs, and LanIDs, as well as email addresses, phone numbers of Experian personnel requesting and approving the changes.
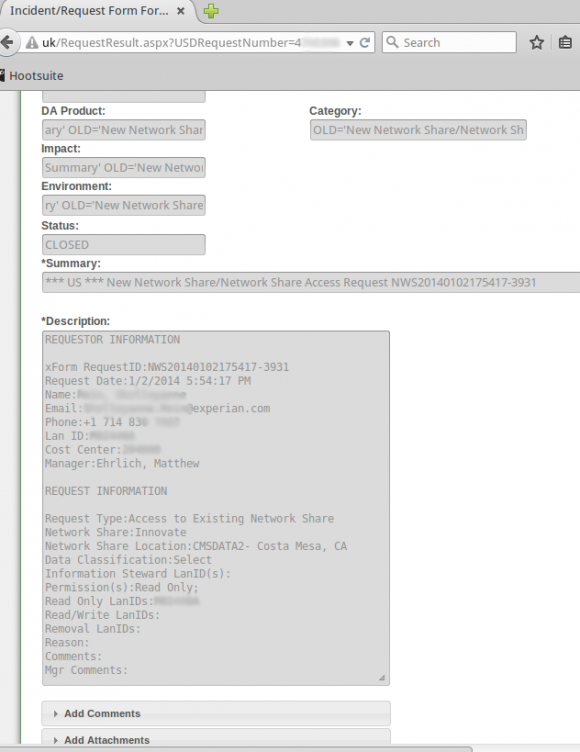
Countless internal support requests for access to Experian’s Decision Analytics credit information platform were exposed to the Internet without authentication until earlier this week.
The support site also apparently allowed anyone to file support tickets, potentially making it easy for clever attackers who’d studied the exposed support tickets to fabricate a request for access to Experian resources or accounts on the system.
In addition, experts I spoke with who examined the portal said the support site allowed anyone to upload arbitrary file attachments of virtually any file type. Those experts said such file upload capabilities are notoriously easy for attackers to use to inject malicious files into databases and other computing environments, and that having such capability out in the open without at least first requiring users to supply valid username and password credentials is asking for trouble.
KrebsOnSecurity sought comment from Experian to find out if it knew that its Decision Analytics support portal allowed anyone to view the tickets within. The company said in a statement that it had disabled the portal in response to what appeared to be unauthorized access to it and had notified law enforcement.
“We take any unauthorized access to our systems very seriously, and when we detected the unauthorized activities, we shut down the website and notified law enforcement,” the company said in a statement. “Our credit database and core infrastructure were not impacted – nor could they be accessed through this website. This site was a legacy version of a service to enable clients and internal users to create and log tickets for issues they may have and we had already deployed its replacement solution.” Continue reading →