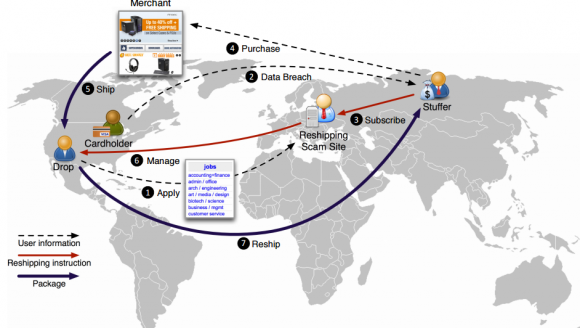
It’s notable whenever cybercime spills over into real-world, physical attacks. This is the story of a Russian security firm whose operations were pelted with Molotov cocktail attacks after exposing an organized crime gang that developed and sold malicious software to steal cash from ATMs.
 The threats began not long after December 18, 2013, when Russian antivirus firm Dr.Web posted a writeup about a new Trojan horse program designed to steal card data from infected ATMs. Dr.Web received an email warning the company to delete all references to the ATM malware from its site.
The threats began not long after December 18, 2013, when Russian antivirus firm Dr.Web posted a writeup about a new Trojan horse program designed to steal card data from infected ATMs. Dr.Web received an email warning the company to delete all references to the ATM malware from its site.
The anonymous party, which self-identified as the “International Carders Syndicate,” said Dr.Web’s ATM Shield product designed to guard cash machines from known malware “threatens activity of Syndicate with multi-million dollar profit.”
The threat continued:
“Hundreds of criminal organizations throughout the world can lose their earnings. You have a WEEK to delete all references about ATM Skimmer from your web resource. Otherwise syndicate will stop cash-out transactions and send criminal for your programmers’ heads. The end of Doctor Web will be tragic.”
In an interview with KrebsOnSecurity, Dr.Web CEO Boris Sharov said the company did not comply with the demands. On March 9, 2014, someone threw a Molotov cocktail at the office of a third-party company that was distributing Dr.Web’s ATM Shield product. Shortly after that, someone attacked the same office again. Each time, the damage was minimal, but it rattled company employees nonetheless.
Less than two weeks later, Dr.Web received a follow-up warning letter:
“Dear Dr.Web, the International carder syndicate has warned you about avoidance of interference (unacceptable interference) in the ATM sphere. Taking into account the fact that you’ve ignored syndicate’s demands, we employed sanctions. To emphasis the syndicate’s purpose your office at Blagodatnaya st. was burnt twice.
If you don’t delete all references about atmskimmer viruses from your products and all products for ATM, the International carder syndicate will destroy Doctor Web’s offices throughout the world, In addition, syndicate will lobby the Prohibition of usage of Russian anti-viruses Law in countries that have representation offices of the syndicate under the pretext of protection against Russian intelligence service.”
After a third attack on the St. Petersburg office, a suspect who was seen running away from the scene of the attack was arrested but later released because no witnesses came forward to confirm he was the one who threw the bomb.
Meanwhile, Sharov said Dr.Web detected two physical intrusions into its Moscow office.
“This is an office where we have much more security than any other, but also many more visitors,” he said. “We had been on high alert after the fire bombings, and we’ve never had intrusions before and never had them after this. But during that period, we had three attempts to enter the perimeter and to do something bad, but I won’t go into details about that.”
Sharov said Dr.Web analysts believe the group that threatened the attacks were not cyber thieves themselves but instead an organized group of programmers that had sold — but not yet delivered — a crimeware product to multiple gangs that specialize in cashing out hacked ATM cards.
“We think this group got very nervous by the fact that we had published exactly what they’d done, and it was very untimely for them, they were really desperate,” Sharov said. “We believe our reports came out just after development of the ATM Trojan had finished but before it was released to customers.” Continue reading