As a greater number of banks in the United States shift to issuing more secure credit and debit cards with embedded chip technology, fraudsters are going to direct more of their attacks against online merchants. No surprise, then, that thieves increasingly are turning to an emerging set of software tools to help them evade fraud detection schemes employed by many e-commerce companies.
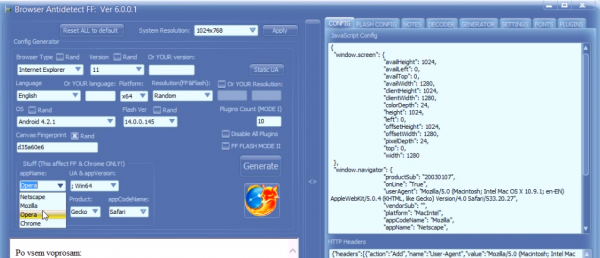
Every browser has a relatively unique “fingerprint” that is shared with Web sites. That signature is derived from dozens of qualities, including the computer’s operating system type, various plugins installed, the browser’s language setting and its time zone. Banks can leverage fingerprinting to flag transactions that occur from a browser the bank has never seen associated with a customer’s account.
Payment service providers and online stores often use browser fingerprinting to block transactions from browsers that have previously been associated with unauthorized sales (or a high volume of sales for the same or similar product in a short period of time).
In January, several media outlets wrote about a crimeware tool called FraudFox, which is marketed as a way to help crooks sidestep browser fingerprinting. However, FraudFox is merely the latest competitor to emerge in a fairly established marketplace of tools aimed at helping thieves cash out stolen cards at online merchants.
Another fraudster-friendly tool that’s been around the underground hacker forums even longer is called Antidetect. Currently in version 6.0.0.1, Antidetect allows users to very quickly and easily change components of the their system to avoid browser fingerprinting, including the browser type (Safari, IE, Chrome, etc.), version, language, user agent, Adobe Flash version, number and type of other plugins, as well as operating system settings such as OS and processor type, time zone and screen resolution.
The seller of this product shared the video below of someone using Antidetect along with a stolen credit card to buy three different downloadable software titles from gaming giant Origin.com. That video has been edited for brevity and to remove sensitive information; my version also includes captions to describe what’s going on throughout the video. Continue reading