My inbox has been flooded of late with pitches for new technologies aimed at making credit cards safer and more secure. Many of these solutions are exceedingly complex and overwrought — if well-intentioned — responses to a problem that we already know how to solve. Here’s a look at a few of the more elaborate approaches.
Some of these ideas may have benefited from additional research into where financial institutions actually experience most of their fraud losses. Hint: Lost-and-stolen fraud is minuscule compared to losses from other types of fraud, such as counterfeit cards and online fraud. Case in point: A new product called Safe Swipe. From their pitch:
“The basic premise of our solution, Safe Swipe…is a technology which ‘marries’ your smart mobile device, phone, tablet and or computer to your credit/debit card(s). We’ve developed a Geo-Locator software program which triangulates your location with the POS device and your mobile phone so that if your phone and credit card are not within a certain predetermined range of one another the purchase would be challenged. In addition, we incorporated an ON/OFF type switch where you can ‘Lock Down’ your credit/debit card from your mobile device making it useless should it ever be stolen.”
The truth is that you can “lock down” your credit card if it’s lost or stolen by calling your credit card company and reporting it as such. Along these lines, I received multiple pitches from the folks who dreamed up a product/service called “Siren Swipe.” Check it out:
“The SIREN SWIPE system immediately notifies local police (via the local 911 center) of a thief’s location (ie merchant address) once heswipes a card that has already been reported stolen,” the folks at this company said in an email pitch to KrebsOnSecurity. “SIREN SWIPE has the potential to drastically impact the credit card fraud landscape because although card credentials being stolen is a forgone conclusion, which cards thieves decide to actually use is not. For a thief browsing a site like Rescator, the knowledge that using certain banks’ cards could result in an immediate police response can make thieves avoid using these banks’ stolen cards over and over again. And in the best case scenario, a carder site admin could just decide not to sell subscribing banks’ cards in the interest of customer service.”
The sad truth is that, for the most part, cops generally have more important things to do than chase around the street urchins who end up using stolen credit and debit cards, and they’re not going to turn on the dome lights and siren over something like this. Also, the signals for fraud are all backwards here: The fraudsters know to use criminal card-checking services before buying and/or using stolen cards, so they don’t generally end up using a pile of cards that have already been cancelled.
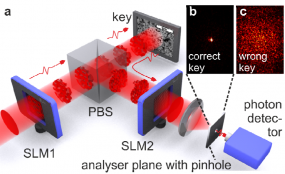
My favorite overwrought solution to making credit cards more secure comes from researchers in the Netherlands, who recently put out a paper announcing a card security idea they’re calling Quantum-Secure Authentication. According to its creators, this approach relies on “the unique quantum properties of light to create a secure question-and-answer exchange that cannot be spoofed or copied. From their literature:
“Traditional magnetic-stripe-only cards are relatively simple to use but simple to copy. Recently, banks have begun issuing so-called ‘smart cards’ that include a microprocessor chip to authenticate, identify & enhance security. But regardless of how complex the code or how many layers of security, the problem remains that an attacker who obtains the information stored inside the card can copy or emulate it. The new approach…avoids this risk entirely by using the peculiar quantum properties of photons that allow them to be in multiple locations at the same time to convey the authentication questions & answers. Though difficult to reconcile with our everyday experiences, this strange property of light can create a fraud-proof Q&A exchange, like those used to authorize credit card transactions.” Continue reading