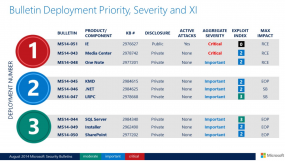
An industrial maintenance and construction firm in Tennessee that was hit by a $327,000 cyberheist is suing its financial institution to recover the stolen funds, charging the bank with negligence and breach of contract. Court-watchers say the lawsuit — if it proceeds to trial — could make it easier and cheaper for cyberheist victims to recover losses.
 In May, 2012, Kingsport, Tenn.-based Tennessee Electric Company Inc. (now TEC Industrial) was the target of a corporate account takeover that saw cyber thieves use a network of more than four dozen money mules to siphon $327,804 out of the company’s accounts at TriSummit Bank.
In May, 2012, Kingsport, Tenn.-based Tennessee Electric Company Inc. (now TEC Industrial) was the target of a corporate account takeover that saw cyber thieves use a network of more than four dozen money mules to siphon $327,804 out of the company’s accounts at TriSummit Bank.
TriSummit was able to claw back roughly $135,000 of those unauthorized transfers, leaving Tennessee Electric with a loss of $192,656. Earlier this month, the company sued TriSummit in state court, alleging negligence, breach of contract, gross negligence and fraudulent concealment.
Both companies declined to comment for this story. But as Tennessee Electric’s complaint (PDF) notes (albeit by misspelling my name), I called Tennessee Electric on May 10, 2012 to alert the company about a possible cyberheist targeting its accounts. I’d contacted the company after speaking with a money mule who’d acknowledged receiving thousands of dollars pulled from the firm’s accounts at TriSummit.
According to the complaint, the attackers first struck on May 8, after Tennessee Electric’s controller tried, unsuccessfully, to log into the bank’s site and upload that week’s payroll batch (typically from $200,000 to $240,000 per week). When the controller called TriSummit to inquire about the site problems, the bank said the site was probably undergoing maintenance and that the controller was welcome to visit the local bank branch and upload the file there. The controller did just that, uploading four payroll batches worth $202,664.47.
[SIDE NOTE: When I spoke with Tennessee Electric’s controller back in 2012, the controller for the company told me she was asked for and supplied the output of a one-time token upon login. This would make sense given the controller’s apparent problems accessing the bank’s Web site. Cyber thieves involved in these heists typically use password-stealing malware to control what the victim sees in his or her browser; when a victim logs in at a bank that requires a one-time token, the malware will intercept that token and then redirect the victim’s browser to an error page or a “down for maintenance” message — all the while allowing the thieves to use the one-time token and the victim’s credentials to log in as the legitimate user.]
On May 9, Tennessee Electric alleges, TriSummit Bank called to confirm the $202,664.47 payroll batch — as per an agreement the bank and the utility had which called for the bank to verbally verify all payment orders by phone. But according to Tennessee Electric, the bank for some reason had already approved a payroll draft of $327,804 to be sent to 55 different accounts across the United States — even though the bank allegedly never called to get verification of that payment order.
Tennessee Electric alleges that the bank only called to seek approval for the fraudulent batch on May 10, more than a day after having approved it and after I contacted Tennessee Electric to let them know they’d been robbed by the Russian cyber mob.
ANALYSIS
This lawsuit, if it heads to trial, could help set a more certain and even standard for figuring out who’s at fault when businesses are hit by cyberheists (for better or worse, most such legal challenges are overwhelmingly weighted toward banks and quietly settled for a fraction of the loss).
Consumers who bank online are protected by Regulation E, which dramatically limits the liability for consumers who lose money from unauthorized account activity online (provided the victim notifies their financial institution of the fraudulent activity within 60 days of receiving a disputed account statement).
Businesses, however, do not enjoy such protections. States across the country have adopted the Uniform Commercial Code (UCC), which holds that a payment order received by the [bank] is “effective as the order of the customer, whether or not authorized, if the security procedure is a commercially reasonable method of providing security against unauthorized payment orders, and the bank proves that it accepted the payment order in good faith and in compliance with the security procedure and any written agreement or instruction of the customer restricting acceptance of payment orders issued in the name of the customer.”
Under state interpretations of the UCC, the most that a business hit with a cyberheist can hope to recover is the amount that was stolen. That means that it’s generally not in the business’s best interests to sue their bank unless the amount of theft was quite high, because the litigation fees required to win a court battle can quickly equal or surpass the amount stolen. Continue reading