Last year, a top official from big-three credit bureau Experian told Congress that the firm was not aware of any consumers that had been harmed by an incident in which a business unit of Experian sold consumer records directly to an online identity theft service for nearly 10 months. Today’s post presents evidence that among the ID theft service’s clients was an identity theft and credit card fraud ring of at least 32 people who were arrested last year for allegedly using the information to steal millions from more than 1,000 victims across the country.
On March 31, 2014, 26-year-old Idris Soyemi of Brooklyn, New York pleaded guilty in a New Hampshire court to one count of wire fraud. In Soyemi’s guilty plea hearing, the prosecutor laid out how Soyemi on several occasions bought Social Security numbers, dates of birth and other personal information from an online identity theft service run by guy named Hieu Minh Ngo.
Ngo is a Vietnamese national who for several years ran an online identity theft service called superget.info. Shortly after my 2011 initial story about his service, Ngo tauntingly renamed his site to findget.me. The Secret Service took him up on that challenge, and succeeded in luring him out of Vietnam into Guam, where he was arrested and brought to New Hampshire for trial. He pleaded guilty earlier this year to running the ID theft service, and the government has been working on rounding up his customers ever since.
According to Soyemi’s guilty plea transcript (PDF), U.S. Secret Service agents seized control over Ngo’s email account in February 2013 and used it to interact with his customers. Posing as Ngo, the undercover agent reached out to Soyemi and wrote, “I’m back. You doing tax refund or credit card?”, asking Soyemi whether he was buying personal data on consumers to set up new lines of credit in their names or to file fraudulent tax refund requests with the IRS — a rapidly growing form of cybercrime. Soyemi responded, “I do credit cards but can you tell me about tax refund?” (if you missed last month’s story about an Ohio man who’s accused of using Ngo’s service to file at least 150 fraudulent tax refund requests with the IRS, check that out here).
Interestingly, Soyemi was part of a huge network of nearly three dozen people who were rounded up last year and charged with taking out new credit cards in victims’ names and then using the cards to make millions of dollars in retail purchases that were then fenced on the black market. From an April 2013 story in the Jersey Journal:
“The leaders of the group, authorities say, purchased the identities of unsuspecting victims from online brokers, who got the information from computer hackers across the United States….”
“In a process known as ‘punching,’ electronic account information from the cards’ magnetic strips would be transferred onto counterfeit cards, which were provided to “strikers” who conducted the purchases at retailers all over the Eastern Seaboard, authorities say…”
….”The investigation has identified nearly 1,000 victims across the country and millions of dollars in phony transactions, authorities say.”
“Authorities say the suspects spent the proceeds on luxury cars, high-end jewelry and other lavish expenses. Some of the money was additionally sent to accounts in Nigeria, authorities say.”
Further tying this group to Ngo’s service is a four-count indictment (PDF) lodged against another man named in that identity theft ring roundup by the New Jersey prosecutor’s office: Oluwaseun Adekoya, 25, of Sewaren, NJ. Adekoya’s indictment makes numerous references to his alleged purchase of hundreds of consumer records from an online identity theft service that was taken over by U.S. Secret Service agents in February 2013 (recall that in Soyemi’s guilty plea hearing government prosecutors said that in that same month undercover Secret Service agents assumed control of the email account tied to Ngo’s identity theft service).
According to the government, Adekoya was a ringleader among the group who directed the activities of several men, including Atlanta, Ga. resident Adebayo Adegbesan, another defendant in the identity theft ring who pleaded guilty in New Hampshire recently. A transcript of Adegbesan’s guilty plea hearing doesn’t mention Ngo, but it does reveal that the New Hampshire district court and the U.S. Attorney who is prosecuting the case — Arnold Huftalen — have their hands full processing a large number of defendants tied to the same case.
Prosecutors told the court that they’d hoped to lure Adekoya to New Hampshire after he’d arranged to collect what he believed was more than $100,000 worth of bank account information encoded onto white plastic cards that could be used to pull cash out of ATMs. Instead, Adekoya allegedly sent Adegbesan and three others to pick up the cards.
I enjoyed reading the discussion between the court and Huftalen, particularly the part about the “SODDI defense.” Here, the two are discussing the large number of defendants related to this case. Also, as it turns out, Matthew O’Neil — the U.S. Secret Service agent who came up with the plan to lure Ngo out of Vietnam and to entice his clients into traveling to New Hampshire — was recently honored with the Secret Service Agent of the Year award for his work on the case.
THE COURT: Okay. Fine. Just curious because I’ve seen a few of them come through now. Maybe related to this, maybe unrelated to this. I seem to have a number of these with you right now.
MR. HUFTALEN: I have more than I’d like, and I’m sure you do, too.
THE COURT: People are told to come up to New Hampshire and do this stuff. It’s a good approach. You end up catching a lot of people.
MR. HUFTALEN: The whole lure, I mean, is to eliminate this SODDI defense, S-O-D-D-I, some other dude did it. When you’re talking with somebody on the computer, as you know, unless you have eyes on him on the keyboard, there’s always that reasonable doubt.
THE COURT: It’s a very effective law enforcement technique. Believe me, I’m not in any way being critical of it. I’m curious about it and I of course want to see that, to the extent I have responsibilities with respect to it, that I fulfill those responsibilities, and I’m just learning about it, trying to understand it.
MR. HUFTALEN: I don’t think you will see a whole lot more of these.
THE COURT: It seems like you have a very creative active agent who’s working with you on at least some of these cases and I just was wondering.
MR. HUFTALEN: Who was in Washington, D.C. this week to get an award because he was selected as the Secret Service Agent of the year.
THE COURT: Really. That’s what I mean. He seems like a go-getter kind of person and people like that tend to produce lots of cases.
MR. HUFTALEN: And the targets that he and I are targeting are not like the person who’s sitting here in court today.
THE COURT: They’re people above him.
MR. HUFTALEN: Way above.
Several state attorneys general are now investigating the apparent breach at Experian’s subsidiary. According to U.S. government investigators, the data was not obtained directly from Experian, but rather via Columbus, Ohio-based US Info Search. US Info Search had a contractual agreement with a California company named Court Ventures, whereby customers of Court Ventures had access to the US Info Search data as well as Court Ventures’ data, and vice versa. Experian came into the picture in March 2012, when it purchased Court Ventures (along with all of its customers — including Mr. Ngo). For almost ten months after Experian completed that acquisition, Ngo continued siphoning consumer data and making his wire transfers.
A transcript (PDF) of Ngo’s guilty plea proceedings shows that his ID theft business attracted more than 1,300 customers who paid at least $1.9 million between 2007 and Feb. 2013 to look up Social Security numbers, dates of birth, addresses, previous addresses, phone numbers, email addresses and other sensitive data on more than three million Americans. Meanwhile, Experian has maintained that “no Experian database was accessed” in the fraud stemming from Ngo’s identity theft service. Check out a fact-checked version of Experian’s talking points on the matter here.



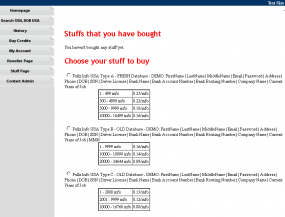

“Experian has maintained that “no Experian database was accessed” in the fraud stemming from Ngo’s identity theft service.”
Seems to me Experian is asserting a little SOFDI smokescreen of its own.
(I wonder if/when Experian management will ever be held to account or be indicted.)
Feels nice.
ಠ_ಠ FAIL
Adebayo Adegbesan and Oluwaseun Adekoya.
Nigerian names.
Is Nigeria the biggest exporter of con-artists in the world?
I think we should be told.
How many Nigerians does it take to screw in a light bulb?
We’ll never know because they keep stealing it.
Great piece Brian. Any idea why such an important case would be handled in New Hampshire as opposed to NY or LA? Seems like NH has a ton of these hacker cases for such a little state.
Probably because there’s no backlog in that court district… That’s my guess. Either that, or the prosecutor has a vacation home up there.
Theodore – I doubt the government decides where to charge someone based on vacation properties of its employees. Maybe there are servers or something up there so that’s why so many cyber cases are there. Maybe Brian knows.
It’s all about establishing jurisdiction. The agent was from NH and had victims in that state. Getting the defendants to travel to there, as stated in the linked complaints, helps prosecutors avoid the “some other dude did it” or SODDI defense.
BRAVO BRIAN KREBS BRAVO…… WILL THANK U LATER
According to the indictment, the defendant was charged with attempting to defraud banks located in New Hampshire.
“…the defendant … devised a scheme and artifice to defraud several “financial institutions” (as that term is defined in 18 U.S.C. §20) including Peoples United Bank in Manchester, NH and St. Mary’s Bank in Manchester, NH…”
And in addition, the undercover agent was located in NH, and the defendant was lured to NH to obtain fake cards and used them at NH ATMs. It’s all in the indictment that Brian links to.
“the defendant, …communicated with an individual who, unbeknownst to the defendant, was an undercover agent located in New Hampshire, with respect to planning and carrying out a scheme whereby the defendant would travel to New Hampshire, and would cause others to travel to New Hamp shire, for the sole purpose of using approximately two hundred (200) white plastic cards (which the defendant believed were encoded with actual bank account info rmation) to fraudulently obtain money and funds from ATMs in New Hampshire. “
i understand that…but why New Hampshire? seems like something more sophisticated places in usa would do…i always thought NH was the West Virginia of the north.
“The recipe for perpetual ignorance is: Be satisfied with your opinions and content with your knowledge.”
Get out your map of the U.S.A. and you’ll see that West Virginia isn’t in the south. Not that New Hampshire and West Virginia have any striking similarities, anyway.
“seems like something more sophisticated places in usa would do”
It seems to me the criminals are flocking to the more sophisticated places where people are sophisticated enough to think that criminals are the real victims.
+100
Brian,
Thanks for you diligence in pursuing this matter.
To me, it is obvious that Experian did a poor job of vetting/due diligence on Ngo (and possibly others). This may be criminal or merely misfeasance on Experian’s part.
Questions/comments:
Experian has access to extremely private data, which it sells to credible creditors (??). It seems to me that the Experian’s bad/misfeasant actors sold the data to the wrong person/people. This seems to be either poor judgment, a systemic problem(s) at Experian, negligence, ineptitude or criminal activity at Experian.
How do we expose the bad actors at Experian who were involved in this, for whatever reason? How do we make sure that these bad actors never again have the opportunity to sell our sensitive data, at any company? How do we force Experian and others to be more forthcoming, honest, transparent in matters like this?
You don’t – their entire business model relies upon cheaply accumulating and selling data about as many people as they can. Spending a lot of money vetting the data breaks their profits, as does vetting the customers. Step one would be imposing strong regulation, which would quickly find their way of doing business unethical and unsupportable in the long run, so because of their power and money that will never happen.
Errata: “you diligence” should be “your diligence” .
Interesting stuff, I need to check out those PDF files
Very interesting case. I agree with Jerry, I think that exposing the people who were involved in this is definitely necessary to solve the problem completely and prevent it from happening again. What do you think the first step in this process should be? And how can people know whether or not to trust employees of Experian in the future once this problem is resolved?
The problem lies squarely with Experian in this breach since they have the deep pockets, the resources and obligation to prevent it. The only way to have them provide better security is through fines and law suits from every fraudulence use of their information. Consumers should be able to request that their information be removed from their databases. If the data isn’t their its less likely to be compromised and consumers can then make other arrangements with vendors for providing personal information. Once upon a time, this is how it was done.
Thanks for the insights, Brian. It took me a couple of read-through a to realize that SODDI stands for “some other guy did it.” It’s a shady situation and your dry wit helps to maintain a sense of humor about an otherwise crummy situation. I hope many Congressional aides are on your distribution list. PS – I hear mention of you on all sorts of data security webinars and conversations – kudos.
The big question I have not yet seen (or completely missed) is was there any *explicit* agreement on who would verify users?
Court Ventures or Info Search, or both?
Its seems there may be no *clear* agreement at all, else one of the two would have notified the press likely.
I’m biased, but that would fit the nature of these companies, that usually don’t care too much about the data they use. After all, they don’t suffer if a breach occurs. Experian tops it all, with no regard to users at all. Even if they turn out to be innocent, their attitude is one that does not suggest any worry about how many people got their data stolen through their services …
Related to this there is also the technical side, in addition to the moral and legal side. Let’s say I’m a legitimate user of Court Ventures / Experian, and I access data from Info Search. What and how will I get logged?
Does Court Ventures / Experian log my attempt or Info Search, or both. And for the latter do they see me as me, of just as someone though Court Ventures / Experian.
I ask, as the original press on this topic seems to suggest the logging was poor on both sides. Court Ventures / Experian only had partial, and Info Search none. Either it was never logged or already discarded.
Again this fits my bias, that no serious logging may have existed at all. But in this case I would be delighted if my bias is indeed that, and companies like this, do in fact keep proper logs most of the time, and this was the exception.
Again, I find it interesting that this is described as an Experian “breach”, when they weren’t hacked — they willingly sold access to this data to Ngo.
Their Terms of Service were breached, if I understand correctly.
Considering the power the credit agencies wield in peoples lives you’d think they would be a bit more careful about who they deal with, after all it’s not like ID theft is something new last week.
Also seem to do poor job of simple sanity checks on data in individuals files. Checking mine several years ago with all 3 agencies so I do not remember who had the obvious error. Technically I am a Jr., but rarely use except on most official of official docs. 1 of my reports had me crossed up with my father so according to the file I was working for the New Haven Railroad 12 years before I was born. Would think that would be a simple catch on their part, but obviously not.
Bullcrap. I know a victim.
“While other industries stagger under the weight of recession, in cybercrime, business is apparently booming.
Yet in terms of economics, there’s something very wrong with this picture. Generally the demand for easy money outstrips supply. Is cybercrime an exception? If getting rich were as simple as downloading and running software, wouldn’t more people do it, and thus drive down returns?
We have examined cybercrime from an economics standpoint and found a story at odds with the conventional wisdom. A few criminals do well, but cybercrime is a relentless, low-profit struggle for the majority. ” http://www.nytimes.com/2012/04/15/opinion/sunday/the-cybercrime-wave-that-wasnt.html?_r=2&
Thomas Piketty’s economic data ‘came out of thin air’
http://www.theguardian.com/business/2014/may/24/thomas-picketty-economics-data-errors
Crime doesn’t pay~Enough…