Mac malware is back in the news again. Last week, security firm F-Secure warned that it had discovered a Trojan built for OS X that was disguised as a PDF document. It’s not clear whether this malware is a present threat — it was apparently created earlier this year — but the mechanics of how it works are worth a closer look because it challenges a widely-held belief among Mac users that malicious software cannot install without explicit user permission.
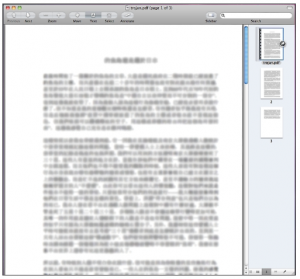
F-Secure said the Mac malware, Trojan-Dropper: OSX/Revir.A, may be attempting to copy the technique implemented by Windows malware, which opens a PDF file containing a “.pdf.exe” extension and an accompanying PDF icon. F-Secure was careful to note that the payload installed by the dropper, Backdoor:OSX/Imuler.A, phones home to a placeholder page on the Web that does not appear to be capable of communicating back to the Trojan at the moment.
I wanted to understand a bit more about how this Trojan does its dirty work, so I contacted Broderick Aquilino, the F-Secure researcher who analyzed it. Aquilino said the sample is a plain Mach-O binary — which we’ll call “Binary 1”, that contains PDF file and another Mach-O binary (Binary2). Mach-O, short for Mach object, is a file format for executable files on OS X.
According to Aquilino, when you run Binary1, it will extract the PDF file from its body, drop it in the Mac’s temporary or “tmp” directory, and then open it. This is merely a decoy, as Binary1 continues to extract Binary2 from itself — also into the “tmp” directory — and then runs the file.
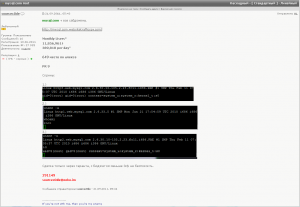
Upon execution, Binary2 downloads another binary from [omitted malware download site] and saves it as /tmp/updtdata. For the sake of continuity, we’ll call this latest file “Binary3.” Binary2 then executes and downloads the third binary, which opens up a backdoor on the OS X host designed to allow attackers to administer the machine from afar.
“All of this happens without the user needing to input their password,” Aquilino said.