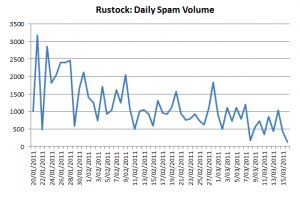
Who controlled the Rustock botnet? The question remains unanswered: Microsoft’s recent takedown of the world’s largest spam engine offered tantalizing new clues to the identity and earnings of the Rustock botmasters. The data shows that Rustock’s curators made millions by pimping rogue Internet pharmacies, but also highlights the challenges that investigators still face in tracking down those responsible for building and profiting from this complex crime machine.
 Earlier this month, Microsoft crippled Rustock by convincing a court to let it seize dozens of Rustock control servers that were scattered among several U.S.-based hosting providers. Shortly after that takedown, I began following the money trail to learn who ultimately paid the botnet controllers’ hosts for their services.
Earlier this month, Microsoft crippled Rustock by convincing a court to let it seize dozens of Rustock control servers that were scattered among several U.S.-based hosting providers. Shortly after that takedown, I began following the money trail to learn who ultimately paid the botnet controllers’ hosts for their services.
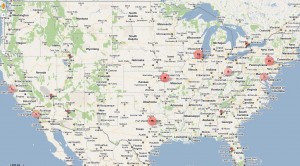
According to interviews with investigators involved in the Rustock takedown, approximately one-third of the control servers were rented from U.S. hosting providers by one entity: A small business in Eastern Europe that specializes in reselling hosting services to shadowy individuals who frequent underground hacker forums.
KrebsOnSecurity.com spoke to that reseller. In exchange for the agreement that I not name his operation or his location, he provided payment information about the customer who purchased dozens of servers that were used to manipulate the day-to-day operations of the massive botnet.
The reseller was willing to share information about his client because the customer turned out to be a deadbeat: The customer walked out on two months worth of rent, an outstanding debt of $1,600. The reseller also seemed willing to talk to me because I might be able bend the ear of Spamhaus.org, the anti-spam group that urged ISPs worldwide to block his Internet addresses (several thousand dollars worth of rented servers) shortly after Microsoft announced the Rustock takedown.
I found the reseller advertising his services on a Russian-language forum that caters exclusively to spammers, where he describes the hardware, software and connection speed capabilities of the very servers that he would later rent out to the Rustock botmaster. That solicitation, which was posted on a major spammer forum in January 2010, offered prospective clients flexible terms without setting too many boundaries on what they could do with the servers. A translated version of part of his message:
“I am repeating again that the servers are legitimate, funded by us and belong to our company. To the datacenters, we are responsible to ensure that you are our client, and that you will not break the terms of use. Also, to you we are responsible to make sure that the servers are not going to be closed down because of credit card chargebacks, as it happens with servers funded with stolen credit cards. In conclusion, they do not have an abuse report center, they are suitable for legitimate projects, VPNs and everything else that does not lead to problems and complaints to the data center from active Internet users. Please, take it in consideration, so that nobody is pissed off and there is no bad impression from our partnership.”
The reseller said he had no idea that his customer was using the servers to control the Rustock botnet, but he hastened to add that this particular client didn’t attract too much attention to himself. According to the reseller, the servers he resold to the Rustock botmaster generated just two abuse complaints from the Internet service providers (ISPs) that hosted those servers. Experts say this makes sense because botnet control servers typically generate few abuse complaints, because they are almost never used for the sort of activity that usually prompts abuse reports, such as sending spam or attacking others online. Instead, the servers only were used to coordinate the activities of hundreds of thousands of PCs infected with Rustock, periodically sending them program updates and new spamming instructions.
The reseller was paid for the servers from an account at WebMoney, a virtual currency similar to PayPal but more popular among Russian and Eastern European consumers. The reseller shared the unique numeric ID attached to that WebMoney account — WebMoney purse “Z166284889296.” That purse belonged to an “attested” WebMoney account, meaning that the account holder at some point had to verify his identity by presenting an official Russian passport at a WebMoney office. A former law enforcement officer involved in the Rustock investigation said the name attached to that attested account was “Vladimir Shergin.” According to the reseller, the client stated in an online chat that he was from Saint Petersburg, Russia.
Continue reading →
 Scammers typically kick into high gear during tax season in the United States, which tends to bring with it a spike in phishing attacks that spoof the Internal Revenue Service. Take, for example, a new scam making the rounds via email, which warns of discrepancies on the recipient’s income tax return and requests that personal information be sent via fax to a toll-free number.
Scammers typically kick into high gear during tax season in the United States, which tends to bring with it a spike in phishing attacks that spoof the Internal Revenue Service. Take, for example, a new scam making the rounds via email, which warns of discrepancies on the recipient’s income tax return and requests that personal information be sent via fax to a toll-free number.