Most Web sites use JavaScript, a powerful scripting language that helps make sites interactive. Unfortunately, a huge percentage of Web-based attacks use JavaScript tricks to foist malicious software and exploits onto site visitors. To protect yourself, it is critically important to have an easy method of selecting which sites should be allowed to run JavaScript in the browser.
It is true that selectively allowing JavaScript on known, “safe” sites won’t block all malicious scripting attacks: Even legitimate sites sometimes end up running malicious code when scammers figure out ways to sneak tainted, bogus ads into the major online ad networks. But disallowing JavaScript by default and selectively enabling it for specific sites remains a much safer option than letting all sites run JavaScript unrestricted all the time.
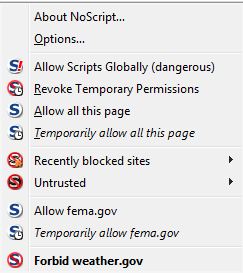 Firefox has many extensions and add-ons that make surfing the Web a safer experience. One extension that I have found indispensable is NoScript. This extension lets the user decide which sites should be allowed to run JavaScript, including Flash Player content. Users can choose to allow specific exceptions either permanently or for a single browsing session.
Firefox has many extensions and add-ons that make surfing the Web a safer experience. One extension that I have found indispensable is NoScript. This extension lets the user decide which sites should be allowed to run JavaScript, including Flash Player content. Users can choose to allow specific exceptions either permanently or for a single browsing session.
The NoScript extension makes it easy to place or remove these restrictions on a site-by-site basis, but a novice user may need some practice to get the hang of doing this smoothly. For instance, it’s not uncommon when you’re shopping online to come across a site that won’t let you submit data without fully allowing JavaScript. Then, when you enable scripting so that you can submit your address and payment information, the page often will reload and clear all of the form data you’ve already supplied, forcing you to start over. Also, many sites host content from multiple third-party sites, and users who prefer to selectively enable scripts may find it challenging to discover which scripts need to be enabled for the site to work properly.
Chrome also includes similar script- and Flash blocking functionality that seems designed to minimize some of these challenges by providing fewer options. If you tell Chrome to block JavaScript on all sites by default, when you browse to a site that uses JavaScript, the upper right corner of the browser displays a box with a red “X” through it. If you click that and select “Always allow JavaScript on [site name]” it will permanently enable JavaScript for that site, but it doesn’t give you the option to block third-party JavaScript content on the site as Noscript does. In my testing, I had to manually refresh the page before Chrome allowed scripting on a site that I’d just whitelisted.