New and novel malware appears with enough regularity to keep security researchers and reporters on their toes. But, often enough, there are seemingly new perils that really are just old threats that have been repackaged or stubbornly lingering reports that are suddenly discovered by a broader audience. One of the biggest challenges faced by the information security community is trying to decide which threats are worth investigating and addressing. To illustrate this dilemma, I’ve analyzed several security news headlines that readers forwarded to me this week, and added a bit more information from my own investigations.
I received more than two dozen emails and tweets from readers calling my attention to news that the source code for the 2.0.8.9 version of the ZeuS crimekit has been leaked online for anyone to download. At one point last year, a new copy of the ZeuS Trojan with all the bells and whistles was fetching at least $10,000. In February, I reported that the source code for the same version was being sold on underground forums. Reasonably enough, news of the source leak was alarming to some because it suggests that even the most indigent hackers can now afford to build their own botnets.
We may see an explosion of sites pushing ZeuS as a consequence of this leak, but it hasn’t happened yet. Roman Hüssy, curator of ZeusTracker, said in an online chat, “I didn’t see any significant increase of new ZeuS command and control networks, and I don’t think this will change things.” I tend to agree. It was already ridiculously easy to start your own ZeuS botnet before the source code was leaked. There are a number of established and relatively inexpensive services in the criminal underground that will sell individual ZeuS binaries to help novice hackers set up and establish ZeuS botnets (some will even sell you the bulletproof hosting and related amenities as part of a package), for a fraction of the price of the full ZeuS kit.
My sense is that the only potential danger from the release of the ZeuS source code is that more advanced coders could use it to improve their current malware offerings. At the very least, it should encourage malware developers to write more clear and concise user guides. Also, there may be key information about the ZeuS author hidden in the code for people who know enough about programming to extract meaning and patterns from it.
Are RATs Running Rampant?
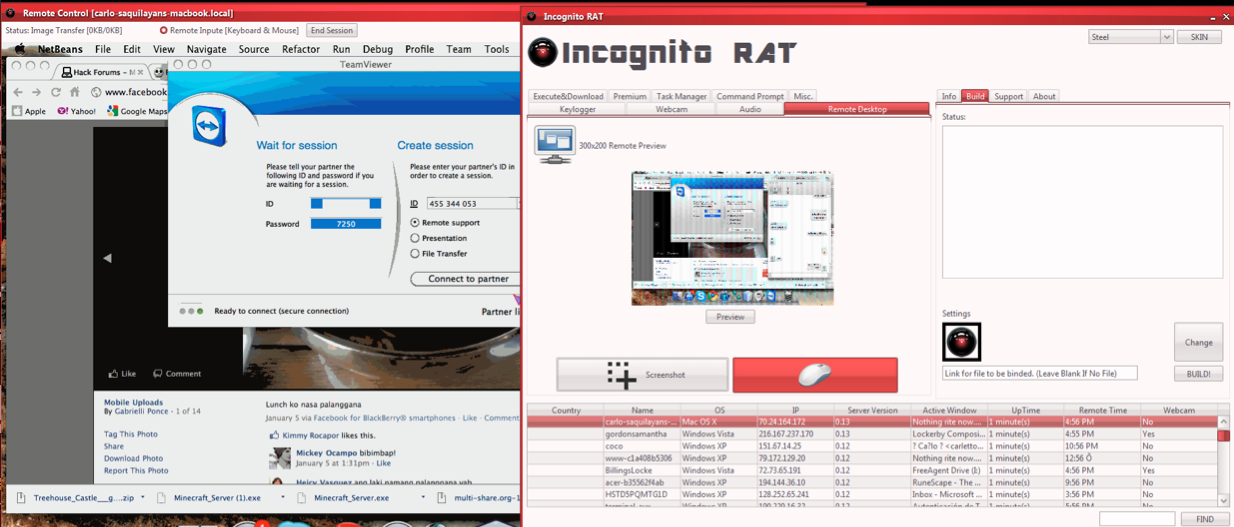
Last week, the McAfee blog included an interesting post about a cross-platform “remote administration tool” (RAT) called IncognitoRAT that is based on Java and can run on Linux, Mac and Windows systems. The blog post featured some good details on the functionality of this commercial crimeware tool, but I wanted to learn more about how well it worked, what it looks like, and some background on the author.
Those additional details, and much more, were surprisingly easy to find. For starters, this RAT has been around in one form or another since last year. The screen shot below shows an earlier version of IncognitoRAT being used to remotely control a Mac system.
The kit also includes an app that allows customers to control botted systems via jailbroken iPhones.
The following video shows this malware in action on a Windows system. This video was re-recorded from IncognitoRAT’s YouTube channel (consequently it’s a little blurry), but if you view it full-screen and watch carefully you’ll see a sequence in the video that shows how the RAT can be used to send e-mail alerts to the attacker. The person making this video is using Gmail; we can see a list of his Gchat contacts on the left; and his IP address at the bottom of the screen. That IP traces back to a Sympatico broadband customer in Toronto, Canada, which matches the hometown displayed in the YouTube profile where this video was hosted. A Gmail user named “Carlo Saquilayan” is included in the Gchat contacts visible in the video.
The IncognitoRat kit is sold on a English-language script kiddie hacker forum called HackForums.net by “Mr. Incognito,” but acquaintances on the forum refer to him as “Carlo.” Carlo describes himself on HackForums as a 19-year-old college student; he did not respond to repeated requests for comment. Anyway, so much for going incognito: This Facebook account belongs to a Carlo Saquilayan from Toronto, Ontario, and includes a nice picture of a young man in sunglasses and a leather jacket.
CrimePack Resurfaces
Several security forums were abuzz last week over the apparent leak of another crimekit. It’s a recent version of CrimePack, an exploit kit that I’ve profiled on this blog a few times. Will this lead to an outbreak of newly-hacked Web sites infected with the CrimePack exploit kit? I don’t think it’s likely, for a couple of reasons. First, this was initially leaked last fall, not long after its author released it. Second, I reached the author of this crimekit via instant message, and got his reaction. He told me that a main component of the kit — the part that tries to attack vulnerabilities in Adobe’s PDF Reader — was broken in the version that got leaked, and remains largely non-functional.
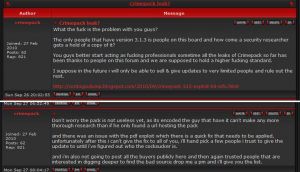 “I deliver this copy to like 20 people without the domain lock as a last copy, but it got leaked to someone, same day,” said “Crim,” the CrimePack author. “After I saw that the PDF exploit was not working, so pretty much no exploits will work as it will generate error when sending exploits. I was so pissed off when it leaked, so I refused to send out fixed copies.” A strongly-worded snippet of chatter from an exclusive hacker forum where Crim is co-administrator is included in the screen shot above, and seems to support his claim.
“I deliver this copy to like 20 people without the domain lock as a last copy, but it got leaked to someone, same day,” said “Crim,” the CrimePack author. “After I saw that the PDF exploit was not working, so pretty much no exploits will work as it will generate error when sending exploits. I was so pissed off when it leaked, so I refused to send out fixed copies.” A strongly-worded snippet of chatter from an exclusive hacker forum where Crim is co-administrator is included in the screen shot above, and seems to support his claim.
Sunspots are Nothing New
Security firm Trusteer said it has identified a little-known Windows malware platform that rivaled ZeuS in sophistication and functionality. In a blog post on May 11, 2011, Trusteer’s Amit Klein described the novelty of this malware, which the company dubbed “Sunspot”. Klein said Sunspot “reveals a new approach to financial malware development. Unlike purpose built financial fraud platforms like Zeus, SpyEye, Bugat, and others, it appears Sunspot was not originally developed as crime ware. If this is the case, we could be witnessing a sea change in malware development where general purpose and little know[n] malware platforms are re-programmed to carry out financial fraud. This will make it even more difficult to defend against attacks since banks will be ambushed by a growing number of unique financial malware platforms.”
When I first read Trusteer’s blog post, I pinged a number of security experts who study malware for a living, to get their thoughts on whether this was a unique threat. Aviv Raff, CTO and co-founder of security alert service Seculert, told me on Wednesday that he’d wrangled a copy of the malware and that it appeared to be a souped-up version of a well-known bot released in the middle of the last decade called Nethell, but also known as Limbo and Ambler. Then on Thursday, Microsoft‘s Tareq Saade & Tim Liu chimed in, saying they’d also pegged Sunspot as an evolved version of Ambler.
Trusteer’s Klein acknowledged that there appeared to be similarities between Sunspot and Limbo/Nethell/Ambler, but said there are major innovations in the way that Sunspot attacks the victim’s browser. He observed that much as the leak of the ZeuS code may soon give some enterprising malware coder ideas about how to extend the capabilities of an existing malware family, it appears that someone has taken a tried-and-true bot family and jazzed it up with a new set of wheels.
“Whether this is an evolution of Limbo/Nethell/Ambler, or merely ‘cannibalizing’ pieces of that malware to build a completely new malware is anyone’s guess,” Klein said in an email to KrebsOnSecurity. “Clearly they are both built with access to some common source code, but beyond that it’s difficult to accurately tell. From our perspective the difference [outweighs] the similarities, so we feel that a new name is in place.”
Keep the tips coming, please – they are usually helpful and always much appreciated. But do turn a skeptical eye to reports of “new” threats – many times we discover that something new is really not news at all.




Incognito Carlo took his picture down pretty quick. Great work, Brian!
Great article Brian.
And kudos on the detective work yet again. The fact that the Facebook account holder removed access to the page points to you being deadon. Silly boy may have even been better just leaving it up 😀
I suppose someone this careless would probably use IP’s to access FB that can be traced to him as well.
Uh oh, you mentioned Macs and Malware in the same article!
I remember all the ruckus that article you wrote called “When Macs Attack” caused.
darkode and hackforums being mentioned in the same article thats a first!
makes me chuckle, though hackforum isnt too bad has lots of kids who dont know the value of the databases they have hacked accidently will sell them to you for a decent price.
but it is full of hormonal scriptkiddies with ego problems.
i do enjoy the fact that after getting a warning there for speaking about black hat activities one of the staff members gave me a link to a carding forum! (though im not a carder!)
Funny how, after a profanity laced rant, the CrimePak author demands that all his follows act professionally.
“Professionally” is a relative term. Every job has its own code of ethics and professionalism.
ooooo, a perp in canada? we’ve got some *nice* criminal mischief laws for that. at least we do if he ever used the tool himself.
Is there a way to found out if someone it using this on you?