Michaels Stores said this month that it had replaced more than 7,200 credit card terminals from store registers nationwide, after discovering that thieves had somehow modified or replaced machines to include point of sale (POS) technology capable of siphoning customer payment card data and PINs. The specific device used by the criminal intruders has not been made public. But many devices and services are sold on the criminal underground to facilitate the surprisingly common fraud.
POS skimmers typically are marketed and sold in one of three ways: Pre-compromised POS terminals that can be installed at the cash register; Fake POS devices that do not process transactions but are designed to record data from swiped cards and PIN entries; or Do-it-yourself kits that include all parts, wiring and instructions needed to modify an existing POS terminal.
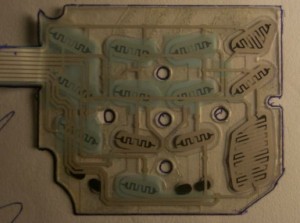
I spoke at length to a POS skimmer seller who has been peddling POS modification devices on an exclusive underground fraud forum for more than a year. From the feedback left on his profile it is clear he had many satisfied customers. Buyers specify the make and model of the POS equipment they want to compromise (this guy specializes in hacking VeriFone devices, but he also advertises kits for devices manufactured by POS makers Ingenico, Xyrun, TechTrex).
His skimmer kit includes a PIN pad skimmer and two small circuit boards; One is a programmable board with specialized software designed to interact with the real card reader and to store purloined data; The other is a Bluetooth-enabled board that allows the thief to wirelessly download the stolen card data from the hacked device using a laptop or smartphone.
The PIN pad skimmer is an ultra-thin membrane that is inserted underneath the original silicon PIN pad. It records every button pressed with a date and time stamp. The thief must also solder the two boards to the existing PIN pad device to hijack the machine’s power and data processing stream.
Many POS manufacturers include tamper-proof seals and other security devices designed to maintain the POS’s original function and form and to make it difficult for would-be thieves to modify the machines. Most POS skimmer makers furnish instructions for bypassing these protections.
The model shown here sells for $3,000 — including the skimmer devices, software and tutorial. Customers who purchase 10 or more kits can get them for about $2,000 apiece.
POS skimmer thieves use the data they steal to create counterfeit cards that can be used in combination with the victim’s PIN to withdraw cash from ATMs. Some POS skimmer sellers I’ve interviewed sell services that allow you to “rent” their skimmers; a few will even handle the ATM “cashout” process for a percentage of the proceeds from the theft.
POS skimmers serve as another reminder that debit cards can be riskier to use than credit cards. KrebsOnSecurity regular reader and commenter said it best in a recent comment:
“Using a credit card is safer for consumers who want to protect their bank accounts from unauthorized entry. Consumer protection laws are a lot stronger for credit cards than for debit cards. Unauthorized transactions on a credit card are simple to report and reverse. Resolving unauthorized withdrawals of [cash from] a debit card requires a lot of time and paper work. Many banks require that you file a police report before they will investigate an unauthorized withdrawal.”
[EPSB]
Have you seen:
Gang Used 3D Printers for ATM Skimmers…An ATM skimmer gang stole more than $400,000 using skimming devices built with the help of high-tech 3D printers, federal prosecutors say. Apparently, word is spreading in the cybercrime underworld that 3D printers produce flawless skimmer devices with exacting precision. In June, a federal court indicted four men from South Texas (PDF) whom authorities say had reinvested the profits from skimming scams to purchase a 3D printer.
[/EPSB]






How does the hacker get sufficient access to a POS device to be able to solder connections to it? I can see store employees maybe having enough time and access but non-employees, how would they pull it off?
They might be an employee of the store or perhaps have an identical machine to swap out at the counter when the teller turns around. It would only take a few seconds to swap the machine, and if it’s not connected intricately with their POS system, they may not notice it booting up when they turn back around, or will assume it’s just acting up.
An employee has a much better opportunity, of course.
If a fraudster wanted to, they could use social engineering and tell the teller they were from the credit card company and the machine is malfunctioning. Not too many tellers care enough to ask questions.
But how have all of Michaels’ stores pos machines been compromised. Did they buy them all at the same time from the same manufacturer? Who had access to all of these machines? This just seems too big to blame on a rogue employee.
They haven’t all been compromised. Michaels said fewer than 100 were compromised at stores around the country. They’ve replaced 7,200 POS terminals in response to the known compromises.
Neither hackers nor employers do it afaik. These skimmers get installed by shop owners.
I think most CC cards get stolen by business owners via their tills, not by ATM skimmers.
The crook usually replaces the store’s POS terminal with their compromised terminal. The process only takes a few moments and usually involves two or more individuals. One to distract while the other does the replacement. So the soldering would be done at home.
another option is pre paid debit cards you charge up when you want to go shopping, i charge mine up online from my regular bank account with the amount i expect to spend. This way if its compromised there wont be any money on it to steal.
…but if they skim the card number and PIN, they can still steal any money loaded on the card.
thats why you only charge up the amount you intend to spend, so there wont be any money on the card to steal
@Jeremy – 2 questions:
Do you pay a fee for using this type of card?
Obviously, you’re a male and you only go shopping when you need something specific. Females shop differently and don’t often “intend” to spend a specific amount. How could they know in advance what amount to pre-load on the card?
Maybe only males should be charged and women should get it for free just like they get everything else for free!
Yes, and budgeting is just way too complicated for any female I’ve met. What’s with all the numbers and those funny + and – symbols! Good thing there are no women on the internet to read my comment.
It’s not a put-down of women. It’s just the difference between hunters and gatherers.
I laugh to think that the gambling commissions of many places have better controls and routine inspections of electronic parts devices than local governments do for Point Of Sale Terminals, atms, and like machinery.
As in any criminal enterprise the lawful and persistent management of means, motive and operation is the only way to deal with this mess.
Means: At some point consumers have to have a trusted path for electronic parts; unfortunately this means that some electronic parts will be come unavailable to hobbyists.
Motive: As long as credit card companies can continue to submerge their losses via shifting costs (often in a hidden way) back onto consumers this will continue as a “victimless” crime which will not motivate improvements in the point of sale industry and _will_ motivate criminals as they can game the system. If a person built something to circumvent the encryption for criminal gain why isn’t the DMCA being used more in the prosecution?
Opportunity: Shouldn’t retailers and smb be held accountable for physical security of point of sale systems? If anyone tampered with a product like medicine or food consumers would be freaked out and retailers would feel the hurt and then make sure to reduce opportunity for these criminals to operate in their stores.
Banks have no choice but to absorb the losses on these types of thefts. It’s the law: Regulation E.
This has got to be a situation where the company contracted by Michaels to provide and service the POS registers is the actual culprit. What other single entity would have access to 7,200 of Michaels POS registers? I highly doubt that Michaels has an individual employee or group of employees who’ve conspired to pull off this massive theft in a multitude of states. The logistics of this operation would be crazy, not to mention easily tracked via travel and expense vouchers.
Brian can correct me if I am wrong , they removed 7200 POS devices for security reasons . I do believe only 70 to 90 of them where compromised . My thoughts are only my thoughts not one parasite but many are involved sure there is the main king pin that’s running the scheme . Anybody think why the USSS is investigating this whole scheme . Is this contained to the areas they claimed or is more why spread that the Joe Blow PUBLIC doesn’t know about . This scheme was well planned from what I am reading . Who’s ever involved they picked Michaels for there lack of over all security , hate to say it but it is true . In my opinion it’s worse than reported .
Actually the Secret Service is the branch of law enforcement that happens to handle counterfeiting and credit card fraud. It’s involvement doesn’t imply they think there is some terrorist plot or something.
Given that Michael’s is replacing so many, I would assume they think the substitution occurred in the chain of supply before the units were distributed to individual stores. They aren’t going to send technicians to every store to test every one of them; they’re going to send them all back to the factory and worry about which ones are compromised then.
I should know very well what the USSS job is it’s a wide scope of many thing (s) .
It’s involvement doesn’t imply they think there is some terrorist plot or something. (never stated that ) .
They aren’t going to send technicians to every store to test every one of them; they’re going to send them all back to the factory and worry about which ones are compromised then.
It’s the cheapest way out of it .
My view they where very weak in the over all security . What you pay for is what you get , the cost of being “CHEAP”.
I agree, there would be no way they would wan’t to take a chance that they missed finding some of the bad POS terminals. This is already a pulic relations nightmare, so to enstill confidence to their customers and say ” Hey we have take steps to stop any further breach” by replacing all our terminals is the only sensible thing to do.
I have to agree with TJ. If the crooks actually got to this many POS terminals, this leads me to believe this as well. All it takes is someone on the inside at the POS terminal company to have access and viola you have compromised POS terminals. If anyone recalls malware infected picture frames were distributed infected from the manufacturer before they even hit the store, it wasn’t till people start using them and d/l pictures to the that their AV clients went bananas and then started reporting it. So it wouldn’t be a stretch to imagine that. Most companies they install POS terminals do have their own people come in and set them up, or even ship them out ready to go to a customer in case of replacement, but to think that a gang covered this many POS terminals over many states seems a little bit of a stretch. I would bet that the POS provider is investigating to see if there is indeed an inside person doing this.
Were the 7200 PIN pads replaced because they were all compromised, or were only a portion compromised, and all were replaced just to be diligent?
It appears that much less than the 7200 were compromised, the wholesale replacement is for both their and consumer confidence. Michael’s has released a few documents on their site for consumers that believe they have been compromised as well as a listing on known “hit” stores
http://www.michaels.com/Corporate-%7C-Consumer-Information/notices,default,pg.html
Yes. Michaels is saying that they are only aware of fewer than 100 terminals that were compromised, but that they replaced 7,200 out of an abundance of caution.
It’s worth noting that Michaels only issued that press release you link to a day after I ran my story saying that compromised terminals were being found all across the United States, not just in Chicago as the company had originally reported.
http://krebsonsecurity.com/2011/05/breach-at-michaels-stores-extends-nationwide/
This should answer a “TON” of questions to everyone .
According to the indictment, which was unsealed on Wednesday, the gang skimmed hundreds of credit and debit card numbers after installing skimmers on cash registers in 99 Cents Only stores across southern California. They then used this information to create counterfeit credit cards, with which they stole $2 million.
http://www.informationweek.com/news/security/attacks/229218933
The lack of security ………….
Lack of security in the stores, yes. And yet the stores won’t pay for the losses because they don’t see them. The banks that issued the cards which were later counterfeited will take the loss.
@ Ray Butlers,
I don’t know how legislation covers this area in different countries, but it is my understanding the shops found to have compromised POS terminals suffer a lot more financially than just through bad P.R. They will pay massive fines/reimbursements to the bank through which the terminals were installed (agreed upon when the contract was signed) and /or they might have the terminals disconnected from the payment processing system (which means business suicide for most shops). I don’t know if or how those fines might be further redistributed to the various banks which issued the skimmed cards, I guess insurance companies might also get involved at some point. Things are even more blurred when the compromise does not occur in the shop but before, in the factory.
One thing is clear: this kind of losses, running in the hundreds of millions of $/Euros are not “sustainable”. Something got to be done quickly or the whole POS payment system will collapse.
So how does article relate to” How Scammers get your Email Address?”
Story on King5 / Seattle about the card swiper on the “vestibule entry” to the ATM machine at a Chase bank having been setup with a skimmer.
Apparently the vestibule entry doesn’t actually need a debit/credit card to open anyhow, they will open with any mag card swipe, e.g. grocery store reward card.
http://www.king5.com/news/consumer/Simple-way-to-protect-yourself-from-skimmers-122263904.html
@axial — I hadn’t seen that King5 story. thanks for the link.
FYI, I wrote about these door/vestibule skimmers back in January.
http://krebsonsecurity.com/2011/01/atm-skimmers-that-never-touch-the-atm/
Brian: your link anchor includes a trailing QUOTE character and as such doesn’t work properly:
a
href=”http://krebsonsecurity.com/2011/05/breach-at-michaels-stores-extends-nationwide/comment-page-1/#comment-21798"”
drop "
grr, and is there an option for me to tell wordpress “please always over-escape everything i write”, or a way to get a preview button?
here’s an overescaped version of what’s in your article…
a
href=”http://krebsonsecurity.com/2011/05/breach-at-michaels-stores-extends-nationwide/comment-page-1/#comment-21798"”
How is it possible for this douche to be selling criminal equipment to the online community for a whole entire year! with going unoticed? ; This really baffles me.
BTW what is the forum site, Brian? I would love to report it to the feds! 😀
If you think that Law enforcement is not on the Site that Brian found the Vendor than you have no idea of what is going on.
Law Enforcement no well were these Websites and are on every single one of them. Many the vendors are anonymous it takes money and time to investigate these guys. In the Past Police have taken down multiple of these sites with in weeks new ones arrive. Thus, they now prefer the sites stay up so they can try and track down the people using them.
If Brian was not a Member on Maza he would not be able to report from them.
In relation to the POS”S in various stores. There has only being one instance were there has being a Belief that POS were modified at the Factory and that has never being verified.
Ill lay out exactly how they did this and how active this activity now is. The US is one of the last countries that has not migrated to Chip and Pin[ which is not a solution] so Mag stripe cards are the Norm.
POS and ATM skimming is now a crime that has reached down into the Mass’s so you have crews from all over Russia , Bulgaria , Canadian Russian Mexican all doing skimming. The Teams that would have Hit Michael’s woud have walked in and swapped out those POS in seconds its that easy to do.
There is ways to stop this crime it so profitable its not stopping any time soon.
It seems to me that the authentication issue for these skimmer devices has to do with the untrustworthyness of machines that we don’t own, like POS terminals and ATMs. I wouldn’t trust a regular computer in a public place with my sensitive information, why should I trust a different kind of machine in a public place.
Especially since compromising one of these machines allows access to as many accounts as there are users of the machine. That’s a tempting target.
It would be great if there was some way to do end-to-end authentication from a device I own and control. It would have to work through the POS or ATM, ending at my bank. It would have a private key in the device, locked with a device-unique Pin/password function to prevent thieves from using it. I have to register my public key with the bank / credit card company. That would get rid of the need to trust the public card scanner and the pin-pad. My device would have to have some computing power since it would be doing one-time authentication, so I wouldn’t have to worry about somebody intercepting my credentials and reusing them – they would need my device.
I’m not sure what kind of infrastructure would need to be in place, but I’m guessing that Michael’s would be an interested customer. I know I would be interested in getting my own device.
I’m sure this would not solve all problems, but it would obsolete skimmer and pin-pad rip-offs.
All PIN pads (PIN Entry Devices aka PEDs) used for debit transactions must pass the PCI PTS approval process. The standards are updated periodically but not retroactively. A PED approved under PCI 1.0 is probably more vulnerable than a PCI 3.0 approved PED.
The hacked devices at Michael s were approved under an older, less robust standard. Current standards require protection of the MSR and more protections against the type of hack used against Michael’s PEDs.
There are a lot of old PEDs in use. Many are not on the current PCI approved list. Some were approved under the original “Visa PED” standards and their approvals have expired. They should be replaced. Unfortunately, many retailers don’t do replace them until they are forced to because of a compromise (Michaels) or they simply stop working. It’s costly and does not generate new revenue. It’s 100% expense.
It is difficult to prevent a determined attacker. Especially if they have access to counterfeit devices and can acquire sophisticated info and materials.
Awesome! where can i buy one of these LOL?
I want to talk to this vendor, care to share this information?