Police in Slovenia have arrested a 23-year-old man in Maribor believed to be responsible for creating the Mariposa botnet, a collection of hacked PCs that spanned an estimated 12 million computers across the globe, according to reports.
The Associated Press cites FBI officials in Washington, D.C. stating that authorities had arrested “Iserdo,” the nickname used by the hacker alleged to have created Mariposa, a botnet that first surfaced in December 2008 and grew to infect more than half of the Fortune 1,000 companies, as well as at least 40 major banks.
Earlier this year, police in Spain arrested three of Iserdo’s associates, who allegedly used the Mariposa botnet to steal credit card accounts and online banking credentials.
The AP story doesn’t identify Iserdo, saying officials declined to release his name and the exact charges filed against him, but says that the arrest took place about 10 days ago, and that the man has been released on bond.
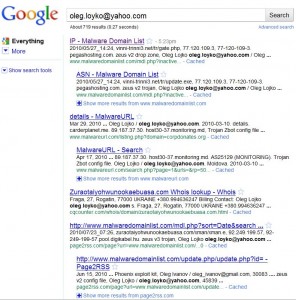
According to information obtained by KrebsOnSecurity.com, Iserdo’s real name is Dejan Janžekovic. Local Slovenian press reports at the time of his arrest said Iserdo was a former student at the Maribor Faculty of Computer and Information Science, but that information could not be independently confirmed.
Individuals close to the case say Janžekovic charged a few hundred dollars for each copy of the bot kit, and that sales frequently were handled by a former classmate who accepted Western Union transfers on his behalf. According to two sources, one of those who helped with the transactions was a 24-year-old woman named Nuša Čoh, pictured here in her high school photo.
Neither Janžekovic nor Čoh could be immediately reached for comment.
Update, July 29, 4:45 p.m: Janzekovic appears only to have been a person of interest in this investigation, according to a law enforcement official I spoke with today. Also, I heard back from Janzekovic himself, who acknowledged having been investigated by the FBI and Slovenian police in connection with Mariposa, and taken in to the police station for questioning. But he said he is not Iserdo, and that the authorities somehow had him mixed up with someone else. From his e-mail to me:
“I am 23 years old (the picture you found is very outdated). I am single, I work as a senior systems administrator for a telco in Slovenia. Fact is that I love technology, I love life (even though the past two weeks it was hell on earth for me), but most of all – I am innocent. Yes, you read right, innocent. I am smarter than this and such things do interest me only from the technological point, as in how to protect against them.
Oh, not to forget, my net nick was and will never be Iserdo.
It is true, that I had the FBI and Slovenian police investigating me but it is also true, that I had nothing to hide. During the investigation I was very cooperative with authorities – I even gave them password for my encrypted partitions. What was the lead to me? It had to be some kind of mix-up and/or identity theft – the only person known to me in this whole story is the girl who I went to school with (as you have already found out).
Neither of authorities did explain to me how they came to conclusion that I was iserdo. I strongly believe the case was identity theft (obviously someone who knew enough about me, to know that I would easily fit in the case) and/or connection through Nusa. And believe me, it was also to my great surprise, when they woke me up at 6 a.m. to search my home on basis of me selling some ‘nasty code’.
But know this – I do not know any technical details about the botnet, program or anything about the criminal backgrounds as I have never seen it or worked with it.”
Continue reading →
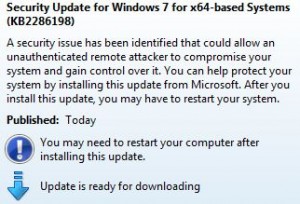 There are a couple of things you should know before installing this update. If you took advantage of the “FixIt” tool that Microsoft shipped last month to blunt the threat from this flaw, you should take a moment now to undo that fix. To do that, visit this link, then click the image below the “Disable Workaround” heading, and follow the prompts. You will need to reboot the system before installing the official fix released today, which is available from Windows Update.
There are a couple of things you should know before installing this update. If you took advantage of the “FixIt” tool that Microsoft shipped last month to blunt the threat from this flaw, you should take a moment now to undo that fix. To do that, visit this link, then click the image below the “Disable Workaround” heading, and follow the prompts. You will need to reboot the system before installing the official fix released today, which is available from Windows Update.