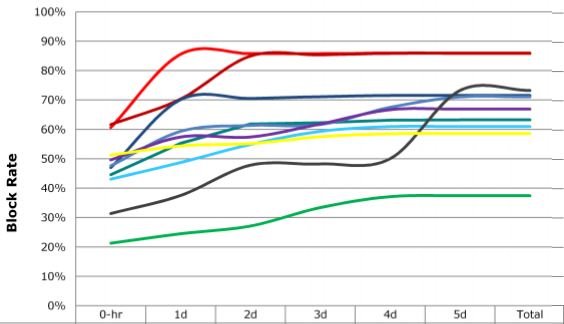
Researchers have discovered a sophisticated new strain of malicious software that piggybacks on USB storage devices and leverages what appears to be a previously unknown security vulnerability in the way Microsoft Windows processes shortcut files.
Update, July 16, 7:49 p.m. ET: Microsoft just released an advisory about this flaw, available here. Microsoft said it stems from a vulnerability in the “Windows shell” (Windows Explorer, e.g.) that is present in every supported version of Windows. The advisory includes steps that can mitigate the threat from this flaw.
Original post:
VirusBlokAda, an anti-virus company based in Belarus, said that on June 17 its specialists found two new malware samples that were capable of infecting a fully-patched Windows 7 system if a user were to view the contents of an infected USB drive with a common file manager such as Windows Explorer.
USB-borne malware is extremely common, and most malware that propagates via USB and other removable drives traditionally has taken advantage of the Windows Autorun or Autoplay feature. But according to VirusBlokAda, this strain of malware leverages a vulnerability in the method Windows uses for handling shortcut files.
Shortcut files — or those ending in the “.lnk” extension — are Windows files that link (hence the “lnk” extension) easy-to-recognize icons to specific executable programs, and are typically placed on the user’s Desktop or Start Menu. Ideally, a shortcut doesn’t do anything until a user clicks on its icon. But VirusBlokAda found that these malicious shortcut files are capable of executing automatically if they are written to a USB drive that is later accessed by Windows Explorer.