Microsoft is warning that hackers have ramped up attacks against an unpatched, critical security hole in computers powered by Windows XP and Server 2003 operating systems. The software giant says it is working on an official patch to fix the flaw, but in the meantime it is urging users to apply an interim workaround to disable the vulnerable component.
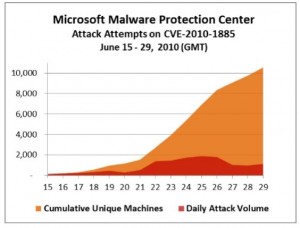 Redmond first warned of limited attacks against the vulnerability in mid-June, not long after a Google researcher disclosed the details of a flaw in the Microsoft Help & Support Center that can be used to remotely compromise affected systems. Last week, Microsoft said the pace of attacks against Windows users had picked up, and that more than 10,000 distinct computers have reported seeing this attack at least one time.
Redmond first warned of limited attacks against the vulnerability in mid-June, not long after a Google researcher disclosed the details of a flaw in the Microsoft Help & Support Center that can be used to remotely compromise affected systems. Last week, Microsoft said the pace of attacks against Windows users had picked up, and that more than 10,000 distinct computers have reported seeing this attack at least one time.
If you run either Windows XP or Server 2003, I’d encourage you to consider running Microsoft’s stopgap “FixIt” tool to disable the vulnerable Help Center component. To do this, click this link, then click the “FixIt” button in the middle of the page under the “enable this fix” heading. Should you need to re-enable the component for any reason, click the other FixIt icon. Users who apply this fix don’t need to undo it before applying the official patch once it becomes available, which at this rate probably will be on Tuesday, July 13.




Thanks as always. You may recall that I sent emails to both Washington Post and NY Times urging them to carry your column. I never received any response. What am I not surprosed?
–John
My assumption has been that it’s better to be free of a third party website, such as The Washington Post and The New York Times. – David
http://n3td3v.blogspot.com/2010/07/message-from-discussion-cyber.html
Andrew
I clicked on the link to download the Fixit routine. It landed on my desktop. I run as a limited user. It won’t install unless I’m an admimistrator. Why can’t Microsoft (or anybody who is updating a program) tell the user what rights and permissions are required BEFORE you download the update?
ALL updates to the system require Admin privileges. Absolutely all. The only updates that don’t require Admin privileges are updates that don’t actually affect the entire OS installation but just one user account.
This vulnerability probably isn’t even exploitable with a decent browser, btw. Opera for example should not process HCP urls so it shouldn’t be vulnerable (unless you’re using the WMP plugin, which you probably shouldn’t be). See here: http://my.opera.com/community/forums/topic.dml?id=610682
As Aurelius so succinctly stated, all Windows Updates and patches should be applied while logged on under the Local Administrator account. Setting Windows Update to download and install patches automatically foregoes the hassle of this log off/log on routine on a monthly basis.
Kudos to you Bob, for running as a Limited User! It may be an inconvenience to have to log off then back on under the Local Administrator account, but this is also inconvenient for malware execution. Most malicious software cannot deliver the intended payload due to lack of authority under the Limited User’s account.
Where ever I can, I set up limited users. If my daughter needs to install something (she’s 34) she still calls dad to help her. I have put the MS Security Essentials on all our computers (desktops, laptop, and netbook) and run limited users all the time.
Knock on wood, no problems yet.
Great points here. I have family whose computers I regularly maintain and I believe that having them use a limited user account has saved me a lot of grief and time.
I’d prefer to see them all using 64bit Windows 7 due to its inherent protections but it’s not going to happen right away so we use the defenses that we have available.
I appreciate and have learned a lot from the informed audience here at krebsonsecurity.com.
Shift-right-click and select RunAs. Now just run it as admin. No need to log out.
The RunAs command is merely a stop-gap solution to, as the name implies, simply RUN an application. ALL installations and updates should be run under the Local Administrator account. RunAs will not give full access to the Registry among other system resources.
What? Runas is a basic functionlity of the OS since the NT days. Windows handles multiple security contexts. Your user account is one and the admin accounts are another. Runas lets you change them. Saying Runas is a stop-gap is like saying su or sudo are stopgaps too.