A call service that catered to bank and identity thieves has been busted up by U.S. and international authorities. The takedown provides a fascinating glimpse into a bustling and relatively crowded niche of fraud services in the criminal hacker underground.
In an indictment unsealed on Monday, New York authorities said two Belarusian nationals suspected of operating a rent-a-fraudster service called Callservice.biz were arrested overseas. Wired.com’s Kim Zetter has the lowdown:
According to the indictment (.pdf), the two entrepreneurs launched the site in Lithuania in June 2007 and filled a much-needed niche in the criminal world — providing English- and German-speaking “stand-ins” to help crooks thwart bank security screening measures.
In order to conduct certain transactions — such as initiating wire transfers, unblocking accounts or changing the contact information on an account — some financial institutions require the legitimate account holder to authorize the transaction by phone.
Thieves could provide the stolen account information and biographical information of the account holder to CallService.biz, along with instructions about what needed to be authorized. The biographical information sometimes included the account holder’s name, address, Social Security number, e-mail address and answers to security questions the financial institution might ask, such as the age of the victim’s father when the victim was born, the nickname of the victim’s oldest sibling or the city where the victim was married.
U.S. authorities have seized the Callservice.biz Web site, which now features the seals for the FBI and Justice Department prominently on its homepage. The feds also seized Cardingworld.cc, a highly-restricted online criminal forum where Callservice.biz was hosted.
If you spend any amount of time on underground forums like Cardingworld.cc, however, you’ll quickly discover that these criminal call centers are among the most popular of fraud services offered. For example, another fraud forum — Verified.su — is home to a number of calling services. Among them are two competing call centers that each began as point-and-click fraud shops that helped customers purchase electronics with stolen credit cards and then split the profits after selling the goods on eBay.
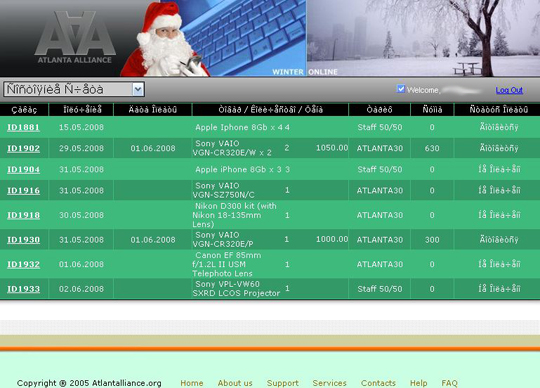
One such service, Atlanta Alliance, used to offer paying members a password-protected Web site where customers could select a range of high-priced gadgets — such as digital cameras, laptops and smart phones — that could be bought with stolen credit cards. The service even allowed customers to manage the shipment of these products to awaiting “reshipping mules,” individuals in the United States recruited for the purpose of receiving stolen goods and reshipping them to Russia, Ukraine and other nations where many vendors refuse to ship due to the high incidence of fraud from those areas.