A network intrusion at the International Committee for the Red Cross (ICRC) in January led to the theft of personal information on more than 500,000 people receiving assistance from the group. KrebsOnSecurity has learned that the email address used by a cybercriminal actor who offered to sell the stolen ICRC data also was used to register multiple domain names the FBI says are tied to a sprawling media influence operation originating from Iran.

On Jan. 19, the ICRC disclosed the compromise of servers hosting the personal information of more than 500,000 people receiving services from the Red Cross and Red Crescent Movement. The ICRC said the hacked servers contained data relating to the organization’s Restoring Family Links services, which works to reconnect people separated by war, violence, migration and other causes.
The same day the ICRC went public with its breach, someone using the nickname “Sheriff” on the English-language cybercrime forum RaidForums advertised the sale of data from the Red Cross and Red Crescent Movement. Sheriff’s sales thread suggests the ICRC was asked to pay a ransom to guarantee the data wouldn’t be leaked or sold online.
“Mr. Mardini, your words have been heard,” Sheriff wrote, posting a link to the Twitter profile of ICRC General Director Robert Mardini and urging forum members to tell him to check his email. “Check your email and send a figure you can pay.”
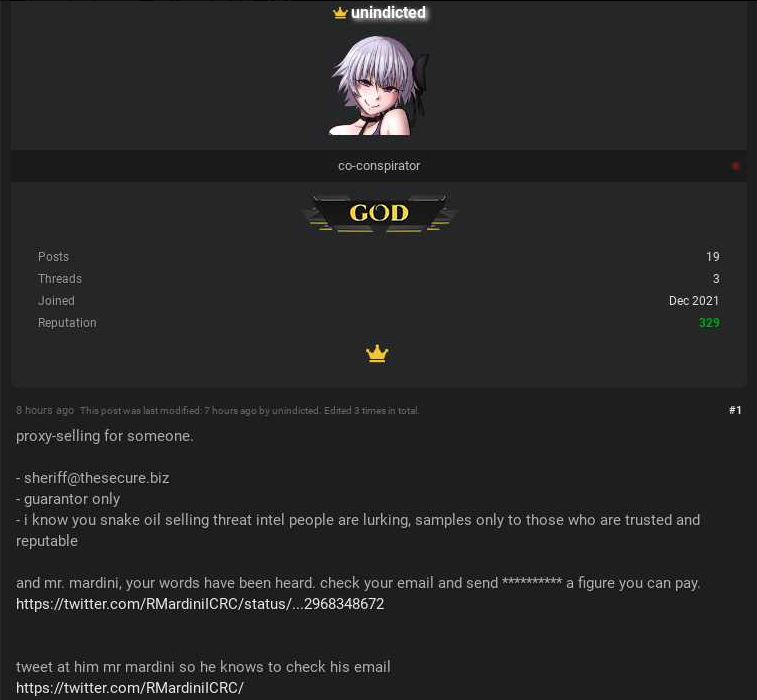
RaidForums member “unindicted” aka Sheriff selling access to the International Red Cross and Red Crescent Movement data. Image: Ke-la.com
In their online statement about the hack (updated on Feb. 7) the ICRC said it had not had any contact with the hackers, and no ransom demand had been made.
“In line with our standing practice to engage with any actor who can facilitate or impede our humanitarian work, we are willing to communicate directly and confidentially with whoever may be responsible for this operation to impress upon them the need to respect our humanitarian action,” the ICRC statement reads.
Asked to comment on Sheriff’s claims, the ICRC issued the following statement:
“Right now, we do not have any conclusive evidence that this information from the data breach has been published or is being traded. Our cybersecurity team has looked into any reported allegation of data being available on the dark web.”
Update, 2:00 p.m., ET: The ICRC just published an update to its FAQ on the breach. The ICRC now says the hackers broke in on Nov. 9, 2021, using an unpatched critical vulnerability (CVE-2021-40539). “This vulnerability allows malicious cyber actors to place web shells and conduct post-exploitation activities such as compromising administrator credentials, conducting lateral movement, and exfiltrating registry hives and Active Directory files. Once inside our network, the hackers were able to deploy offensive security tools which allowed them to disguise themselves as legitimate users or administrators. This in turn allowed them to access the data, despite this data being encrypted.”
Original story:
The email address that Sheriff used to register at RaidForums — kelvinmiddelkoop@hotmail.com — appears in an affidavit for a search warrant filed by the FBI roughly a year ago. That FBI warrant came on the heels of an investigation published by security firm FireEye, which examined an Iranian-based network of inauthentic news sites and social media accounts aimed at the United States., U.K. and other western audiences.
“This operation is leveraging a network of inauthentic news sites and clusters of associated accounts across multiple social media platforms to promote political narratives in line with Iranian interests,” FireEye researchers wrote. “These narratives include anti-Saudi, anti-Israeli, and pro-Palestinian themes, as well as support for specific U.S. policies favorable to Iran.”
The FBI says the domains registered by the email address tied to Sheriff’s RaidForums account were used in service of the Liberty Front Press, a network of phony news sites thought to originate from Iran.
According to the FBI affidavit, the address kelvinmiddelkoop@hotmail.com was used to register at least three different domains for phony news sites, including awdnews[.]com, sachtimes[.]com, and whatsupic[.]com. A reverse WHOIS search on that email address at DomainTools.com (an advertiser on this site) shows it was used to register 17 domains between 2012 and 2021, including moslimyouthmedia[.]com, moslempress[.]com, and realneinovosti[.]net. Continue reading