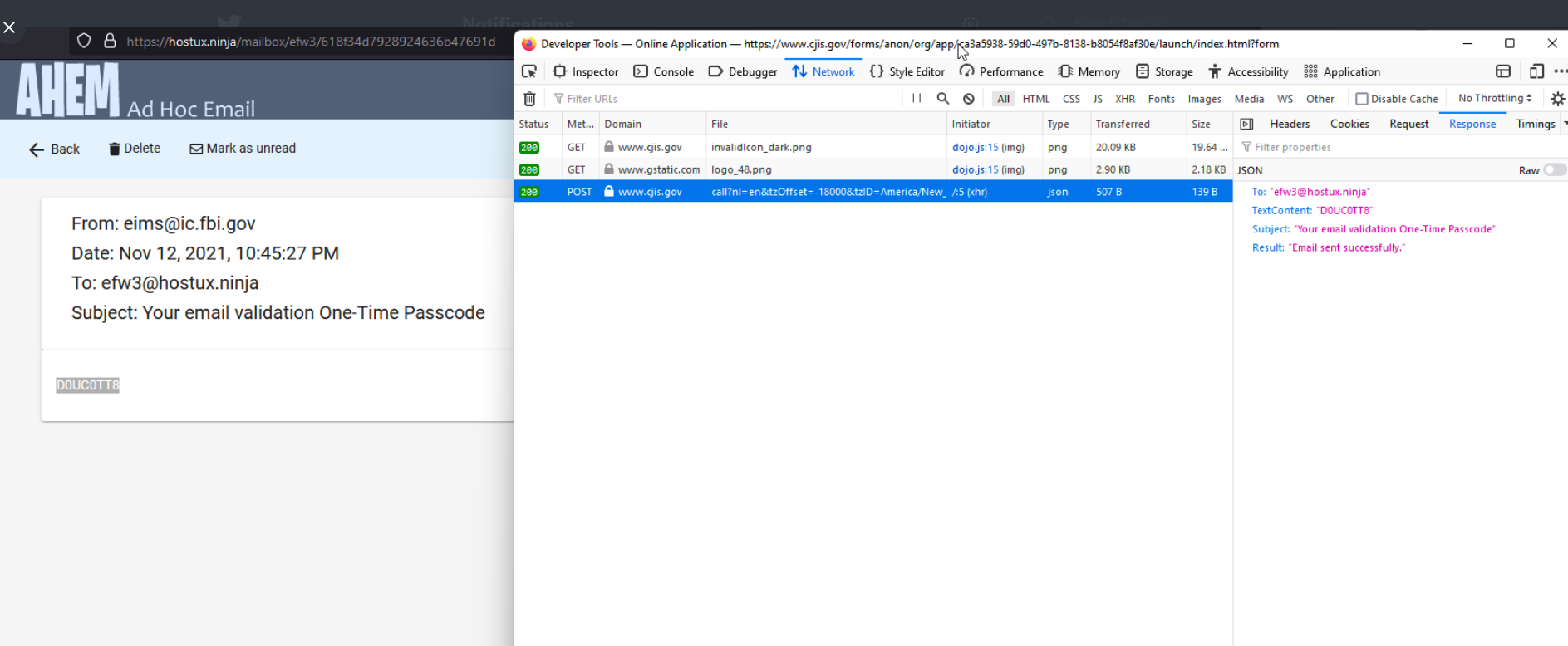
The Federal Bureau of Investigation (FBI) confirmed today that its fbi.gov domain name and Internet address were used to blast out thousands of fake emails about a cybercrime investigation. According to an interview with the person who claimed responsibility for the hoax, the spam messages were sent by abusing insecure code in an FBI online portal designed to share information with state and local law enforcement authorities.
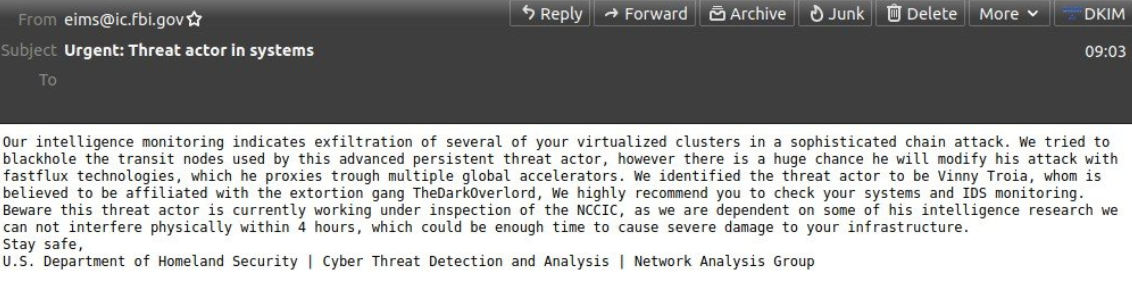
The phony message sent late Thursday evening via the FBI’s email system. Image: Spamhaus.org
Late in the evening on Nov. 12 ET, tens of thousands of emails began flooding out from the FBI address eims@ic.fbi.gov, warning about fake cyberattacks. Around that time, KrebsOnSecurity received a message from the same email address.
“Hi its pompompurin,” read the missive. “Check headers of this email it’s actually coming from FBI server. I am contacting you today because we located a botnet being hosted on your forehead, please take immediate action thanks.”
A review of the email’s message headers indicated it had indeed been sent by the FBI, and from the agency’s own Internet address. The domain in the “from:” portion of the email I received — eims@ic.fbi.gov — corresponds to the FBI’s Criminal Justice Information Services division (CJIS).
According to the Department of Justice, “CJIS manages and operates several national crime information systems used by the public safety community for both criminal and civil purposes. CJIS systems are available to the criminal justice community, including law enforcement, jails, prosecutors, courts, as well as probation and pretrial services.”
In response to a request for comment, the FBI confirmed the unauthorized messages, but declined to offer further information.
“The FBI and CISA [the Cybersecurity and Infrastructure Security Agency] are aware of the incident this morning involving fake emails from an @ic.fbi.gov email account,” reads the FBI statement. “This is an ongoing situation and we are not able to provide any additional information at this time. The impacted hardware was taken offline quickly upon discovery of the issue. We continue to encourage the public to be cautious of unknown senders and urge you to report suspicious activity to www.ic3.gov or www.cisa.gov.”
In an interview with KrebsOnSecurity, Pompompurin said the hack was done to point out a glaring vulnerability in the FBI’s system.
“I could’ve 1000% used this to send more legit looking emails, trick companies into handing over data etc.,” Pompompurin said. “And this would’ve never been found by anyone who would responsibly disclose, due to the notice the feds have on their website.”
Pompompurin says the illicit access to the FBI’s email system began with an exploration of its Law Enforcement Enterprise Portal (LEEP), which the bureau describes as “a gateway providing law enforcement agencies, intelligence groups, and criminal justice entities access to beneficial resources.”
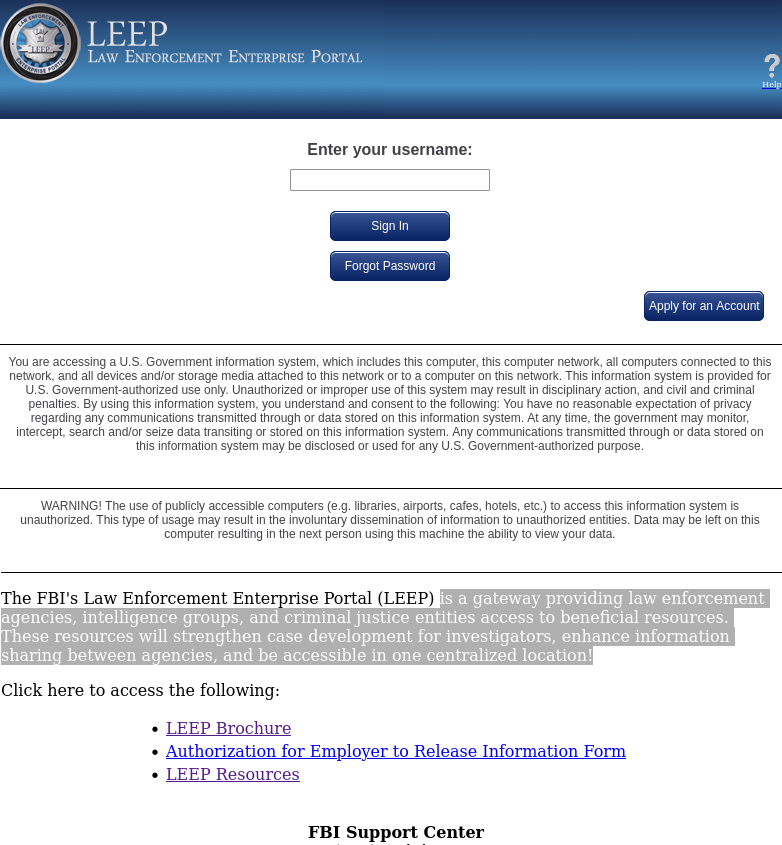
The FBI’s Law Enforcement Enterprise Portal (LEEP).
“These resources will strengthen case development for investigators, enhance information sharing between agencies, and be accessible in one centralized location!,” the FBI’s site enthuses.
Until sometime this morning, the LEEP portal allowed anyone to apply for an account. Helpfully, step-by-step instructions for registering a new account on the LEEP portal also are available from the DOJ’s website. [It should be noted that “Step 1” in those instructions is to visit the site in Microsoft’s Internet Explorer, an outdated web browser that even Microsoft no longer encourages people to use for security reasons.]
Much of that process involves filling out forms with the applicant’s personal and contact information, and that of their organization. A critical step in that process says applicants will receive an email confirmation from eims@ic.fbi.gov with a one-time passcode — ostensibly to validate that the applicant can receive email at the domain in question.
But according to Pompompurin, the FBI’s own website leaked that one-time passcode in the HTML code of the web page.