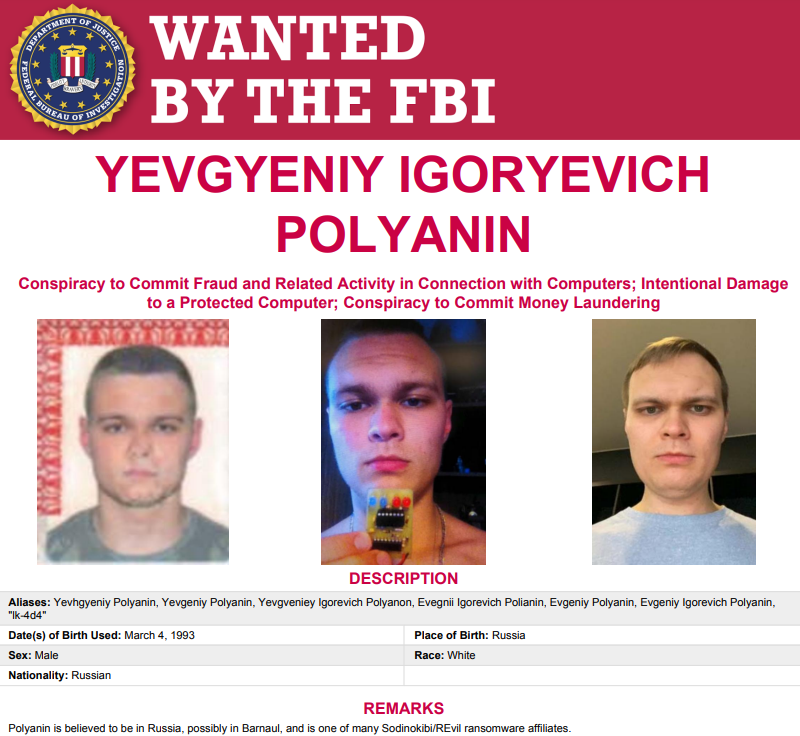
The CEO of a South Carolina technology firm has pleaded guilty to 20 counts of wire fraud in connection with an elaborate network of phony companies set up to obtain more than 735,000 Internet Protocol (IP) addresses from the nonprofit organization that leases the digital real estate to entities in North America.

In 2018, the American Registry for Internet Numbers (ARIN), which oversees IP addresses assigned to entities in the U.S., Canada, and parts of the Caribbean, notified Charleston, S.C. based Micfo LLC that it intended to revoke 735,000 addresses.
ARIN said they wanted the addresses back because the company and its owner — 38-year-old Amir Golestan — had obtained them under false pretenses. A global shortage of IPv4 addresses has massively driven up the price of these resources over the years: At the time of this dispute, a single IP address could fetch between $15 and $25 on the open market.
Micfo responded by suing ARIN to try to stop the IP address seizure. Ultimately, ARIN and Micfo settled the dispute in arbitration, with Micfo returning most of the addresses that it hadn’t already sold.
But the legal tussle caught the attention of South Carolina U.S. Attorney Sherri Lydon, who in May 2019 filed criminal wire fraud charges against Golestan, alleging he’d orchestrated a network of shell companies and fake identities to prevent ARIN from knowing the addresses were all going to the same buyer.
Each of those shell companies involved the production of notarized affidavits in the names of people who didn’t exist. As a result, Lydon was able to charge Golestan with 20 counts of wire fraud — one for each payment made by the phony companies that bought the IP addresses from ARIN.

Amir Golestan, CEO of Micfo.
On Nov. 16, just two days into his trial, Golestan changed his “not guilty” plea, agreeing to plead guilty to all 20 wire fraud charges. KrebsOnSecurity interviewed Golestan about his case at length last year, but he has not responded to requests for comment on his plea change.
By 2013, a number of Micfo’s customers had landed on the radar of Spamhaus, a group that many network operators rely upon to help block junk email. But shortly after Spamhaus began blocking Micfo’s IP address ranges, Micfo shifted gears and began reselling IP addresses mainly to companies marketing “virtual private networking” or VPN services that help customers hide their real IP addresses online.
In a 2020 interview, Golestan told KrebsOnSecurity that Micfo was at one point responsible for brokering roughly 40 percent of the IP addresses used by the world’s largest VPN providers. Throughout that conversation, Golestan maintained his innocence, even as he explained that the creation of the phony companies was necessary to prevent entities like Spamhaus from interfering with his business going forward.
Stephen Ryan, an attorney representing ARIN, said Golestan changed his plea after the court heard from a former Micfo employee and public notary who described being instructed by Golestan to knowingly certify false documents.
“Her testimony made him appear bullying and unsavory,” Ryan said. “Because it turned out he had also sued her to try to prevent her from disclosing the actions he’d directed.”
Golestan’s rather sparse plea agreement (first reported by The Wall Street Journal) does not specify any sort of leniency he might gain from prosecutors for agreeing to end the trial prematurely. But it’s worth noting that a conviction on a single act of wire fraud can result in fines and up to 20 years in prison. Continue reading