Virus writers and botmasters increasingly are turning to new subscription services that test when and whether malicious links have been flagged by Web reputation programs like Google Safe Browsing and McAfee SiteAdvisor.
 Nothing puts a crimp in the traffic to booby-trapped Web sites like being listed on multiple Internet reputation services that collect and publish information on the location of nasty Web sites. People who maintain the bad sites can stay ahead of such services by moving their malware to new domains once the present hosts start showing up on too many blacklists. But constantly checking these lists can be a time-consuming pain.
Nothing puts a crimp in the traffic to booby-trapped Web sites like being listed on multiple Internet reputation services that collect and publish information on the location of nasty Web sites. People who maintain the bad sites can stay ahead of such services by moving their malware to new domains once the present hosts start showing up on too many blacklists. But constantly checking these lists can be a time-consuming pain.
Enter sites like check-crypt.com. For a mere 20 cents, subscribers can check to see whether their malicious sites are flagged by any of 18 different blacklists, including Spamhaus, ZeuSTracker, SpamCop, SmartScreen (anti-malware and anti-phishing technology built into IE7/IE8), Norton Safe Web, Phishtank, Malwaredomainlist and MalwareURL.
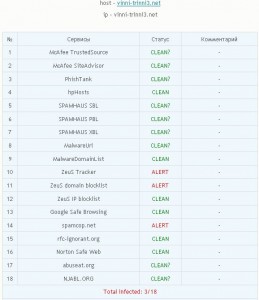
As we can see from the screen shot here, this service acts as a kind of Virustotal for bad domains, listing the percentage of blacklists that detect any submitted malware sites.
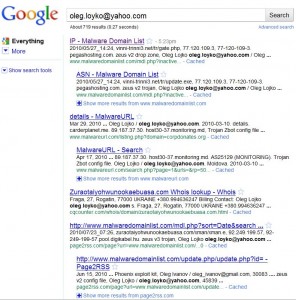 The name and address of the person who registered check-crypt.com is protected by a domain privacy service, but if we dig far enough back in the WHOIS history we see it was registered to someone named Oleg Lojko in Rogatin, Ukraine. A search for the e-mail address attached to that record turns up a domain (vinni-trinni3.net) that a couple of the malware blacklists have flagged for distributing the infamous Zeus Trojan, a powerful password-stealing strain of malicious software.
The name and address of the person who registered check-crypt.com is protected by a domain privacy service, but if we dig far enough back in the WHOIS history we see it was registered to someone named Oleg Lojko in Rogatin, Ukraine. A search for the e-mail address attached to that record turns up a domain (vinni-trinni3.net) that a couple of the malware blacklists have flagged for distributing the infamous Zeus Trojan, a powerful password-stealing strain of malicious software.
I wanted to test this service, and so I thought I’d pick on vinni-trinni, because that site was first flagged by Malwaredomainlist and MalwareURL back in March of this year. The results were underwhelming: As we can see from the above screen shot, this service detects that three out of 18 blacklists have flagged it as malicious, but the author’s own service fails to show listings by either Malwaredomainlist or MalwareURL.




So you mean, the service is not perfect and could be improved?
Hiya Mark — Thanks for dropping by, and I’m glad you’re enjoying the blog. I try to keep it stocked with stuff you can’t find anywhere else 🙂
Yeah, I’m saying this service has room for improvement 🙂
By the way, Brian, I heard about you on the RiskyBiz podcast – you reported about this Belorussian company that found the lnk virus – and I am sure glad I did, I love your blog.
It’s always a cat and mouse game. The bad guys are always testing, looking for any opportunity! 🙁
Even so, blacklisting is very helpful in providing an effective layer against security threats. I’ve been using a blocking hosts file from MVPS (http://www.mvps.org/winhelp2002/hosts.htm) for years with great efficacy. It gets updated at least monthly to keep up with the changing threat landscape. It can also be easily updated yourself on the fly (by adding an entry for a new known bad site). I strongly believe it alone has kept malware from even getting to my systems many a time while browsing the far reaches of the Internet. It’s more effective too because it works for the entire system regardless of what application is used to access the Internet.
While the blocking hosts file has been effective, along with web reputation services such as Google’s safe browsing and IE’s smart screen filter, I believe end user behavior is actually much more important! An example, simply hovering over links before clicking to see where they go (the URL is displayed in the bottom left of the browser), similar for links in e-mail; if it looks questionable, don’t click. Blindly clicking on things is just asking for trouble! 🙁
So basically the author is hiding his malicious sites, and people are handing over there CC# to another possible carding ring.
No exactly.
It appears to me that this is a scheme to get malware purveyors to hand over their *stolen* CC#s.
not sure what you guys are saying. the only way you can pay for this service is via webmoney, and that doesn’t involve exchanging credit cards with this site.
Checking it here:
– http://www.urlvoid.com/
… 2/17 – raises questions about reputation of the site.
Yes it showed up on two sites that likely reported it because it is a service for blackhat crimeware guys. That doesn’t mean that it is serving out iframes or hosting command and controls. The site is legit. I’ve seen email reports it produces before and for it’s purpose it is functional.
And infolookup and faust like Brian said the people pay with wmz..
Interesting but doesn’t this provide spammers with a tool to reverse engineer why they are getting banned? They will just throw up more sites and create more effective spam tools.
You are talking very professionally about a guy that doesn’t seem to be professional at all ! Malwareurl.com has blacklisted our website for 94 days now. We have checked evreything there is and there probably has never been a Trojan horse in the indicated URL. The problem is that these zealots of the MyWot community in Finland catched us and reported the allegations from their friends from malwareurl, they trust each other, you know ? Now there is no way to contact malwareurl. This is not a serious service. The only open door goes to the MyWot church community, where they invite us to pray and meanwhile they steal our identy with their spyware. Great, isn’t it ?