Most of the ATM skimmers I’ve profiled in this blog are comprised of parts designed to mimic and to fit on top of existing cash machine components, such as card acceptance slots or PIN pads. But sometimes, skimmer thieves find success by swapping out ATM parts with compromised look-alikes.
On May 16, 2009, a company representative from ATM maker Diebold was servicing an ATM at a Bank of America branch in Sun Valley, Calif., when he discovered a skimming device and a camera that were attached to the machine. The technician took pictures of the camera and card skimmer (click picture at right for larger image), and then went into the branch to contact his supervisor.
But when the Diebold employee returned, the camera had been removed from the ATM, suggesting that the skimmer scammer was lurking somewhere nearby and had swooped in to salvage his remaining equipment. This is similar to what happened when an ATM technician discovered a compromised ATM a year ago.
Investigators of the present scam learned that the thief had somehow pried off the plastic cover of the ATM’s card acceptance slot and replaced it with an identical, compromised version that included a modified magnetic stripe reader and a flash storage device. The new card slot came with its own clear plastic face that was situated in front of the plastic one that was already attached to the ATM’s internal card reader (see picture below). The entire fraudulent device was glued onto the ATM with silicon.
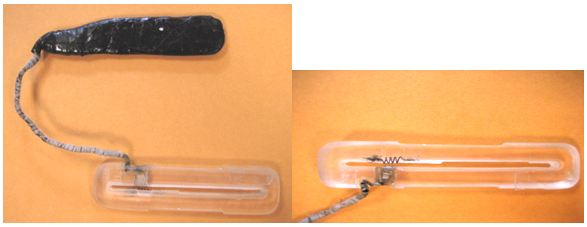
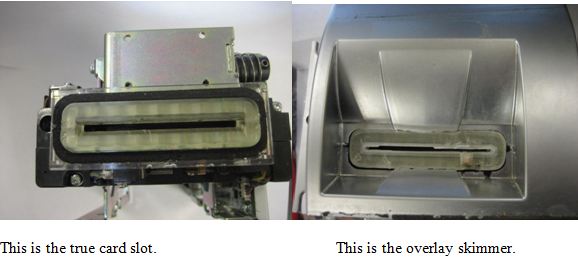 Below are a few close-ups of the silicon-based magnetic stripe reader attached to the compromised card acceptance slot overlay.
Below are a few close-ups of the silicon-based magnetic stripe reader attached to the compromised card acceptance slot overlay.
Here’s a closer look at the electronics inside this handmade reader:
 The camera was in a trim piece that was attached above the PIN pad, cleverly designed to match the rest of the ATM in color and contour. Although the camera was removed by the thief, investigators said the trim piece was similar to a hidden camera found attached to an identical ATM at a Washington Mutual bank branch in the area.
The camera was in a trim piece that was attached above the PIN pad, cleverly designed to match the rest of the ATM in color and contour. Although the camera was removed by the thief, investigators said the trim piece was similar to a hidden camera found attached to an identical ATM at a Washington Mutual bank branch in the area.
In other skimmer cases, ATM thieves also have been known to hack apart and modify portions of the ATM. Last week, the Palm Beach Sun Sentinel published a story about crooks in Boynton Beach, Fla. who have been cutting the bottom of ATM card readers to remove the microchip inside and replace it with their own battery-operated card reader.
 If you visit a cash machine that looks strange, tampered with, or out of place, then try to find another ATM. And remember, the most important security advice is to watch out for your own physical safety while using an ATM: Use only machines in public, well-lit areas, and avoid ATMs in secluded spots. Also, cover the PIN pad with your hand when entering your PIN: That way, if even if the thieves somehow skim your card, there is less chance that they will be able to snag your PIN as well.
If you visit a cash machine that looks strange, tampered with, or out of place, then try to find another ATM. And remember, the most important security advice is to watch out for your own physical safety while using an ATM: Use only machines in public, well-lit areas, and avoid ATMs in secluded spots. Also, cover the PIN pad with your hand when entering your PIN: That way, if even if the thieves somehow skim your card, there is less chance that they will be able to snag your PIN as well.







The moral of this (and similar stories) may be to not withdraw your cash from ATMs. Or maybe only from ones in highly public places, like your local supermarket, where it would be extremely difficult for someone to sneak in to install this equipment, and to retrieve it later.
Me, personally I don’t withdraw much cash from any ATM. There are so many ways to pay people these days, cash is only rarely required. And when it is, like the painter who wants to be paid in cash, I can go direct to my bank for it.
YMMV (Your Mileage May Vary)
Heh. Well, Deborah, I hate to burst your bubble, but the next skimmer series I’m going to post talks about fake point of sale systems swapped in at grocery stores.
Brian, look for Stop n Shop POS machines getting swapped out… it happened…
why be so crude as swap them for compromised ones?
Why not (as happened in Europe last year) have the swap made at the factory and send compromised ones to be installed by the hundreds by official bank technicians?
you also need to watch for the quick second swipe through a seperate machine while shopping as rougue employees have been known to do this here in australia so am sure it would be wide spread.
See:
http://krebsonsecurity.com/2010/06/atm-skimmers-separating-cruft-from-craft/comment-page-1/#comment-6490
http://krebsonsecurity.com/2010/06/atm-skimmers-separating-cruft-from-craft/comment-page-1/#comment-6497
I agree that there are many ways to pay people these days. Unfortunately there are opportunities for crooked activity all over the place.
There’s no place which will accept a traveler’s check any more.
I am in Evansville Indiana. Approx 3/4 of the retail places where I pay by credit card, do NOT ask me to sign the sales slip. I have asked why not? Clerk points to my signature on back of card saying that’s the only signature they need. Well **** if the card was stolen, it would work just as well for them. I asked at my bank about this, was told it is up to the retailer what rules they want to follow.
When you are at grocery, paying by credit card, how much info can someone behind you in same aisle, or another aisle capture with cell phone camera?
My employer sends me to stay at el cheapo motel on a business trip. Yes, they have Internet connection, consisting of a PC in the lobby, with id being hotel name letters acronym, and password “guest.”
I limit my access to extremely limited stuff, change my password after visit there. I am not impressed with what passes for security on the motel PC.
I notice other patrons of the motel have placed all kinds of dangerous stuff in work folders, such as access to their bank accounts. I figure this kind of motel must be a prime target for bad actors.
Hotel key cards are also prone to security glitches, big time. Off-topic for this thread, but I suggest using a chair against door-knob, or other addition to the hotel lock (an oxymoron).
yes, i seems as if these businesses *want* their customers exploited.
what other explanation for these operations by our fine upstanding smartest and brightest entrepreneurial society’s winners?
My local supermarkets ATM got done 3 Fridays in 4 before Christmas.
However, living in chip and pin land, one of my cards has had it’s mag stripe wiped 😉 Skimmers can GFY with that one 😉
Here’s to burst your bubble: when you need cash the ATM is the only place to get it.
Bank offices now refuse to hand out cash, instead directing you to the nearest ATM (usually the one on their outside wall).
Your Mileage May Vary? Have you been using TV Tropes?
It’s a frustrating situation no matter what, who, where or why. Just another reminder to be constantly vigil. As for me personally, ever since I first read of these skimmers, wherever I make a purchase using my debit I find myself looking for this kind of crap. People usually look at me funny as I run my hands over and under any machine that skims my card. But that’s a small price to pay in exchange for my privacy. I read your articles all the time and am a loyal follower. Thank You.
Brian, you can buy them freely at least in EU. Take a look here:
http://www.cardreaderfactory.com/shop/magnetic-stripe-readers.html
Maybe you need a few too, for your households 🙂
I think the moral it is not, not to use anymore these ATMs, the moral is to pressure the financial institutions to sell something secure, and I can come with lots of arguments for this. Of course it is guilty the robber, but also I am guilty if I leave the door opened, and the banks have the door open at this moment.
Well, we’ve come a long way baby from the days when Collins R-390 communications receivers used by the military, actually had resistors replaced by different value resisters in the BFO circuit, where the new resistor of a different value in ohms had ‘freshly painted’ color code stripes for the value of the original resistor.
Why do something like that you may ask? The R-390 was designed to receive primarily CW/AM and teletype communications, but not SSB and in order to copy SSB voice communications clearly, one had to lower the injection signal from the BFO into the mixer circuit and while this made the receiver less sensitive, it prevented the audio output from being distorted.
So what you say. Well it was against military regulations to modify equipment — UGH and so the modification had to be done covertly to prevent its discovery if the unit was inspected, least one be subjected to ‘military justice.’ And while an SSB adapter was available [I believe] as an external unit, the government cost for that ‘adapter’ was a heck of a lot more than changing one single resistor.
Brian, I have read a couple of stories about these fake PoS systems in Germany. Basically, there seems to be a gang of burglars that’s specialized on large DIY chains (“Hornbach”, “Obi”, “Bauhaus”), breaks in and steals nothing – but modifies the GSM-based PoS systems.
they have hit australian macdonalds quite a few times in the past with comprimised eftpos machines. Recently a staff member of a burger king here in australia was arrested – inside job!
“inside job”
punished by grinding,, then “get in my belly!”
Can security cameras capture footage of skimmer “technician” work, compare the pictures with those of authorized ATM employees, then e-mail any mismatches to local security force, to come out and request identification from the suspicious guy?
i thought of that, but the fake tech probably ‘services’ during least busy hours, and probably disguised.
or maybe we haven’t read of successful arrests based on vid .
I hope we don’t have to rely only on those ATMs in the lobby of the bank or credit union. That would pretty much defeat the whole idea.
According to Paul Volcker, and I agree, the ATM was the only worthwhile recent banking innovation.
Why bother making fake ATM parts when you can steal the whole ATM. That’s the way they do it in Romania :))
I am standing in front of the QuikTrip gas pump, shivering in the sub-zero temperature, squinting my eyes against the sleet slashing at my face, ice forming in my hair, as I carefully examine the card slot device before me. Is it protruding from the pump’s face too much? No. Does it look tampered with? No. Is there a suspicious looking trim? No. I swivel my head to the left and the right. Are there any people lurking about, people who turn their heads too quickly when I look their way? No. I slowly insert my bank card (but remove it quickly!). I enter my PIN. Success! I have once again avoided the skimmer scammers. But suddenly there is a shout and Brian jumps out from behind the gas pump. “Did you read my post this morning?” he asks, sort of yelling actually, and I hesitate. “Don’t lie,” he says. “If you had read my post, you would have hidden the PIN key pad with your hand!” I stomp my foot. “Doh!” I say, adding, “you have caught me again, Brian Krebs!” He glares at me for a few moments before running to another gas pump and ducking behind it. I jump in my car, lock the doors, and immediately get on my phone to read Brian’s post. Before driving away, I lower my window and yell, “I read your post, are you happy now?” He doesn’t reply, but as I drive away, I hear a scream, followed by a stern voice: “Did you read my post this morning?”
Thanks, Brian.
The skimmers can and have been installed inside the pump where they’re impossible to detect, so you can never be 100% sure you’ve avoided the skimmer scammers. [I’m still trying to say that real fast five times :)]
One dirty employee is all it takes.
Look, even if you have done all of that, a dedicated attacker can still sniff and capture data over the network the ATM uses.
Even if it is encrypted, it’s still not secure from intelligent analysis,
Thanks for your comment! Made me smile. Dunno if you’ve read CloudLiam’s reply, but he’s spot on: A majority of the pump skimmers are hidden inside of the pump and aren’t overlays. Since the thieves are able to put the skimmer on the part where the data is sent out, they don’t need to hide a camera or have any kind of pad overlay to steal your PIN.
What’s GFY? I’ve googled it and can find only
stuff that in effect tells me to go “lose my virginity”.
I’m sure you all get my drift.
Happy Easter
Peter
“Go F Yourself” is the most likely meaning, although the sentence has to be read as if the author is talking to the skimmer scammer.
Thanks Tony, I should have figured that out.
The grammar of that sentence is a bit awkward
Kind regards,
Peter McLeod in Sydney, Australia
All your gas pumps belong to me!
Minor point, but the glue is silicone, not silicon.
which cures/set rather slowly. odd choice of adhesive…
will tell you all again, the only safe way to have a card and a pin number is to have enough security so that you can hand your card and pin number over to anyone and they can steal NO cash….have been able to do this for years now. So go ahead card skimmers, you cannot withdraw money when the account balance is zero.
account is only of value as decoy, if balance is forever zero.
but maybe the atm operators should monitor activity of honeypot accounts
Do the skimmers read both Tracks on the mag strip? I presume they do, but the banks apparently are taking the position that only the card number was compromised and therefore no “notification” to Government authorities is required.
That’s right, an ATM gets compromised and the public does not know, ever. (well, unless your card was one of the unlucky ones – you’ll certainly know then)
Speaking of gas pumps, I heard a few years ago about how easy it is to access the guts of many pumps and install a hard drive to record all scanned cards. There are two kinds of gas pump keys: one style is fairly generic (the key hole looks like an office cabinet lock) and one is specific to the particular gas station (usually requiring collusion to open the pump for nefarious purposes).
The take-away: avoid the generic lock pumps, if feasible, and if not, only use pumps that are easily visible from the attendant’s booth and therefore less likely to be compromised.
Brian I think you either need to stop writing this series of articles or at least add some data concerning the chances of any reader actually being a victim of these types of crimes to put it into perspective for folks.
Because the facts (as opposed to people’s wild imaginations) indicate that any reader here is 100’s of times more likely to *die* in a car accident everyday than be a victim of ATM related fraud.
Of course as is often the case people are desperate to give themselves a good scare so instead of focusing on the facts – that they have a far higher probability of DEATH let alone the far higher chance of serious, life changing injury doing something that most do everyday – they focus on the picture their own imagination gives them which is always far worse than cold hard reality.
Unfortunately many people are like children and are easily led astray by fearmongers (the media often enough). For example the current “nuclear disaster” in Japan that has killed no people and caused one person only, a worker at the plant, to have cancer risk elevated by a tiny fraction of 1 percent.
In the interests of ethical journalism I think you should provide figure for the probability of the average user here being a victim of this type of fraud. Or else, judging by the comments, people start to behave like children who have a mother who tells them tales of the monster under the bed but insists that the monster is real.
The U.S. Secret Service estimates that annual losses from ATM fraud totaled about $1 billion in 2008, or about $350,000 each day. I’m not aware of more recent statistics in the US on this type of fraud, but I’ve since had conversations with agents working a national task force on skimming and they tell me the incidence of this type of crime is off the charts, particularly at gas pumps.
Sure there are a lot more serious and dangerous things that can happen to people than have their card skimmed. I try to impress on people that most skimmer victims aren’t going to lose any money permanently as a result of the fraud. And people probably are more likely to get physically mugged than become victims of skimmers.
Following in your line of reasoning, I guess my response would be that people aren’t likely to be impacted by the Cosa Nostra on a daily basis either, but that doesn’t mean people don’t find what they do and how they do it interesting.
Plus, I’ve been up front about the fact that I have grown fascinated with these skimmers and the various innovations behind them.
Neej
According to statistics of the USA government
one American in six, at some point in life time, will become a victim of identity theft
By comparison, how many of us will be victims of an auto accident? I have been driving since I was a teenage (at that time in history, it was legal to drive a 2 wheeler with under 5 horsepower … my second one was 4.98 … I do not remember what my first one was) – I am now age 67 … in that time frame about once every 10 years I get into an accident, and for every 1 accident I am in, there are 2-3 incidents leaving dents on my car, where I was not a witness to the incidents.
50 years of driving and 5 accidents with me in the vehicle and maybe a dozen additional incidents when my car got hit and I was not around
lots of near misses, where I had to suddenly swerve, step on brakes, gas, horn, or whatever to avoid an accident
I am still alive – none of the accidents were harmful to me, except my 2 wheeler accident taught me to drive slowly on gravel, wear long sleeved shirt and pants
ID theft does not kill us
The nature of the id theft varies with the individual
I guess it was maybe 15 years ago when I first started receiving notifications that data about me got breached. I guess I get 1 of them on average every 6 months or so, so for me, the exposure is considerably higher than risks on public highway.
We avoid accidents by being aware of the hazards.
I know when I come to a railroad crossing, to stop the car, look both ways, if there is a traffic jam, do not get into position of being stopped on the railroad tracks.
I know that there is a blind spot between my rear view mirror, and side view mirror, which is large enough to hide one and a half car lengths, so before changing lanes, I look into that blind spot to see if anything is there.
Similarly I know when I use my credit card, ATM card, etc. to take certain precautions.
It is not a case of panic, it is prudent behavior, because I know what has happened to other people who have not conducted themselves as cautiously as I.
Even with all my cautious efforts, which include both a hardware firewall and a software firewall (one catch what the other misses) anti-virus and many other protections, I have still managed to get a personal computer infected twice in 40 years of using computers, infections not blocked by my defenses.
However, I believe that if I had not been cautious, the rate of accidents for me would have been much higher. Being cautious requires being informed about the risks.
I’ve been a victim of data theft; presumably the thief only got the card data, because there have been no further inroads to my credit. I keep it monitored. I am also very careful of how and where I use my cards – but with gas pumps being internally compromised, and PoS devices cracked at brick and mortar stores it is difficult to nail the perpetrators. Because the loss is so low, I doubt institutions are going to bother to follow up.
I’m assuming my data came from an online merchant breach, because the criminal bought server space for what I believe to be bot net control at a nefarious server service site. I suppose this information could have come from skimming data sales, but because of the purchase, I imagine it came directly from the criminal. It is not hard to imagine many brick and mortar stores and online merchants both being compromised from network vectors. It may not always be big money, but it is still an easy source of pocket change to keep business going for the big breaches.
So I’m reading the comments here and figured out the only way to be truly safe is to stay home and not make any financial transactions. These read more like a Chicken Little contest. Where I live (Boston) if someone wants to take your money they’ll just mug you – seems more personal and they get to interact with people more often.
ah, like the good old days… crime with a personal touch.
Hi Brian,
Your ATM skimmer posts rock = greatly appreciated. I CAN’T WAIT for the POS series! Though I generally lurk here – your blog is an absolute favorite of mine.
Cheers!
Any chance of one knowing how this fraudsters decoder the sound to get the card details. r there softwares that decode wav files with that much ease for this crooks?
people talking about ingenico bluetooth sniffing RAW,,no physical acces to POS for dumps, can you write about this next post.