Supermarket giant Kroger Co. is the latest major business to disclose that its customer email list has fallen into into the hands of spammers and scam artists.
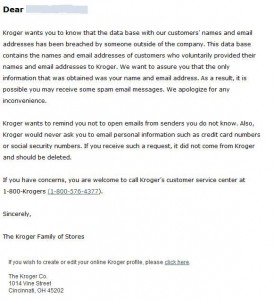 In a communication sent to customers today, Kroger said its database of customer names and email addresses had been breached by someone outside the company. A call to the 1-800 number included in the missive connects to a lengthy recorded message warning customers about an increase in phishing attacks and spam targeting Kroger customers. Kroger’s media relations folks have not yet returned calls seeking comment.
In a communication sent to customers today, Kroger said its database of customer names and email addresses had been breached by someone outside the company. A call to the 1-800 number included in the missive connects to a lengthy recorded message warning customers about an increase in phishing attacks and spam targeting Kroger customers. Kroger’s media relations folks have not yet returned calls seeking comment.
The disclosure comes close on the heels of similar acknowledgments from McDonalds, Walgreens, Honda, deviantART, and most recently TripAdvisor and play.com. They appear to be the lingering fallout from a series of sophisticated, targeted attacks against dozens of email service providers (ESPs) that manage communications between some of the world’s top brands and customers that have opted-in to receive messages from these companies.
In most cases, the spam sent to customers of these companies pushed recipients to buy dodgy services and software. It’s not clear which email service provider may have leaked the Kroger customer information, but it seems that few — if any — ESPs have escaped injury.
 According to the CEO of play.com, that breach involved an attack against marketing firm SilverPop Systems. SilverPop did not respond to requests for comment.
According to the CEO of play.com, that breach involved an attack against marketing firm SilverPop Systems. SilverPop did not respond to requests for comment.
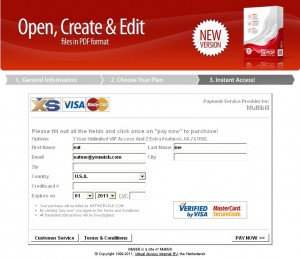
I called SilverPop today because a source forwarded a junk email message to me that appears to have been sent directly from SilverPop’s internal email systems (the text and headers from that email are here). The missive is an offer to download Adobe Reader, and recipients who click the included link are brought to a page that tries to charge them for the free software. This approach is almost identical to the scam emails sent out directly after the successful attacks against email services providers in November of last year.
My initial reporting on this attack against the email service provider industry indicates that most of the providers in the industry had client customer data stolen. I’m left wondering how long we have to keep watching this stream of disclosures trickle out, and how long it might take for email service providers like SilverPop to get their houses in order?
Update, 6:55 p.m. ET: A story in the Cincinnati Business Courier says the breach occurred at Epsilon, an email service provider headquartered in Dallas.
Update, 9:45 p.m. ET: Several readers have reported receiving similar disclosures today from gift store Brookstone.
Update, Apr. 2, 9:35 a.m. ET: Another reader wrote in to say he’d received a notification (PDF) from U.S. bank, which said the financial institution’s customer email list was stolen due to a breach at Epsilon.
Update, Apr. 2, 5:41 p.m. ET: The Epsilon breach extends to JP Morgan Chase, McKinsey Quarterly, and apparel chain New York & Co, according to new disclosures from those companies.
Update, Apr. 2, 8:45 p.m. ET: And the list of disclosures continues: The Home Shopping Network just issued a release (PDF) saying its customer list was compromised via the Epsilon breach.
Update, Apr. 2, 9:00 p.m. ET: Looks like we can add TiVo to the list, although the company’s disclosure doesn’t say which email service provider was responsible.
Update, Apr. 3, 9:11 a.m. ET: According to SecurityWeek.com, the brands impacted by the Epsilon breach include Capital One, City Market, Dillons, Jay C, Food 4 Less, Fred Meyer, Fry’s, King Soopers, Marriott Rewards, QFC, Ralphs, Ritz Carlton, and Smith Brands and Walgreens.




I’m mildly amused how many people who follow this blog had opted into marketing emails and have now ended up getting these alerts. Email communication done properly can be a perfectly acceptable way for a company to communicate with its regular customers, even with customers who normally hate spam with a passion.
But surely some of you folks had used unique email addresses for these subscriptions, so you’ll recognize which spammers will be the first to use the stolen addresses. Please name and shame them when it happens.
How can you pay bills online or bank online w/o an email address?
I didn’t opt into emails, but Chase enabled one of their customers to sign up with my email address a number of years ago. I’ve been trying to get Chase to get rid of all records of my email address from their database since the beginning, but I’ve failed.
So now I have the email from chase informing me that my information has been stolen.
I wonder if now I’ll be able to get them to delete my email address from their system….
I don’t really care about the thieves, it’s the idiots running the bank that bother me….
This comment may very well belong in the “punch drunk” category, but I just don’t hate spammers the way I used to. No, I never open their messages and sure as heck would never buy anything from them, but the constant pitter-patter of spam email does serve its purposes. Like I can close Outlook and reboot anytime, and when I boot up the incoming spam will trigger all my notifications so I can set up my desktop the way I like it, and then forget about it. You know, like you use the junk mail from your snail mail to line garbage cans, etc.
To every thing it’s purpose…
From Target:
Date: April 4, 2011 4:57:49 PM CDT
From: Target.com
To our valued guests,
Target’s email service provider, Epsilon, recently informed us that their data system was exposed to unauthorized entry. As a result, your email address may have been accessed by an unauthorized party. Epsilon took immediate action to close the vulnerability and notified law enforcement.
While no personally identifiable information, such as names and credit card information, was involved, we felt it was important to let you know that your email may have been compromised. Target would never ask for personal or financial information through email.
Consider these tips to help protect your personal information online:
Don’t provide sensitive information through email. Regular email is not a secure method to transmit personal information.
Don’t provide sensitive information outside of a secure website. Legitimate companies will not attempt to collect personal information outside a secure website. If you are concerned, contact the organization represented in the email.
Don’t open emails from senders you don’t know.
We sincerely regret that this incident occurred. Target takes information protection very seriously and will continue to work to ensure that all appropriate measures are taken to protect personal information. Please contact Guest.Relations@target.com should you have any additional questions.
Sincerely,
Bonnie Gross
Vice President, Marketing and Guest Engagement
Dear 1800Flowers.com Customer:
One of our email service providers, Epsilon, has informed us that we
are among a group of companies affected by a data breach that may
have exposed your email address to unauthorized third parties.
It’s important to know that this incident did not
involve other account or personally identifiable information.
We use permission-based email service providers such as Epsilon
to help us manage email communications to our customers.
We take your privacy very seriously and we work diligently to ensure
your private information is always protected. Epsilon has assured
us that no private information, other than your email address,
was involved in the incident. We regret any inconvenience
that this may cause you.
Because of this incident, we advise you to be extremely cautious
before opening emails from senders you do not recognize.
We thank you for your understanding in this matter.
Sincerely,
Bibi Brown
Director, Customer Service
Add another big fish to the catch: Dell.
Dell Australia just emailed me to notify me that my address and name were potentially taken.
An Important Message from Dell Australia
Dell’s global email service provider, Epsilon, recently informed us that their email system was exposed to unauthorised entry. As a result, your email address, and your first name and last name may have been accessed by an unauthorised party. Epsilon took immediate action to close the vulnerability and notify US law enforcement officials.
…
etc etc
Added to that, I have to question why this isn’t getting more coverage in mainstream media.
Looking at all the very large companies who’s customers have been put at risk I’m a little shocked – there’s been _nothing_ in the mass mainstream media about this, certainly not locally (Australia).
Best Buy sent me an email stating their customers’ email addresses are included in the Epsilon hacking. I don’t have the email anymore from Best Buy to show you.
Marks & Spencers in the UK have also issued an advisory:
Your M&S
We have been informed by Epsilon, a company we use to send emails to our customers, that some M&S customer email addresses have been accessed without authorisation.
We would like to reassure you that the only information that may have been accessed is your name and email address. No other personal information, such as your account details, has been accessed or is at risk.
We wanted to bring this to your attention as it is possible that you may receive spam email messages as a result. We apologise for any inconvenience this may cause you. We take your privacy very seriously, and we will continue to work diligently to protect your personal information.
Marks and Spencer plc. Registered office: Waterside House, 35 North Wharf Road, London W2 1NW.
Registered number: 214436 (England and Wales)
Verizon among hacker victims
– http://news.yahoo.com/s/ibd/20110406/bs_ibd_ibd/568362
Apr 6, 2011 6:36 pm – “The largest U.S. mobile carrier was among the companies that had the email addresses of customers exposed in a massive online data breach last week… a hacker penetrated online marketer Epsilon… which controls email databases for 50 companies. Verizon… said only email addresses were exposed.”
.
Delivered-To: timeless@gmail.com
Received: by 10.42.159.133 with SMTP id l5cs26771icx;
Fri, 8 Apr 2011 09:54:26 -0700 (PDT)
Received: by 10.231.113.86 with SMTP id z22mr2379887ibp.93.1302281666170;
Fri, 08 Apr 2011 09:54:26 -0700 (PDT)
Return-Path:
Received: from jpmchase.com (imhvj2.jpmchase.com [159.53.110.149])
by mx.google.com with ESMTPS id he42si8258108ibb.66.2011.04.08.09.54.25
(version=TLSv1/SSLv3 cipher=OTHER);
Fri, 08 Apr 2011 09:54:26 -0700 (PDT)
Received-SPF: pass (google.com: domain of chase.269072909.3788.0@emailnotify.chase.com designates 159.53.110.149 as permitted sender) client-ip=159.53.110.149;
Authentication-Results: mx.google.com; spf=pass (google.com: domain of chase.269072909.3788.0@emailnotify.chase.com designates 159.53.110.149 as permitted sender) smtp.mail=chase.269072909.3788.0@emailnotify.chase.com
Received: from ([169.81.136.158])
by imhvj2.jpmchase.com with ESMTP id 80CHCH1.406160217;
Fri, 08 Apr 2011 12:46:16 -0400
From: “Chase”
Reply-To: Chase.269072909.3788.0@emailnotify.chase.com
To: TIMELESS@GMAIL.COM
Subject: Please read important message about your e-mail address
Date: Fri, 8 Apr 2011 12:54:21 -0400
Message-ID:
X-Mailer: Kana Connect 10
Mime-Version: 1.0
Content-Type: multipart/alternative; boundary=”1302281662084.MimeBoundarY”
Notice: This is a multi-part message in MIME format. If you are reading this text, you may want to consider changing to a mail reader that support MIME multipart messages. Or let us know by replying to this message and putting “Change to text” in the subject of the message.
–1302281662084.MimeBoundarY
Content-Type: text/plain; charset=”ISO-8859-1″
Note: This is a service message with information related to your
e-mail address.
=====================================================================
Chase is letting our customers know that we have been informed by
Epsilon, a vendor we use to send e-mails, that an unauthorized person
outside Epsilon accessed files that included e-mail addresses of some
Chase customers. We have a team at Epsilon investigating and we are
confident that the information that was retrieved included some Chase
customer e-mail addresses, but did not include any customer account or
financial information. Based on everything we know, your accounts and
confidential information remain secure. As always, we are advising
our customers of everything we know as we know it, and will keep you
informed on what impact, if any, this will have on you.
We apologize if this causes you any inconvenience. We want to remind
you that Chase will never ask for your personal information or login
credentials in an e-mail. As always, be cautious if you receive e-mails
asking for your personal information and be on the lookout for unwanted
spam. It is not Chase’s practice to request personal information by
e-mail.
As a reminder, we recommend that you:
————————————-
– Don’t give your Chase Online(SM) User ID or password in e-mail.
– Don’t respond to e-mails that require you to enter personal
information directly into the e-mail.
– Don’t respond to e-mails threatening to close your account if you do
not take the immediate action of providing personal information.
– Don’t reply to e-mails asking you to send personal information.
– Don’t use your e-mail address as a login ID or password.
The security of your information is a critical priority to us and we
strive to handle it carefully at all times. Please visit our Security
Center at chase.com and click on “Fraud Information” under the “How to
Report Fraud.”
http://notifications1.chase.com/269072909.3788.0.782
It provides additional information on exercising caution
when reading e-mails that appear to be sent by us.
Sincerely,
Patricia O. Baker
Senior Vice President
Chase Executive Office
=====================================================================
If you want to contact Chase, please do not reply to this message,
but instead go to Chase Online. For faster service, please enroll or
log in to your account. Replies to this message will not be read or
responded to.
Your personal information is protected by advanced technology. For
more detailed security information, view our Online Privacy Notice:
http://notifications1.chase.com/269072909.3788.0.563
To request in writing: Chase Privacy Operations, P.O. Box 659752,
San Antonio, TX 78265-9752.
JPMorgan Chase Bank, N.A. Member FDIC
(C) 2011 JPMorgan Chase & Co.
LCEPAEM0311
This e-mail was sent to: TIMELESS@GMAIL.COM
–1302281662084.MimeBoundarY
Content-Type: text/html; charset=”ISO-8859-1″
Content-transfer-encoding: quoted-printable
161229.rfs
=20
Note=
:
This is a service message with information related to your e-mail address.
Chase is letti=
ng our customers know that we have been informed by Epsilon, a vendor we us=
e to send
e-mails, that an unauthorized person outside Epsilo=
n accessed files that included
e-mail addresses of some Chase customers. We have =
a team at Epsilon investigating and we are confident that the information t=
hat was retrieved included some Chase customer
e-mail addresses, but did not include any cu=
stomer account or financial information. Based on everything we know, your=
accounts and confidential information remain secure. As always, we are ad=
vising our customers of everything we know as we know it, and will keep you=
informed on what impact, if any, this will have on you.
We apologize if this causes you any inconvenience. =
We want to remind you that Chase will never ask for your personal informat=
ion or login credentials in an
e-mail. As always, be cautious if you receive e-ma=
ils asking for your personal information and be on the lookout for unwanted=
spam. It is
not Chase’s practice to request personal inf=
ormation by
e-mail.
As a reminder, we recommend that you:=
Don’t give =
your Chase OnlineSM User ID or password in
e-mail.
Don’t respo=
nd to
e-mails that require you to enter personal inform=
ation directly into the
e-mail.
Don’t respo=
nd to
e-mails threatening to close your account if you =
do not take the immediate action of providing personal information.
Don’t reply=
to
e-mails asking you to send personal information. =
Don’t use y=
our
e-mail address as a login ID or password. =
The security o=
f your information is a critical priority to us and we strive to handle it =
carefully at all times. Please visit our Security Center at
chase.com an=
d click on "Fraud Information" under
the "How to Report Fraud." It provides ad=
ditional
information on exercising caution when reading e-ma=
ils
that appear to be sent by us.
Sincerely,
Patricia O. Baker
Senior Vice President
Chase Executive Office
If you want to =
contact Chase, please do not reply to this message, but instead go to Chase=
Online. For faster service, please enroll or log in to your account. Repli=
es to this message will not be read or responded to.
Your personal information is protected by advanced technology. For =
more
detailed security information, view our
Online Privacy Notice. To request in writing: Ch=
ase Privacy
Operations, P.O. Box 659752, San Antonio, TX 78265-9752.
JPMorgan
Chase Bank, N.A. Member FDIC
=A9 2011 JPMorgan Chase & Co.
LCEPAEM0311
This e-mail was sent to: TIMELESS@GMAIL.COM
–1302281662084.MimeBoundarY–