Some of the recent scams that used bogus security alerts in a bid to frighten Mac users into purchasing worthless security software appear to have been the brainchild of ChronoPay, Russia’s largest online payment processor and something of a pioneer in the rogue anti-virus business.
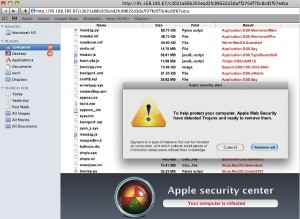 Since the beginning of May, security firms have been warning Apple users to be aware of new scareware threats like MacDefender and Mac Security. The attacks began on May 2, spreading through poisoned Google Image Search results. Initially, these attacks required users to provide their passwords to install the rogue programs, but recent variants do not, according to Mac security vendor Intego.
Since the beginning of May, security firms have been warning Apple users to be aware of new scareware threats like MacDefender and Mac Security. The attacks began on May 2, spreading through poisoned Google Image Search results. Initially, these attacks required users to provide their passwords to install the rogue programs, but recent variants do not, according to Mac security vendor Intego.
A few days after the first attacks surfaced, experienced Mac users on Apple support forums began reporting that new strains of the Mac malware were directing users to pay for the software via a domain called mac-defence.com. Others spotted fake Mac security software coming from macbookprotection.com. When I first took a look at the registration records for those domains, I was unsurprised to find the distinct fingerprint of ChronoPay, a Russian payment processor that I have written about time and again as the source of bogus security software.
The WHOIS information for both domains includes the contact address of fc@mail-eye.com. Last year, ChronoPay suffered a security breach in which tens of thousands of internal documents and emails were leaked. Those documents show that ChronoPay owns the mail-eye.com domain and pays for the virtual servers in Germany that run it. The records also indicate that the fc@mail-eye.com address belongs to ChronoPay’s financial controller Alexandra Volkova.
The leaked documents also have given ChronoPay’s enemies access to certain online records that the company maintains, such as domain registration accounts tied to the firm. Both mac-defence.com and macbookprotection.com were suspended by the registrar — a company in the Czech Republic called Webpoint.name. But a screen shot shared with KrebsOnSecurity.com shows that someone recently used that fc@mail-eye.com account to register two more Mac security-related domains that haven’t yet shown up in rogue anti-virus attacks against Mac users: appledefence.com and appleprodefence.com.
Perhaps Apple will have better luck than others who have tried convincing ChronoPay to quit the rogue anti-virus business, but I’m not holding my breath. As I noted in a story earlier this year, ChronoPay has been an unabashed “leader” in the scareware industry for quite some time. In 2008, it was the core processor for trafficconverter.biz, the rogue anti-virus affiliate program that was designed to be the beneficiary of the first strain of the Conficker worm, a menacing contagion that still infects millions of PCs worldwide. Last March, the company was at the forefront of another emerging scam, when it began processing payments for icpp-online.com, a scam site that targeted filesharing users and stole victims’ money by bullying them into paying a “pre-trial settlement” to cover a “Copyright holder fine.”
Update, May 29: ChronoPay responded by publishing a statement denying any involvement in the MacDefender attacks.
Original post:
Apple has issued an official support note telling users how to avoid or remove Mac Defender malware. ZDNet also got hold an unofficial document that Apple apparently is distributing to its customer support personnel in charge of fielding complaints about the attacks. I should point out that all of the rules from my recent blog post Krebs’s 3 Basic Rules for Online Safety apply just as well to Mac users as they do to Windows folks. But #1 is the most important, and keeps Mac users out of trouble here: “If you didn’t go looking for it, don’t install it!”





Just last week i cleaned a pc with this type of scareware ie fake antivirus from a freshly installed windows7. My believe is that if you can not tell the difference from these type of software and the real deal the scammers will earn a lot of money. Take in consideration of what people run these systems mostly for its ease of use… (well mac anyway)its might also be really easy to trust the software. And as the userbase of osx also is growing the threats will also grow.
I agree with your statement that threats will continue to grow as the Mac community grows. Several years ago I had several friends who were Mac fans and they always used to get me to watch the PC vs Mac commercials (or whatever they were called). You know, the one where the PC guy is sick and the Mac guy is fine.
My response to them was that any platform can be targeted with malware, and the only reason Macs hadn’t been targeted yet was because the user base wasn’t large enough to make it worth the bad guys’ time.
Apparently now someone has decided the user base was large enough to give it a try, and by all accounts they’re making a lot of money. The cat’s out of the bag now.
For the record, I’m not anti-Mac now and I’ve never been anti-Mac in the past. I just always found the idea that Macs couldn’t get infected with malware a bit silly. Any system can be infected with malware, especially if the attack vector is the user.
inetnum: 95.168.185.0 – 95.168.185.255
netname: GIBIBITS-LTD-966647
descr: Gibibits-Limited
country: HK
admin-c: KB1643-RIPE
tech-c: SR614-RIPE
status: ASSIGNED PA
mnt-by: NETDIRECT-MNT
mnt-lower: NETDIRECT-MNT
mnt-routes: NETDIRECT-MNT
source: RIPE # Filtered
person: Konstantin Begidzhanov
address: FLAT/RM 813 8/F Hollywood Plaza
address: 610 NATHAN RD, KL
address: Hong Kong
phone: +852 36931522
fax-no: +852 36931522
abuse-mailbox: support@gibibits.com
nic-hdl: KB1643-RIPE
mnt-by: NETDIRECT-MNT
source: RIPE # Filtered
Hello Brian, gibibits.com this not a bulk hosting for this illegal sites?
I believe Apple has been most irresponsible in the way it markets it’s product as well as how they train their front line retail sales personnel.
They seem to be pushing the idea onto consumers, who don’t know better, that Apple products cannot get attacked due to being superior in some way and in fact have no malware.
This not only leads their consumers to trust scareware dialogs such as this more easily but also leads them to believe that they cannot be attacked and thus not check their systems for evidence of malware.
I have no argument with the line that Apple has far, far less attacks than Windows however to insist that they are invincible during sales pitches is downright disingenuous (unfortunately not an uncommon thing across the entire sector of retail computer sales).
The computers weren’t attacked, since that’s technically impossible, it was the USERS who were attacked through social engineering, and nearly all of them were former Windows users. Every Mac User knows you can’t get viruses on OSX, the UNIX framework simply doesn’t allow it. So anyone who got duped isn’t a Mac User.
Apple will now go ahead and put these criminals in jail, the Mac Community does not allow this type of activity.
Spoken like a true Mac zealot. If they got taken in by this scam, they’re excommunicated from the Mac user base! Take away their Mac cards!
You should take note that while Apple calls this “malware” in their advisory (contrary to your comment I don’t use the word ‘virus’) I am careful to call this scareware.
If you just say it’s third party software and you want to remove it, Apple support usually will help you. 😀
> that’s technically impossible
> Every Mac User knows you can’t get viruses on OSX, the UNIX framework simply doesn’t allow it
Yeah, yeah, yeah. Ask Apple why do they ever bother to regularly issue patches for dozens of critical vulnerabilities.
> it was the USERS who were attacked
FYI almost all Windows-malware are trojans that attack users, not OS. So what is your point exactly?
Also spoken like someone who knows nothing about the “UNIX framework”.
Great report, Brian, and I say this after having read all the ZDNet reports, as well as reports from other sources on this. A much better report than ZDNet’s which is so caught up in the mac vs pc silliness they seemed almost gleefull that macs were being targeted. Their reports bordered on scareware. You gave much better information.
Intego, which is doing a great job discovering these scareware products, already protects against at least the initial variants of this scareware with its product VirusBarrier X6.
But, as you noted, your rule #1 applies very well here as it is not mac software vulnerability that is taken advantage of, rather it is the user vulnerability, buying something they didn’t go looking for in the first place.
Just a note for those who may not be aware of this: VirusTotal only checks Windows security products. It does not include VirusBarrier in it’s list of virus detection software, even though VirusBarrier detects both windows and mac viruses.
Browsing the IP neighbourhood we see:
mstoolkit.com
mac-defence.com
mstoolonline.com
macbooksecurity.com
macbookprotector.com
macbookprotection.com
macbookprotector.com
Brian, you write that “Initially, these attacks required users to provide their passwords to install the rogue programs, but recent variants do not, according to Mac security vendor Intego.”
About those ‘recent variants’, do I understand that the user would still have to take some action, like clicking ‘yes’ somewhere, to get this malware installed?
Yes, installing software on OS X generally requires three clicks at a minimum.
as I understand it, the download is now set to install into areas that only need standard privileges so that a password isn’t needed. But it does look like you have to “register” it or something after it downloads… here’s a article about it from Sophos (they also offer a free mac anti-virus for home users which helps detect these):
http://nakedsecurity.sophos.com/2011/05/26/apple-malware-evolved-no-password-required/
Thanks to both of you. I suppose it would be best to close the browser as soon as possible during their install process.
Best bet – Close it / turn off safe file opening in safari pref’s.
The biggest issue people have been having with removing it is that they forget that when the APPLICATION IS RUNNING, it is a process (which can be found in Activity Monitor.) – Just got to end that first. :]
The brainchild or they’ve been used?
Remember that ChronoPay was hacked last December 2010. My point is, maybe the online processing company was hacked and the attackers made it look like it was ChronoPay that spread the Mac scareware.
The Mac scareware incident is a syndicated attack. The one or the group behind this is obviously financially-backed by someone with interest against Mac.
Mac computers have been the focused of many hackers these couple of months. It’s a sure sign that something big is going to happen next. I just hope that Apple is doing something about this.
It does seem really dumb to leave such an obvious trail. Maybe the point was not gain but fame.
MacDefender is now news so money or not, the author must be very pleased.
By all accounts, it does appear to indicate an increasing threat against the Mac OS X platform. I’d say this was a big test to see how many systems they could compromise. Keep in mind the payload here was not all that malicious. But, what about next time? 🙁
http://blogs.mcafee.com/mcafee-labs/mac-malware-monsoon-in-may
As is becoming increasing apparent regardless of OS platform, the user is being exploited. SANS has a good write up of this today:
http://isc.sans.edu/diary/Managing+CVE-0/10933
Let’s go ahead and have them arrested, we don’t need this type of behavior within the Mac community.
We don’t need it in any community – not just the Mac one. But lets face it – odds are the criminals will try to get it anyway they can… regardless of what type it is…
There needs to be more action taken against this type of illigal activity… however, even that won’t stop people from trying – it will hopefully just make it a smaller pool.
True enough, but in the Mac Community this activity is simply not tolerated, so arresting them is the only proper solution.
We’ll find them, crush them, we are the most savvy computer users on earth. We built this industry, we built the www, so nothing will be resolved until these criminals are in jail for 15+ years.
It’s just how the Mac Community operates. You’ll see!
That doc isn’t close to being legit.
I have seen the real documents that Apple release, I was working as CPU Tier 1 Tech support for them, Of course I cannot tell you what it said, but in the beginning it revolved around telling the cx to go and get help else where because we can’t help remove malware (most guys removed it anyways.
Dogg – Apple does give guidance on how to avoid or remove Mac Defender:
http://support.apple.com/kb/HT4650
I know, they also had internal documents at first when the main call driver was Mac Defender – atleast 20% of the calls I got per day was because of this.
They told us we do not remove malware, when I was leaving I think that changed, we can now remove it.
Brian,
Great reporting man! You have leaped beyond investigative reporting and are predicting the criminals’ future moves! Thumbs Up!!
Scareware frightens the user into installing it voluntarily. It’s unimportant which operating system the computer is running. If the OS allows you to install a desirable program, then it will allow you to install a malicious one.
Yes, many Mac users are technically sophisticated. But many others are not. Many bought Macs in hopes of staying safe despite having no computer training, or they may even have been advised to get a Mac by friends and relatives who feared the worse if they were let loose on the internet with a Windows machine. Many users are elementary school children and their teachers, since Mac is strong in educational software. It isn’t necessary for the perpetrators to be able to infect every Mac for this scheme to be profitable.
Nicely said, Alpha.
What a pity we can’t send the Seal team over and rid the world of some more useless scumbags.
The entire world would rejoice at the execution of these losers.
I just had today email on yahoo account. Email was not stored as scam.
After i opened email mac defender picture came up and downloaded automatically
zip file into download files. I immediately deleted files and email.
So now i’m hopping that my MacBook is not infected. I did not install nothing.
@Sihmet – I heard from another reader yesterday who had the same thing happen to her via a Yahoo email. Same exact experience: She said the file downloaded automatically onto her Mac.
Sounds like this was through webmail (access via web browser)? This is why I really hate webmail and instead prefer to use an e-mail client set to read all mail as plain text, which disables any active content by default and neuters this type of thing before it has any chance of executing its payload. 🙂
hmm, yahoo usually diverts bulk scams into the spamfolder.
Brian, why not take all the information with the police and Visa/MC? You can do it in the US so not to depend on Russian police. Chronopay’s payment processing is totally dependent on payment systems. Moreover their legitimate payment business far exceeds this stuff. So take away their merchant IDs and Chronopay will really really suffer.
Ahhh… And one more obvious thought if you want an all out war and if you manage to open an official investigation. Since you have IBANs police can request all transactions for them. Judging by the ease of communications and transaction volumes there’s a good chance the guys didn’t put too many protective layers. Cyprus banks will comply and the investigation can start backtracking. Like what corporate entity paid the Cyprus lawyers for opening new fronts. Where does it get its own money in return and how does it use them? Bet the story can get much more exciting 🙂
You gotta love all the sites that are reporting on Brian’s findings without any attribution whatsoever. A perfect example is this TopTenReviews post: http://www.toptechreviews.net/apple/chronopay-executive-tied-to-mac-defender-malware/
I did post a comment that’s currently awaiting moderation which points out the fact that the writer, Mike Vang, didn’t provide a citation or an acknowledgement of Brian’s work. Here’s a screen shot of the original if it just happens to change: http://db.tt/K9vtAyr
Oops! That should read TopTechReviews.
Whoever wrote that article is a moron. His information on Mac Defender isn’t even correct. I left a comment too…we’ll see if it gets out of moderation.
He seems to be a serial offender. One would not write an article like this one:
http://www.toptechreviews.net/apple/chinese-workers-treated-inhumanely-by-apple/
without pretty serious evidence to back it up. But he is completely vague about his sources, making it difficult to know if he plagiarized.
It doesn’t appear to be just Mike Vang. Out of curiosity I clicked on several posts over at that site, and apparently their authors are supernaturally inclined toward just knowing things.
Most computer security bloggers seldom have an original thought in their heads. They’re able to bask in the spotlight simply by cataloging and linking to the work of others.
Brian Krebs stands out in the crowd because he actually gets down and does it, so he’s a popular guy for self-proclaimed “security experts” to quote … and in some instances, plagiarize.
Most computer security bloggers are egotistical posers who have NEVER had an original thought in their heads! Brian is one of the few exceptions.
The fact that all those self appointed security gurus attract armies of fawning sycophants who hang off their every word is sad testament to the dumbing down of the computer user base.
Daily compilations of quotes and links doth NOT a guru make!
And MY AXE!
and MY AXE!!
opening another front in the ‘war of words’?
Apple Macs are based on BSD – appaears weak
security.
But BSD appeas to have STRONG security.
But may it depends upon the intelligence of the
system administrator?
Scaring for ‘over-reaction’ and Normal Corporate
Advisories – ‘under-reaction’ tend to confuse
the REAL situation.
Physical analogy: food quality in general
appears to have declined compared to 100 or 1000
years ago.
At least today, we have China’s Melamine Scandal. Melamine fools the protein tests and
slowly poisons children/etc. Melamine was not
known in 1000 years ago.
It looks like I am the first to write here after I have installed and also payed the amount. 99 dollars! First I was upset but after that I realized that I have no chance to take my money back and I started to mock at myself! At least, after I payed the amount no other pop-up showed and no more virus warnings!:) I’m wondering if the hacker has the common-sense to remove the virus after he receive the money :)))
Anyway, my MAC OS X is 10.5.8 and I need at least 10.6 in order to download and install the Mac malware remover software. I would appreciate your suggestion is order to remove the malware.
I don’t hesitate in lodging a complaint against the hacker. But I’m not very good in tracking my money in order to determinate the state I have to address.
Here are the payment details:
Voucher: 2011060757005453 / Tranzactie
comerciant – Tranz: Nr card
421144XXXXXX5160, Ref 006883530529, Suma
platita 99.9 USD, Suma in valuta contului 68.78
EUR, Suma decontata 68.78 EUR Rata de
schimb 1EUR=1 EUR. Comision: 1.38 EUR.
Locatie: 17200230 AZ
SATISFACTORYSOFT.COM BAKU. Data_Ora:
05-06-2011 15:55:28
-68,78 EUR
I don’t even have a mac but they got into my bank account for $99.90 on 6/25. It just showed up today. I hope my bank can help me because I didn’t order anything. It gives a time for transaction while I was at work. Damn Russians!!!! We should have nuked them too!!!!