An agency of the European Union created to improve network and data security is offering some blunt, timely and refreshing advice for financial institutions as they try to secure the online banking channel: “Assume all PCs are infected.”
The unusually frank perspective comes from the European Network and Information Security Agency, in response to a recent “High Roller” report (PDF) by McAfee and Guardian Analytics on sophisticated, automated malicious software strains that are increasingly targeting high-balance bank accounts. The report detailed how thieves using custom versions of the ZeuS and SpyEye Trojans have built automated, cloud-based systems capable of defeating multiple layers of security, including hardware tokens, one-time transaction codes, even smartcard readers. These malware variants can be set up to automatically initiate transfers to vetted money mule or prepaid accounts, just as soon as the victim logs in to his account.
“Many online banking systems….work based on the assumption that the customer’s PC is not infected,” ENISA wrote in an advisory issued on Thursday. “Given the current state of PC security, this assumption is dangerous. Banks should instead assume that PCs are infected, and still take steps to protect customers from fraudulent transactions.”
ENISA cited as an example the heavy reliance on passwords + basic two-factor authentication — such as tokens. Check the Target: Small Businesses category for a number of stories in which thieves bypassed these schemes.
“A basic two factor authentication does not prevent man-in-the-middle or man-in-the-browser attacks on transactions,” the alert stated. “Therefore, it is important to cross-check with the user the value and destination of certain transactions, via a trusted channel, on a trusted device (e.g., an SMS, a telephone call, a standalone smartcard reader with screen). Even smartphones could be used here, provided smartphone security holds up.”
ENISA further admonishes banks not to take smartphone security for granted, and that additional security measures will be needed to shore up security in the mobile space (for example, in a veiled reference to Google’s Android platform, they call for more “vetted appstores”).
No doubt security is a constantly moving target; it is necessarily reactive and therefore lags behind new methods adopted by cybercriminals. But from my perspective, the advisory highlights a fundamental reality gap between threat perception and security practice in the banking sector today.
My experience on this matter is limited mostly to the situation in the United States, where many financial institutions seem to pay lip service to security. Many simply urge customers to follow security advice that is increasingly quaint and irrelevant: Use firewall and antivirus software; don’t respond to phishing emails; pick complex passwords and change your password often.
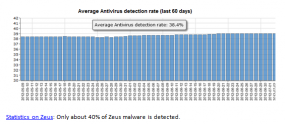
What is almost never mentioned is that all of these security procedures amount to nothing if the customer’s system is already compromised by a powerful banking Trojan like ZeuS or SpyEye. ENISA’s advisory is accompanied by a graphic showing that only about 38 percent of ZeuS malware is detected by antivirus software; that data, taken from ZeuSTracker, is slightly higher than the average I found in a similar analysis over nearly the exact same time period as the ZueSTracker sample. As I told a reader recently, I’m not saying antivirus software is completely useless, just that users should behave as though it is.
Perhaps some banks here in the U.S. already operate under the assumption that all customer PCs are compromised. But if so, I have yet to see a financial institution willing to communicate that to their customers. Larger financial institutions realize huge cost savings from having customers bank online, and are wary of doing anything to spook customers away from this medium. Smaller institutions may not realize such savings, but offer ebanking because their customers have come to expect it.
In any case, ENISA’s advisory resonated with me because I have long urged online banking customers to assume that their PCs are compromised, and to use a Live CD approach when banking online. This is more of a “must” for small businesses banking online, since — unlike consumers, who enjoy legal protection from financial losses due to cybercrime — U.S. companies of all sizes have no such guarantee when cyberheists strike.
It is true that many U.S. banks are starting to adopt promising technologies and approaches that seek to more accurately identify activity that typically precedes a cyberheist. Other banks are turning to solutions that try to create more trusted and exclusive modes of communication between financial institutions and their customers.
But this adoption process is spotty at best. In a number of upcoming stories, I’ll show showcase a series of recent cyberheists in which small businesses victims banked at institutions that continue to allow the transfer of hundreds of thousands of dollars of their customers’ money, while requiring nothing besides a simple username and password.
ENISA’s advice is all the more relevant because it is frequently difficult for customers to “shop around” for banks with the best security, beyond inquiring about customer-facing security precautions such as tokens or dual authorization: For better or worse, most financial institutions are reluctant to talk about what they may be doing to protect customers.
The “High Roller” report from McAfee and Guardian Analytics highlights a sophisticated threat that has mainly targeted European customers, but which has recently been spotted being used against high-dollar targets at U.S. banks. Perhaps one reason these particular automated attacks have been slow to target U.S. customers is the relative uniformity and low number of financial institutions in Europe, South America and other regions, in comparison to the United States. For example, the United Kingdom has only a handful of financial institutions servicing commercial and retail customers, whereas in the United States, there are more than 7,000 financial institutions.
Of course, it is not enough to fight this problem by constantly reacting to the latest malware tactics. I have long believed that although the cybercrime underground is expanding each day, much of it is run by a fairly small, loose-knit, and innovative group of hackers. That’s why I was gratified to see ENISA calling for a more coordinated response to fighting cybercriminals and their infrastructure.
Many skeptics counter that cybercrime is a whac-a-mole problem, and that as soon as you take out one prominent cybercriminal mastermind, another will rise up to take his place. This belief seems to stem from an understandable but misguided belief that the underground is a highly structured organization akin to the traditional mafia. To my mind, nothing could be further from the truth: Most of these guys can be best described as taking part in disorganized cybercrime. That is to say, they are a confederation of independent contractors who work together because it is of mutual financial benefit. The key here is that there is no loyalty in these alliances, and when one party gets arrested or disappears, it has an immediate and measurable impact on his peers.
Having spent an untold number of hours on countless underground forums, it seems to me that many of the same characters run the same sections on multiple fraud forms. As a result, targeting just a few dozen individuals — as opposed to going after a group of people engaged in a specific forum or cyberattack or crime — could have a disproportionate effect on overall cybercrime levels and losses. This was largely the conclusion of a study released last month in the U.K., called Measuring the Costs of Cybercrime (PDF).
If you run a small or mid-sized business, consider doing your banking from a Live CD. I’ve published some instructions at this link that can have you running Puppy Linux from a CD within minutes. Puppy is extremely lightweight (it fits on a regular CD), boots very quickly, and supports most hardware.
[EPSB]
Have you seen:
Banking on a Live CD…An investigative series I’ve been writing over the past three years about organized cyber crime gangs using malware to steal millions of dollars from small to mid-sized organizations has generated more than a few responses from business owners concerned about how best to protect themselves from this type of fraud. I said this nearly three years ago, and it remains true: The simplest, most cost-effective answer I know of? Don’t use Microsoft Windows when accessing your bank account online.
[/EPSB]




I cant understand why banks can’t provide dedicated secured common hardware devices for banking, like netbooks,iPads or dedicated cellphones?
It’s looks much easier to pre-made “secure locked special purpose device for online banking” instead of fighting all modern threats. Such solution could be pretty mobile and can be shipped with 3G modem\contract for to ensure that Internet connection also not compromised. No other software could be installed, updates could be built-in, but device actuually should forbid any other activity not related to banking. Usb stick with bank keys could be used as logon credentials.
Modern cheap and moble hardware could be pretty affordable and add some serious security layer to online banking.
Banks with such servcie could earn more customers care reputation with such optional service.
It’s probably as simple as they don’t want to provide technical support for hardware.
The hardware would ship with buggy software. No one would ship updates. Eventually someone would discover a successful exploit and take that bank and its customers to the cleaners.
The customers would sue the bank and a court would find it financially liable.
If you don’t believe hardware comes with buggy software, you’ve ignored the mobile phone, video game player, DVD player, and Blueray player markets.
On the update side, at least mobile phones have a pretty bad track record of getting updates (dating back to Symbian and forward to Android).
Note that while Windows isn’t wonderful, a useful feature is that Microsoft pushes software updates. They recently dropped support for weaker Certificates. The banks are unlikely to get certificates right (even big companies like Microsoft and Apple get them wrong, you can’t expect a small company to get it right).
The worst press case would probably be closer to the Picture Frame model where a factory creating your bank device has an infection and the bank device is shipped infected to customers.
Or, just like skimmers are added to ATMs, a criminal might sneak in and insert something into your device, or even swap it for a fake. The fake could act as a MITM to your real device.
This problem can’t be solved by hardware.
I’m glad to be back in North America, where I can do my banking by phone. I trust my banks to log all phone calls (at least one bank affiliated insurance company informed me they keep all phone logs for 7 years).
This is strange, szorry
I’m glad to be back in North America, where I can do my banking by phone. I trust my banks to log all phone calls (at least one bank affiliated insurance company informed me they keep all phone logs for 7 years).
to trust phone calls (and voice in that) ??? You must be kidding. [not even talking about recent flaws misusing phone communication by nasty ways]
To paraphrase you, I’m better glad to be not in US/be in Europe, and use mine ‘standalone smartcard reader with screen’ (different names for the device) produced by verified company and given to me by my bank, to be used together with bank’s chip card, and can choose level of security, for example whether to use one-time code for InternetBanking login only, or for each txn, or even to ‘sign’ the values/amount/recipient account in the specific money transfer.
[yes, aware of potential risks (like producer of device can be compromised, as stated in post above) , but would be bank’s problem, not mine]
Support for hardware is important, but the price is the problem here. I don’t know about US but in Europe most on-line accounts are just free, money tranfers are for free, cards are for free (or really small fee under $0.5 per month). Such device with 3g connectivity and stuff would cost too much.
Brian: this is great news. I look forward to the equivalent American and Canadian regulators making the same pronouncement.
I completely agree with this article but I think that as a security professional we are swimming against a cultural tide of, “No me, I’m not infected because I don’t go to ‘THOSE’ websites”. It is difficult educating users that their computer is very blatantly infected with a virus or malware and let alone the ZueS or Spyeye Trojans, where they will never see any outward signs of infection. Online banking has always been a two sided equation and financial institutions can only do so much to prevent fraud. I see a need to bring the public into the security conversation in a friendly, non-scary way. Educate the public about the invisible threat their financial security is in and how they need to take responsibility for their end. I can also see banks charging a fee to bank online if you do not provide a means to verify your transactions out of band.
@Chuck: “It is difficult educating users that their computer is very blatantly infected with a virus or malware and let alone the ZueS or Spyeye Trojans, where they will never see any outward signs of infection.”
It is common even for security experts to believe they are not infected, mainly because malware has not jumped up and slapped them in the face. They will claim to never have been infected, even though they cannot know any such thing. Tools do not exist to prove that claim, at least on normal computers.
The inability to detect hiding malware is a very serious problem, which reflects into social responsibility: How can we blame a user for being infected, if there exists no tool which can guarantee that he is absolutely clean? How could a user prove himself innocent of malware charges?
Advising for a LiveCD is completely impractical for 99% of the userbase. Just because it “technically” protects the user doesn’t mean it is an actual solution. Ignoring that a large amount of the userbase is disinclined to even upgrade to a newer version of Windows because it looks different, who on earth wants to shut down all of their current work and reboot to a different OS JUST to access the bank website. That’s ridiculous.
Something is weird with this site, after I just posted comment (below you) I saw your name and email address in the fields…
Tell that to the victims. I guarantee you that they’re always interested in doing this, but only *after* they’ve had six figure losses. Talked to two more victims this week, in fact, that lost collectively more than a half million in two separate heists. They’re both going to be moving to either a stand-alone, dedicated system or Live CD.
And hey, following Sept 11 everyone was more than willing to allow poorly thought out security measures in the airports – obviously since people were ok with them when they were hurt and scared those measures must be good.
Just because people who have lost boat loads of money are willing to jump through lots of hoops to avoid losing more money doesn’t validate your advice – in fact admitting they only do so AFTER they lost money shows the flaw in your advice since people are only willing to accept the inconvenience after they are burned, not before.
This is a problem banks could solve – they could allow people to whitelist where money is transferred, profile transfers and require escalation on abnormal behavior, etc. ENISA is going the right direction and putting the impetus on the banks, rather than the clients
You’re right, Josh. Mom and pop businesses should just shake their fists at the banking sector and bury their heads in the sand. I realize this solution is not ideal, and that banks *should* be doing more (a theme that comes up in much of my reporting). But until they do, wishing the situation were different doesn’t make you any more secure.
I’m not suggesting Mom and Pops just shake their fists and do nothing – rather I am suggesting that if we are giving advice among other things we can point people to services that actually provide some level of protection of small business accounts. There are several credit unions that are far more proactive about this than banks as they feel the loss of even small clients more, and also feel the loss of any fraud they eat more. It has created financial motivations to engineer appropriately that larger banks do not have. Alternatively, following the ENISA guidance I suspect the Euro banks that also offer services in the US will be more competitive in this regard than their US counterparts.
Directing people to be choosy about their institutions (and how to be choosy) will create market forces that cause the rest of the banks to change to remain competitive. Advising users to assume all of the responsibility themselves will not create those market forces. Of course it would be helpful if courts actually watched out for the little guys instead of the large corporations, but that I am not optimistic of changing (and certainly the current trends are going in the opposite direction)
I mention the need to shop around, but according to you, asking people to bank on a live cd is unrealistic. So, is it any more realistic that small businesses that may have been with a bank for many years suddenly disrupt their operations and move to another bank? Which one is more likely do you think?
Honestly I think one time disruptions are significantly more tolerable to people than reoccurring disruptions, wouldn’t you agree? If you could have the oil changed in your car once and it was good for life, but took 3x as long as a normal oil change, wouldn’t you still prefer that option? And honestly security is just one reason to encourage small businesses to look at certain credit unions – not only do the tend to be more progressive about protecting SB accounts and limiting liability, but they tend to have lower fees, far more branches and ATMs if they are part of the NCUA, and higher return on account balances (because you don’t just get interest, but also dividend payments based on your balance). In that regard the decision produces returns even if the business never has their credentials compromised.
One of the issues is that institutions view security controls as a tax as opposed to a competitive enabler. Some organizations have found they need to pay that tax because it is cheaper than the alternative, but the large ones haven’t. Someone like you who has the influence could solicit policies/controls that protect SBS customers from various institutions and publicize the institutions that do a great job, and that would matter. I could very easily see a google query for “safest bank for small businesses” having the first link be on your site with a list of progressive companies. You have enough audience (and enough media that follows you) that you really could draw attention to the good companies and create market conditions that reward protecting small business accounts
I don’t really see how you can argue that changing institutions is going to be less hassle than using Live CD or dedicated computer if there is added security measures at the new institution which presumably requires extra steps to be carried out by the banks customers for transactions.
Josh wrote:
“There are several credit unions that are far more proactive about this than banks as they feel the loss of even small clients more, and also feel the loss of any fraud they eat more. It has created financial motivations to engineer appropriately that larger banks do not have.
If you look at the report (PDF) that Brian linked and referenced in the article, “Dissecting Operation High-Roller”, you’ll see in the Executive Summary that it’s not only the banks. It includes credit unions, large global banks and regional banks.
I have no doubt that there are credit unions out there that are proactive. Apparently, though, not all credit unions have been proactive.
P.S. 1 ENISA put the onus squarely on the financial instirutions and did not provide specific recommendations for organizations and consumers. Brian’s article filled in an important deficiency in the ENISA advisory. Namely, actions that business owners and consumers can take to protect themselves in the meantime.
P.S. 2 I agree with you that both organizations and consumers should be more selective as to which financial institutions they conduct business with. At a minimum, a shopping list for organizations and consumers with which to make comparisons of various financial institutions would be valuable.
How much of this is perpetuated by the economic structure of banks and customers? I know someone now who was a victim of bank fraud, it takes the bank 4 months to ‘investigate’ meanwhile tying up all of his money and the bank sharing no real responsibility for the transfers or blatant fraud it permitted to happen.
Until the lions share of risk belongs to the banks instead of the poor sap home user, expect this to keep happening. This is actually a good step in the direction of forcing banks to actually stand behind the transactions they permit, requiring them to hold some accountability for losses or risky transfers they generally permit on a large scale then blame the victims.
When the bank itself stands to lose thousands or millions from fraud, that is when we will actually see them start to focus on weeding out these bad players, until then they write off any losses, sock the customer with fees and penalties, and the crook walks away with a low risk of ever getting caught.
“what’s in a name”:
America’s small- and medium-sized banks *can’t* be held responsible for commercial-account online banking funds transfer fraud–their capital bases are too small with respect to the size of the flows in and out of the demand accounts of their small- and medium-sized enterprise customers. They also do not have, and cannot acquire the cybersecurity expertise needed to even read the FFIEC’s 2005 and 2011 Guidances with understanding. Lastly, they don’t actually run the information technology on which online banking is done; they outsource the function to one of 13 “processors” such as Intuit Financial Services (formerly: Digital Insight) or Metavante.
Nor would we want them to. We need America’s bankers out making loans that will boost employment, not trying to become part-time cybersecurity jocks.
Of course, the small- and medium-sized banks commercial customers are even less able to secure online banking.
yourmoneyisnotsafeinthebank.org does even want America’s small- and medium-sized banks to have to *know* cyberattacks are possible, much less their customers be burdened with that information. There is nothing they can do with that information anyway–the Pentagon cannot reliably fend off attacks on its information technology infrastructure. Having our small banks have to deal with things like the FFIEC Guidances is itself an important victory for our adversaries, much as the cost and hassle we impose on ourselves via TSA Security is Al Qaeda’s largest and most enduring victory over us.
This is not to say that we don’t want America to have an informed citizenry. Our democracy depends on it. But during the Cold War average Americans were not asked to personally conduct defensive operations against the Evil Empire, and it makes no more sense to ask Americans to do the equivalent during our current Cyber Cold War.
If public policy could move all Americans to run tests, the tests would not be for malware on their Windows PCs! Undiagnosed diabetes and hypertension are costing us 10s of billions of dollars per year, a number that is rapidly escalating. The fact that our best efforts at educating the public can’t get *these* rates down should give pause to those of you who think “user education” can be any important part of the solution to cybercrime.
I have been having trouble with your RSS Feed for some time now. I read my feeds in Microsoft Outlook 2010. I do not have issues with my other feeds, just this one. I have removed it, unsubscribed, resubscribed, deleted all content repeatedly – and no matter what I do, it re-downloads the last 10 articles, showing them as unread, even though I already have copies that I have read. This leaves me 20 articles listed, for instance, 10 that I have read, 10 that have downloaded newly which are copies of the 10 I already have. Any idea why this is occurring? Thanks.
Sorry all… I didn’t realize the comment space was just for this thread. I’ve submitted my issue elsewhere now.
Don’t get me wrong, I’m all for increased security and always assume that customers’ PCs are infected, but from the community bank standpoint, we walk a very thin line. Customers expect free accounts, free online banking, everything free, but as you all know, providing increased security costs money that the customers don’t want to pay for – whether through online banking fees or any other fees (and typically our Board members don’t want to pay for it either). Additionally, here in rural America, just adding multi-factor authentication caused a huge stir. We always recommend that our business banking customers use dedicated PCs for their sessions, but we have yet to see them follow suit. We also provide a wide variety of educational information regarding security, but we all know how often it gets read by the average customer. I would love to have a cure all for this, but as much as I tell my banks to champion information security, they often get stuck between a rock and a hard place that are customer demands and regulatory requirements/best practices.
Some of the rootkits out there can infest the BIOS/CMOS and rewrite the firmware on the network card and graphics card. A live CD is no protection against these.
@Jonathan Rynd: “Some of the rootkits out there can infest the BIOS/CMOS and rewrite the firmware on the network card and graphics card. A live CD is no protection against these.”
Sadly, “security” is not about absolutes: There is, and can be, no *absolute* security. Instead, security is inherently comparative, and since current systems are completely vulnerable to normal (software) infection, why would we expect anything better against hardware infection?
Infection is a computer equipment problem and cannot be solved by software alone, even software from a DVD. On the other hand, if malware cannot run in the encountered OS, it is not going to be doing much infecting. So in that sense, yes, a LiveDVD is indeed protection against *new* hardware infection. It just cannot reverse an infection which has already occurred.
The user is well advised to use only their own hardware; to protect it and take it with them. An older laptop with a DVD writer and hard drive removed is a good choice. A small external router may provide added protection.
To quote Voltaire: “Perfect is the enemy of good.”
From a security perspective, we can all come up with scenarios where a Live CD isn’t absolutely perfect, but it’s still exponentially more secure than a standard Windows install.