Credit and debit card accounts stolen in a recent data breach at retail giant Target have been flooding underground black markets in recent weeks, selling in batches of one million cards and going for anywhere from $20 to more than $100 per card, KrebsOnSecurity has learned.
Prior to breaking the story of the Target breach on Wednesday, Dec. 18, I spoke with a fraud analyst at a major bank who said his team had independently confirmed that Target had been breached after buying a huge chunk of the bank’s card accounts from a well-known “card shop” — an online store advertised in cybercrime forums as a place where thieves can reliably buy stolen credit and debit cards.
There are literally hundreds of these shady stores selling stolen credit and debit cards from virtually every bank and country. But this store has earned a special reputation for selling quality “dumps,” data stolen from the magnetic stripe on the backs of credit and debit cards. Armed with that information, thieves can effectively clone the cards and use them in stores. If the dumps are from debit cards and the thieves also have access to the PINs for those cards, they can use the cloned cards at ATMs to pull cash out of the victim’s bank account.
At least two sources at major banks said they’d heard from the credit card companies: More than a million of their cards were thought to have been compromised in the Target breach. One of those institutions noticed that one card shop in particular had recently alerted its loyal customers about a huge new batch of more than a million quality dumps that had been added to the online store. Suspecting that the advertised cache of new dumps were actually stolen in the Target breach, fraud investigators with the bank browsed this card shop’s wares and effectively bought back hundreds of the bank’s own cards.
When the bank examined the common point of purchase among all the dumps it had bought from the shady card shop, it found that all of them had been used in Target stores nationwide between Nov. 27 and Dec. 15. Subsequent buys of new cards added to that same shop returned the same result.
On Dec. 19, Target would confirm that crooks had stolen 40 million debit and credit cards from stores nationwide in a breach that extended from Nov. 27 to Dec. 15. Not long after that announcement, I pinged a source at a small community bank in New England to see whether his institution had been notified by Visa or MasterCard about specific cards that were potentially compromised in the Target breach.
This institution has issued a grand total of more than 120,000 debit and credit cards to its customers, but my source told me the tiny bank had not yet heard anything from the card associations about specific cards that might have been compromised as a result of the Target breach. My source was anxious to determine how many of the bank’s cards were most at risk of being used for fraud, and how many should be proactively canceled and re-issued to customers. The bank wasn’t exactly chomping at the bit to re-issue the cards; that process costs around $3 to $5 per card, but more importantly it didn’t want to unnecessarily re-issue cards at a time when many of its customers would be racing around to buy last-minute Christmas gifts and traveling for the holidays.
On the other hand, this bank had identified nearly 6,000 customer cards — almost 5 percent of all cards issued to customers — that had been used at Target stores nationwide during the breach window described by the retailer.
“Nobody has notified us,” my source said. “Law enforcement hasn’t said anything, our statewide banking associations haven’t sent anything out…nothing. Our senior legal counsel today was asking me if we have positive confirmation from the card associations about affected cards, but so far we haven’t gotten anything.”
When I mentioned that a big bank I’d spoken with had found a 100 percent overlap with the Target breach window after purchasing its available cards off a particular black market card shop called rescator[dot]la, my source at the small bank asked would I be willing to advise his fraud team on how to do the same?
CARD SHOPPING
Ultimately, I agreed to help in exchange for permission to write about the bank’s experience without actually naming the institution. The first step in finding any of the bank’s cards for sale was to browse the card shop’s remarkably efficient and customer-friendly Web site and search for the bank’s “BINs”; the Bank Identification Number is merely the first six digits of a debit or credit card, and each bank has its own unique BIN or multiple BINs.
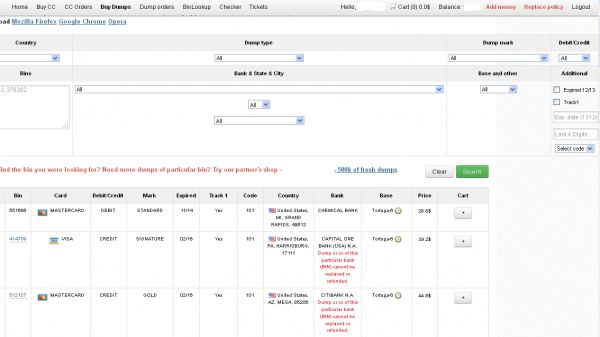
According to the “base” name for all stolen cards sold at this card shop, the proprietor sells only cards stolen in the Target breach.
A quick search on the card shop for the bank’s BINs revealed nearly 100 of its customers’s cards for sale, a mix of MasterCard dumps ranging in price from $26.60 to $44.80 apiece. As one can imagine, this store doesn’t let customers pay for purchases with credit cards; rather, customers can “add money” to their accounts using a variety of irreversible payment mechanisms, including virtual currencies like Bitcoin, Litecoin, WebMoney and PerfectMoney, as well as the more traditional wire transfers via Western Union and MoneyGram.
With my source’s newly registered account funded via wire transfer to the tune of USD $450, it was time to go shopping. My source wasn’t prepared to buy up all of the available cards that match his institution’s BINs, so he opted to start with a batch of 20 or so of the more recently-issued cards for sale.
Like other card shops, this store allows customers to search for available cards using a number of qualifications, including BIN; dozens of card types (MasterCard, Visa, et. al.); expiration date; track type; country; and the name of the financial institution that issued the card.
A key feature of this particular dumps shop is that each card is assigned to a particular “base.” This term is underground slang that refers to an arbitrary code word chosen to describe all of the cards stolen from a specific merchant. In this case, my source at the big bank had said all of the cards his team purchased from this card shop that matched Target’s N0v. 27 – Dec. 15 breach window bore the base name Tortuga, which is Spanish for “tortoise” or “turtle.”
Indeed, shortly after the Target breach began, the proprietor of this card shop — a miscreant nicknamed “Rescator” and a key figure on a Russian-language cybercrime forum known as “Lampeduza” — was advertising a brand new base of one million cards, called Tortuga.
Rescator even created a graphical logo in the Lampeduza forum’s typeface and style, advertising “valid 100% rate,” and offering a money-back guarantee on any cards from this “fresh” base that were found to have been canceled by the card issuer immediately after purchase. In addition, sometime in December, this shop ceased selling cards from other bases aside from those from the Tortuga base. As the month wore on, new Tortuga bases would be added to shop, with each base incrementing by one with almost every passing day (e.g., Tortuga1, Tortuga2, Tortuga3, etc.).
Another fascinating feature of this card shop is that it appears to include the ZIP code and city of the store from which the cards were stolen. One fraud expert I spoke with who asked to remain anonymous said this information is included to help fraudsters purchasing the dumps make same-state purchases, thus avoiding any knee-jerk fraud defenses in which a financial institution might block transactions out-of-state from a known compromised card.
The New England bank decided to purchase 20 of its own cards from this shop, cards from Tortuga bases 6-9, and Tortuga 14 and 15. The store’s “shopping cart” offers the ability to check the validity of each purchased card. Any cards that are checked and found to be invalid automatically get refunded. A check of the cards revealed that just one of the 20 had already been canceled.
The bank quickly ran a fraud and common point-of-purchase analyses on each of the 19 remaining cards. Sure enough, the bank’s database showed that all had been used by customers to make purchases at Target stores around the country between Nov. 29 and Dec. 15.
“Some of these already have confirmed fraud on them, and a few of them were actually just issued recently and have only been used at Target,” my source told me. Incredibly, a number of the cards were flagged for fraud after they were used to make unauthorized purchases at big box retailers, including — wait for it — Target. My source explained that crooks often use stolen dumps to purchase high-priced items such as Xbox consoles and high-dollar amount gift cards, goods that can be fenced, auctioned or otherwise offloaded quickly and easily for cash.
My source said his employer isn’t yet sure which course of action it will take, but that it’s likely the bank will re-issue some or all of the 5,300+ cards affected by the Target breach — most likely sometime after Dec. 25.
The bank is unconcerned that its cards compromised in the Target breach might be used for online shopping fraud because the stolen data does not include the CVV2 — the three digit security code printed on the backs of customer cards. Most online merchants require customers to supply the CVV2 as proof that they posses the legitimate, physical card for the corresponding account that is being used to fund the online purchase.
Update, 5:20 p.m. ET: In a message to consumers, Target CEO Gregg Steinhafel said Target would be offering free credit monitoring for affected customers. Not sure how credit monitoring helps with this specific breach, but at any rate here’s the rest of his statement:
“Yesterday we shared that there was unauthorized access to payment card data at our U.S. stores. The issue has been identified and eliminated. We recognize this has been confusing and disruptive during an already busy holiday season. Our guests’ trust is our top priority at Target and we are committed to making this right.
We want our guests to understand that just because they shopped at Target during the impacted time frame, it doesn’t mean they are victims of fraud. In fact, in other similar situations, there are typically low levels of actual fraud. Most importantly, we want to reassure guests that they will not be held financially responsible for any credit and debit card fraud. And to provide guests with extra assurance, we will be offering free credit monitoring services. We will be in touch with those impacted by this issue soon on how and where to access the service.
We understand it’s been difficult for some guests to reach us via our website and call center. We apologize and want you to understand that we are experiencing unprecedented call volume. Our Target teams are working continuously to build capacity and meet our guests’ needs.
We take this crime seriously. It was a crime against Target, our team members, and most importantly, our guests. We’re in this together, and in that spirit, we are extending a 10% discount – the same amount our team members receive – to guests who shop in U.S. stores on Dec. 21 and 22. Again, we recognize this issue has been confusing and disruptive during an already busy holiday season. We want to emphasize that the issue has been addressed and let guests know they can shop with confidence at their local Target stores.”
[EPSB]
Have you seen:
Non-US Cards Used At Target Fetch Premium”…An underground service that is selling millions of credit and debit card accounts stolen in a recent data breach at retail giant Target has stocked its virtual shelves with a new product: Hundreds of thousands of cards issued by non-U.S. banks that were used at Target across the United States during the retailer’s 19-day data breach. It’s not clear how quickly the non-U.S. cards are selling, but they seem to be fetching a much higher price than those issued by U.S. banks.
[/EPSB]






One news report said the risk affects other cards owned by people affected by the breach even if those cards were not used at Target. How big is this risk and what can be done to protect against it?
Could be wrong but I don’t understand how other cards would be at risk. Stolen card info aside, wouldn’t a name and a bank be the only thing they have?
There is a great deal of overly alarmist and inaccurate reporting on this breach. There is no reason why the compromise of a card used at the store would affect or jeopardize other cards that were not.
Use cash. Once you deposit in a bank it becomes phony funny money and can be stolen or manipulated by anyone talented enough to “fool” a machine.
This is unlikely and another rumor that needs to be quashed. This breach will be limited to the cards used at Target and were part of the hacked information.
As a person with a card used at Target- you have two choices. Cancel the card now and get a new card. Or monitor your account online at least daily for the next few months and let your card issuer know of any purchases you have not made immediately. You will not be held responsible for the charge if you do this. Also, you probably will be notified if the issuer has assessed that your card is at risk and be issued a new card.
Cards not used during the time frame or not used at Target do NOT need to be cancelled.
“Cancel the card now and get a new card. Or monitor your account online at least daily for the next few months and let your card issuer know of any purchases you have not made immediately. ” I went to a local bank branch, got a new debit card and returned home all within an hour. The time necessary to monitor your card for months would be much more than an hour. Plus there is the constant worry. Therefore, get new cards. Please read my other entries for more advice when changing card numbers. Merry Christmas!!
Interesting, because the media is saying that the CVV was part of the data stolen.
The CVV is not the same thing as CVV2. CVV is on track 1 of the magnetic stripe, from which the data in this breach was stolen. The CVV2 is the 3-digit number printed on the back of the card for phone and internet transaction verification, and is *not* on the mag stripe.
Excellent reporting on a new story with so much bullshit surrounding it.
Kudos and thanks to you Brian. It can be hard finding other news sites of this nature that are actually written by people with knowledge and experience on the subject, and when they are found they rarely have the same level of reporting skill and quality of information that you have.
Obviously you don’t need my approval, but please do keep up the great work.
Great response! I am a new subscriber to “Krebs” and am extremely impressed! Look forward to using this site each day.
There’s actually two CVV’s on a card. CVV1 is on the magstrip and is different from CVV2 which is on the back.
These guys got the CVV1. But the CVV from the back of the card that you need for online purchases (CVV2) didn’t get lifted because that isn’t part of the instore transaction.
So the media doesn’t quite have it correct…
The main stream media never gets all that facts right, it’s just a rehash of available information from third party sources
There was some early confusion because Target’s initial announcement said the “CVV” was stolen, then described it as the CVV2; they later changed the notice to describe it as the CVV1 (consistent with a magstripe breach).
Fantastic article Brian.
And for anyone dithering, just go get a new card number now, before you forget it.
I will. I am going to take a chance however and wait until I have all my x-mas shopping done since it takes days to get new cards issued. In the meantime all I can do is watch statements. I have a separate bank account with a debit card that I use only for online purchases and just put enough money in it to cover my purchases, so if they get that card they won’t have access to but perhaps $10.
“I have all my x-mas shopping done since it takes days to get new cards issued.” I got a new debt card in about 15 minutes. See my other entries for more critical info. Get new cards ASAP.
Debit cards can be dicey if you have a lot of money in the account. What you are doing is smart but I still would not use a debit card online. Debit cards have less protection than credit cards especially if the PIN is used.
Re : it takes days to get a new card.
Well, it depends.
Earlier this year I was in Europe and tried to use my credit card from Chase and it was declined. I called the Chase customer number and found out that the card was stopped because they could not verify that suspicious purchase was valid or not (Tried to call me, but of course could not reach me. Yes, I did tell them in advance that I was going to be out of the country within X and Y dates).
BTW, the suspect purchase was not made by me.
The customer rep said they would issue a new card, with new account #, AND they would have it delivered to me in Europe within one business day (within 24hrs. if in the U.S.).
I was trying to search for card numbers in my state (Maine) for a newspaper article I am writing, but now the Rescator website is “under construction.”
Is that normal?
Brian probably published this article, they saw it, and then moved their site.
This happens a lot. Brian goes and posts an exposé on some underground site…and within hours it’s gone dark…
I call it the Krebs Effect. (also seen as The Digg Effect, Slashdot Effect, etc.)
Sadly though, the site will still be available on the Deep Web somewhere.
http://en.wikipedia.org/wiki/Deep_Web
I’m wondering how Target Red cards might be particularly effected by this, since those are tied directly to a customer’s bank account and the signup process involves entering the customer’s bank info into some (similar? the same?) system at the point of sale. Changing that card might not matter if the thieves have the bank info.
Target Red Cards can be setup as either credit or debit accounts. I have a Red Card credit account that is just a store credit account. Hopefully that type of card would be notably less valuable to thieves than a Mastercard or Visa, since it only works at Target.
Using debit cards for anything other than getting cash from an ATM or making deposits at an ATM is asking for trouble, when these types of situations occur.
The debit cards are the ones I’m speaking of. Is the potential problem here even grater than is being discussed?
Its impossible to know (as an outsider) the extent of the information breached, but if the POS was the point-of-compromise so to speak, then the thieves will only have your “red card” number and not your bank details (which is quite worthless unless they like to shop at target). If the primary database holding “red card -> bank info” data were compromised then yes, that would constitute a problem for red card holders but would also be a “holy ****” moment in the financial world as all those millions of bank account numbers and routing numbers would be in the wild, and that would certainly be making headlines alongside or above the story of stolen credit card data.
Target Red debit card is known as a decoupled debit card. It gets its name from the fact that rather than riding the online card transaction network rails for transaction processing, Target (the card can only be used in Target stores) has a record of the cardholder’s bank and account number and converts the transaction to an ACH transaction. From all reports, only the card track data was stolen so there was no compromise of the cardholder’s bank account information for the ACH conversion.
As to the comment about not entering a PIN, I think that is a bunch of nonsense. The liklihood of having a PIN compromised is much greater at an ATM then it is at a retail POS. Issuers used to encourage customers to run their debit as a “credit” transaction as it meant higher interchange revenue, but that has all changed since the Dodd-Frank Act no longer differentiates signature from PIN debit transactions as to interchange revenue.
Go to the Target website and change the pin on your card. Also, do not use the card for now and put an alert both at Target and at your bank for any transaction greater than 50 cents.
Easier said than done. My wife has tried to get to the Target site and log in and has found it impossible to use for the past two days.
Don’t stress about contacting Target, its impossible at this time. Just call or go to your bank, tell them to look at your history for an ACH debit from Target, and they can use that info to create a new specific ACH reject. So anything from .01c to $50,000 as an ACH from Target will be rejected by the bank.
And then go cancel that RedCard as soon as they can answer their phones!
I was able to check my Target credit card account this evening. (Target’s now only offering Red Cards, but they used to offer Target Visa cards.)
Josh,
The RedCard has its own proprietary account information in embedded in the Mag. The “linked” bank account information is not in the Mag. What the fraudsters has is access to this proprietary number and cross reference key that enables their back office to process a debit against the checking account the card is tied to.
It’s important to understand that to use a RedCard in a Target, you “Must” PIN and the PIN was not compromised.
The best the fraudster could do would be to clone the RedCard and then go back into a Target store and attempt to use “white plastic”, which would do them no good as the POS would prompt for PIN.
The mag on these, as with the mag track 1 data on normal debit and credit cards does have the name of holder, but again that information is printed on the face of the card. There is no means to link a simple name “Joe Smith” back to anything other than the Target in-house account number for the RedCard.
To my knowledge, no backs are reporting any fraud activity associated with the RedCard.
This past year the associated reported well over 500 compromises, primarily from smaller merchants, but larger institutions such as Raley’s, Schnucks and Zaxbys were reported, so the fraudsters still have caches of these cards.
ATM Skimming is still rampant, so any fraud people are seeing on their cards is automatically associated with Target. If you used a tampered with ATM over that period with your debit you would most likely see ATM fraud, but could not associate it to Target as PIN was not compromised, but again the media will report that any fraud now must be associated with Target.
Make no mistake these cards will be sold and counterfeited, but the fraudsters use them in fairly predictable patterns, so your banks will pick up on any fraud activity and notify you. If there is fraud, the consumer has “Zero Liabiltiy” and most banks will process a reversal in a few days or less and process a new card.
Thank you so much Brian for writing what I consider the only balanced, well-written and informative story on this topic. Your two blog posts saved me a lot of grief, as I was able to cancel my card before I travel for the holidays and now do not have to worry about it non-stop for my entire vacation.
I shopped at Target on a day in the dreaded period and went ahead and cancelled my debit card and got a new one. I was able to go to my bank and get a new one in person so I now have peace of mind for just a little bit of inconvenience.
This article explaining how numbers are sold is really an eye opener for me. Sadly it is clear that this type of activity is only going to increase.
Your blog is truly providing an excellent public service and really helped me avoid having my bank account cleared while I was on vacation.
Thanks again.
Seems like the perfect way to use these is this gadget at self-service checkout lines:
https://onlycoin.com/
I suspect Tortuga is a nod to “Pirates of the Caribbean.”
Great article and a service to us all. What a great service it would be for someone to create a secure website where a card number could be checked to determine if the number in question had been “breached”. So many ideas…so little expertise 🙂
How likely is it that someone makes a fraudulent online purchase without a CVV2 code with a stolen card? I noticed that on occasion I haven’t been asked for one (e.g. something like utility bill payment). I am surprised that such transactions are allowed without a CVV2.
Very interesting article , one of the better ones here in a while.
In the article it didn’t state if any of those new credit cards used at Target for the first time where not from identity theft of a person. This then would allow the criminals to make purchases at Target to fenced immediately. Furthermore, it would allow for the resale of the card information in a underground forum which then it would guarantee that it’s 100 percent valid information
Any PIN’s for Debit showing up yet?
Great report Brian, thanks for clarifying all of the misinfo being spread elsewhere. Was any PII taken in this breach that could lead to identity theft & additional problems for consumers? Or, was it just the card numbers that were compromised? My wife shops at Target w/ our CC at least once a week, so I’m curious if canceling that CC pretty much terminates the risk, or if our name, address, & other info is now being shopped around too.
Here is a link that explains what is on the mag strip of financial cards. Name and account number. Among other things. I don’t recall is the PAN is your account number or a number associated to your account at the back.
http://en.wikipedia.org/wiki/ISO/IEC_7813#Track_1
Brian, I’d like to suggest some follow up along the lines of people asking whether the Target Red Cards are going to be a problem. It turns out that while the PCI council has all kinds of rules about protecting PANs, they have almost none about ACH data. (As a security person in the industry, I always found this rather ironic.)
The most helpful bit of information would be for Target to explain how the Red Cards actually work. Frequently, cards like that are actually issued by the payment processor/processor’s BIN bank. If that’s the case, there would be no reason for Target to store the ACH data in their systems (Target needs to confirm) and the stolen Red Cards would only be useable at Target. On the other hand, if Target decided to do the Red Cards in house, given the size of the breach, they could have lost everyone’s ACH data. That would be a big deal and consumers (and their banks) need to know that now. Having someone steal your credit card number is almost a non-issue (for you) because of limited liability, at least in the US. Having someone steal ACH data is a much bigger deal. There are much more limited consumer protections for fraudulent withdrawals from bank accounts.
One final note, I think you should update your general security advice to “never enter your PIN when making a purchase.” Most “DEBIT” cards can be used as a credit card. This is the preferred approach since in situations like this it means the PIN won’t be compromised. PINs should only be used for ATMs.
My bet is they are simply cross-referenced with ACH data stored on a separate database.
You swipe your card for payment, the terminal checks with the database to see if the card # is valid, and then makes the ACH payment using information stored in a secure database in Target’s Data Center.
The idea being that if the card is compromised, it does not also compromise your bank account.
+1 on that. Though I’m not an industry insider, as a consumer I once got Target to change the bank account behind a REDcard debit purchase *after* it was made; that suggests the ACH data is retrieved from a central database AFTER purchase. So far, all indications are this was a store-level hack that did NOT affect the central database. At most, anyone with REDcard debit magstripes would have to (a) guess or steal the PIN (as Brian has said there is currently *NO* indication of any large-scale PIN breach), then (b) copy the magstripe to a blank card and (c) use it *ONLY* at Target.
There should be *no* ACH data in Target card terminals, where reports currently say the breach occurred. Even if (as I and some others suspect) the breach was actually in the store registers, at most they would *only* have ACH data for (a) checks, thanks to “e-check”, and (b) new REDcard debit cardholders who signed up at the register while the hack was active.
PCI is a requirement of the card issuers who would rather that ACH based systems become less secure and reliable. They’re all about the transaction fee and interest generated using Visa, MC and other charge and debit cards used on their networks. Vendor ACH chards avoid these fees and are bad for the credit/debit card issuers.
On *that* point, you & Tim are definitely on the money. PCI applies to general-purpose cards (Visa, etc.), but usually *not* to store-branded cards like REDcard. But then, Target is likely to bear *ALL* the risk for the REDcard side of the breach, PCI or no PCI; I suspect TD Bank will make Target reimburse it for breach-related losses on REDcard credit, and as the issuer Target itself is on the hook for REDcard debit. (If the worst happened and the central ACH database were breached, surely the banks will make Target pay in court — most likely via class action. At that point even consumers might go after Target, since the REDcard agreements do *NOT* contain arbitration clauses.)
To answer a specific question: Target Corporation (the parent company) issues all REDcard debit cards itself; I understand they’re serviced from the same Target office in South Dakota that services REDcard credit cards (formerly issued by a Target-owned bank in SD, now issued by TD Bank but still serviced by Target). I’m 99% sure the ACH data is in a Target database in SD, but all indications are the hack was at STORE level (whether at card terminals, registers or store servers). I doubt the thieves have any ACH data, thus at most they could make purchases at Target *IF* they have PINs (reportedly they don’t).
I checked out the detailed standard and the glossary and found that the security code in the mag stripe (called variously the CAV, CVC, CVV or CSC) is used to protect the integrity of the stripe.
The CID, CAV2, CVC2 or CVV2 is the three digit code printed on the back of the card which ties the PAN to the piece of plastic.
They are quite different things, AND the only transactions affected were store (not online) transactions.
So, how did they get all these CVV2s? Or, did Target accidentally apologize to a far worse incident than what really happened?
Target’s initial disclosure was incorrect when it suggested CVV2’s were stolen. The current version only describes the code used in the magstripe (CVV1), and explicitly says *NO* CVV2’s were stolen. Since I already knew it was a magstripe breach from initial reports, I suspected the Target claim about CVV2’s was wrong from the beginning.
+1 to what RBB said. CVV2’s were *not* taken. Reports that say otherwise are wrong.
This is why I own multiple cards; if one gets frauded or stolen, I still have 4-5 other cards to live with.
Same thing when I travel: 1 card is on me for purchases, one in the hotel safe for backup, the rest stay home.
Also, have cards from all three main issuers, as sometimes Visa or MasterCard or (often) American Express isn’t accepted.
Breach could prove very costly for Target
Past major breaches cost TJX $250 million and Heartland $140 million; Target can expect similar costs, experts say
htxx://www.computerworld.com/s/article/9244900/Breach_could_prove_very_costly_for_Target?source=CTWNLE_nlt_security_2013-12-20
What an informative site. Can someone tell me whether banks have a legal obligation to reimburse customers whose debit cards have been used to make unauthorized charges to their checking accounts? Thanks!
Yes, as long as the account is not a commercial account type, they are protected by Regulation E.
Customers must watch their statement closely and report any Suspicious activity immediately in order to avoid liability, however.
If the customer is a credit card customer rather than a debit card customer, the protections tend to be far more complete.
What about cards that were read using the chip as opposed the magnetic strip. Are they able to clone the information on to blank chip cards?
Unfortunately, the real losers in this deal (besides Target, of course) are the banks that issued the cards.
Through no fault of their own, they have now incurred a very significant expense in writing off losses and reissuing all of the cards that fit the criteria for this compromise.
$3-5 per card adds up fast when you have to issue 100k of them, and the banks did nothing wrong.
I don’t understand why the industry doesn’t adopt a PIN-based system (like debit cards), where the PIN is used for transaction verification (like CVV2) and not stored. Wouldn’t this wipe out these continual problems?
It looks like in this case, that would not have helped either because the hackers apparently re-programmed the credit card swipe terminals. So even though a retailer doesn’t store PINs, the hackers programmed the terminals to send them the PINs anyway.
Seems like you should fix the Non-SSL assets on your site…
I know how these things work. “Turn and Burn”. People will attempt to use these up as quickly as possible. If you were compromised, it’s simple: draw out the cash you need for a week, call and cancel the card and request a new one.
Thanks for the excellent journalism!
I am unclear about the counterfeiting of credit cards. Are the crooks using stolen blanks or are they making their own? The cards are supposed to have anti-counterfeiting measures. Are those measures not working?
They can use either. If they can get the mag stripe data, they can encode it onto anything with a mag stripe that can fit through a card swipe reader. A while back, I wrote about thieves in Las Vegas who were encoding stolen card data onto hotel keys they’d found on the ground or in the trash at local resorts, because they knew getting caught with a bunch of credit cards looked bad, but maybe not so much with a hotel key.
http://voices.washingtonpost.com/securityfix/2006/03/street_level_credit_card_fraud.html
Many stores, including grocery stores and big box retailers, let customers swipe their own cards, and the cashier may never even see the card. At certain times of year and at certain stores they will ask to see the card, but even grocery stores sell prepaid cards of up to $200 now, so this is a very easy way to cash out stolen cards.
YIPPEE ! I just got back from my bank where I quickly canceled my old debt card and was issued a new debt card with a new number. I now solemnly swear to only use my cash back credit card for purchases and to only use my debit card for getting cash or making a deposit at an ATM located in a bank lobby or in a bank drive-thru.
Is it possible that a stolen credit card number in the Target breach could lead to identity theft? If I read the article correctly names of cities where the cards were used were also sold along with the card numbers.
Can stolen information be parlayed in some cases to get more information? Sure. Is it likely in this case? Not at all, IMO. The guys who are cashing out these stolen cards couldn’t give one iota about stealing identities; they just want to wring the maximum amount of each card in the shortest time possible. For those guys, it’s a race against the clock.
Also, I continue to see a lot of people conflate credit card fraud with identity theft. They are not the same thing. ID theft involves the creation of new accounts or synthetic accounts in someone else’s name, and is much, much more difficult, time-consuming and expensive for the average consumer to fully recover from.
Thanks for the info.
The reason I ask is that my wife has received several credit cards in the mail opened in her name that she did not apply for on 12/16. She did use her Visa several times since Thanksgiving at the local target. The cards were used in CA. We live in New England. When I saw the cards I put a security alert and credit freeze on her credit report on 12/16. Since then we have recieved 5 or 6 rejection letters from other companies when someone tried to open up a credit account.
The media is encouraging people to worry about identity theft, in some cases. A New York Times guide for Target shoppers, for example, says this:
Q. How do I monitor for identify theft?
A. While experts emphasize that a data breach and identify theft are different, Ms. Velasquez says that the former can increase your chances of the latter.
You can receive a free annual credit report from each of the three major reporting bureaus at AnnualCreditReport.com. You can also add a 90-day fraud alert to your credit file so creditors will know to take extra precautions before approving any credit applications.
— “For Target’s Shoppers, a New Holiday To-Do List,” http://www.nytimes.com/2013/12/20/business/for-targets-shoppers-a-new-holiday-to-do-list.html
For the non-debit Target Red Cards, the only way to use the data would be to create a physical card off of the redcard data, and use that physical card in a Target store? I would think that is a highly unlikely scenario, and it makes me feel just a little bit better about my card of that type (given that I can’t get any information about it with Target’s systems swamped). Target should probably start verifying the physical cards now going forward…
That’s true of Target stores, but unless clerks verify the card *ANY* magstripe card would do; fraudsters do that all the time. Also, the card number could be used at Target.com, though that could be foiled with a CVV2 requirement. (I don’t know if REDcard *credit* cards have CVV2’s, but my REDcard *debit* card has one.) The one saving grace is they can be used *only* at Target or its websites.
REDcard debit cards are actually a bit MORE secure in that regard, assuming no PIN or ACH breach; they require a PIN on *all* transactions, so you’d need a magstripe card *AND* PIN.
Brian,
Thanks again for your great reporting. You are always the “go to” source for issues on online security. We all respect you because you know what you are talking about and you don’t hype…you just give the facts. Thank you so much!
I wonder how long they will be performing all their forensic investigations? I am sure it will be a bit before we find out all the details. My suspicion is that they got through a backdoor with social engineering. Just a thought. Any thoughts on this that you are at liberty to share?
Have a great weekend! Scott
Found my credit card on rescator.la for $21. Needless to say, that card has now been deactivated.
Any details on *how* it was compromised?
I agree – HOW the heck was this compromised? I read about what happened after the fact. Why is there no mention of HOW it happened? Copycat fears?
The mag strip readers are merely input devices that connect to a computer. My guess is that the computers (which are in a network – as they have to transmit data) are likely unpatched (based on my experience with customers who have business leaders who demand 100% uptime and no time for security updates. Although these systems are not connected to the internet, other systems can access them. Once you compromise one system, you only need to revisit the Pacific theater of WWII.
While possible, that’s extremely unlikely. A business like Target wouldn’t have passed their PCI-DSS audits and scans had that been the case. And a business that large is required to undergo those audits – by an independent “Qualified Security Assessor” company, BTW – frequently, with the full audit being yearly and the system scans being quarterly.
Yes, your scenario is not impossible, but it would’ve had to have been a really, seriously freak occurrence, like a single system being brought online and the IT staff screwing up their security checklist before putting it into production. It definitely would not have been a systemic failure to patch systems, not for a Level 1 vendor, because that sort of problem would cause a big fail on the compliance checkup. The payment card industry takes these things seriously and would fine the bejezzus out of a merchant who blew it’s scan and audit that badly. Worse yet, payment card businesses could refuse to deal with them, and that would KILL their business for the time it took to get compliant again.
If that traced to an unpatched system, I’d be surprised. If it turned out that they had a systemic failure to patch systems, that I’d be shocked beyond belief. That would mean that it wasn’t only Target who screwed up, but also the QSA. And THAT would put the QSA in seriously hot, perhaps business-fatal water.
My card was compromised and my theft took everything I got and left me with $1.03 . I have absolutely nothing to buy for my family for the holidays, I have no money to buy food, gas or anything until we get this investigation settled. I am beyond furious upset and its not good for my unborn child. I don’t want to shop at target anymore. How can this happen to anyone at this time of the year.
At least you have enough money left to pay for web service.
But you at least still have your Duck Dynasty jammies, right?
Contact Target and tell them what happened. And your bank, I bet they can have money in your accounts within 24-48 hours. If you can’t survive that long without your credit cards then you made a mistake somewhere.
Unless you’re just a troll.
If someone used a Visa debit card, it is directly tied to their bank account. Telling her that she shouldn’t be relying on credit cards for her daily expenses is inaccurate. She may not even have a credit card. These crooks can clean out your whole bank account!
I think you’ll find that if you pay EMV enough, you can self-certify yearly.
Also, I’ve been through several PCI audits with different companies, and as a consutant, I find that I either have to keep silent or get fired. One big problem, as I see it, is that PCI auditors are at the mercy of in-house IT specialists when it comes to actually seeing what really exists.
I will say that while I’ve seen deception-by-omission, none of my clients have ever provided incorrect information to an auditor.
[quote]E.M.H.
While possible, that’s extremely unlikely. A business like Target wouldn’t have passed their PCI-DSS audits and scans had that been the case. And a business that large is required to undergo those audits – by an independent “Qualified Security Assessor” company, BTW – frequently, with the full audit being yearly and the system scans being quarterly.
[/quote]
Having worked in IT Security for about 10 years now… I can name many a customer who managed their own PCI Audits and pulled plenty of wool over the eyes of a “Qualified” SA, intentionally or not. Many of the QSA’s are there to collect a paycheck, fail to validate information provided and sometimes will let things slide because the evidence was obscure enough they didn’t dig further. Not to mention my favorite phrase, “Remediation list”, and its staggering scale of overlap to the “do not do this anywhere in the world unless you are a total moron” list.
Historical favorite examples from this list of overlaps… Some of these large organizations…
1. Organization running packet captures of the entire network outside of “normal business hours” to identify odd applications running. This organization ran a web front end from this network, and was capturing all data related to online transactions. Nightly captures were sent to an internal FTP. That FTP was also available over the internet, and with right credentials you could download those captures…
2. CC information being transmitted from 1 application to another over a “VPN” in plaintext. VPN had no encryption set for phase 2 and DES only for phase 1. Negotiation was also set to aggressive, so it might have well been unencrypted.
3. Organization tied to a large online shopping community with TONS of CC information passing through it… they ran a properly secured honeypot network at some point in time historically. Then someone moved the honeypot server to the wrong network, and the infections it contained… 2 years later someone noticed it…
All these customers were PCI-DSS compliant, and when discovered they were “Remediation Items”. Depending on if the QSA actually used his brain or eyes, these might have not even made it that far. PCI-DSS is starting to mean less and less. Hopefully these QSA’s and organizations requiring these standards will step it up with the adoption of PCI-DSS 3.0.
Most likely through sql injection.
I highly doubt it was SQL injection. This was clearly the work of a group that understands network vulnerabilities and intrusion.
They stayed undetected for quite awhile too. Since this was a MITM attack there is no doubt in my mind that the track data was being passed clear text inside the network.
It should have been encrypted at the device and left that way until it reached the gateway (external to target’s network).
Worse yet would be that it wasn’t clear text and the attackers found the decryption key on some servers, but that’s unlikely with how large Target is and complying with PCI audits.
Zero day vulns could be included too, hence going undetected for so long.