Credit and debit card accounts stolen in a recent data breach at retail giant Target have been flooding underground black markets in recent weeks, selling in batches of one million cards and going for anywhere from $20 to more than $100 per card, KrebsOnSecurity has learned.
Prior to breaking the story of the Target breach on Wednesday, Dec. 18, I spoke with a fraud analyst at a major bank who said his team had independently confirmed that Target had been breached after buying a huge chunk of the bank’s card accounts from a well-known “card shop” — an online store advertised in cybercrime forums as a place where thieves can reliably buy stolen credit and debit cards.
There are literally hundreds of these shady stores selling stolen credit and debit cards from virtually every bank and country. But this store has earned a special reputation for selling quality “dumps,” data stolen from the magnetic stripe on the backs of credit and debit cards. Armed with that information, thieves can effectively clone the cards and use them in stores. If the dumps are from debit cards and the thieves also have access to the PINs for those cards, they can use the cloned cards at ATMs to pull cash out of the victim’s bank account.
At least two sources at major banks said they’d heard from the credit card companies: More than a million of their cards were thought to have been compromised in the Target breach. One of those institutions noticed that one card shop in particular had recently alerted its loyal customers about a huge new batch of more than a million quality dumps that had been added to the online store. Suspecting that the advertised cache of new dumps were actually stolen in the Target breach, fraud investigators with the bank browsed this card shop’s wares and effectively bought back hundreds of the bank’s own cards.
When the bank examined the common point of purchase among all the dumps it had bought from the shady card shop, it found that all of them had been used in Target stores nationwide between Nov. 27 and Dec. 15. Subsequent buys of new cards added to that same shop returned the same result.
On Dec. 19, Target would confirm that crooks had stolen 40 million debit and credit cards from stores nationwide in a breach that extended from Nov. 27 to Dec. 15. Not long after that announcement, I pinged a source at a small community bank in New England to see whether his institution had been notified by Visa or MasterCard about specific cards that were potentially compromised in the Target breach.
This institution has issued a grand total of more than 120,000 debit and credit cards to its customers, but my source told me the tiny bank had not yet heard anything from the card associations about specific cards that might have been compromised as a result of the Target breach. My source was anxious to determine how many of the bank’s cards were most at risk of being used for fraud, and how many should be proactively canceled and re-issued to customers. The bank wasn’t exactly chomping at the bit to re-issue the cards; that process costs around $3 to $5 per card, but more importantly it didn’t want to unnecessarily re-issue cards at a time when many of its customers would be racing around to buy last-minute Christmas gifts and traveling for the holidays.
On the other hand, this bank had identified nearly 6,000 customer cards — almost 5 percent of all cards issued to customers — that had been used at Target stores nationwide during the breach window described by the retailer.
“Nobody has notified us,” my source said. “Law enforcement hasn’t said anything, our statewide banking associations haven’t sent anything out…nothing. Our senior legal counsel today was asking me if we have positive confirmation from the card associations about affected cards, but so far we haven’t gotten anything.”
When I mentioned that a big bank I’d spoken with had found a 100 percent overlap with the Target breach window after purchasing its available cards off a particular black market card shop called rescator[dot]la, my source at the small bank asked would I be willing to advise his fraud team on how to do the same?
CARD SHOPPING
Ultimately, I agreed to help in exchange for permission to write about the bank’s experience without actually naming the institution. The first step in finding any of the bank’s cards for sale was to browse the card shop’s remarkably efficient and customer-friendly Web site and search for the bank’s “BINs”; the Bank Identification Number is merely the first six digits of a debit or credit card, and each bank has its own unique BIN or multiple BINs.
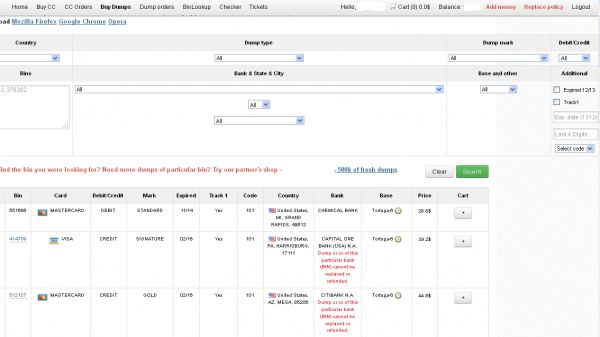
According to the “base” name for all stolen cards sold at this card shop, the proprietor sells only cards stolen in the Target breach.
A quick search on the card shop for the bank’s BINs revealed nearly 100 of its customers’s cards for sale, a mix of MasterCard dumps ranging in price from $26.60 to $44.80 apiece. As one can imagine, this store doesn’t let customers pay for purchases with credit cards; rather, customers can “add money” to their accounts using a variety of irreversible payment mechanisms, including virtual currencies like Bitcoin, Litecoin, WebMoney and PerfectMoney, as well as the more traditional wire transfers via Western Union and MoneyGram.
With my source’s newly registered account funded via wire transfer to the tune of USD $450, it was time to go shopping. My source wasn’t prepared to buy up all of the available cards that match his institution’s BINs, so he opted to start with a batch of 20 or so of the more recently-issued cards for sale.
Like other card shops, this store allows customers to search for available cards using a number of qualifications, including BIN; dozens of card types (MasterCard, Visa, et. al.); expiration date; track type; country; and the name of the financial institution that issued the card.
A key feature of this particular dumps shop is that each card is assigned to a particular “base.” This term is underground slang that refers to an arbitrary code word chosen to describe all of the cards stolen from a specific merchant. In this case, my source at the big bank had said all of the cards his team purchased from this card shop that matched Target’s N0v. 27 – Dec. 15 breach window bore the base name Tortuga, which is Spanish for “tortoise” or “turtle.”
Indeed, shortly after the Target breach began, the proprietor of this card shop — a miscreant nicknamed “Rescator” and a key figure on a Russian-language cybercrime forum known as “Lampeduza” — was advertising a brand new base of one million cards, called Tortuga.
Rescator even created a graphical logo in the Lampeduza forum’s typeface and style, advertising “valid 100% rate,” and offering a money-back guarantee on any cards from this “fresh” base that were found to have been canceled by the card issuer immediately after purchase. In addition, sometime in December, this shop ceased selling cards from other bases aside from those from the Tortuga base. As the month wore on, new Tortuga bases would be added to shop, with each base incrementing by one with almost every passing day (e.g., Tortuga1, Tortuga2, Tortuga3, etc.).
Another fascinating feature of this card shop is that it appears to include the ZIP code and city of the store from which the cards were stolen. One fraud expert I spoke with who asked to remain anonymous said this information is included to help fraudsters purchasing the dumps make same-state purchases, thus avoiding any knee-jerk fraud defenses in which a financial institution might block transactions out-of-state from a known compromised card.
The New England bank decided to purchase 20 of its own cards from this shop, cards from Tortuga bases 6-9, and Tortuga 14 and 15. The store’s “shopping cart” offers the ability to check the validity of each purchased card. Any cards that are checked and found to be invalid automatically get refunded. A check of the cards revealed that just one of the 20 had already been canceled.
The bank quickly ran a fraud and common point-of-purchase analyses on each of the 19 remaining cards. Sure enough, the bank’s database showed that all had been used by customers to make purchases at Target stores around the country between Nov. 29 and Dec. 15.
“Some of these already have confirmed fraud on them, and a few of them were actually just issued recently and have only been used at Target,” my source told me. Incredibly, a number of the cards were flagged for fraud after they were used to make unauthorized purchases at big box retailers, including — wait for it — Target. My source explained that crooks often use stolen dumps to purchase high-priced items such as Xbox consoles and high-dollar amount gift cards, goods that can be fenced, auctioned or otherwise offloaded quickly and easily for cash.
My source said his employer isn’t yet sure which course of action it will take, but that it’s likely the bank will re-issue some or all of the 5,300+ cards affected by the Target breach — most likely sometime after Dec. 25.
The bank is unconcerned that its cards compromised in the Target breach might be used for online shopping fraud because the stolen data does not include the CVV2 — the three digit security code printed on the backs of customer cards. Most online merchants require customers to supply the CVV2 as proof that they posses the legitimate, physical card for the corresponding account that is being used to fund the online purchase.
Update, 5:20 p.m. ET: In a message to consumers, Target CEO Gregg Steinhafel said Target would be offering free credit monitoring for affected customers. Not sure how credit monitoring helps with this specific breach, but at any rate here’s the rest of his statement:
“Yesterday we shared that there was unauthorized access to payment card data at our U.S. stores. The issue has been identified and eliminated. We recognize this has been confusing and disruptive during an already busy holiday season. Our guests’ trust is our top priority at Target and we are committed to making this right.
We want our guests to understand that just because they shopped at Target during the impacted time frame, it doesn’t mean they are victims of fraud. In fact, in other similar situations, there are typically low levels of actual fraud. Most importantly, we want to reassure guests that they will not be held financially responsible for any credit and debit card fraud. And to provide guests with extra assurance, we will be offering free credit monitoring services. We will be in touch with those impacted by this issue soon on how and where to access the service.
We understand it’s been difficult for some guests to reach us via our website and call center. We apologize and want you to understand that we are experiencing unprecedented call volume. Our Target teams are working continuously to build capacity and meet our guests’ needs.
We take this crime seriously. It was a crime against Target, our team members, and most importantly, our guests. We’re in this together, and in that spirit, we are extending a 10% discount – the same amount our team members receive – to guests who shop in U.S. stores on Dec. 21 and 22. Again, we recognize this issue has been confusing and disruptive during an already busy holiday season. We want to emphasize that the issue has been addressed and let guests know they can shop with confidence at their local Target stores.”
[EPSB]
Have you seen:
Non-US Cards Used At Target Fetch Premium”…An underground service that is selling millions of credit and debit card accounts stolen in a recent data breach at retail giant Target has stocked its virtual shelves with a new product: Hundreds of thousands of cards issued by non-U.S. banks that were used at Target across the United States during the retailer’s 19-day data breach. It’s not clear how quickly the non-U.S. cards are selling, but they seem to be fetching a much higher price than those issued by U.S. banks.
[/EPSB]






Every few weeks there’s news about a new breach of a website/retailers systems. Massive numbers of compromised credit cards etc. And the one thing that never surprises me is the fact that almost all of the compromised cards seem to be American.
Someone over there has got to make the banks move to Chip and Pin. It won’t stop card fraud but it’ll put a real crimp in the activities of the eastern European crims who seem to specialize in this. I’m guessing that banks are baulking at the perceived costs of moving to C&P but those sums are minuscule compared to the costs of a major breach. And those costs would, of course, be spread over a number of years- switch to C&P now and it should protect your bank, and your customers, for a number of years.
Of course such a move would remove quite a lot of Brians content but I figure he’d cope with that ( because there will still be lots of SME’s having their PC’s compromised and their bank accounts vacuumed)
Regarding CVV codes, major news sources are reporting that those numbers have also been compromised. For example, Boston Globe says ” three-digit security codes located on the backs of cards”. Can you confirm this?
http://www.bostonglobe.com/business/2013/12/19/answers-questions-about-target-data-breach/pN7ikzJzFWYhHtsFXHISeL/story.html
Unfortunately, the comments section of this post and the other one keeps going so fast that the answer to this keeps falling off the front page. No one’s fault.
Anyway: That story is in error. The “CVV” must be distinguished between the “CVV1” which is information encoded into the magnetic strip, and the “CVV2” which is that number the Globe is referring to.
Target confirms that the CVV1’s were stolen, but the CVV2s were not. And indeed they could not have been since they’re not part of the magnetic strip data.
Unfortunately, several sites on the internet and news organizations do not make this distinction, and therefore the information gets published with an error. The bottom line is that the CVV2s – the numbers printed on the backs of the cards – were NOT compromised. Stories saying they were are in error.
Oh, also: Brian himself mentions this in his last paragraph up above.
Hi Brian
Excellent article and investigation. Finally, someone shed some light on the subject. I am actually visiting the US on holiday, and woke up today to fraudulent activities on my bank account. Even though my bank has a great feature of sending an SMS text message every time there is a transaction on my card, it was too late by the time I saw the messages (I was asleep when my card got used). The credit card fraudsters had maxed out my credit card.
Turns out I am a victim of this mess, and to make things worse, it happens to be my birthday today. Oh, and the fraudulent transactions were made at – wait for it – Target. All New York Target stores too (Flushing, Valley Stream and Brooklyn). Been trying to call Target to tell them this in case it may be helpful, but haven’t been able to get a hold of anyone – I am sure they are being hammered with calls.
Here’s my question: Why don’t stores (especially Target, now that they know about this) check for IDs to match names on the credit card to names on an ID? I was angry about the fraud, but I understand these things can happen. However, what made me really angry is that this breach was caused at Target, they found out about it, and a day AFTER they acknowledged it on their website, my card information was used… AT TARGET!
Non-Target stores out in Colorado check for IDs when you use your credit card, and I appreciated that. That should be the norm. Don’t you think that, while this may not sort out or prevent breaches like this, it would make it much more difficult for people to use the fake cards?
Just a thought.
Thanks again,
-HQ
” Here’s my question: Why don’t stores (especially Target, now that they know about this) check for IDs to match names on the credit card to names on an ID? ” I am not the author of the advice listed below. The following advice is six years old but it still could be of some help:
A corporate attorney sent the following out to the employees in his company.
Do not sign the back of your credit cards. Instead, put “PHOTO ID REQUIRED”.
Place the contents of your wallet on a photocopy machine. Do both sides of each license, credit card, etc. You will know what you had in your wallet and all of the account numbers and phone numbers to call and cancel.
Keep the photocopy in a safe place. I also carry a photocopy of my passport when I travel either here or abroad. We’ve all heard horror stories about fraud that’s committed on us in stealing a name, address, Social Security number, credit cards.
Unfortunately, I as an attorney, have firsthand knowledge because my wallet was stolen last month. Within a week, the thieve(s) ordered an expensive monthly cell phone package, applied for a VISA credit card, had a credit line approved to buy a Gateway computer, received a PIN number from DMV to change my driving record information online, and more But here’s some critical information to limit the damage in case this happens to you or someone you know:
1. We have been told we should cancel our credit cards immediately. But the key is having the toll free numbers and your card numbers handy so you know whom to call. Keep those where you can find them.
2. File a police report immediately in the jurisdiction where your credit cards, etc., were stolen. This proves to credit providers you were diligent, and this is a first step toward an investigation (if there ever is one).
But here’s what is perhaps most important of all: (I never even thought to do this.)
3. Call the 3 national credit reporting organizations immediately to place a fraud alert on your name and Social Security number. I had never heard of doing that until advised by a bank that called to tell me an
application for credit was made over the Internet in my name. The alert means any company that checks your credit knows your information was stolen, and they have to contact you by phone to authorize new credit.
Now, here are the numbers you always need to contact if your wallet, etc., has been stolen:
1.) Equifax: 1-800-525-6285
2.) Experian (formerly TRW): 1-888-397-3742
3.) Trans Union : 1-800-680-7289
4.) Social Security Administration (fraud line): 1-800-269-0271
End of advice letter dated 2007. I called all of the numbers and they are still in service.
A friend has “photo id required” on his card. At the buffet in a local casino, he gave the clerk his c.c. and his i.d. She didn’t even look at the i.d. – because she thought it was a players club card and tried to scan it! Couldn’t figure out why the machine wouldn’t read it, so he had to explain to her what “photo id required” meant.
Yes, calling the credit bureaus is a good idea – if you believe information beyond a credit card is available to thieves. If they have your SSN, yes, they can try to apply for credit in your name. If they have your address they can try to intercept mail and/or change mailing addresses for things.
Not signing the back of credit cards is a terrible idea and just plain bad advice. The merchant rules for accepting credit cards say such cards are invalid and must not be accepted. The rules for checking secondary id other than looking at the card are very clear and basically asking for photo id is against the rules.
They don’t check ID because they have put in customer operated POS terminals to save time on checkout. Having the clerk take time to check the ID largely defeats that time saving measure. Many merchants apparently consider this more expensive in terms of labor than the losses incurred from not checking ID.
If a Target customer’s card # was stolen and used to buy five X-Boxes at Target for later sale on Ebay by the perp, guess who still makes money? Yes, Target! Yes, Microsoft! Yes, chip manufacturers! It is the job of the CC processor to reject a fraudulent transaction. And only a signature, not ID, is needed in most in-person CC transactions. The CC congloms may try to recoup their losses by suing the CC processors or Target, but I think this “Mega40″event is not zero sum. I think it is economy stimulating. Think of all the lethal forensicator billing hours!
The liability always lies with the merchant who accepted the card. The merchant agreement makes that very clear. When a fraudulent purchase is made someone – either the card issuer or the card holder – starts a chargeback process where the charge is rejected and a fee (the chargeback fee) is assessed against the merchant.
The problem is, all merchants have insurance for this, so it really costs them nothing. There is no incentive in the system to stop credit card fraud and it is never prosecuted.
No, all merchants do not have insurance for this. Few small businesses do.
Wrong. The charge will be charged back as fraudulent and the merchant (target) will eat it. If you don’t know that you don’t know enough to be posting on this subject.
I wish that stores would check ID or something more than they do now, but half the time I got to stores they don’t even require a signature for a credit card purchase under a certain dollar amount – not that they check the signatures most of the time anyway. But with that kind of set up at so many major stores (I won’t name any because I don’t want to get into trouble) it is not surprising that stores won’t check ID’s and that states and card issuers actually make it difficult for a store to do so if they even want to. While I am really angry about the Target breach (I have already cancelled my debit card but unlike a lot of you I wasn’t able to get a new card right away – smaller banks don’t do that I guess) I have to say that is one thing I have never found at Target – sure, they never look at my signature, but at least they still require it for smaller purchases (not that I am going to use a card at Target any time soon of course).
Everyone should realize it doesn’t matter if you sign or not.
They have the track data. They are going to create brand new cards with their fake ID name on it. Then they go into the store and pay with their shiny new card with your number on it, but their name on it.
It matches every time. Hopefully that helps out a bit with everyone confused about how this whole fraud thing works, and how it has nothing to do with signing your card.
What happens if one thief walks into the store with his fabricated CC with tracks he purchased from Rescator and at checkout it is found the CC number was already flagged for fraud and blocked ? Is he kept by security personnel until police arrives and the problem is clarified or he can just say “Oh sorry, probably my bank screwed-up again, here is another CC that should work.” ?
Not all non-Target stores in Colorado check ID’s. Without going into lengthy details, I caught a $965 purchase at Home Depot on my Amex card. Reported it. Soon after, a letter from Amex informed me that a firm that handles payments to merchants for online purchases reported that credit card information in their system had been hacked and that my card was one that was compromised. If Home Depot had checked the person’s ID, there would have been no fraudulent sale. Lazy rules and lazy employees contribute to this problem.
There is zero incentive for shops to do so, they do their sale and cash the commission, if they are too vigorous in fighting fraud they a) might be perceived as harassing customers with too many ID checks and b) say bye-bye to all the sales to their patrons that might just
“happen” to use a stolen CC.
Back home where I’m from, and actually in most countries outside of the US, one thing that has helped banks reduce fraud dramatically is using chip-enabled credit cards rather than magnetic strip cards. The chipped cards issue a unique code for every transaction, and is verified by a four digit pin number rather than signature. The reason behind the pin code is simple: everyone knows signatures are useless, and can easily be forged. Much harder to guess a four digit code, which is extremely hard to hack. I read somewhere that the US is moving to chipped cards by fall 2015.
I found my platinum credit card on cardshop.su for $3. It was working. Looks like cards on http://www.cardshop.su were the only ones still working.
The CVV2 rumor is false, media outlets are confusing the Cvv2 values withe CVV track data which is similar but not the same as the actual 3 digit code on the back of the card.
Also, EMV (Chip and PIN) cards are mandated to be used in the US by 2017 and even earlier for some transactions (fuel pumps, ATMs)
Kinda makes me want to go to target, load up a cart with a ton of small items from across the store go to the checkout, get it all rung up, whip out my card and go whoa, wait a minute, what am I thinking and leave…
But that is just punishing the little guy so… no…
But if millions did it…
Just saying…
Lulz…
Sinonymous:
“just saying”….. like an idiot?
With 40 million unhappy customers, I think Target has gotten the message loud and clear.
How about posting an IP address to this site, I have a couple of boxes of ammo I need to use.
Brian-
Thanks for all of your hard work. This article prompted me to call our bank today and they let me know that my wife’s card was compromised. They are working to alert folks but this will give us a jump on getting a new card and preventing theft. Happy Holidays to you and your family.
So how can rescator.la have a website, but is not a registered domain ??? I checked whois.net, etc. and none show who, or where they are.
Doing a reverse IP shows they have a server IN SAN FRANCISCO ????
Rescator – Rescator.la
Rescator IP: 108.162.202.124
Rescator server location: San Francisco
Rescator ISP: CloudFlare
IP Country: ip address flag United States
3 Hosts on this IP
Number Domain / Host Functions
1. paleorecipebook.com [Whois]
2. http://www.nx8.com [Whois]
3. http://www.jailbreakiphone5.co [Whois]
Registered through https://www.centralnic.com/
I found this through a whois lookup at dnsstuff.com.
Yes it’s a common technique used by legitimate people and also criminals to avoid DDOS (legitimate) avoid being found (criminals). Cloudflare hosts the incoming request and distributes traffic, then sends to the destination, which you won’t see.
Regardless the domain isn’t a TLD and is hosted offshore… won’t be shut down. But hopefully enough cards are cancelled now that people are aware so that the fraud is minimized.
If anyone bought mine, they wasted their money. I’m cancelling my current one and having a new one issued.
The registration for rescator.la shows an address down to a room number in Hong Kong. Has anyone just for kicks or otherwise visited the address to see who/what is there? I’m guessing it’s bogus or just a dropbox but who knows? Any info on what’s being done to trace the flow of $ via wire transfer for card info purchases to the destination?
It says, “Private Registration.” That’s just the forwarding address used by domainsproxy.net.
A Message from CEO Gregg Steinhafel about Target’s Payment Card Issues
http://www.abullseyeview.com/2013/12/ceomessage/
It’s mostly a new shine on the same old story. Two new things: (a) A 10% off discount this weekend and (b) free credit monitoring for “those impacted” (how will THAT be defined?), which will make the Facebook crowd cheer but won’t actually stop a magstripe breach like this.
One small thing: He says “just because they shopped at Target during the impacted time frame, it doesn’t mean they are victims of fraud”; yet the reports out there suggest almost *every* U.S. Target store was affected by the breach. He *still* just says “check your credit”, but if the reports are true *EVERY* card used during that timeframe was compromised (though REDcard impact may be limited), which should call for a cancel-and-reissue of *ALL* 40 million cards. If he KNOWS it’s less than 100%, why doesn’t he disclose HOW he knows that?
Until Target can (a) DEFINITELY identify WHICH cards were affected, preferably by explaining EXACTLY how it occurred (the CVV confusion is due to their OWN lack of proper explanation — first they said CVV2, *then* changed it to the correct CVV1), and (b) have ALL affected issuers (both Target *and* banks) cancel & reissue ALL affected cards, this story will NOT go away.
If they only stole in store transactions, then it would be impossible to harvest the CVV2, as it is not on the card and is not entered. If they did steal cards from online transactions, it is possible, but very difficult. In the online case, the thief would have to intercept the credit card data transaction to the bank, as per PCI rules (assuming Target follows them), the CVV2 code cannot be stored on any system. It should only exist in their systems for the duration of the transaction.
Bloomberg news is quoting an anonymous source “familiar with the investigation” that the “the breach occurred when a computer virus infected Target’s point-of-sale terminals.”
Take that with a grain of salt because so much of the media reports so far have been in some way inaccurate, but if true this has interesting implications for smart payment terminals. Sometimes low tech is better, maybe we should go back to making imprints of cards.
There is a report that in October 2013, a variant of the Dexter virus was modified to avoid detection and was recently active in South Africa. Dexter targets Track 1 and Track 2 credit card data on POS terminals and used botnet style communication to ex-filtrate the data.
http://www.techcentral.co.za/sa-banks-in-massive-data-breach/44338/
SecurityLedger reports that research into this malware pointed to a Russian using the handle “hgfrfv” is also linked to the e-mail addresses Mark.Jacobs@live.com and possible similarities to Zeus.
https://securityledger.com/2012/12/tantalizing-clues-in-dexter-malware-lead-to-mystery-man-and-zeus/
How about a further step back in time and go to a cash based society?
Maybe a step forward in time is better.
Something like: Credit card companies should issue phones, and everybody use phones to pay for products and services.
With regard to the use of zip code and city of the store where the credit cards were used, from the article:
“Another fascinating feature of this card shop is that it appears to include the ZIP code and city of the store from which the cards were stolen. One fraud expert I spoke with who asked to remain anonymous said this information is included to help fraudsters purchasing the dumps make same-state purchases, thus avoiding any knee-jerk fraud defenses in which a financial institution might block transactions out-of-state from a known compromised card.”
Note that with a customer’s credit card number and zip code, one can call the card company (I checked MasterCard today) and get the available balance on the card. One wonders if the miscreants behind this heist or the miscreants that purchase and use the stolen cards (banks and law enforcement excepted), will do this bit of research in an effort to identify those cards having the most potential value. If a card holder lives in the same zip code as the store or relatively close to the store, it wouldn’t take many attempts for the miscreants to uncover this additional information.
I hope that the credit card companies either add more requirements than the card number and zip code or that they monitor their system for multiple phone calls attempting to uncover the the balance for individual cards until the correct zip code is entered.
“Note that with a customer’s credit card number and zip code, one can call the card company (I checked MasterCard today) and get the available balance on the card.”
I believe they have an additional piece of information : they can tell if the call is from the main phone number registered with the account.
I just obtained a Citi MasterCard (from Citi, not from the underground 🙂
First of all, it is a chip card. Second, if you call you have to provide, in addition to card #, name and zip code, the password that you submitted when you applied for the account.
I’ve been reading a bit of Target’s facebook page. What a mess. Some people have been seriously impacted by this. I would like to see Target come out with a list of specific locations that were affected. They could save themselves and a few thousand people a lot of grief. Brian, if a person were a couple of weeks outside that window having used a card at Target, what do you think of that?
It is /ALL/ locations.
You know what im going to do !!!??? I know for a fact that my card numbers have been stoles in Target , so im going to spend all the money i have on that card .Then i will call my bank and tell them that it was compromised Yeeppe.Free gifts for everyone .
P.s If you ain’t first you’re last.
The Banks’ fraud departments are not as dumb as you seem to think. They’ll likely figure your scheme out.
The thing was an inside job – that is why the Secret Service is involved. It sounds like someone inside Target put “malware” on the main “push” server that pushes updates out to the card readers which basically “skimmed” off the card information for cards that were “swiped” on the card readers..
the secret service is involved because credit card fraud is their jurisdiction.
http://www.secretservice.gov/criminal.shtml
Why would they need to push a firmware update out to thousands of readers? The readers already read the card info and send it up the network to Target’s servers to be forwarded to to the banks. Presumeably the servers are infected, to intercept card data and forward it to the crooks.
Several people have posted that Target does not use the same manufacturer’s scanning devices in all stores. So it would be difficult to do something this comprehensive at the level of the scanners themselves.
Liberals are the DERP DERP ret@rds of IT. They are always developers and always deadly business ending SysAdmins.
The closer they are to reality, and away from their VM session- the closer they are to ending your company. You can NEVER trust a Liberal. Put that in your security manual. They will never accept the blame for what they’ve done, and they have no grasp of reality, much less morality.
I would bet that a developer, dba, or vertical app code monkey swiped those numbers.
Good or bad security has NOTHING to do with personal politics. Take your Tea Party extremism elsewhere.
Where is the NSA? Perhaps they could get some positive reviews if they just told us who is doing this, ya know they know, well come on NSA stop tracking teenage lovers and do some good.
Over the summer I was on Target’s website and my anti-virus notified me that a Trojan horse was blocked. They are creepy people. Now I want to cancel my Red Debit card but I’m having trouble getting through.
My daughter has read HAD a Discover card which she used during the wrong time at Target. Discover summarily cancelled the card without letting her know.
Will there be run on new bank cards?
Jag, I want you to read your last post on here and then call a hospital and check yourself in for mental evaluation, do this quickly as you have a severe personality disorder. My guess is you lost your first and many loves to a democrat or three when your girlfriends listened to your never ending diatribe of who??
Question: Target is saying I think this started Nov 15 is that FOR SURE the date.
Where are they giving the start date as Nov 15th?
I walked into a Target store today to finish up on some last minute Christmas shopping and I saw the security guard at the entrance as usual. It was kind of funny when you think about it; the banks and retailers will pay a guy or gal $5-6.00 an hour to deter theft their goods or money by customers, but spend very little to secure our financial information. I can understand why the retailers don’t care, but the banks, or credit card companies? How come they don’t patrol the underground to head off this kind of stuff? Oh yeah, when I went to Target it was with cash only.
Trunk Monkey:
You explained how much is spent on the ground for security protection at Target.
Please explain how much is spent on computing security at Target….. or are you on the tree trunk and talking out of your orifice closest to us, who are on the ground?
Credit monitoring does not help affected customers find fraud on their cards related to the breach, transaction monitoring does. Target should offer all affected customers BillGuard (http://billguard.com/), the #1 transaction monitoring app. Our free app has already identified fraud related to the breach and alerted hundreds of thousands of Target customers that shopped at retail stores during the breach window. If anyone has a contact at Target, please email me at ceo@billguard.com. Thanks!
Yaron Samid
Founder & CEO
BillGuard
Yaron, people who advertise their companies by posting about them in comment sections look really desperate. It’s not a good way to get your name out there.
Yaron: (of billguard.com)
I agree with Anon, you sound desperate.
If your product is as good as you indicate, I would assume you have industry contacts already, without needing to troll a comments section.
Plus, a good computer sleuth should be able to find the contacts on the Internet rather easily. (hint: you are showing your lack of skills)
Dear anonymous people — I believe in the power of crowds and have never been ashamed to ask for help publicly, especially when I can help others. I’m sorry you consider that desperate. I consider trolling an important comment thread anonymously lame, but its your right.
We would like to help the cardholders affected by this data breach, for free, with the crowd-powered technology we’ve built specifically for this purpose, but have yet to get a response from Target. If someone reads this and one more person gets protected, it would certainly be worth being perceived as desperate for putting the offer out there.
Good for you Yaron! That is my primary mission on forums as well. I never charge my clients unless they insist on paying – most of them are indigent, and I do not ask for money, as that should be considered an insult to good people. I am not a communist; this is just something I personally do to help defeat crime as well as I can. It is one of my favorite pastimes!
Target won’t contact you because you posted here. You need to find a different way to connect with potential customers. Advertising your wares in comment sections is akin to posting spam, and it doesn’t look professional at all.
LMAO You are going to protect my cards but can’t figure out how or who to contact at target to That’s funny.
Target insists on running your drivers license when purchasing alcohol.Were the licenses breached and what information was obtained?
I go to Walmart, so no concern. I suspect this breach was due to the UNIONIZED people at Target.
Thank you for that comment, how much did the tea party pay you to post that crap?
If our country can hack into the networks of other countries for spying purposes, why can’t we hack into these card shops and take them down? If you don’t want the government to do it, why don’t banks and their commercial customers start their own hack warriors to take these card shops down? If Anonymous is so pure in its intentions why doesn’t Anonymous do something positive for society and help take these card shops down and identify publicly who is running them and from what country that are allowed to operate.
PC
Does PC stand for
Politically Correct
or
Pure Crap
America has LAWYERS to sue ANYBODY who takes any kind of action! Whether it be for illegal reasons, righteous reasons, or for no reason at all!
Or, why doesn’t the NSA locate the card shops and send in the drones?
Why do you assume that websites setup by cyber criminals intimately familiar with hacking are easy to hack? What exception in US federal law permits the hacking of websites because the hacker asserts they are engaged in illegal activity. Finally, you do realize that many of these sites are run by organized crime including Russian organized crime. If they sell a block of one million card numbers for the low price of $20 a number that’s 20 million in revenue just on that batch. The cost to have a pro put 3 or 4 rounds in the back of a hackers head to set an example runs around 10 – 15K. Mess with OC at your own peril.
Brian- Great job breaking and covering this story! It will be interesting to see how this all plays out. Your website made Warrior’s list of Top Ten Websites Of 2013 – Here’s the link –
http://www.cyclopswarrior.blogspot.com/2013/12/warriors-top-10-websites-for-2013.html
Keep up the great work!