An examination of the malware used in the Target breach suggests that the attackers may have had help from a poorly secured feature built into a widely-used IT management software product that was running on the retailer’s internal network.
As I noted in Jan. 15’s story — A First Look at the Target Intrusion, Malware — the attackers were able to infect Target’s point-of-sale registers with a malware strain that stole credit and debit card data. The intruders also set up a control server within Target’s internal network that served as a central repository for data hoovered up from all of the infected registers.
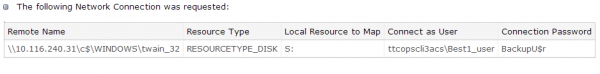
“ttcopscli3acs” is the name of the Windows share used by the POS malware planted at Target stores; the username that malware used to upload stolen card data was “Best1_user”; the password was “BackupU$r”
That analysis looked at a malware component used in Target breach that was uploaded to Symantec’s ThreatExpert scanning service on Dec. 18 but which was later deleted (a local PDF copy of it is here). The ThreatExpert writeup suggests that the malware was responsible for moving stolen data from the compromised cash registers to that shared central repository, which had the internal address of 10.116.240.31. The “ttcopscli3acs” bit is the Windows domain name used on Target’s network. The user account “Best1_user” and password “BackupU$r” were used to log in to the shared drive (indicated by the “S:” under the “Resource Type” heading in the image above.
That “Best1_user” account name seems an odd one for the attackers to have picked at random, but there is a better explanation: That username is the same one that gets installed with an IT management software suite called Performance Assurance for Microsoft Servers. This product, according to its maker — Houston, Texas base BMC Software — includes administrator-level user account called “Best1_user.”
This knowledge base article (PDF) published by BMC explains the Best1_user account is installed by the software to do routine tasks. That article states that while the Best1_user account is essentially a “system” or “administrator” level account on the host machine, customers shouldn’t concern themselves with this account because “it is not a member of any group (not even the ‘users’ group) and therefore can’t be used to login to the system.”
“The only privilege that the account is granted is the ability to run as a batch job,” the document states, indicating that it could be used to run programs if invoked from a command prompt. Here’s my favorite part:
“Perform Technical Support does not have the password to this account and this password has not be released by Perform Development. Knowing the password to the account should not be important as you cannot log into the machine using this account. The password is known internally and used internally by the Perform agent to assume the identity of the “Best1_user” account.”
I pinged BMC to find out if perhaps the password supplied in the Target malware (BackupU$r) is in fact the secret password for the Best1_user account. The company has so far remained silent on this question.
This was the hunch put forward by the Counter Threat Unit (CTU) of Dell SecureWorks in an analysis that was privately released to some of the company’s clients this week.
“Attackers exfiltrate data by creating a mount point for a remote file share and copying the data stored by the memory-scraping component to that share,” the SecureWorks paper notes. “In the previous listing showing the data’s move to an internal server, 10.116.240.31 is the intermediate server selected by attackers, and CTU researchers believe the “ttcopscli3acs” string is the Windows domain name used on Target’s network. The Best1_user account appears to be associated with the Performance Assurance component of BMC Software’s Patrol product. According to BMC’s documentation, this account is normally restricted, but the attackers may have usurped control to facilitate lateral movement within the network.”
According to SecureWorks, one component of the malware installed itself as a service called “BladeLogic,” a service name no doubt designed to mimic another BMC product called BMC BladeLogic Automation Suite. BMC spokeswoman Ann Duhon said that the attackers were simply invoking BMC’s trademark to make the malicious program appear legitimate to the casual observer, but it seems likely that at least some BMC software was running inside of Target’s network, and that the attackers were well aware of it.
Update Jan. 30, 5:48 p.m.: BMC just issued the following statement:
There have been several articles in the press speculating about the Target breach. BMC Software has received no information from Target or the investigators regarding the breach. In some of those articles, BMC products were mentioned in two different ways.
The first was a mention of a “bladelogic.exe” reference in the attack. The executable name “bladelogic.exe” does not exist in any piece of legitimate BMC software. McAfee has issued a security advisory stating that: “The reference to “bladelogic” is a method of obfuscation. The malware does not compromise, or integrate with, any BMC products in any way.
The second reference was to a password that was possibly utilized as part of the attack, with the implication that it was a BMC password. BMC has confirmed that the password mentioned in the press is not a BMC-generated password.
At this point, there is nothing to suggest that BMC BladeLogic or BMC Performance Assurance has a security flaw or was compromised as part of this attack.
Malware is a problem for all IT environments. BMC asks all of our customers to be diligent in ensuring that their environments are secure and protected.
I parse their statement to mean that the “BackupU$r” password referenced in the Target malware is not their software’s secret password. But nothing in the statement seems to rule out the possibility that the attackers leveraged a domain user account installed by BMC software to help exfiltrate card data from Target’s network.
Original story:
According to a trusted source who uses mostly open-source data to keep tabs on the software and hardware used in various retail environments, BMC’s software is in use at many major retail and grocery chains across the country, including Kroger, Safeway, Home Depot, Sam’s Club and The Vons Companies, among many others.
A copy of the SecureWorks report is here (PDF). It contains some fairly detailed analysis of this and other portions of the malware used in the Target intrusion. What it states up front that it does not have — and what we still have not heard from Target — is how the attackers broke in to begin with….
HOW DID IT HAPPEN?
The folks at Malcovery (full disclosure: Malcovery is an advertiser on this blog) have put together a compelling case that the avenue of compromise at Target stemmed from an SQL injection attack. Malcovery notes that techniques that may be similar to the Target breach were used by the Alberto Gonzalez gang, as illustrated in an indictment against Vladimir Drinkman, Aleksandr Kalinin, Roman Kotov, Mikhail Rytikov, Dmitriy Smilianet (see Hacker Ring Stole 160 Million Credit Cards for more information on these guys).
As that report notes, Drinkman and his associates were co-conspirators of Albert Gonzalez (famous for the TJX breach), Damon Toey, and Vladislav Horohorin (BadB). Drinkman and his gang of Russian hackers were active from at least August 2005 through at least July 2012 and were charged with stealing data from NASDAQ, 7-Eleven, Carrefour, JCPenney, Hannaford Brothers, Heartland Payment Systems, Wet Seal, Commidea, Dexia Bank, JetBlue Airways, Dow Jones, an unspecified bank in Abu Dhabi, Euronet, Visa Jordan, Global Payment Systems, Diners Singapore (a regional branch of Diner’s Club), and Ingenicard.
Malcovery’s CTO and co-founder Gary Warner writes:
“In each of these cases, an SQL Injection attack resulted in malware being placed on the network and credit card or personal information being exfiltrated from the network. According to the indictment for the above, Gonzalez and Toey would travel to retail outlets and make observations about which Point of Sale terminal software was being used, afterwards, they would pass the information to the hacker crew who would penetrate the network, customize and load the malware, and exfiltrate the stolen data.”
A copy of the Malcovery report can be downloaded here.
EAGLE CLAW, RESCATOR, AND LAMPEDUZA
Meanwhile, the cybercrook known as Rescator and his merry band of thieves who are selling cards stolen in the Target breach continue to push huge new batches of stolen cards onto the market. In an update on Jan. 21, Rescator’s network of card shops released for sale another batch of two million cards apparently stolen from Target, a collection of cards which these crooks have dubbed “Eagle Claw.”
Working with several banks anxious to know whether this batch of two million cards really was from Target (or else some other recent breach like Neiman Marcus), we were able to determine that all of the cards purchased from Eagle Claw were used at Target between Nov. 27 and Dec. 15. The method behind that research was identical to that used in my previous research on this topic.
Incidentally, anyone who wants to understand the hierarchical pecking order of Rescator’s crew should check out this analysis by security researcher Krypt3ia, which examines the Lampeduza cybercrime forum of which Rescator is a leading member.
Anyone hoping that this retail breach disclosure madness will end sometime soon should stop holding their breath: In a private industry notification dated January 17 (PDF), the FBI warned that the basic code used in the point-of-sale malware has been seen by the FBI in cases dating back to at least 2011, and that these attacks are likely to continue for some time to come.
“The growing popularity of this type of malware, the accessibility of the malware on underground forums, the affordability of the software and the huge potential profits to be made from retail POS systems in the United States make this type of financially-motivated cyber crime attractive to a wide range of actors,” the FBI wrote. “We believe POS malware crime will continue to grow over the near term despite law enforcement and security firms’ actions to mitigate it.”





I believe the J Jonah Hameson laugh is appropriate to this revelation.
http://www.youtube.com/watch?v=lhckuhUxcgA
What a great read! Fantastic links to the dell report and the write-up on Lampeduza. The dell report is fascinating in its detail and really throws a bright light on how this was done.
The mitigation ideas from the detail will help me setup the appropriate defenses I need to protect what I can.
Thanks again Brian! The best part of my day is catching up on your latest work.
SecureWorks has always done a really good job on analysis, even before they were bought by Dell. One of my previous employers outsourced their firewall and IDS to SecureWorks and they did an excellent job of managing the devices and keeping us informed of what was happening on our network. I had to explain some of the more technical things to our VPs, but most of it was very will explained.
Dell took over after I left that job, so I can’t say if things are better or worse, and I don’t have the same access to the reports that Brian had, but from what I’ve seen from their blogs and the reports that have been posted publicly, the analysts are still top notch.
Brian,
Don’t know if it matters, but I have seen 2 news reports on this subject today. Fox National news said that a vendor was the actual cause of the breach, and one of our local stations where I am also said the same. As you and I know, the root cause of the breach has not been devolved, but the vendor issue was regarding how the attackers off loaded the data. Just thought you would want to know that some news outlets are misunderstanding or misinterpreting your story.
The reporters need to read the Dell document Brian posted.
PLEASE GIVE US UPDATED INFO ON RELATED TARGET BREACH RE: HAPPENING THROUGH VENDORS
PLEASE DON’T SCREAM ON MY BLOG.
Thanks.
Brian -Great blog. Besides NM is anyone guessing who the other retailers are that may have gotten hit when Target did?
Kevin
Kevin, etc: now days, all retail is suspect, even if the other three aren’t yet known, esp. now with the motel hacking. If travelling : cash or Am Ex blue bird (prepaid) or bank prepaid Visa cards. Ditto for gas cards prepaid. I’m through with debit cards, “mothballed” mine indefinitely. I use a grocery prepaid card and Walmart prepaid, checks for monthly bills. If this country has no laws on hacking, retail security and no chip cards like other countries have, I view this country a third world dysfunctional mess run by scum loser politicians who can’t get us into the twenty first century,and can’t be trusted.
Brian,
(Total stalking horse comment) – Wouldn’t it be nice to see all of the SQL traffic going to all of the interesting databases and be able to pick out the “bad” SQL based on behavior modeling?…:-)
– Stuart
Yes, to some extent it’s called “writing secure code”. Although it’s hard to prevent eveything, this doc is a good start:
https://www.owasp.org/index.php/SQL_Injection_Prevention_Cheat_Sheet
Secure code is the answer. Also the holy grail. Way too many parts in motion to ever perfect code, for a whole variety of reasons.
Watching all of the traffic and calling out the bad actors is the play, IMO.
– Stuart
Thanks for the pointer W Sanders. Interesting article. On that same site I found they list SQL injection (and other forms of injection) as their top threat.
https://www.owasp.org/index.php/Top_10_2013-Top_10
This is very fine work Mr. Krebs. You are covering a fascinating story here. The details are intriguing. Keep up the good work.
The problem with your posts are people take it as fact even though it is mostly speculation.
Even your last edit is dishonest.
“But nothing in the statement seems to rule out the possibility that the attackers leveraged a domain user account installed by BMC software to help exfiltrate card data from Target’s network.”
So you are saying because they didn’t mention X, then X could be true. It is dishonest at best, and malicious at worst.
That’s what words like “seems” (and your “could”) are for. Someone who misinterprets it needs to work on their basic comprehension skills.
Because the default user account created by their software was used by the malware, therefore the default user account created by their software was used by the malware.
Assuming that’s not the default password they used (a certain level of suspicion must be maintained for anyone depending on security through obscurity), then someone changed the password on it. Either Target or the miscreants. And gave it sufficient privileges to accomplish the required tasks. Again could be either target or miscreants.
However, the account their software creates was clearly the account the miscreants used.
Yes, speculation, but one needs to speculate to read between the lines. For example, as mentioned, the users that was involved with the exfiltration, authenticated with target’s internal domain, and had the name of a well know BMC user account.
It seems the user account password was changed, and since it’s function is logon as batch job, it could easily move data.
The password could have been changed by the attackers after they obtained admin credentials elsewher.
The Best1_user account does not generate that password by default. The password was created by the hackers. Aside from the statement by BMC, I think it’s important to understand that the software in question is capacity management software, not backup software. Even if someone was dumb enough to use a default password and attempt to hide it with obfuscation, why would they use one that had anything to do with backups? Anyway, the press release from BMC is below.
http://www.bmc.com/news/press-releases/2014/BMC-Software-Comments-on-Speculation-Concerning-the-Target-Breach.html
What is likely is the hackers commandeered that account as a way to hide what was going on for as long as possible, and changed the permissions as well as the password of the account so they could do the transfer. They probably figured that a password like BackupU$r would lead the sys admins to believe it was some kind of backup software that was supposed to be running…
Brian,
As Diana “screamed” and TheHumanDefense noted, do you have any intelligence supporting recent news reports suggesting the breach was due to a vendor of Target’s?
Thanks for your continued efforts and appreciate any comments relative to the above.
Just to be clear on my previous post, and to clarify for those who have commented about point of entry on this breach.
Brian has rarely been wrong and I believe he has his finger on the pulse of this situation, this I am certain.
When sitting in front of an organizations CISO, you must be able to say with complete certainty that a situation is confirmed. My point is this “The folks at Malcovery (full disclosure: Malcovery is an advertiser on this blog) have put together a compelling case that the avenue of compromise at Target stemmed from an SQL injection attack”.
A compelling case indeed, and more then likely correct. However, it is a compelling case. Until it is confirmed that this is the case, I was merely stating that it is speculative.
The point of entry, at a 100% level of certainty has yet to be sustained.
I look forward to further details and I believe that the retailers are now talking, and hopefully sharing defensive measures to further protect their customers. I believe, this blog was absolutely why that would have happened.
Hi Brian,
Would it be possible for you to host a copy of the Malcovery report on your domain or somewhere else.
I tried to subscribe to their service, but, it won’t take a gmail account as an “official” work Email. Well – Some of us do actually use gmail as our primary work Email. Sheeesh! Talk about paranoia! Or is it that they want to make sure they can spam me at will?
Thank you!
-b
You’re getting warm. Target, Hannaford and a host of other security breaches are the result of mis-configured internal security. This is from decades old message oriented middleware systems that are considered “plumbing” by the security community. These sophisticated and targeted breaches are occurring “in spite” of perimeter security being in place. Tese POS systems use a service oriented architecture (known as SOA) which includes message oriented middleware and enterprise services buses. This concept is used by IBM, Amazon, MS, Tibco and Oracle to implement POS systems. I did over 5 years of research in conjunction with UWA to show that over 90% of middleware across the globe is underwhelming insecure. Over $500 quadrillion (that’s 50x U.S. GDP) flow through middleware annually making it low hanging fruit for hackers. BMC Patrol is supposed to monitor these systems on the AS400 for the POS applications. It doesn’t collect any security metadata, it just uses alerts that are not useful to identify rogue users or relate security issues to NIST CVEs. In order to “stop” these hacks, companies have to actually have eyes on the message queuing security controls and look at administrative access, encryption, auditing and version issues. See http://www.security4soa.com for more details.
> 5 years of research in conjunction with UWA to show that over 90% of middleware across the globe is underwhelming insecure.
can you provide a link to that reference?
TIA
Chewy? Looks like RSA found a POS trojan bot:
https://blogs.rsa.com/rsa-uncovers-new-pos-malware-operation-stealing-payment-card-personal-information/
Kinda curious that under the mitigation suggested, no mention of blocking the startup folder is mentioned. But then this whole thing of poor standards is just getting to be a joke anyway.
In none of these incidents, is it clear to me just how the malware gets on the server in the 1st place; but then I haven’t followed a lot of the links that have been provided by Brian in other here on the discussion.
It would seem that Target would increase security across the board as a result of the breach. Over the last two weeks jobs have been posted on Field Nation to replace memory and hard drives of POS systems at local Target locations. These jobs do not require a background check and ask that the technician pick up the new memory and hard drive at a UPS Store, drive it to the store, and then remove old memory and hard drives from in store systems. Once the job is complete the technician then is tasked with packing up the old memory and hard drive for drop off at the UPS Store. I look at these job postings and wonder what type of security is in place to ensure there is no tampering of the new drives or imaging of the old.
Europe starting rolling out chip-and-PIN, what, 15 years ago. Not only have they seen a long-lasting drop in card fraud, it means I can be reasonably confident that when I insert my card into a PoS terminal, it’s not going to be cloned -irrespective of how broken the shop’s IT infrastructure is.
Criticisms of the tech as expensive are misplaced: think how much target will lose from this, and think how much the credit card companies will lose once people switch to paying by cash. Which I’ll be doing the next time in the US.
The only alternative would be NFC, but that is so politicised, with everyone wanting a slice of the data, not just the money: card companies, phone manufacturers, phone app authors, mobile telcos, and then the shops themselves. A solution there will only come if they are told to get their act together by an organisation with power.
Who is going to be next? And when are the shops, banks and card companies going to go beyond elastoplast fixes to “one off security breaches” and go so for some solutions that address the root cause: secrets being made visible to easily subverted PoS terminals.
I don’t see many who say EMV is totally ineffective. I did say it was not cost-effective, not easy to use, and had been compromised (and more, see original post reference below), points not refuted. Don’t get me started on NFC here, see the link below.
Criticism of those who say “tech as expensive” by comparing it to the cost of breaches in general, and the Target breach in particular, sets up a logical fallacy. In the US (“the colonies”) this is called a “Straw Man”. In the United Kingdom it is more commonly known as an “Aunt Sally”. I call it comparing apples to oranges, a specious comparison that does not inform, but misleads readers, blinding them to even awareness of other alternatives that may be more beneficial. It is like comparing the cost of seat belts to the cost to the medical bills due to an automobile crash. The better comparison is the effectiveness and cost of seat belts to 6+ airbags; a comparison of one protective system versus another protective system.
There is little doubt that the high cost of EMV implementation is cheap compared to the even higher cost of breaches. Yet, the cost of EMV is expensive compared to _other forms_ of effective protection.
Any protective service can be breached, if not today, then on some tomorrow. Knights in “invincible” armor fell to crossbows, the “unsinkable” RMS Titanic fell to hubris in design and an errant iceberg, the
NASA Orbiter OV-099, the Challenger, fell during mission STS-51-L due to the failure of a protective O-ring that hadn’t ever been tested at the environmental temperatures present at launch. The list is sadly lengthy, a testament to Santayana’s “Those who cannot remember the past are condemned to repeat it.”
Given all of the above, the public, starting with you, should consider a change of direction. For the purpose of transactional commerce security, look forward past locks and vaults as protection of vital data and consider not having the data there at all. Simply and logically: If the data isn’t there then it can’t be stolen from there. Merchants get paid, consumers get billed, ease of use for consumer and merchant goes up, costs are low (compared to EMV, and especially to a breach ), and with myriad other benefits, there is at least one alternative to EMV. It, and others, should be considered before embracing a system that has been compromised several ways in the past.
Just because we’ve always done it that way before does not mean we should do it that way again.
Jonathan
The original post was
http://krebsonsecurity.com/2014/01/new-clues-in-the-target-breach/comment-page-1/#comment-226623
What is a Straw Man argument?
http://en.wikipedia.org/wiki/Straw_man_argument
In the UK the argument is called an “Aunt Sally”
http://en.wikipedia.org/wiki/Aunt_Sally#Other_kinds_of_Aunt_Sally
Problems with NFC
http://nc3.mobi/references/#NFC
The Life of Reason, The Phases of Human Progress, written in five volumes by George Santayana
The quote can be found in Volume 1, I think the 7th paragraph from the end
http://www.gutenberg.org/files/15000/15000-h/vol1.html
To read the whole book start here http://www.gutenberg.org/ebooks/15000
The Seven Deadly Words of Management are actually
“We’ve always done it that way before.”
People keep bringing up EMV as the obvious solution. How about simply encrypting the track data at the read head? Encrypting card readers are readily available.
That changes the hackers target (no pun intended) from thousands of POS terminals, to a small set of hosts and HSM’s in the core of a merchant’s data center. The smaller target is far easier to protect.
One wonders how far the track data was transmitted in Target’s systems before it was encrypted, and how it was determined to be PCI compliant.
Hans – Encrypting plain text material at the scanner’s read head is a good idea and would have defeated the exploit used at Nordstrom. It would _not_ have defeated skimmers that read the magnetic strip BEFORE it gets to the real scanner such as those used at ATMs. See below.
Jonathan
Nordstrom
http://krebsonsecurity.com/2013/10/nordstrom-finds-cash-register-skimmers/
ATM Skimmers
http://arstechnica.com/security/2013/02/how-alleged-crooks-used-atm-skimmers-to-compromise-thousands-of-accounts/
and a good backgrounder
https://krebsonsecurity.com/all-about-skimmers/
I thought these comments were in relation to the above article on the Target breach, and similar ones, not ATMs.
From what we’re told, the Target breach appears to have been caused by skimming plain-text track data in the memory of a POS terminal. Remove the plan-text, and the problem is greatly minimized. Don’t forget to manage encryption keys well.
All this talk of technology, encryption that and SOA this and put a chip in the card and it all goes away.
Lets get back to basics in thinking about security in a none complex, none technology will cure it, the silver bullet is technology.
Hundreds of million of dollars spent on security technology over the last 2 or 3 years, and what???????? What has it done??????? Every get into a fight and pull out a collapsible police baton, but you never were trained how to use it? The attacker now takes the baton cuz you exposed yourself, and beats the holy hell out of you? Just think about that.
The attackers are using our own technology against the security teams…….why?? Because they have holes in them….so why not grab it and beat the holy hell out of the security team with their own weapons.
Lets get back to training people to develop code with more then functionality in mind and time to market.
Train security teams to be more focused on what tools don’t we need any longer because there is too much noise in our logs.
Lets get back to showing people how easy it really is to just simply follow a standard that says “Installation Procedure” Item 1. Once device is connected to network, update username and change the password to a 26 character passphrase following a guide line that looks like this xxxxxxxxx (whatever fits your needs)
Lets get back to helping employees see the value in a strong security procedure, policy and standard and have them start helping the security teams fight the fight
Read all the analysis of the most recent breaches, and think from a perspective of “where was there a human touching this” and you’ll find a human factor in almost all of it.
How do you stop a basic SQL injection??? Knowing how to code against it
How do you defend against the guessing of a password in an appliance???? Understanding why longer is better through the use of pass-phrasing and demonstrating this and combining this with dual authentication is stronger
How do you find the insider threat? Start showing managers and those in charge what behaviors are found as common denominators in these people. Ask anyone who has been a victim of the insider threat, and they will point out at lease 3 red flags. Most of the insider threats are not some sleeper cell that shows up like 007 in the night. They are a person who has decided to wake up and step over the line one day. This is either because someone has offered them a deal, threatened them with extortion or harm, drug and or alcohol problem, or just simple revenge.
Lets just start getting back to the human side of defense. My house alarm doesn’t do me any good if all it does is make a loud sound and turn on lights, when the average burglary takes less then 3 minutes to snatch and grab….why? Because they know that when the alarm goes off it might take at minimum a 3 minute response time for law enforcement. Take what you can and get out. But, what if now I throw in my German Shepard (600 lbs per square inch of bite strength), closed blinds so they cannot see what I own, not letting any strangers into the house to see what I have. Avoiding the convenience of a cleaning person and doing it myself. If a stranger does come over, let them see the large barking beast. No dog? Keep large dog dishes out when strangers have to come in, keep them on your back patio so when they look over the fence “Oh, big dog….where…I don’t see it…not gonna try…move on”
Not saying I’m right, not saying it’s the silver bullet….there isn’t one….just saying, please, I beg you all to stop thinking technology is the only response here. Chip cards cracked time and time again, encryption cracked but it’s really about the amount of time they want to spend on decryption, morphing viruses so the signature isn’t identified (by the way, this is done by re-coding the virus, a human does this).
Just wanted to through some food for thought….what’s the risk in that? None, really
You wrote well, bit of a rant and Dennis Miller would be proud.
As for building up the human side of defense, it certainly would help, but only so far. “The best defense is a good offense.” *1 We don’t really punish spammers, yet they cost our economy billions in resources consumed, unfathomable people-hours in deleting, etc. How do we punish cyber-miscreants who hack, crack, take, then sell valid charge card data? What does it cost to even catch them? Big bucks and what is the catch percentage? The conviction rate? The average sentence? I’ll wager a nickel it isn’t enough to pay for the damage caused or the prosecution expense. If retribution (ok, justice) isn’t an effective deterrent, and we can’t take offensive (you know, pre-emptive self defense) then consider an effective countermeasure, the simplest, most cost effective one available.
Writing secure code is a grail pursued by many, but what one can design another can crack. Consider shifting direction from expensive, ineffective, barrier creation to mis-direction and psychological warfare. Remove the goal of the crooks by making it simply not there. What isn’t there can’t be taken. Or:
If crooks are going to crack the vault,
why put jewels in there in the first place?
As long as the system works within existing communication and transaction infrastructures (low barriers to adoption), the merchant gets paid, the consumer gets billed, and the treasure (consumer credentials) are not ever (ever!) at the merchant in plain-text or common-encryption form, the information isn’t there so it can’t be compromised, today, tomorrow or the foreseeable future.
Think on it.
Jonathan
*1 – don’t know who wrote that first. There are sources for Sun Tzu, Machiavelli, Mao Zedong and a whole lot of football coaches.
Since it’s my primary area of interest (SQLi), I’ll say that coding against it is the right answer. But our experiences in this space indicate that it’s not possible, effectively, to make application code bullet-proof, especially in more complex environments. Also, even if the application code was, in fact, bullet-proof, it doesn’t fix a host of other holes, such as zero-day attacks/vulnerabilities in 3rd-party libraries (and there are many of these and legendary). So we believe that looking at every unique SQL statement from the applications to the databases – while watching the wire in front of the databases – is the key, and alerting on those that don’t fit normal application behavior. That’s the behavior modeling approach, and it’s extremely effective.
– Stuart
Hi Brian – In your caption under the first picture, “ttcopscli3acs” refers to a domain or computer name, not a share name.
Don’t use a system for secure fin. transactions that shares a code base with a consumer product. Bitcoin has eliminated the need for money mules. Use pre-2000 hardware that has less in the way of intelligence back doors built in to function with national security systems that make stuff less secure. Keep a worm on your end of the line because we have lots more end of the line for you as Wolfman Jack used to say.
“Bitcoin has eliminated the need for money mules…”
Really? Please explain how this is the case in practice.
Interesting … I had received a letter from the provider of the card I had used at Target during the breach period that they were sending me a new card because of the breach. I assumed I was getting a new card number. I use that card to automatically pay several bills, so I updated those accounts to use a different provider’s card. My new card arrived, I opened the envelope, and I was surprised to see the same 16-digit card number, just different CSC and expiration date.
The new CSC and expiration date will prevent someone from using a fake card created from my old info. But I’m concerned about online shopping. Some retailers don’t require the CSC. All online retailers I’ve shopped with do require the expiration date, but if the old date doesn’t work what prevents the thief from guessing the new date? The new date is not so different than the old, it’s possible they could guess it on the first try. I’ve typo’d the expiration date, I know I get at least 2 tries to get it right.
I called the provider, and after some discussion the rep offered to send me a new card with a new number. I accepted the offer.
IBM WebSphere Message Queue is the mostly likely that lead to the insertion of the malware by BMC patrol BMC patrol is a WMQ systems performance application that has non-console administrative access to WMQ. In over 90% of organizations it is left wide open (like admin admin security 101). WMQ is the conduit in many cases to the insertion of malware. You can ask IBM’s red team about this. IBM WebSphere MQ runs over $250 Quadrillion of transactions annually through POS and other financial systems. Like all other hacks there are on line cookbooks. Since this technology is over 20 years old and is running on over 80% of the fortune 500 it gets inherited in acquisitions and no one checks to see if it’s secure. One day folks will see that middleware is not just plumbing it’s the weakest link in the security chain. Here is a link to our research done in conjunction with the University of WA information school. http://www.screencast.com/t/UDNFGPpYBUzD
Ariel, you should read the technical documents. I don’t think there’s any evidence that BMC’s Patrol product was involved in the breach. The hackers did use an account for BMC’s Perform product to copy files to a central location.
Also, did you mean to write Patrol HAS a WebSphere systems performance application? There is a Patrol KM to monitor WebSphere, but again I don’t think there’s any evidence that Patrol was involved in the breach, and I don’t think there’s any evidence that WebSphere did either.
I’m not clicking on your link, btw. I have a feeling it’s an advertisement.
Serena- With all due respect. I read the technical documents and access to Patrol was identified. If you connect the dots you would ask the question how did the access patrol in the first place? It is a clue. They didn’t only copy files. The forensics on this needs to go deeper and identify the interconnectivity back doors that are allowing admin access to insert malware. It’s not enough to know what happened at the target. We need to prevent these types of issues from costing users more banking fees that these irresponsible companies leave their networks wide open. As for the advertisement, IEEE is not in the business of advertising, nor is the University of WA. My intention is to educate and ask folks to look in places that they are not looking. All the best, Ariel.
The documents stated that best1_user was utilized to copy files, not to access the systems. And the hackers didn’t “access Patrol”. The best1_user account is not a Patrol account. It’s a Perform account. Perform is not Patrol.
We now know more because Brian published a new article about the method of accessing the Target system. It appears the initial access had nothing to do with BMC products or user accounts.
We must always remember:
People make mistakes.
Software is written by people.
Software contains mistakes.
The same adage goes for database design, system design, system administration, etc. We must bring more attention to bear on the response to a breach incident.
We must become better at detecting the bad guys, and faster at responding to intrusions. This will take a combination of people and technology.
Great reading and a lot of details. Awesome work Mr. Krebs. I’m a fan of your site. Good Job!