Earlier this month, I wrote about an organized cybercrime gang that has been hacking into HR departments at organizations across the country and filing fraudulent tax refund requests with the IRS on employees of those victim firms. Today, we’ll look a bit closer at the activities of this crime gang, which appears to have targeted a large number of healthcare and senior living organizations that were all using the same third-party payroll and HR services provider.
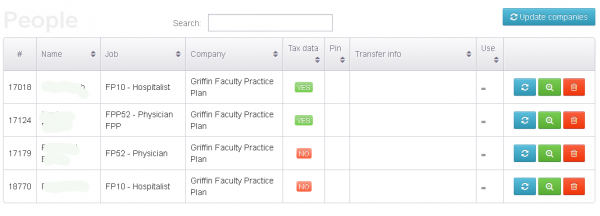
 As I wrote in the previous story, KrebsOnSecurity encountered a Web-based control panel that an organized criminal gang has been using to track bogus tax returns filed on behalf of employees at hacked companies whose HR departments had been relieved of W-2 forms for all employees.
As I wrote in the previous story, KrebsOnSecurity encountered a Web-based control panel that an organized criminal gang has been using to track bogus tax returns filed on behalf of employees at hacked companies whose HR departments had been relieved of W-2 forms for all employees.
Among the organizations listed in that panel were Plaintree Inc. and Griffin Faculty Practice Plan. Both entities are subsidiaries of Derby, Conn.-based Griffin Health Services Corp.
Steve Mordecai, director of human resources at Griffin Hospital, confirmed that a security breach at his organization had exposed the personal and tax data on “a limited number of employees for Griffin Health Services Corp. and Griffin Hospital.” Mordecai said the attackers obtained the information after stealing the organization’s credentials at a third-party payroll and HR management provider called UltiPro.
Mordecai said that the bad guys only managed to steal data on roughly four percent of the organization’s employees, but he declined to say how many employees the healthcare system currently has. An annual report (PDF) from 2009 states that Griffin Hospital alone had more than 1,384 employees.
“Fortunately for us it was a limited number of employees who may have had their information breached or stolen,” Mordecai said. “There is a criminal investigation with the FBI that is ongoing, so I can’t say much more.”
The FBI did not return calls seeking comment. But according Reuters, the FBI recently circulated a private notice to healthcare providers, warning that the “cybersecurity systems at many healthcare providers are lax compared to other sectors, making them vulnerable to attacks by hackers searching for Americans’ personal medical records and health insurance data.”
According to information in their Web-based control panel, the attackers responsible for hacking into Griffin also may have infiltrated an organization called Medical Career Center Inc., but that could not be independently confirmed.
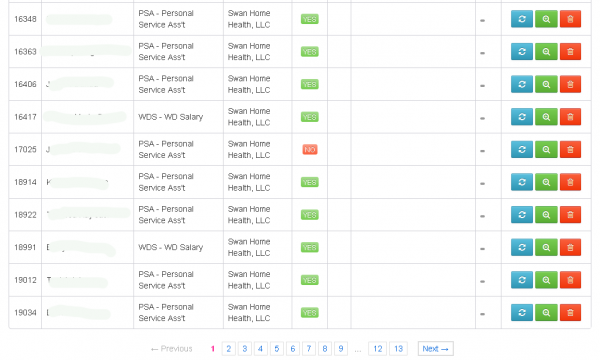
This crime gang also appears to have targeted senior living facilities, including SL Bella Terra LLC, a subsidiary of Chicago-based Senior Lifestyle Corp, an assisted living firm that operates in seven states. Senior Living did not return calls seeking comment.
In addition, the attackers hit Swan Home Health LLC in Menomonee Falls, Wisc., a company that recently changed its named to Enlivant. Monica Lang, vice president of communications for Enlivant, said Swan Home Health is a subsidiary of Chicago-based Assisted Living Concepts Inc., an organization that owns and operates roughly 200 assisted living facilities in 20 states.
ALC disclosed in March 2014 that a data breach in December 2013 had exposed the personal information on approximately 43,600 current and former employees. In its March disclosure, ALC said that its internal employee records were compromised after attackers stole login credentials to the company’s third-party payroll provider.
That disclosure didn’t name the third-party provider, but every victim organization I’ve spoken with that’s been targeted by this crime gang had outsourced their payroll and/or human resources operations to UltiPro.
Enlivant’s Lang confirmed that the company also relied on UltiPro, and that some employees have come forward to report attempts to file fraudulent tax refunds on their behalf with the IRS.
“We believe that [the attackers] accessed employee names, addresses, birthdays, Social Security numbers and pay information, which is plenty to get someone going from a tax fraud perspective,” Lang said in a telephone interview.
ULTIPRO & THE TWO-FACTOR SHUFFLE
I reached out to Ultipro to learn if they offered their customers any sort of two-factor authentication to beef up the security of their login process. Jody Kaminsky, senior vice president of marketing at Ultipro, confirmed that the company does in fact offer multi-factor authentication for its customers.
“We strongly encourage them to use it,” Kaminsky said. “We’d prefer not to provide any specific details about how it works that might assist or enable those who may attempt to break the law. Unfortunately, it does seem like this tax fraud scheme is pretty widespread and certainly not limited to our customers. We are aware of a few of our customers who have been impacted, however we can’t provide any further information due to confidentiality obligations.”
Kaminsky did not respond to questions about how long UltiPro has been offering the multi-factor solution. But information shared by an employee at a victim firm that has not been named in this series indicates that UltiPro only recently added multi-factor logins — after a large number of its customers had already been compromised by fraudsters who were plundering W-2 data to file fraudulent tax refunds.
A copy of a message sent by UltiPro to its customer base indicates that on Feb. 6, 2014 the company temporarily suspended access to individual employee W-2 records for all customers. That message reads, in part:
“On February 6, 2014, we applied an update to UltiPro to remove administrator/manager access to W-2s as a proactive measure in response to a specific new security threat we have been alerted to this tax season. Across all industries and providers, there is increasing activity that targets payroll administrators and any user with access to multiple employee records, where malicious groups or individuals are attempting to obtain employee W-2 information for the purpose of committing tax fraud. Any organization, regardless of payroll provider, is a potential target of this threat where the malicious group uses malware to spy on customer or end-user’s workstation to obtain user names and passwords. If obtained, any user name and password can then be used to log in, obtain employee W-2 information, and file that information for tax fraud purposes.”
“For this reason, we took immediate action to protect your employees by removing access for managers and administrators to individual employee W-2s. We will be releasing an UltiPro update restoring administrator and manager access with an additional level of authentication to validate the identity of the user. This UltiPro update is targeted for Sunday, February 9.”
On Feb. 9, UltiPro told customers that it was restoring access to employee W-2 information, and that managers and payroll administrators trying to access those records would be presented with an eight-digit “security access code request” — a text message delivered to a mobile phone designated by each user. That communication stated that each access code would be valid for only a short time before it expired, and that administrators could view employee W-2s for an hour before being logged out and forced to request another code.
UltiPro also told customers that it was instituting new changes to alert administrators via email about any users that modify their contact information:
“If a user changes a primary email address in UltiPro, he/she will receive an email to the previous email address communicating that a change occurred and to contact the administrator if the change was not initiated by him/her,” the company said in an Feb. 10 email to users. “If a user changes a secondary email address, he/she will receive an email to the primary email address with that same message.”
It remains unclear why so many individuals in the healthcare industry have been targeted by tax fraud this year. Last week, I published a story showing that hundreds of physicians in numerous states were just discovering that they’d been victimized by tax fraud, although the pattern of fraud in those cases did not match the attacks against healthcare organizations detailed in this story. As I noted in that piece, the tax fraud committed against individual physicians this year was far more selective, and did not impact other employees at those healthcare organizations.
Earlier this month, the University of Pittsburgh Medical Center confirmed that a data breach thought to affect only a few dozen employees actually revealed the personal information of approximately 27,000 employees — including at least 788 who reported experiencing some form of tax fraud or bank accounts that were wiped clean as a result of the breach. It is unclear how the breach occurred, and the UPMC has declined a request for an interview.




How much can you trust a PAYROLL company if they can cannot keep W-2s safe?
Brian clearly points out in the initial article that the HR admins were compromised. That would put the issue on the IT department of the company that lost W2s.
Coming from the healthcare industry, we’re seeing this across our entire network of hospitals. I think we need to look to any central repository for all this physicians… CMS anyone?
Interesting article ! I am very familiar with Griffin Hospital, not only was I born there, but also grew up in that community which is called the “Naugatuck Valley”
As in the comment I made with the previous post I feel the IRS should be doing much more to protect refund disbursements. In an effort to speedily process refunds they don’t seem to be following best practices in authenticating recipients or that the refunds, are in fact, going to them. There are thousands of payroll sites, but only one IRS. Doesn’t it make sense that this is where the most effort should be made to get it right even if it takes more time to process refunds. If this is tightened up it will take the pressure off those hacking at the other end.
Secure Computing in a Compromised World
It’s not a State Secret: much of our Personally Identifiable Information (“PII”) has been leaked, hacked, sold, or otherwise distributed to most anyone interested, including disreputable re-sellers.
If we accept that as an existing condition ,– what sort of response might we make now?
The answer lies in the proper authentication of transactions.
Any miscreant may have my PII — or yours — or — untold thousands of files. This is the reality we must all live with today.
Which leads me to a key sentence in the testimony of Whitfield Diffie in behalf of the NewEgg Supply Co v TQP Holdings: *reference(1)
quote:
There was one other big need: proving authenticity.
“The receiver of the document can come into court with the signed document and prove to a judge that the document is legitimate,” he said. “That person can recognize the signature but could not have created the signature.”
:unquote
The CRITICAL POINT is well stated by Mr. Diffie here: a signature must be such that it can be authenticated — but not forged.
PGP signatures — are one answer. A miscreant might have your Social Security number, your date of birth and your dog’s name — but he would not be able to file a 1040 with the IRS or make charges to your credit card or log into your Credit Union — if proper use of PGP — including trust models — were common practice. *note(2)
Proper use of PGP should be taught in school. and especially the procedures for establishing trust models for keys — and protecting public keys from tampering. all of which is covered beautifully in Phil Zimmerman’s original essay. *reference(3)
all of us should have PGP installed, and have our own public/private key pair, and maintain a Trust Model in our keyring.
this represents a significant change in computing practices. Many of us see the need for change while many are unfortunately resigned to thinking hacking is inevitable.
Change is in the wind though,– *reference(4)
*reference(1): Whitfield Diffie
“http://arstechnica.com/tech-policy/2013/11/newegg-trial-crypto-legend-diffie-takes-the-stand-to-knock-out-patent/
*note(2): secure operating software required. like PGP this is available but not commonly used.
*reference(3): Phil Zimmerman
http://www.pa.msu.edu/reference/pgpdoc1.html
*reference(4) power of FTC to sue companies for poor security practice:
http://www.zdnet.com/judge-enhances-ftcs-power-to-sue-over-security-breaches-7000028357/
>A miscreant might have your Social Security number, your date of birth and your dog’s name — but he would not be able to file a 1040 with the IRS or make charges to your credit card or log into your Credit Union — if proper use of PGP — including trust models — were common practice.
But what happens if the PGP user’s Linux system were compromised and the private keys were stolen? We’re right back here where we started.
First, rather than compromising one easy target, a database with a lot of valuable info, you’re making the bad guys go out and find individuals to steal from which is much harder to get the same level of value.
Second, I would suggest NOT tohave a system that requires training. Complexity is contrary to good security. You want a system that’s brain dead easy. There are probably many good solutions, I like the idea of a crypto smart card where you can’t get at the private key and with a pin if you lose it
The advantage of certificate based augments to transaction security is that one can published revoked keys. So, even if the private keys are stolen, the public key can be revoked and now public/private key pair issued.
The speed that this can be done is rather fast. So, I think the notion of a password protected private key and public key pair can provide sustainable digital signatures even in after a hacking theft of private keys.
First, one also has to flush the password for the private key and test against the public key for valid signatures — this requires work for the attacker.
Second, one has to complete the validation faster than the detection and key revoking process works.
The second point is the true risk. If 30% of firms cannot tell they are under active attack for 2 years, then the detection process needs real enhancement.
This clears up a puzzle I’ve had for several years. I was the email administrator at my previous job and the only people who were really spearphished were the HR people. Luckily they were smart and careful and forwarded the messages to me without opening any attachments. They were really the only people getting this sort of messages.
We were wondering what the point of the messages were, I thought it was to get employee information and now I bet that fraudulent tax returns were the goal. This is an investment firm with around 200 employees at that time (3 years ago).
HR departments also may have access to employee bank account information for direct deposit.
I had a very strong hunch the problem was related to HR/Payroll processing, especially W-2s. Miscreants had to have gotten their grimy paws on W-2s to pull this off. Imagine if they had gotten in to a huge processor like ADP. It’s a horrifying thought.
I remember laughing to myself at a poster in the initial blog entry about this issue blaming the ACA when the problem very clearly pointed elsewhere.
The IRS is behind the times in the worse possible way and in the meantime taxpayers are on the hook for their screw ups. The IRS cannot be issuing refunds without some sort of verification process. If this isn’t corrected soon, imagine how much taxpayers will lose in subsequent years. Sigh!
ADP had their clients attacked as well prior to June 13, 2013. http://www.cpapracticeadvisor.com/news/10960446/hackers-hit-commercial-and-us-military-payroll-services
“Stolen identities were also used to file fraudulent tax returns with the IRS seeking refunds.”
If this is a new group they are just picking up where the old group left off. Probably the same people are involved.
For the past 5 years I have mailed my 1040A to IRS in Austin on the first Monday in April. My refund was EFT to my bank within 2 weeks. My 2013 was mailed the first Monday in April. As of this date, no EFT to my bank.
I’m concluding all this fraud filing has stalled a lot of timely refunds. All the IRS has to do is compare my filing with the past 5 years and see that the only change to my filing status is the slim COLAs and related withholdings.
I never give out my SS# to any physician or hospital. If you have medical insurance there is no need to. Your insurance company already has that information. Well stupid me, when I wasn’t feeling good, my doctor who worked in a Florida Hospital asked for mine and I gave it to him.(The hospital had a new system for all the hospitals, so doctors could access your medical info easier) Funny that was the same year I had income tax fraud on my SS#
ADP got hit by Heartbleed and I had to actively go search for alerts since they’ve been one of our vendors.
They put out a press release on the 10th saying a few of their systems were vulnerable. No word on a fix or anything.
https://www.adp.com/~/media/Media/Trust%20Center%20Alerts/GSOSecurityAlert_041014.ashx
Hopefully, some day people will actually take security seriously.
DB
I feel like I’m missing something. If these companies were victims of spearphishing to steal login credentials to their UltiPro accounts, why are there so many different companies that all happen to be UltiPro customers? Obviously they targeted UltiPro customers because UltiPro doesn’t force multi-factor authentication, but how did they know all these companies were UltiPro customers? The commonality is that they are all healthcare related, but that doesn’t explain how the attackers knew they were all UltiPro customers. Either there is another commonality, or UltiPro has/had a breach. Am I wrong?
There can be many explanations for this. The simplest is that the attackers merely went to several underground forums/communities and said hey, botnet owners selling stuff from your botnet logs: I’ll take any and all credentials you may have for victims who have logged in at UltiPro.
Why then the healthcare theme? Though an UltiPro breach wouldn’t explain that either.
I guess what I don’t understand is why all UltiPro customers AND Healthcare?
Ultipro’s target market is Healthcare Management.
What makes you think UltiPro’s target market is Health Management? Their website disagrees with you. Even if the majority of their customers are health management, we should still see one or two victims from other industries. I still feel like we’re missing an important detail.
I commented too soon. I had mistaken HCM to mean HealthCare Management not Human Capital Management.
IMHO, as an auditor who is by nature suspicious of everything and everyone, UltiPro probably has a low tech data thief like Heartland did inside their organization who has access to UltiPro customer admin userids, passwords/phrases, and the ability to decrypt them. At just about every corporation I worked at, there was at least 3 people who could (for DR/BC) decrypt password files with supposedly enterpise breakglass keys. Copy some files during routine maintenance or (dare I say it) a DRP/BCP test, decrypt them at home, sell ’em piecemeal online. Doesn’t matter if the locking mechanism gets changed, if it’s the thief changing the locks.
Not knowing much about the internet undergroud, your explanation explains alot on how targeting can take place.
This isn’t the full picture. Brian only has access to a very small subset of the underground community. If you look at the broad scope of attacks using fraudulent tax claims as a method to obtain money you will see that there is no single provider of software that’s being targeted. PeopleSoft customers got hit earlier in the year, as did ADP customers and whatever system was used by the US military that got hit. Most likely a number of smaller companies were targeted as well but didn’t garner enough attention because there wasn’t enough users to complain.
The curious thing is why the attackers are only filing false tax claims. Why have the attackers only siphoned money out of bank accounts off a few customers of ADP? Don’t they have all the necessary information from these payroll providers? Is it harder to siphon out the money from a bank account than it is to collect on a fraudulent tax return?
Don’t lose sight of the trees looking at the forest.
Carrying your logic a step farther, if you look at the broad scope of attacks to obtain money fraudulent tax returns are just a small part of it, so why suspect there’s a common root cause?
It’s looking at patterns in the data, using correlation to identify relevant factors. There is a common point in the fraud against medical practitioners so that’s a good place to start looking. In the past Brian has been the first to disclose (and possibly even to recognize) some major breaches, based on just the same sort of patterns. Remember Target?
So please don’t discount it so blindly. Or are you just muddying the waters because he cut close to the truth again?
Why file false income tax claims on a few customers? Simple – it’s a test to see if their process flow works, profile the response, and work out the kinks in their theft logic. Then go big.
“after a large number of its customers has already been compromised by fraudsters who were plundering W-2 data to file fraudulent tax refunds.”
May have wanted to use “had already”.
As usual your follow-ups are as great reading! Thanks Brian.
A good article inspires smart and insightful comments. Glad to see all that here. Now if Brian could only expose those IRS impersonators/scammers who keep calling my house!
I have just received an email from sbcglobal.net and it looks like this has been hacked. It came my company email address. Do you know anything about sbcglobal being hacked?
BK doesn’t usually answer questions like that in his column comment sections, Lynn. You might want to email him about it. The fact of the matter is, though, that many email accounts are hacked because people use passwords that electronic information thieves can crack easily, or click on links in email messages that they shouldn’t have clicked on.
If you’re not sure what to do about your email account, there are a lot of good guides out there about how to deal with an account hijacking. Here’s one, for instance, about how to change your sbcglobal password: https://answers.yahoo.com/question/index?qid=20110805075747AA7tr7S
Here’s a blog post from BK about creating good passwords: http://krebsonsecurity.com/password-dos-and-donts/
Best wishes to you.
Commenting to User (4/30/14 2:20pm): Yes, tax refund fraud is much easier than bank account-takeover fraud. And the reason they’re attacking HR departments is because of one-stop-shopping for identity theft; and W2’s contain everything else you need for a legit-looking tax return that will fly through the IRS system and spit out a hefty refund.
The real problem lies with Congressional mandate. The IRS is obligated by law to churn out those refunds fast, and given relatively little in the way of resources to stop refund fraud. Everybody likes to blame the IRS, but they can only do what Congress funds them to do which, for the last few years, has been less than the year before.
And yes, the solution to tax refund fraud also lies with the IRS. They could implement the same CIP (customer identification program) procedures required by the US Patriot Act, which are followed by every bank for new accounts. That would stop about 80% of refund fraud and slow down legit refunds by about a week — if Congress mandated it and paid for it.
Today, according to: http://www.whitehouse.gov/the-press-office/2014/05/01/fact-sheet-big-data-and-privacy-working-group-review
“Big data is making government work better and saving taxpayer dollars. The Centers for Medicare and Medicaid Services have begun using predictive analytics—a big data technique—to flag likely instances of reimbursement fraud before claims are paid. The Fraud Prevention System helps identify the highest-risk health care providers for waste, fraud, and abuse in real time and has already stopped, prevented, or identified $115 million in fraudulent payments.”
And found within the accompanying (three-months-in-the-making) PDF report entitled:
BIG DATA: SEIZING OPPORTUNITIES, PRESERVING VALUES presented to the President today:
“…in 2014, the Internal Revenue Service made it possible for taxpayers to digitally access their last three years of tax information through a tool called Get Transcript. Individual taxpayers can use Get Transcript to download a record of past tax returns, which makes it easier to apply for mortgages, student loans, and business loans, or to prepare future tax filings.”
So there you go! We’re well on our way to a Congressional mandate.
I just wonder why “taxpayers” isn’t capitalized… no wait!
“Interesting article ! I am very familiar with Griffin Hospital, not only was I born there, but also grew up in that community which is called the “Naugatuck Valley””
I as well, live in the valley and was just at the hospital. The room I was in had an unlocked XP machine in it.
Being a recent victim of tax fraud id theft, I was very interested in your article. For my situation, I have no relationship to the hacked health care facilities you mentioned. My guess is that the problem is much worse than you state. Still I am unsure where the vulnerability arises. Was it my doctor’s office, the hospital I went to, my insurance company, my employer? Even though I am very careful of the security on my computer, apparently less care is taken elsewhere.
Who is this cybercrime gang? The IRS won’t tell me where the tax refund was deposited or any other information.
What is it with the dates of your time warped articles, Brian?
Many previous ones have a dateline of Apr 14
This one has a prophetic dateline of May 15!
I wonder what galaxy these articles come from.
The content is certainly out of this world 🙂
Terry, I’m pretty sure you’re being facetious, but in case you’re not, the big number is the day.
Oops, my mistake, I was misreading 14 as the date instead of the year. Time to put my brain back in gear.
I had commented in the prior UltiPro article that I discovered UltiPro has a phone app called UltiPro Mobile. Am I overly paranoid? Phone app access to my personal data makes me very nervous! Maybe it’s only intended to be used by employees for performing their own functions (like requesting time off or viewing latest paycheck details) and not intended for those with admin privileges. Who knows though.
UltiPro is partially at fault. They offer two factor authentication but don’t require it? They should be the experts at securing employee data, not the HR departments which purchase their services.
ULTIPRO & THE TWO-FACTOR SHUFFLE –
UltiPro’s two-factor implementation is broken, at least in their current SaaS offering. It’s a global setting which when turned on, forces a two-factor challenge before a user can access another user’s sensitive data (PII, W2, etc.). So far, so good. Here’s the scenario where UltiPro’s 2FA is broken.
A HR admin can login to the UltiPro site with only their username/password. Only when they attempt to access PII are they prompted to either receive a code by text or voice, before they are allowed to see the data. The admin selects which number to send the text or voice code, and clicks submit. They enter the code, and are then able to access the PII.
The problem is that the 2Factor prompt page also includes a link to “Update or Add a New Number”, where you can then choose to receive the code! Obviously, if a bad actor already has the credentials of a HR Admin, all they need to do is login, add a new number when the 2Factor page appears, and have the code sent to their phone. They get the code, and are then allowed to see the PII and export it at will.
Broken 2Factor, right?