Until today, Microsoft Windows users who’ve been unfortunate enough to have the personal files on their computer encrypted and held for ransom by a nasty strain of malware called CryptoLocker have been faced with a tough choice: Pay cybercrooks a ransom of a few hundred to several thousand dollars to unlock the files, or kiss those files goodbye forever. That changed this morning, when two security firms teamed up to launch a free new online service that can help victims unlock and recover files scrambled by the malware.
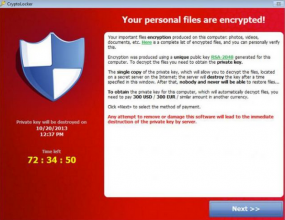 First spotted in September 2013, CryptoLocker is a prolific and very damaging strain of malware that uses strong encryption to lock files that are likely to be the most valued by victim users, including Microsoft Office documents, photos, and MP3 files.
First spotted in September 2013, CryptoLocker is a prolific and very damaging strain of malware that uses strong encryption to lock files that are likely to be the most valued by victim users, including Microsoft Office documents, photos, and MP3 files.
Infected machines typically display a warning that the victim’s files have been locked and can only be decrypted by sending a certain fraction or number of Bitcoins to a decryption service run by the perpetrators. Victims are given 72 hours to pay the ransom — typically a few hundred dollars worth of Bitcoins — after which time the ransom demand increases fivefold or more.
But early Wednesday morning, two security firms – Milpitas, Calf. based FireEye and Fox-IT in the Netherlands — launched decryptcryptolocker.com, a site that victims can use to recover their files. Victims need to provide an email address and upload just one of the encrypted files from their computer, and the service will email a link that victims can use to download a recovery program to decrypt all of their scrambled files.
The free decryption service was made possible because Fox-IT was somehow able to recover the private keys that the cybercriminals who were running the CryptoLocker scam used on their own (not free) decryption service. Neither company is disclosing much about how exactly those keys were recovered other than to say that the opportunity arose as the crooks were attempting to recover from Operation Tovar, an international effort in June that sought to dismantle the infrastructure that CryptoLocker used to infect PCs.
That effort culminated in the takeover of the GameOver Zeus botnet, a huge crime machine that infected an estimated 500,000 to 1 million PCs and that was being used as a distribution platform for CryptoLocker.
“After Operation Tovar, a significant blow was dealt to criminals infrastructure and we stopped seeing new Cryptolocker infections being spread,” said Uttang Dawda, a malware researcher with FireEye. “They tried to recover that infrastructure, but in the process copied over the private encryption keys to a part of Fox-IT’s infrastructure.”
Dawda said it’s important to note that this service only unlocks files encrypted by CryptoLocker. Although there are several copycat strains of malware — including CryptoWall, CryptoDefense and OnionLocker — CryptoLocker has by far the largest “market share” among them.
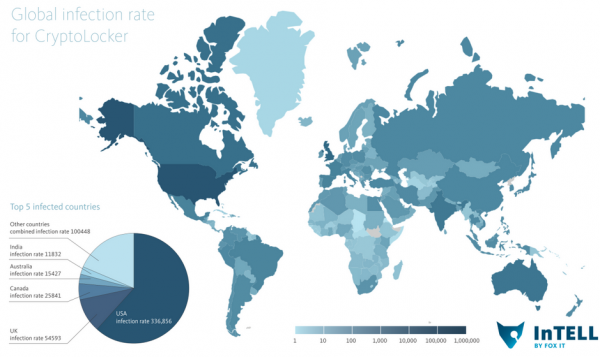
It’s not clear how many systems are infected with CryptoLocker, but it is likely to be in the six figures. According to Fox-It, when CryptoLocker infections first started in September 2013, the largest number of infections in one month occurred during October 2013, with over 155,000 systems affected worldwide. After October 2013 the rates dropped, but still steadily pacing at around 50,000 infections per month.
Sadly, most of those victims probably lost all of their most treasured files. Fox-It says that only 1.3% of victims paid a CryptoLocker ransom.
“Therefore, a large amount of victims likely permanently lost files due to this attack,” the company wrote in a blog post about the new service.




If you want to get a good deal from this piece of writing then you have to apply such methods too your won blog.
My bblog posxt web site (Ines)
Great article! We will be linking to this
particularly great article on our website. Keep up the great
writing.